Ever been cruising through a highly productive day, being unstoppable, and suddenly, bam! You’re stuck in an unexpected traffic jam! Your flow screeches to a halt, and the frustration creeps in; your next-to-perfect day goes down in shambles!
DDoS does something similar, but at an IT infrastructure level. Result? Downtime, loss of efficiency, and a sudden decrease in productivity. This leaves IT organizations in chaos, disrupting the entire system.
So, we bring to you the crux of DDoS and how to prevent it completely using miniOrange solutions. We will also talk about the types of DDoS and the functioning of a DDoS attack.
What are DDoS Attacks?
DDoS stands for Distributed Denial-of-Service (DDoS), a type of malicious cybersecurity threat that clogs the target server or network by flooding it with unwanted traffic.
DDoS attacks lead to compromised systems, preventing users from reaching their destination (accounts or digital resources).
Were you aware that denying the denial had led to three days of massive attacks?
In February 2020, AWS experienced one of the largest DDoS attacks, which targeted an unidentified AWS client. A Connectionless Lightweight Directory Access Protocol (CLDAP) reflection was used, which depended on compromised third-party CLDAP servers to maximize the data sent to the victim’s IP address by 56 to 70 times.
DDoS attacks can come from anywhere in the world, and one of the worst facts is that they’re hard to track. So, implementing impactful cyberattack prevention plans, such as miniOrange MFA products, firewalls, or securing Internet of Things (IoT) devices, can go a long way.
Note: Get a free 30-day miniOrange IAM trial today!
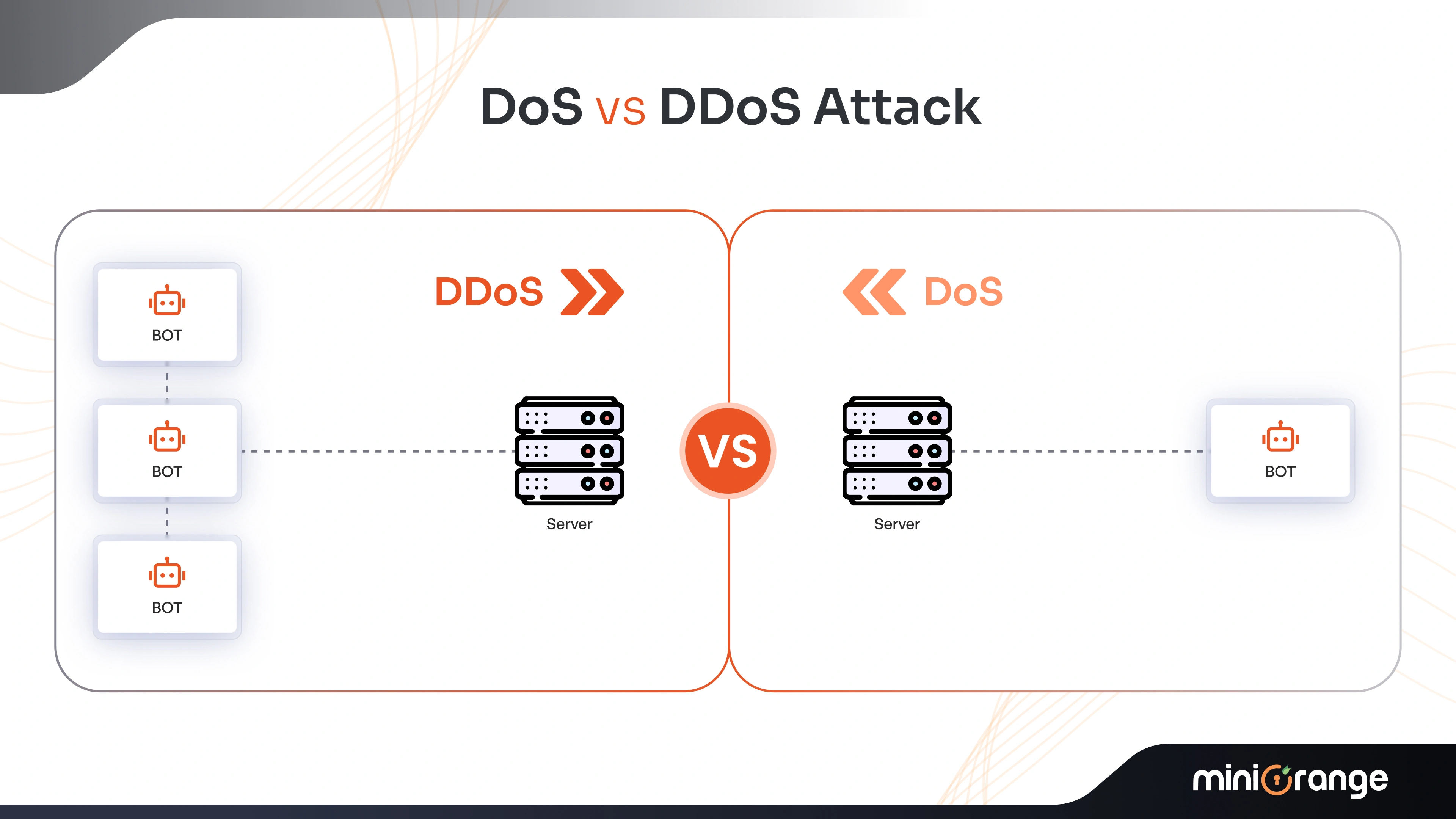
DoS vs. DDoS Attack
Cyberattacks are distinguished according to the type of systems and networks.
There are mainly two attack categories: Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS).
Both DDoS and DoS cyberattacks flood the systems with unwanted traffic, making them inaccessible to users and slowing down the system's performance.
We’ve already discussed DDoS, but what is a Denial-of-Service attack?
So, Denial-of-Service (DoS) attacks are like digital traffic jams, where a hacker floods a server with lots of fake traffic. This prevents users from getting through to their accounts and resources.
Here, the goal isn’t to steal something but to disrupt the system, so they become unavailable for legal users.
How Does a DDoS Attack Work?
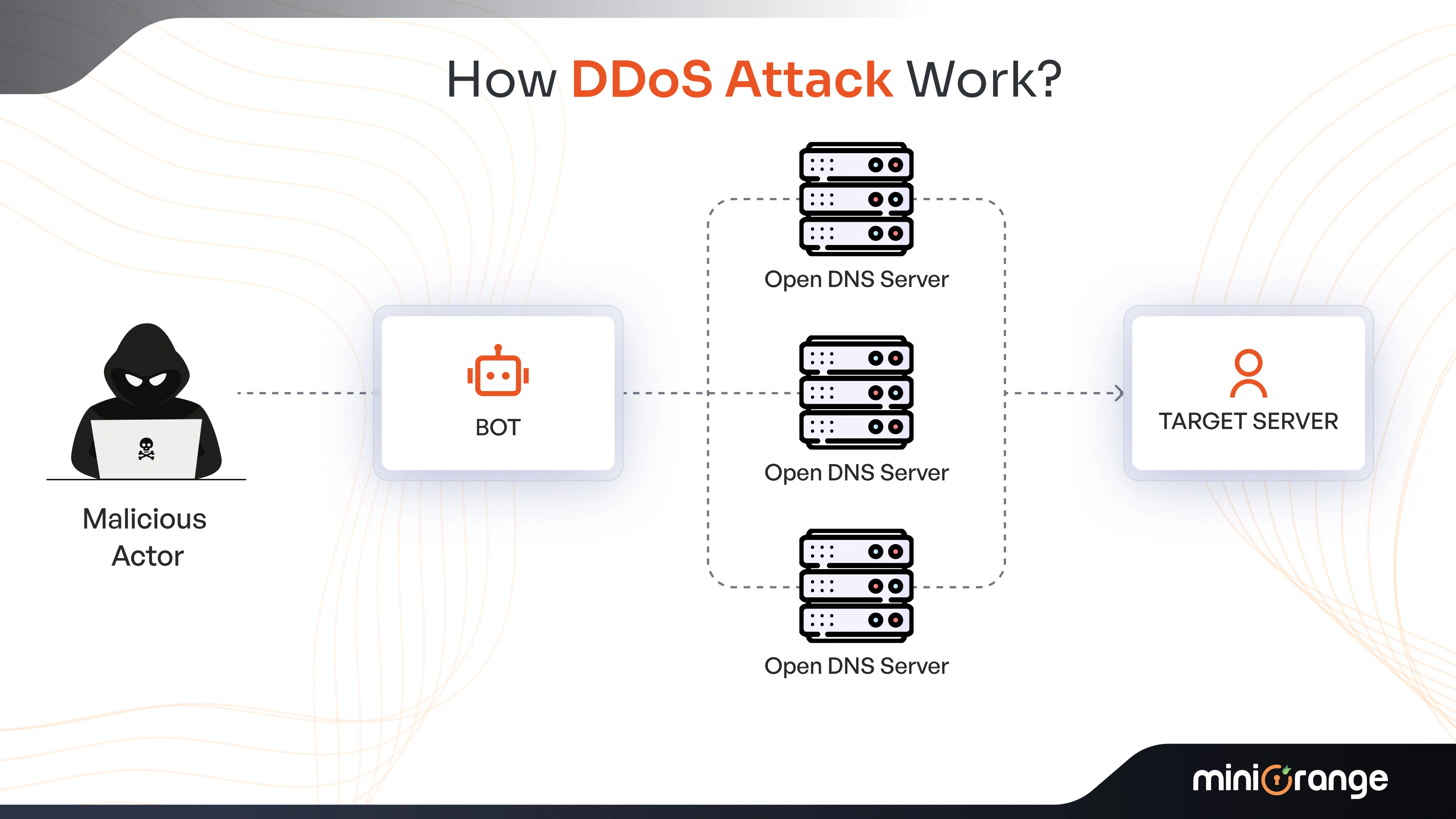
We know that Distributed Denial-of-Service (DDoS) attacks are capable of overwhelming the target network with unwanted traffic. This is conducted by networks of internet-linked devices or machines.
These networks include devices such as IoT and computers, which are infested with malware beforehand and controlled by hackers. The devices are called bots or zombies, and a collection of bots is called a botnet.
DDoS attacks are carried out with botnets. The hacker infects the system with a bot, instructing it to flood the network, servers, and devices with heavy traffic.
Impact of DDoS Attacks on IT Organizations
DDoS attacks in cybersecurity are perilous for IT organizations because they can cost millions of dollars for remediation, and they are inexpensive and simple to execute.
Here’s what DDoS costs an organization
- Loss of Productivity - When a server is degraded or taken down completely, employees won’t be able to work efficiently, resulting in a loss of productivity and time.
- Remediation Expenses - Rushing to recover IT servers after a DDoS attack leads to infrastructure expenses, outsourcing, and legal help if needed. This strains out the IT organization completely, leaving them drowning in debt (in case the expenses are too high to sum up).
- Customer Churn - When a client is denied entry to an account, it disturbs the user experience, forcing them to turn elsewhere for the services.
The impact of DDoS attacks can be either long or short, depending on the level of malware or virus attack. To avert a long-lasting impact, you may want to mitigate the risks before losing too much money.
What’s the Motivation Behind DDoS Attacks?
DDoS can bring an entire business to a halt! The reason for doing this could be
- Business Competition: Launching an attack on competitors to downgrade them.
- Cyber Warfare: This can be used to incur damage to an enemy state.
- Entertainment: Launched by psychopaths who are looking to wreak havoc on the servers or simply experimenting with their new malware.
- Extortion: Use DDoS to extort money from companies.
- Hacktivism: Attack on companies with whom there are disagreements on ideologies or philosophies.
There could be many other reasons for a traffic attack, but the ones stated above are the primary reasons for cyberattacks.
What are Some Common Types of DDoS Attacks?
DDoS attacks are largely classified into three major types: Application, protocol, and volumetric attacks.
These three categories encompass several other DDoS attack types, such as ICMP, UDP, TCP, IP, and HTTP flood attacks.
Let’s look at them in more detail.
1. Application Layer Attacks
An example will help us better understand application layer attacks. When a shopping cart is prepared for checkout, it can be misused by sending numerous requests to overload your computer or the application. This disrupts databases, making it impossible to buy the items.
These types of attacks prey on app vulnerabilities, causing it to fail. They also focus on ruining the Layer 7 software of the Open System Interconnection (OSI) model, which is the area where users interact with the applications.
Additionally, application layer attacks can overload the CPU system, disrupting it to the core.
Some of the types of application attacks are as follows:
- ReDoS - The Regular Expression Denial-of-Service (ReDoS) exploits vulnerabilities, causing systems to reach extreme situations and work slowly.
- HTTP Flood Attacks - These attacks abuse the HTTP commands and overwhelm the sites, along with the servers that host them.
HTTP attacks usually include GET, POST, low-and-slow POST, and many more.
2. Protocol Attacks
Protocol attacks target specific protocols to flood resources, firewalls, servers, and load balancers. These attacks are measured in packets per second. Specific protocols and their respective attack types are as follows:
- TCP Flood Attacks
The Transmission Control Protocol (TCP) flood attacks often infect the TCP via malformed packets or spoofing. Also, the SYN attack is another way to abuse the TCP protocol. - IP Null Attack
Here, an attacker sends huge volumes of IP packets with the ‘Protocol’ field in the IP header set to zero. This downgrades the server’s ability to correctly process and identify the traffic, leading to a system crash. - Ping of Death
Ping of death preys on how systems handle malformed or oversized IP packets, especially those using the Control Message Protocol (ICMP). The hackers send larger packets (more than 65,535 bytes), causing the system to crash and burn.
3. Volume-Based DDoS Attacks
Volumetric attacks overwhelm the system’s capacity with requests, traffic, and too much data. It includes UDP, ICMP, and CharGen flood attacks, along with misused applications.
Let’s look at them in more detail.
- UDP Flood Attacks - The User Datagram Protocol (UDP) sends lots of UDP packets to the targeted system, making it difficult for the system to respond to every packet, thus slowing down its performance.
- ICMP (Ping) Flood - So, this resembles a situation where hundreds of people are shouting your name concurrently, and you’re just trying to keep up with the talks. Here, the hacker sends tons of ping requests to a server. The server tries to respond with its processing and internet power. But the server feels overwhelmed, making it impossible to respond to the real requests.
- Misused Application Attack - The misused application attack, also known as the application consent attack or the illicit consent grant, takes place when hackers infect legitimate apps to gain unauthorized access to data or servers. So, instead of directly attacking the system, it uses the permissions granted to apps via compromised user accounts or by tricking the users into giving access.
Now that we know about the types of DDoS attacks, let’s move on to something that we would look for in case of adverse scenarios: ‘Ways to Prevent the Attacks.’
How to Prevent DDoS Attacks?
Organizations can get rid of DDoS attacks through a strong and superior DDoS mitigation strategy, which comprises high-grade cybersecurity solutions.
Let’s look at some of the mitigation strategies in detail.
1. Use a DDoS Protection Service
Distributed Denial-of-Service protection services are always on the lookout for unusual traffic or patterns that indicate an attack, which helps to prevent it instantly. Also, these services make use of smart filters to separate legal users from hackers, thereby screening out the traffic.
These services use authentication methods such as miniOrange Single Sign-On (SSO) to make sure that only verified users access accounts.
Moreover, DDoS protection services map and generate reports to understand what’s happening and how to best handle adverse situations.
2. Configure Rate Limiting and Firewalls
Let’s break down rate limiting and firewalls to understand them better.
- Rate Limiting
This limits the number of requests a server accepts in a certain period. It slows down web scrapers from stealing content and mitigates brute force attacks. However, rate limiting isn’t sufficient to manage complicated attacks. - Firewalls
Web Application Firewalls (WAFs) assist in preventing layer 7 DDoS attacks. Also, by adding a WAF between the server and the internet, it functions as a reverse proxy, safeguarding the server from vicious DDoS attacks.
3. Monitor Network Traffic
Monitoring network traffic is like keeping an eye on all the cars on a highway to spot jams or accidents.
Continuous and real-time monitoring detects threats at an early stage, allowing organizations to avert them immediately.
Ways to monitor network traffic are to deploy network monitoring tools, packet sniffers, and port mirroring.
4. Black Hole Routing
Imagine there’s a trapdoor in your network where you can send unwanted traffic without affecting the rest of your system.
Black hole routing is that trapdoor, which acts like a special path called the "black hole" or the "null route" that leads to nowhere.
Network traffic coming from suspicious sources is redirected to this black route or the null route. It is discarded silently, with no processing or response.
5. Risk Assessment
Organizations should conduct periodical risk assessments on their systems. This helps to avoid a DDoS attack, as there’s complete awareness about the organization's strengths and weaknesses.
Knowing the weakest spots of an organization is crucial to devising strategies to prevent cyberattacks and network disruptions.
Explore smarter access control with Context-Based Authentication
How to Tell if You’ve Been DDoS’ed?
An IT admin is likely to break into a sweat just at the thought of being DDoS'ed! Since these attacks remain undetected for a long time, it is quite difficult to mitigate them at the right time.
However, there are ways to know immediately if your server is under a DDoS attack.
Here’s a list of clues to look out for:
- A single IP address may receive too many requests.
- A 503 error is displayed on the screen.
- The Time-to-Live (TTL) event times out on a ping request.
- A gigantic increase in traffic is showcased in the logs.
Keep a lookout for these clues to safeguard your systems from vicious attacks.
How miniOrange Defends Against DDoS?
miniOrange, your trusted security partner, defends against DDoS attacks using proactive defense mechanisms such as
- Zero Trust Infrastructure
We verify every request beforehand, allowing users to access resources. Thus, avoiding malicious attacks and reducing a sudden boost in traffic. We implement MFA solutions such as OTP, push notifications, and more to build a Zero Trust Principle. - Implementation of Firewalls
DDoS is often combined with firewalls such as WAF to block suspicious attacks, adding a security layer. - Filtering Out Traffic
We carry out real-time and continuous monitoring to detect unusual activities in traffic, such as sudden spikes. This can be rerouted or blocked automatically.
Don’t miss out on securing your systems from cyberattacks! Contact us for a quote now! Here’s a detailed pricing list for your convenience.
Conclusion
So, what is DDoSing? In a nutshell, DDoS attacks are one of the slyest forms of cybercrime, as they cannot be detected under normal conditions. They need to be tracked meticulously through DDoS tracking tools.
Also, authentication security solutions such as Identity and Access Management (IAM) and Privileged Access Management (PAM) can be used to prevent DDoS attacks, as they only permit authorized users to log in and access resources/servers.
FAQs
What are the top three types of DDoS attacks?
The top three types of DDoS attacks are volumetric, protocol, and application layer attacks.
Is a DDoS attack illegal?
Yes! The DDoS attacks are considered illegal, and the accused entity is sued, fined, or imprisoned for malpractices.
What is the largest DDoS attack in cybersecurity history?
In November 2021, Microsoft mitigated a DDoS attack targeting an Azure customer with a throughput of 3.45 Tbps and a packet rate of 340 million PPS, believed to be the largest DDoS attack ever recorded.
Can DDoS attacks steal data?
No, DDoS is not made to rob user data; rather, it disrupts the systems by overwhelming them with suspicious traffic.
What’s an example of a DDoS attack?
In June 2025, pro-Russian hackers launched DDoS attacks on the Dutch municipalities ahead of the NATO Summit.
What is the most preferred way to protect from a DDoS or DoS attack?
One of the preferred ways for organizations is to outsource DDoS protection services.




Leave a Comment