SAMA compliance in Saudi Arabia marks a pivotal cybersecurity evolution, safeguarding the booming financial sector against sophisticated cyber threats. As Saudi Arabia advances its Vision 2030 digital transformation, the Saudi Arabian Monetary Authority (SAMA) has rolled out the SAMA compliance framework, a comprehensive set of regulations mandating robust cybersecurity for all licensed financial institutions.
What is SAMA compliance? At its core, it's Saudi Arabia's strategic cybersecurity move to fortify banks, insurance firms, financing companies, and financial market infrastructures. The framework spans four key domains: governance and oversight, cybersecurity controls (including identity and access management), third-party risk management, and incident response. Enforced since 2020 with periodic updates, it requires organizations to achieve specific maturity levels, verified through annual audits.
This guide breaks down SAMA compliance in Saudi Arabia, from framework basics to a practical roadmap. Whether you're building a SAMA compliance checklist or seeking consulting, miniOrange's identity and privileged identity solutions align seamlessly to speed up your compliance.
Understanding SAMA Compliance Framework
The SAMA compliance framework serves as the cornerstone of SAMA compliance in Saudi Arabia, providing a structured blueprint for cybersecurity resilience. Drawing from global benchmarks like NIST CSF, ISO 27001, Basel Committee guidelines, and PCI DSS, it ensures financial entities in the Kingdom maintain high maturity across critical areas. SAMA compliance in cybersecurity emphasizes proactive defenses, making it indispensable for protecting sensitive customer data and operations.
What is SAMA Compliance?
SAMA compliance in cybersecurity delivers a unified approach to cyber risk management, fostering optimal maturity in security controls while safeguarding the broader financial ecosystem. Unlike generic standards, it's tailored to Saudi Arabia's regulatory environment, integrating Sharia principles where applicable. The framework mandates 20 control objectives across domains, scored on a 1-5 maturity scale, Level 3+ required for most banks.
Who Must Comply with SAMA Compliance?
SAMA compliance in Saudi Arabia mandates adherence for these SAMA-licensed entities:
- Banks and banking institutions (full framework required)
- Insurance and reinsurance companies (risk-based implementation)
- Financing companies and money changers (cybersecurity/third-party focus)
- Financial market infrastructures (e.g., stock exchanges, clearing houses)
- Fintech firms and digital banks (pre-licensing proof required)
- Foreign branches/subsidiaries (subject to on-site inspections)
Core SAMA Compliance Principles & Internal Control
The SAMA Compliance Principles & Internal Control drive execution through these pillars:
- Board-endorsed cybersecurity governance (strategy approval, KPIs)
- Risk management integrated with enterprise processes (annual threat modeling)
- Operational controls for information assets (IAM, PAM, encryption, vulnerability management)
- Third-party security (vendor assessments, SLAs, right-to-audit)
Consequences of Non-Compliance
Non-compliance triggers escalating penalties under SAMA compliance. Financial fines reach SAR 5 million per breach (e.g., SAR 100K+ for IAM gaps), alongside operational restrictions like service suspensions. Severe cases lead to license revocation, public disclosures, and executive liability under Saudi cyber laws. In 2025, SAMA levied over SAR 20M in penalties across 50+ violations.
The Four SAMA Compliance Framework Domains
The SAMA compliance framework structures cybersecurity requirements into four interconnected domains that collectively fortify Saudi Arabia's financial ecosystem. Each domain addresses specific risk areas while ensuring organizations achieve maturity-optimized security controls aligned with SAMA compliance principles & internal control standards. Here's the detailed breakdown:
Cyber Security Leadership & Governance
Boardroom Accountability is Non-Negotiable. This foundational domain demands executive-level commitment through a board-endorsed cybersecurity governance structure that cascades responsibility throughout the organization. Organizations must establish:
- Documented cybersecurity strategy aligned with Vision 2030 business objectives
- Enterprise-wide cybersecurity policy communicated to all employees
- Clear roles & responsibilities matrix following SAMA internal audit principles
- Cybersecurity governance integrated into project management frameworks
The Outcome: Significant shift from siloed IT security to enterprise-wide risk ownership. Boards answer directly to SAMA for cybersecurity maturity, ensuring SAMA compliance principles drive organizational culture.
Cyber Security Risk Management & Compliance
From Reactive Firefighting to Proactive Risk Mastery. This domain mandates enterprise risk-aligned cybersecurity processes that identify, assess, prioritize, and mitigate threats systematically. Key requirements include:
- Cybersecurity risk management process integrated with enterprise risk frameworks
- Regulatory compliance tracking for PCI-DSS, EMV standards, and SWIFT CSCF
- Continuous risk monitoring with documented risk registers
- International standards adherence (NIST, ISO 27001, Basel Committee)
Business Impact: Converts cybersecurity from a cost center to a strategic advantage. SAMA laws and regulations compliance becomes an automated, audit-ready reality rather than an annual scramble. Risk officers gain executive visibility into threats affecting financial stability.
Cyber Security Operations & Technology
Where Technical Controls Meet Business Reality. Domain 3 delivers 17+ operational controls protecting information assets across the technology stack:
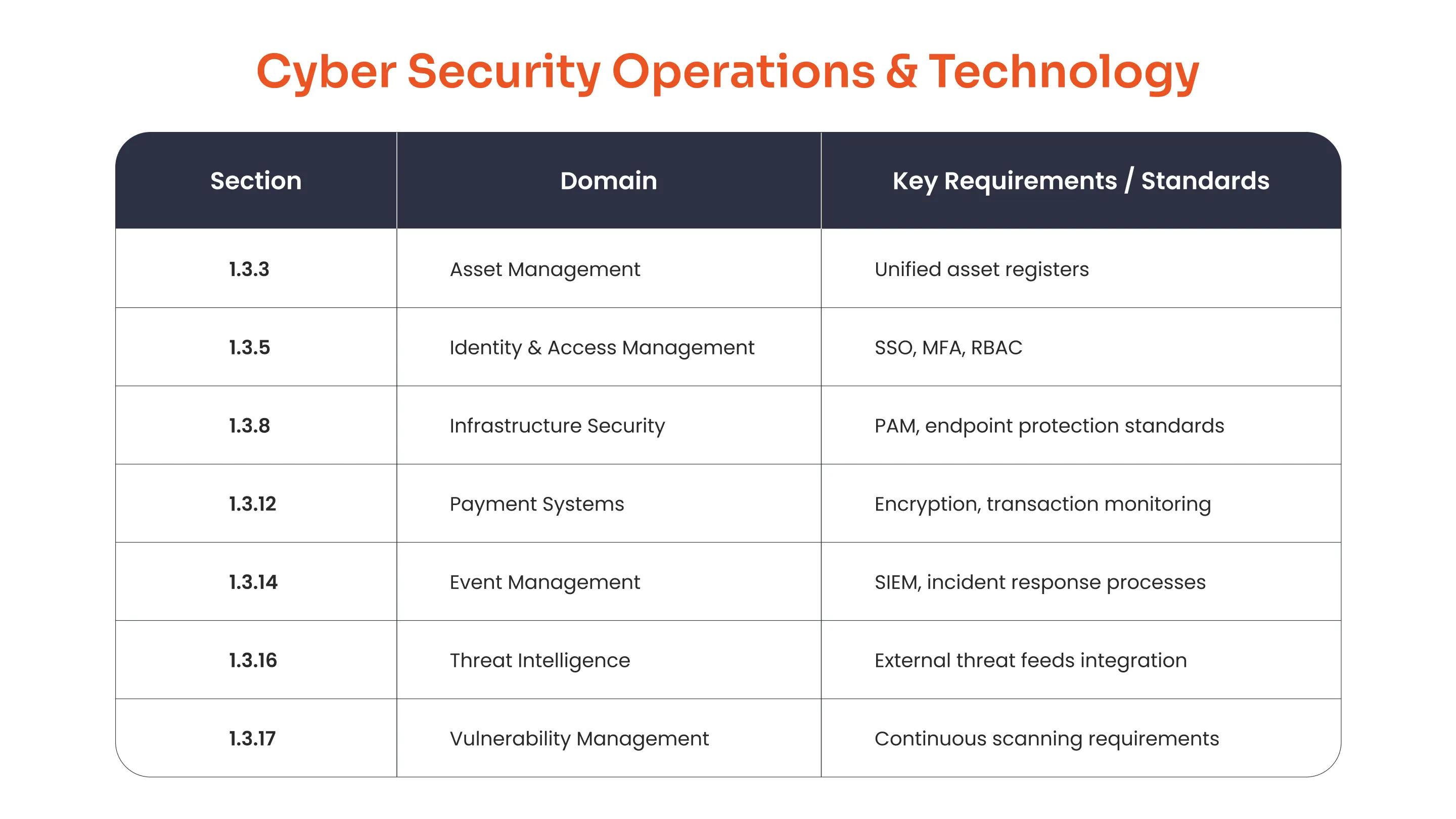
Reality Check: Banks require 100% Domain 3 compliance. Fintechs prioritize 1.3.5 IAM with 1.3.12 Payments. SAMA compliance in cybersecurity demands production-grade controls, not theoretical policies. This domain represents the technical foundation proving organizational maturity to SAMA auditors.
Third-Party Cyber Security
Your Weakest Vendor is Your Biggest Risk. Domain 4 extends SAMA compliance boundaries beyond corporate walls, mandating:
- Vendor contract cybersecurity clauses with audit rights
- Third-party risk assessments before engagement
- Outsourcing policy with security exit criteria
- IAM enforcement on partner access (Control 1.3.5 extension)
The Challenge: 70%+ of Saudi financial breaches trace to third-party compromise. SAMA compliance in Saudi Arabia holds you accountable for vendor security failures. Organizations must demonstrate equivalent security controls that extend to all external relationships.
Critical SAMA Compliance Controls
While the four domains provide the strategic framework, SAMA compliance Saudi Arabia certification depends entirely on implementing and documenting specific technical controls that SAMA auditors verify during mandatory annual self-assessments.
The Priority SAMA Compliance Controls Reference Table
| Control Code | Requirement Summary | Auditor Evidence Requirements | Banks | Fintechs | Insurance |
|---|---|---|---|---|---|
| 1.3.3 Asset Management | Define, approve, implement asset management process supporting unified, up-to-date asset register | Complete asset inventory, update procedures documentation, and asset classification policy | Required | Required | Risk-based |
| 1.3.5 Identity & Access Management | Restrict access to information assets based on business requirements and need-to-know principles | Access control policy, 90-day user entitlement reviews, privileged account logs, and failed login analysis | MANDATORY | MANDATORY | Required |
| 1.3.6 Application Security | Define, approve, implement cybersecurity standards for application systems with periodic effectiveness evaluation | Secure coding standards document, quarterly vulnerability scan reports, and application security testing results | Required | Required | Risk-based |
| 1.3.8 Infrastructure Security | Define, approve, implement cybersecurity standards for infrastructure components | Server hardening checklists, network segmentation diagrams, and firewall rule audits | MANDATORY | Required | Required |
| 1.3.12 Payment Systems | Define, approve, implement, monitor cybersecurity standard for payment systems ensuring confidentiality/integrity | TLS certificate validation, payment gateway security configs, transaction monitoring logs, and tokenization proof | MANDATORY | MANDATORY | N/A |
| 1.3.14 Cyber Security Event Management | Define, approve, implement security event management process analyzing operational/security logging | SIEM configuration reports, incident response timelines, and log retention policy compliance | Required | Required | Required |
| 1.3.16 Threat Management | Define, approve, implement the threat intelligence management process | Threat intelligence feed subscriptions, quarterly threat reports, and intelligence integration evidence | Required | Risk-based | Risk-based |
| 1.3.17 Vulnerability Management | Define, approve, implement the vulnerability management process for identification/mitigation | Vulnerability scan schedules, patch management records, and remediation SLA compliance | MANDATORY | Required | Required |
Common Challenges in Achieving SAMA Compliance
Governance Buy-In & Executive Accountability
Boards treat cybersecurity as IT's problem rather than enterprise risk. Only 42% of Saudi banks have established board-endorsed governance structures required by SAMA. Budgets remain trapped in IT departments, CISOs lack executive reporting cadence, and project governance ignores security requirements. SAMA rejects self-assessments failing Control 1.1.1. This creates a critical roadblock for all organizations. No governance guarantees automatic SAMA rejection.
Technical Debt & Legacy Systems
65% of banks run unsupported mainframes that block modern IAM implementation for Control 1.3.5. Custom payment gateways lack the tokenization required by Control 1.3.12. Mixed OS environments defy hardening standards mandated by Control 1.3.8. Remediation delays span 6-18 months. This creates operational restrictions during modernization under SAMA scrutiny. Legacy systems ultimately dictate certification timelines.
Third-Party Risk Management Complexity
Banks average 200+ vendors, but 87% lack standardized security contract clauses. Organizations fail to deploy vendor security questionnaires. Offshore developers operate beyond SAMA jurisdiction. SaaS platforms provide no audit rights. 70% of breaches originate from third parties. SAMA holds primary institutions fully accountable regardless. Vendor failures directly cause your audit failure.
Resource & Skills Shortage
Saudi Arabia faces a 47% cybersecurity skills gap that cripples compliance execution. Compliance teams consist of 2-3 FTEs managing 47 controls simultaneously. Banks lack dedicated IAM engineers, SIEM experts, and third-party risk specialists. SAMA rejects 60% of self-assessments for incompleteness. Talent competition with Aramco and NEOM kills timelines, as local hiring also requires 6-9 months.
Evidence Collection & Monitoring Gaps
Manual access reviews consume 4 weeks every quarter. Excel-based asset inventories remain perpetually outdated. Organizations lack centralized logging, providing Event Management capability for Control 1.3.14. Maturity remains capped at Level 2 maximum. SAMA demands continuous measurement rather than one-time deployment. Manual processes limit compliance to the minimum.
Evolving Regulatory Requirements
SAMA updates its framework annually, with 2026 cloud and AI revisions pending. Static compliance policies become obsolete during mid-project execution. Organizations lack mechanisms for tracking SAMA circulars. Riyadh and Jeddah offices apply varying interpretations. This moving target frustrates roadmap execution. Mid-year control additions force planning cycle restarts.
How miniOrange Maps to SAMA Compliance Requirements
Saudi financial institutions struggle with the same SAMA controls year after year, particularly Control 3.3.5 Identity and Access Management, cited in 60%+ of audit findings. miniOrange delivers production-grade solutions specifically engineered for SAMA compliance across both Identity and Access Management (IAM) and Privileged Access Management (PAM). This section details exact control mappings with auditor-ready evidence generation.
A. Identity and Access Management Solutions
SAMA Control 3.3.5 mandates that access to information assets must be restricted based on "need-to-know" business requirements, with only approved users receiving sufficient privileges. miniOrange provides comprehensive IAM capabilities that directly satisfy this control and its sub-requirements.
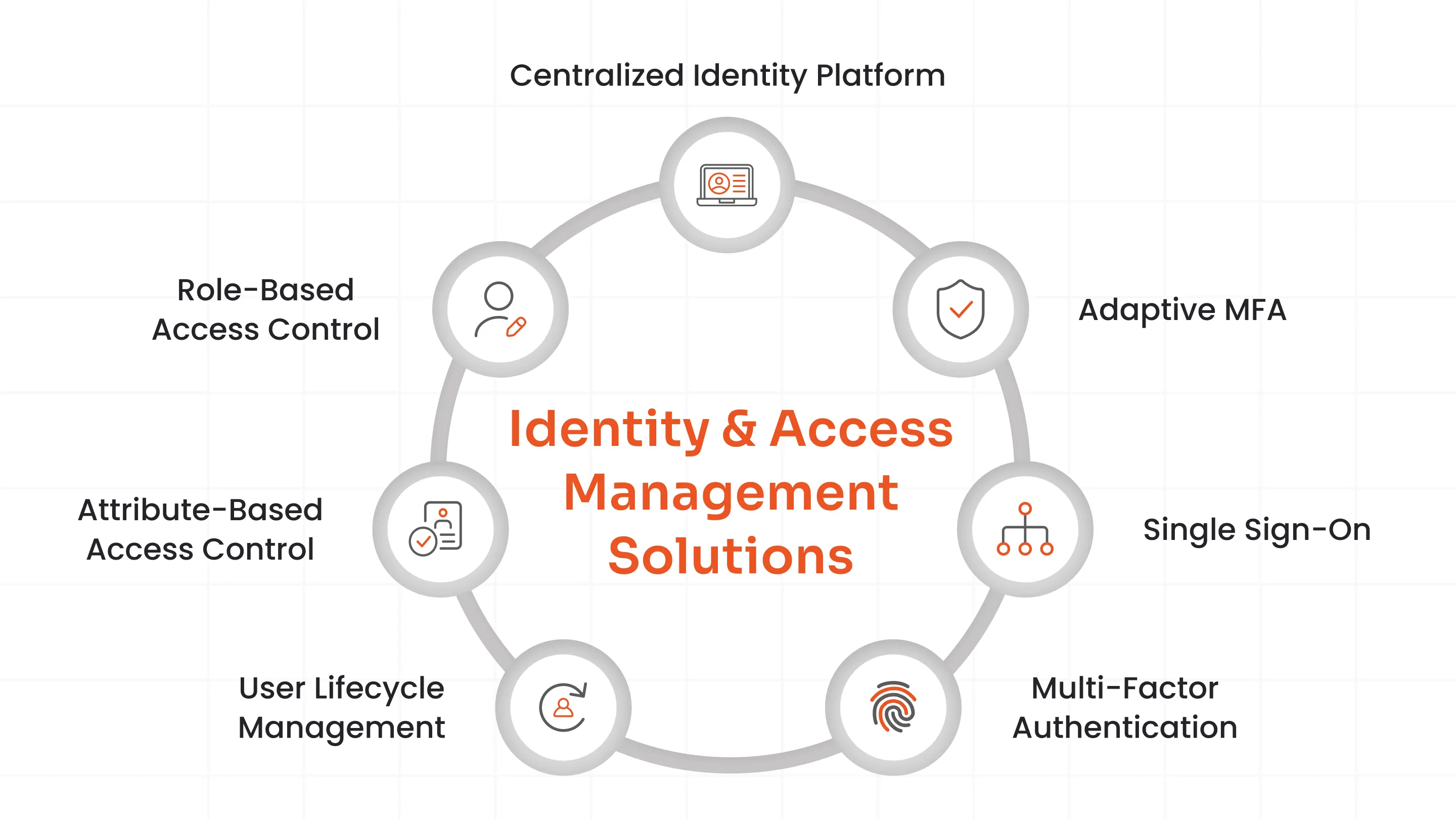
Centralized Identity Platform
miniOrange delivers a single platform managing identities and access across all enterprise applications, infrastructure components, and user populations, both internal employees and external third parties. This eliminates siloed access management systems that create compliance gaps. The centralized dashboard provides SAMA auditors with immediate visibility into access entitlements across the entire organization, satisfying the unified management requirement (SAMA 3.3.5-1).
Role-Based and Attribute-Based Access Control
The platform enforces both Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC) to map business roles and contextual attributes to permissions precisely. Least privilege enforcement occurs automatically at enterprise scale, ensuring employees only access systems necessary for their specific job functions. Quarterly access certification campaigns generate audit-ready reports proving ongoing compliance with SAMA's need-to-know principles (SAMA 3.3.5-4a).
Automated User Lifecycle Management
miniOrange integrates with HR systems, Active Directory, and other authoritative sources to automate user provisioning, modification, and de-provisioning. When employees join, change roles, or leave the organization, access rights update automatically according to predefined workflows. Third-party contractor access follows identical lifecycle controls, ensuring external users never retain access beyond contractual periods (SAMA 3.3.5-4 b1–b3).
Enterprise-Grade Multi-Factor Authentication
MFA deployment proves comprehensive across all sensitive systems:
- Core banking applications: Hardware tokens, FIDO2, and biometrics
- Payment gateways: SMS OTP fallback with adaptive authentication
- Administrative consoles: Mandatory push notification approval
- Remote access channels: VPN, RDP, SSH, and Citrix with continuous re-authentication
miniOrange supports 15+ authentication methods, ensuring 100% MFA coverage required by SAMA for critical and remote systems (SAMA 3.3.5-4e, 4f1a).
Federated Single Sign-On
Support for SAML 2.0, OAuth 2.0, OpenID Connect, and SCIM enables seamless federation across cloud, on-premises, and partner applications. Centralized policy enforcement ensures consistent authentication and authorization regardless of application location or ownership, simplifying SAMA compliance across hybrid environments.
B. Privileged Access Management Solutions
SAMA explicitly mandates strict controls over privileged and remote accounts, requiring individual accountability, password rotation, and session monitoring. miniOrange PAM solutions deliver complete coverage.
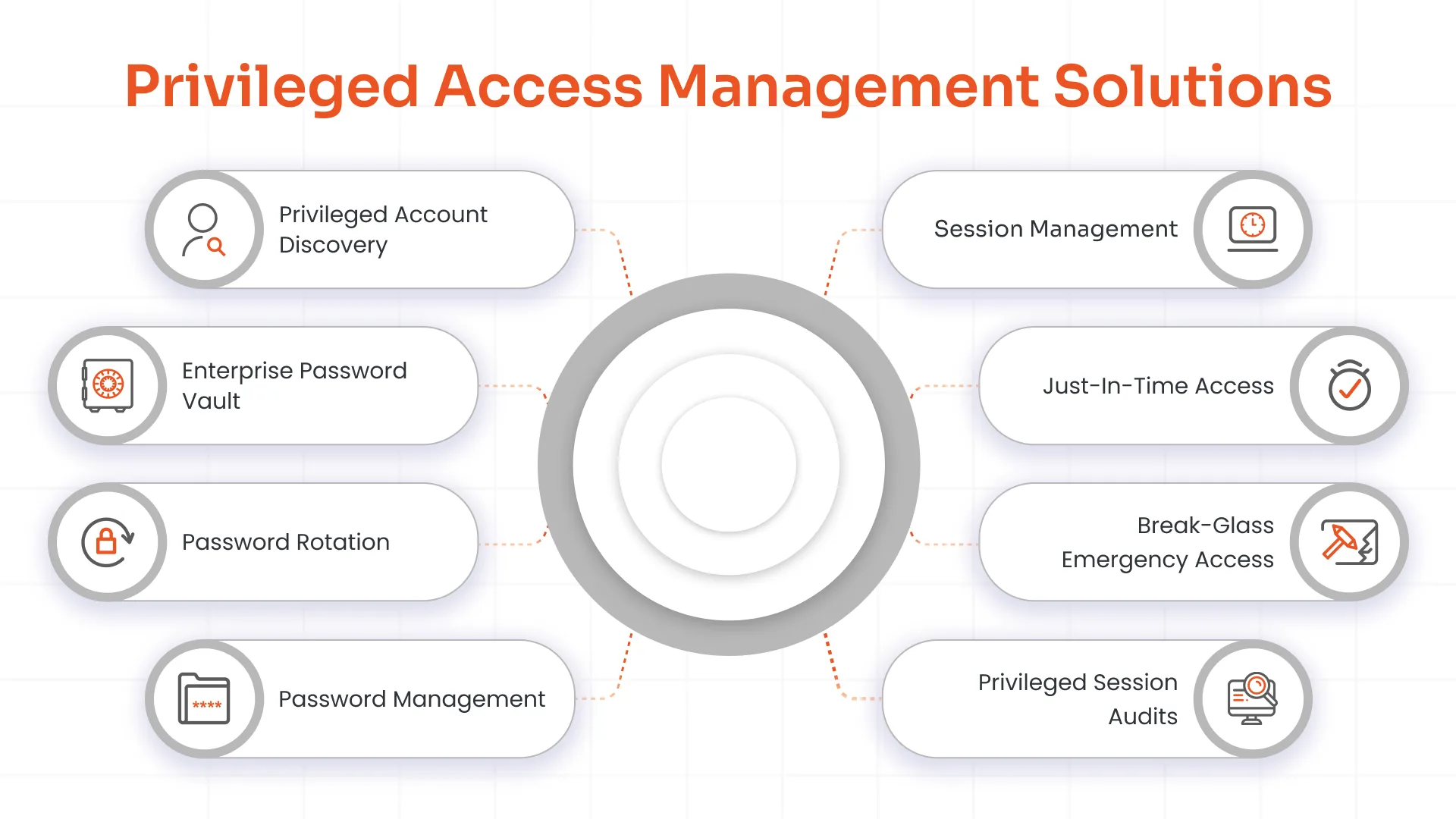
Automated Privileged Account Discovery
The platform automatically discovers all privileged accounts through the Privileged Account Discovery feature, such as local administrator, domain admin, service accounts, database owners, network device credentials across Windows, Linux, Unix, databases (Oracle, SQL Server, MySQL), and cloud infrastructure (AWS IAM roles, Azure AD). No manual inventory required, eliminating the common audit gap where organizations overlook service accounts (SAMA 3.3.5-4f1).
Secure Credential Vaulting
With the Enterprise Password Vault Solution, all discovered privileged credentials are stored in an encrypted vault. Administrators never know actual passwords, eliminating password sharing and insider threat risks. Checkout/check-in workflows ensure credentials remain protected while enabling legitimate administrative tasks (SAMA 3.3.5-4f4a).
Automated Password Rotation
Non-personal privileged account automates the password rotation, following configurable policies: Daily rotation: Service accounts, application accounts Post-session rotation: Elevated administrator accounts Pre-defined schedules: Database and network device credentials
Rotation events generate immutable audit logs proving compliance with SAMA password management requirements (SAMA 3.3.5-4f4c).
Comprehensive Session Management
All privileged sessions proxy through miniOrange with:
- Keystroke/video recording for forensic analysis
- Real-time session monitoring with termination capabilities
- Complete command logging with contextual metadata
- RDP/SSH/VNC gateway eliminating direct server access
The session management through miniOrange PAM enables SAMA auditors with direct evidence of privileged activity, who performed actions, and compliance with operational policies (SAMA 3.3.5-4f1–f3).
Just-In-Time Privilege Elevation
Standing administrator privileges become obsolete. With just-in-time access, users request temporary elevated access for specific systems with a defined duration and scope. Approval workflows, risk-based MFA, and automatic de-elevation ensure privileges exist only when business justified, satisfying SAMA's least privilege mandate.
Individual Accountability Enforcement
Every privileged action traces to a specific individual identity, not shared accounts. Integration with enterprise directories ensures actions link to verifiable user identities. Audit logs contain complete accountability chains proving which human performed which actions on which systems at which times.
Break-Glass Emergency Access
Controlled break glass account scenarios support multi-approver MFA workflows, comprehensive session recording, and mandatory post-incident reviews. All break-glass usage generates immediate executive notifications and detailed forensic evidence for SAMA incident reporting requirements.
Audit-Ready Evidence Generation
miniOrange automatically generates SAMA self-assessment deliverables:
- Access certification reports proving Control 3.3.5 effectiveness
- Privileged session logs with complete accountability chains
- Password rotation audit trails spanning the credential lifecycle
- MFA enforcement statistics across all covered systems
- User lifecycle management reports demonstrating provisioning/de-provisioning
Centralized dashboards provide real-time compliance status across all 3.3.5 sub-controls, eliminating months of manual evidence collection common with legacy approaches.
Roadmap to Achieve SAMA Compliance: Your 6-Step Certification Journey
This roadmap addresses the documented challenges from governance gaps, legacy systems, and resource constraints, while providing clear milestones for self-assessment submission.
Step 1: Framework Comprehension and Gap Analysis
Begin by understanding SAMA laws and regulations, and objectives for managing cybersecurity risks within your specific organizational context. Review all four domains - Governance, Risk Management, Operations, and Third-Party Security, identifying which controls apply based on your institution type. Banks face mandatory compliance across all 47 controls. Fintechs prioritize Control 3.3.5 IAM and 3.3.12 Payment Systems. Insurance companies focus on Governance and Risk Management domains.
Conduct initial gap analysis comparing current security posture against SAMA requirements. Document existing controls, identify missing capabilities, and estimate remediation effort. This assessment informs executive presentations, securing the necessary budget and board endorsement. Engage external SAMA compliance consulting if internal expertise lacks depth; early expert guidance prevents costly mid-project course corrections.
Step 2: Scope Definition and CISO Accountability
The Chief Information Security Officer must formally determine compliance requirements and document all compulsory controls with explicit scope boundaries and justified exclusions. Create the compliance project charter, defining:
In-scope systems: Core banking platforms, payment gateways, customer databases, and administrative infrastructure. Out-of-scope systems: Justified exclusions with risk acceptance documentation signed by executive leadership. Control applicability matrix: Mapping all 47 SAMA controls to organizational assets with implementation priority rankings. Resource allocation: Dedicated FTEs, external consultants, and technology budgets spanning a 12-18 month implementation timeline.
Step 3: Governance Foundation Establishment
Domain 1 implementation begins immediately because governance provides the authorization structure enabling all subsequent technical deployments. Without board endorsement, cybersecurity remains an IT project lacking enterprise commitment.
Define the cybersecurity governance structure endorsed by the board. Create a cybersecurity committee with independent senior leadership reporting directly to the board. Establish meeting cadence (minimum quarterly) with documented minutes proving active oversight. Define escalation paths, ensuring cyber incidents reach board awareness within prescribed timelines.
Establish a comprehensive cybersecurity strategy aligned with Vision 2030 business objectives and organizational risk tolerance. Strategy documents must address a three-year cybersecurity maturity roadmap, budget projections, technology modernization plans, and integration with enterprise risk management frameworks.
Document and communicate enterprise-wide cybersecurity policy. Policy must mandate employee compliance, define acceptable use standards, establish consequences for violations, and integrate cybersecurity responsibilities into employment agreements. Conduct an organization-wide policy acknowledgment campaign with signed attestations providing audit evidence.
Define roles and responsibilities following SAMA internal audit principles. Create RACI matrix clarifying who owns each control, who implements technical requirements, who provides consultation, and who receives status information. Governance without accountability fails immediately.
Step 4: Operational Control Implementation
Domain 3 technical controls represent the compliance heavy lifting, consuming 60-70% of total project effort. This is where miniOrange solutions directly accelerate SAMA compliance.
Phase 4A: Identity and Access Management (Control 3.3.5)
Deploy the miniOrange IAM platform, implementing need-to-know access principles across all enterprise applications. Configure Role-Based Access Control, mapping business roles to system permissions. Integrate with HR systems, enabling automated provisioning and de-provisioning. Deploy Multi-Factor Authentication across core banking, payment systems, administrative consoles, and remote access channels. Establish quarterly access certification campaigns, generating audit-ready compliance reports. Control 3.3.5 represents the highest audit priority.
Phase 4B: Privileged Access Management (Control 3.3.5 sub-requirements)
Deploy miniOrange PAM, discovering all privileged accounts across the infrastructure. Configure secure credential vaulting, eliminating password sharing. Implement automated password rotation for service accounts and elevated credentials. Enable comprehensive session recording for all privileged activities. Establish Just-In-Time access, replacing standing administrator privileges. PAM deployment proves individual accountability required by SAMA auditors.
Phase 4C: Infrastructure and Payment Security (Controls 3.3.8, 3.3.12)
Implement infrastructure hardening standards based on CIS Benchmarks. Deploy network segmentation, preventing lateral movement. Configure database access controls beyond the application layer. For payment systems, validate end-to-end encryption, deploy transaction monitoring, implement tokenization for cardholder data, and prove PCI DSS alignment. Payment system failures trigger immediate SAMA intervention—prioritize accordingly.
Phase 4D: Event Management and Vulnerability Tracking
Deploy centralized logging and SIEM capabilities, capturing security events across all systems. Establish incident response procedures with defined escalation paths. Implement continuous vulnerability scanning with defined remediation SLAs. Integrate vulnerability assessment tools providing systematic identification and mitigation processes.
Step 5: Self-Assessment Preparation and SAMA Audit
SAMA requires annual self-assessments gauging cybersecurity maturity across all implemented controls. Organizations submit detailed documentation proving control effectiveness, not just deployment.
Conduct a comprehensive internal self-assessment following SAMA internal audit principles. Evaluate each control against maturity levels (Initial, Repeatable, Defined, Managed, Optimized). Target Maturity Level 3 (Defined) minimum with documented processes. Collect evidence proving effectiveness: access review reports, privileged session logs, password rotation audit trails, MFA statistics, vulnerability scan results, and incident response timelines.
Generate a self-assessment report documenting current maturity, identified gaps, and remediation plans with timelines. miniOrange automatically produces required IAM and PAM evidence, eliminating months of manual log analysis common with legacy systems. Submit report to SAMA within prescribed timelines (typically 90 days following fiscal year end).
SAMA auditors validate self-assessments through evidence review, technical interviews, and potential on-site inspections. Auditors verify control implementation authenticity, test technical capabilities, and assess organizational culture. Auditor findings require formal responses with corrective action plans for identified deficiencies.
Step 6: Continuous Compliance and Improvement
SAMA compliance represents an ongoing commitment, not a one-time certification. Organizations must maintain compliance through consistent monitoring, regular updates, and cultural embedding.
Establish continuous monitoring using miniOrange real-time dashboards tracking IAM effectiveness, privileged access usage, MFA adoption, and access certification status. Configure automated alerts for policy violations requiring immediate investigation. Continuous evidence collection eliminates annual audit scrambles.
Conduct regular framework reviews as SAMA updates requirements annually. Subscribe to SAMA circulars tracking regulatory changes. Adjust policies and technical controls, maintaining alignment with evolving standards. 2026 cloud and AI revisions require proactive roadmap adjustments.
Implement comprehensive employee awareness training covering cybersecurity policies, social engineering threats, incident reporting procedures, and individual responsibilities. Track training completion with documented attestations proving organization-wide awareness. Cybersecurity culture separates mature organizations from checkbox compliance.
Perform quarterly internal audits validating control effectiveness before SAMA reviews. Identify gaps early, enabling remediation without regulatory pressure. Leverage external SAMA compliance consulting for periodic independent assessments, providing objective maturity evaluation.
Summing It Up
SAMA compliance in Saudi Arabia represents mandatory cybersecurity maturity for financial institutions operating in Vision 2030's digital economy. This roadmap, from governance establishment through technical control deployment and continuous monitoring, transforms regulatory complexity into structured execution. With 68% first-time audit failures, organizations require proven solutions to accelerate certification while ensuring audit success and ongoing compliance.
Frequently Asked Questions
What is SAMA compliance in Saudi Arabia?
SAMA compliance refers to the Cyber Security Framework (CSF) mandated by the Saudi Arabian Monetary Authority for all financial institutions. It requires comprehensive cybersecurity controls across governance, risk management, operations, and third-party security. Banks need full compliance; fintechs follow risk-based controls.
How long does SAMA certification take?
Banks average 18 months; fintechs require 12-18 months. Strong governance accelerates to 9-12 months. Legacy systems extend timelines 6-18 months. miniOrange reduces evidence collection by 3-6 months through automated reporting.
How do SOPs ensure SAMA compliance?
Standard Operating Procedures document control implementation processes proving SAMA maturity Level 3+. SOPs detail access request workflows (3.3.5), incident response (3.3.14), vendor assessments (Domain 4), and evidence collection procedures required for self-assessments.
What happens with the SAMA audit failure?
68% first submissions require remediation. SAMA issues corrective action plans (90-180 days). Repeated failures trigger financial penalties, operational restrictions, and license suspension. External consultants recommended for remediation.
Does ZATCA relate to SAMA compliance?
ZATCA (Zakat, Tax and Customs Authority) governs e-invoicing and tax compliance for Saudi businesses. SAMA regulates financial institutions specifically. Both require strong IAM, but ZATCA focuses on fiscal compliance while SAMA emphasizes cybersecurity framework adherence.



Leave a Comment