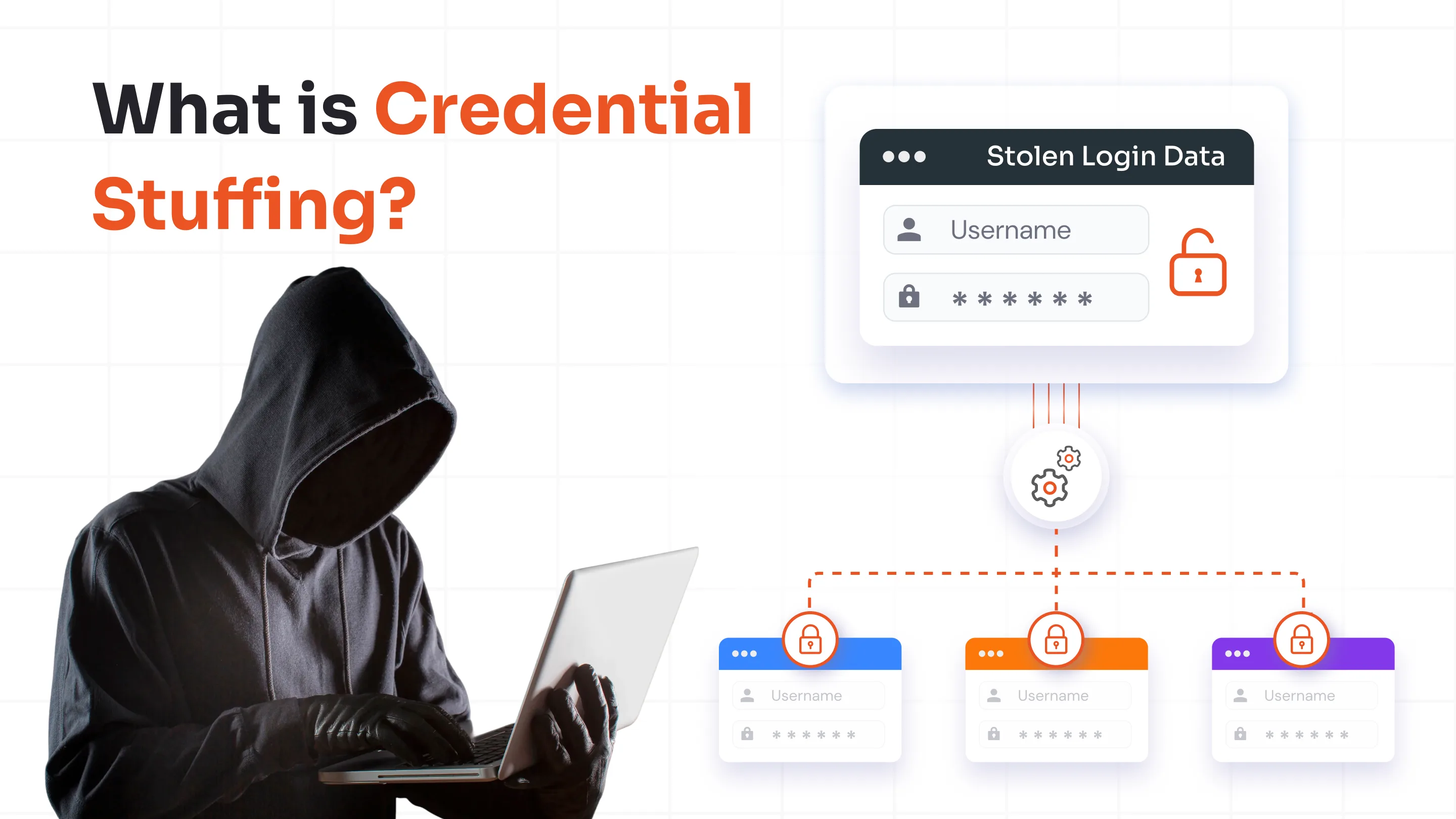
Organizations successfully blocked 99.9% of automated cyberattacks through the implementation of Multi-Factor Authentication (MFA) for their Active Directory (AD) systems. The implementation of MFA transforms organizational security by requiring attackers to overcome multiple verification barriers. Research indicates that more than 80% of data breaches start with compromised credentials, which makes MFA adoption essential for organizations to protect themselves.
Organizations that implement MFA for AD along with real-time monitoring and adaptive risk management practices experience major reductions in successful cyberattacks. The blog examines important data points and practical implementation methods to prove MFA serves as a fundamental element of contemporary cybersecurity approaches.
Why You Need Multi-Factor Authentication for Active Directory
The implementation of multi-factor authentication (MFA) strengthens Active Directory security because it requires authentication methods beyond passwords. Your environment must authenticate identities through multiple security layers, which makes unauthorized access extremely difficult. MFA provides protection against phishing attacks, brute-force attacks and stolen credentials.
AD multi-factor authentication helps organizations meet the requirements of industry standards and regulatory requirements. Your security posture improves while sensitive data protection increases through the implementation of an additional verification process. MFA has become a standard security measure for enterprises because it helps organizations protect their valuable IT assets from cyber threats.
MFA simplifies security operations through its ability to reduce breaches while making risk management more straightforward. The identity verification process evolves from a single vulnerable point into a strong multi-step authentication system. Your organization will gain trust through this approach while showing dedication to modern cybersecurity practices.
Benefits of Using MFA for Active Directory (AD)
Active Directory security depends on multi-factor authentication to protect sensitive data while enhancing cybersecurity measures. The implementation of MFA for AD protects against unauthorized access when passwords are compromised while simultaneously reducing attacks that rely on credentials. The additional security measure helps organizations build a strong identity and access management (IAM) framework.
The self-service capabilities for password resets and authentication challenges significantly reduce IT overhead. Fewer support requests allow your team to focus on high-impact strategic initiatives. Among the key benefits of MFA is its ability to help organizations comply with industry regulations such as HIPAA and GDPR, fostering increased trust among customers and stakeholders.
The integration of MFA with AD allows your business to expand its operations according to your growing requirements. The system adapts to new threats while providing smooth user access across your network without disrupting operations. Your business becomes more resilient when you improve security and operational efficiency, which creates a vital advantage in modern digital environments.
The implementation of MFA for Active Directory provides your organization with secure IT infrastructure protection, reduced operational risks and a dependable, agile security ecosystem that stays ahead of potential threats.
How to Enable MFA for Active Directory (On-Premise)
Multi-factor authentication provides an important security feature to protect your Active Directory infrastructure. You must understand both locations and procedures for implementing MFA throughout your organizational infrastructure. This guide provides complete instructions to establish robust MFA protection for every access point.
MFA on Windows and Linux Machines
The implementation of multi-factor authentication represents an essential security measure that strengthens protection for both Windows and Linux operating systems. The following analysis demonstrates how specific MFA active directory on-premise approaches can integrate into various systems to defend digital assets.
MFA for Windows Domain-Joined Machines
A robust MFA protection system must be activated before users can access domain resources during their Windows logon processes. Implementation options include:
- Users can authenticate with Windows Hello for Business through Group Policy to access Active Directory with biometric and PIN-based methods.
- The security platform miniOrange provides third-party MFA connectors that stop unauthorized logon attempts until users present extra authentication verification.
- The implementation of smart card requirements through Group Policy establishes certificate-based authentication that requires physical verification in addition to password authentication.
Your Windows endpoints remain secure through these solutions both in-office and remote because stolen credentials alone cannot grant access to your systems.
Linux MFA Authentication
Implement these methods to extend MFA protection to your Linux servers and workstations:
- The Linux authentication process can be extended with MFA through Pluggable Authentication Modules that function as authentication hooks.
- The combination of SSH key security gets additional protection from miniOrange's Linux MFA solution.
- Linux systems should validate their users through a RADIUS server, which will enforce MFA authentication requirements.
Linux MFA implementation secures critical infrastructure servers that often house your most sensitive data and systems.
MFA for Windows Remote Desktop Services
The security risks of remote access get resolved through MFA implementation. Secure these connection points with:
- MFA solutions at the RD Gateway level can be used to require verification before users obtain access to internal resources.
- The security feature of RD Web Access implements authentication portals that demand MFA verification before showing accessible resources.
- End users must authenticate through endpoint agents, which block unauthorized RDP connections until MFA validation occurs.
This protection stops attackers who have obtained valid credentials from connecting to your internal systems through remote desktop services.
MFA over VPNs and Network Infrastructure
Network perimeter security depends on strong authentication controls:
- The miniOrange RADIUS server serves as a security solution that enforces MFA policies for all VPN connections.
- The authentication process for network devices should extend MFA security features to administrative access for switches and routers and firewalls using RADIUS challenges.
- All connections through split-tunnel VPN configurations need to verify users through MFA authentication before they establish their VPN links.
The implementation of MFA across network boundaries protects your internal infrastructure from credential-based security breaches.
MFA for Cloud and On-Premise Applications
MFA should be integrated as a security feature across all applications in your system.
- Microsoft Office 365 users need to enable modern authentication while setting up conditional access policies that mandate MFA authentication for all user sessions.
- miniOrange Identity Server serves as an authentication broker to enforce MFA across thousands of pre-integrated applications.
- The configuration of authentication protocols should require MFA validation as users go through the authentication process.
Through this approach, organizations can enforce MFA authentication for any application access regardless of their deployment locations or user connection methods.
MFA for Legacy Applications
The authentication mechanisms of older applications create special challenges for protection.
- The deployment of proxy servers functions to intercept authentication requests to legacy applications and then demands MFA verification for authorization.
- miniOrange provides API connectors that enable MFA functionality for applications that do not have built-in support.
- Solutions must be implemented to modify HTTP headers for authentication token validation using MFA processes.
The security methods introduced here protect applications that were developed before MFA became an industry standard.
MFA for Mobile Applications
Mobile access requires specialized MFA approaches:
- Mobile applications require SDK integration to force MFA authentication at each login attempt.
- The authentication system requires certificate-based validation that checks mobile devices before asking for more verification elements.
- The authorization process incorporates MFA challenges through OAuth and OpenID Connect protocols.
Mobile MFA safeguards the increasing user population which uses mobile devices to access corporate resources.
Implementation Considerations
Your deployment of MFA across different connection points demands evaluation of these factors.
- Choose MFA methods that offer both security and usability to meet the needs of your workforce population.
- You must create defined recovery processes for times when primary authentication methods become inaccessible.
- MFA effectiveness monitoring along with potential bypass attempts detection requires implementation of logging and analytics systems.
A well-designed implementation strategy elevates MFA from basic security functionality into an extensive protection system for Active Directory environments.
How to Apply MFA for AD Without Azure: Step-by-Step
The implementation of MFA for Active Directory requires third-party solutions or custom integrations because Azure is not involved. Here’s a streamlined process for MFA integration with Active Directory:
1. Select an MFA Provider
Select a third-party MFA solution that provides Active Directory integration. Choose a solution that supports RADIUS, LDAP or SAML authentication protocols for smooth integration.
2. Install and Configure the MFA Server
The MFA server should be deployed either on-premises or in a hybrid environment. The MFA server needs to be connected to Active Directory to perform user synchronization and enforce authentication rules.
3. Enable MFA for AD Logins
Create MFA policies that can be based on group membership, device type or login method. Implement conditional access rules to improve security measures.
4. Integrate MFA with VPN and Remote Access
MFA should be extended to VPN logins and RDP sessions and other remote access points. All external connections need to comply with security policies.
5. Test and Deploy
Perform thorough testing with a pilot group before implementing the solution for everyone. The authentication process should be optimized to reduce user inconvenience while maintaining security standards.
6. Monitor and Optimize
Use logging and analytics to track authentication trends. Modify policies to improve protection while keeping usability at a high level.
This setup strengthens Active Directory authentication without Azure AD, ensuring compliance and reducing security risks.
Best MFA Methods for Active Directory
Businesses protect their Active Directory environments through leading MFA methods, which provide enhanced protection and simplified user access.
- App-based Authenticators: Microsoft Authenticator Google Authenticator and miniOrange Authenticator—enable fast, secure verification that provides seamless verification. These apps work effectively with both on-premises and hybrid AD environments and actively fight phishing and credential theft.
- Hardware Tokens: Organizations implement YubiKey hardware tokens to generate FIDO2 authentication one-time codes. The physical devices function as a tangible security element that protects against complex cyberattacks.
- Passwordless Methods: Enterprises select passwordless authentication methods, including Windows Hello and FIDO2 passkeys, to remove traditional password vulnerabilities. The solutions create easier sign-in procedures while improving compliance standards and strengthening overall security measures.
The implementation of these MFA methods enhances Active Directory security while fulfilling regulatory requirements and establishing enduring user trust. The combination of multiple security layers transforms identity verification into an unbreakable defense against cyber threats while promoting user adoption of trusted security practices.
Read More: What is the Difference Between 2FA and MFA?
Is MFA for Active Directory Necessary? Why Do You Need It?
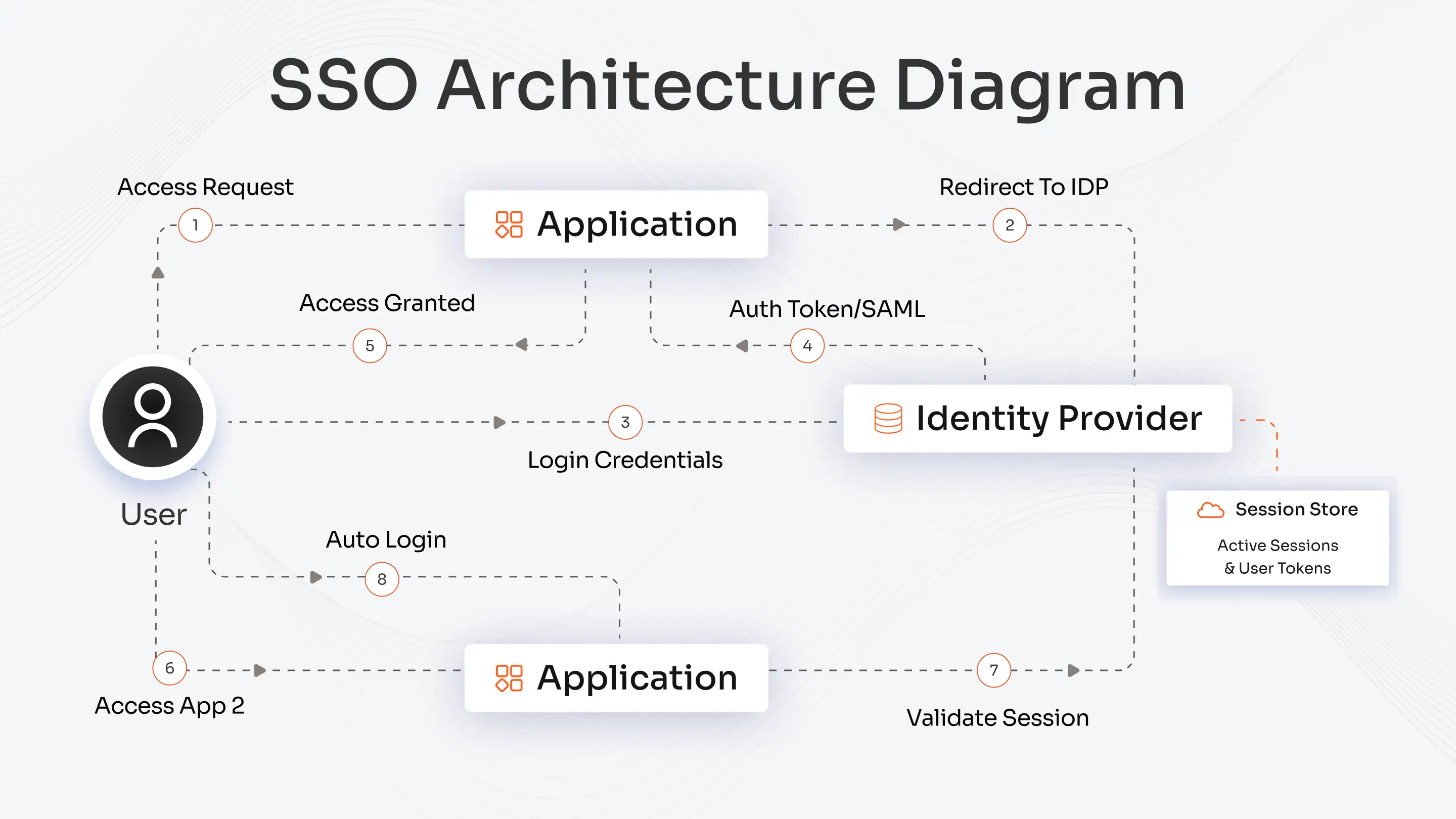
MFA stands as a crucial security measure for protecting Active Directory (AD). Single sign-on (SSO) streamlines authentication, allowing users to log in once and access all resources. The absence of MFA leaves Active Directory exposed to credential-based attacks, particularly when employees work remotely.
The security of on-premise AD depends solely on internal controls because it functions as a closed system. The lack of MFA makes it possible for attackers to use stolen credentials to access protected data and systems. MFA implementation adds an extra verification step, which protects against unauthorized access and decreases security threats.
MFA can be integrated using:
- The verification process through SMS or phone call sends a one-time code to the registered mobile device.
- Hardware tokens operate as physical devices that produce authentication codes.
- The software token authentication system includes Google Authenticator and Microsoft Authenticator applications, which generate time-based OTPs.
The MFA solutions from miniOrange offer customized authentication options that work across multiple AD environments.
Additional Features and Functionalities for MFA
The miniOrange MFA system provides organizations with an easy-to-implement security solution that delivers robust protection and maintainable functionality for various business requirements.
- Offline MFA: The system enables authentication operations even when there is no internet connection, thus providing uninterrupted protection across all network conditions.
- Effortless AD Integration: The system provides support for both cloud-based and on-premise identity server implementations. The miniOrange Gateway module enables secure non-public AD connections, while LDAP serves as the protocol for on-premise Active Directory integration.
- Streamlined Self-Enrollment: Users who register through a secure link can perform self-enrollment for MFA regardless of their on-site or remote location. Users can access a simple self-service console to modify MFA methods, reset passwords and manage their credentials autonomously.
- Flexible Groups and Policies: Through group segmentation, administrators can establish specific MFA policies for their AD users. The approach enables organizations to implement adaptive authentication while maintaining exact control over application access and restrictions which matches their business model.
The advanced feature set provides organizations with a secure and simple and scalable MFA deployment solution.
How miniOrange Helps You Secure Active Directory with MFA
The miniOrange platform enhances Active Directory security through powerful MFA protocols, which protect your network infrastructure without performance degradation. Our solution integrates quickly and seamlessly with on-premise AD, ensuring that your authentication process remains smooth and secure from day one.
Our company provides affordable, scalable solutions that meet the needs of worldwide enterprises. Our MFA strategy includes components that scale up with your business growth. Your organization benefits from advanced security technology through our solutions, which maintain both financial efficiency and deployment flexibility.
Our organization maintains ongoing operations through 24/7 support and flexible deployment choices to protect your environment throughout the day. Our team of experts will analyze your specific requirements to develop identity management solutions that optimize your framework.
Take control of your security today. Talk to an expert at miniOrange to discover how our team will implement seamless MFA integration with Active Directory against contemporary threats.
Conclusion
The implementation of Multi-Factor Authentication (MFA) for Active Directory (AD) represents an essential requirement in the current threat environment. Organizations strengthen their authentication systems to protect their sensitive information and user identity credentials. MFA implementation for AD enhances security while improving compliance standards and establishing enduring user trust.
Success depends on both simplicity and scalability. Your organization can achieve strong protection through either Microsoft built-in tools or trusted third-party integrations like miniOrange MFA Product, which supports multiple types of biometric authentication, including fingerprint scanning, facial recognition, and iris detection, while maintaining an easy-to-use experience for users. Security investments made today will prevent breaches, enhance credibility, and establish long-term stability.
Your digital future becomes secure through confident protection. Choose miniOrange to power your MFA strategy with solutions that protect and perform. Request a demo and POC for miniOrange MFA for AD. Your users and your business depend on it.
FAQ's
Can I enable MFA for AD without Azure?
The implementation of MFA for Active Directory becomes possible without Azure. The native certificate-based authentication system in Windows Server 2019 works alongside miniOrange's dedicated on-premises MFA solution that connects directly to Active Directory. The solution supports various authentication protocols and functions autonomously, while RADIUS servers with OTP or smart cards via AD Certificate Services provide additional security for Windows systems.
What’s the best MFA method for AD?
The majority of Active Directory environments find certificate-based authentication to be the perfect solution for security and convenience needs. Users experience a smooth authentication process through push notifications, TOTP works offline and smart cards provide maximum security for sensitive data. Additional security can be achieved through the combination of biometric authentication with another authentication factor. Select your method according to compliance needs, user experience requirements and security requirements.
Is MFA for AD compliant with NIST?
The implementation of MFA for AD fulfills NIST SP 800-63B requirements through the use of two authentication factors together with phishing-resistant methods, including certificates or FIDO2. The implementation of SMS-only systems should be avoided because NIST has withdrawn its recommendation for this method. The authentication chain needs to use approved cryptographic standards together with correctly configured account lockout policies to stay compliant.
How long does AD MFA setup take?
The deployment process for enterprise AD MFA typically spans between one and three months. The deployment process includes 1–2 weeks for planning, followed by 1 week for pilot deployment, 1–2 weeks for testing, 1 week for user training, and 2–8 weeks for phased rollout depending on organization size. A strategic implementation approach reduces disruptions while enabling you to reach your security targets.


Leave a Comment