Certain code is dangerous for your systems and those kinds of codes are categorized in malware attacks. Cybercrimes today are extremely organized, relentless and undeniably automated to their core. Globally, over 1 billion active malware programs are in distribution, which underscores the pressing challenge that it poses. These range from basic Trojans to advanced spyware and fileless attacks.
Speaking of the scale of malware threats, around 5.6M new malware threats are detected daily using cybersecurity systems. This calls for impervious authentication solutions such as miniOrange that stand the test of time for your organization’s security. This article aims to provide insight into malware attacks and their prevention and how miniOrange solutions can guide your systems into better security.
What is a Malware Attack?
Cybercriminals try to get dangerous software onto your computer, or your network, with hidden attacks. After it gets into your computer, this program may take your private details, watch what you do, or lock it, requesting money for access.
Malware is like a sneaky thief getting into your computer. It hides inside things you use, like files, messages, or downloads. It then operates secretly, causing problems before you notice.
Frequently, you’ll find these kinds:
- Malware moves between files, or jumps from one device to another
- Malware that holds your files hostage, requesting money for their return
- Software secretly tracks your activity, without your knowledge
- Deceptive programs disguise themselves as legitimate applications
These attacks frequently succeed because people use simple passwords, programs haven't been updated, or someone clicks a dangerous web address. Businesses can lose money, face lawsuits, and experience damage to how people see them if malware gets into their systems, even just one time.
Intent and Purpose of Malware
Harmful software exists to take advantage of computers, grab information, or cause problems. Bad actors build this to get into networks or devices without permission, then take charge.
The primary objectives are:
- Criminals will obtain credit card numbers and bank account information or will use ransomware to extort money from individuals.
- Anyone that steals important information, whether it be a business secret, a list of customers, or a new idea, does so to sell to others or spy on the organization.
- Malware could do serious damage to computer systems, degrade service or cause a complete work stoppage. This damages the organization's reputation and slows productivity.
- Spies working for governments frequently employ harmful software to collect information and observe what people do.
- People break into computer systems, creating secret openings to return later.
Bad software isn’t something that happens by chance; it’s a tool created to do specific things. Knowing what attackers want allows companies to build better protection, implementing security plans that stop problems before they start.
Explore the Top Cybersecurity Threats You Should Know
Malware 101
How Malware Spreads and Common Infection Sources
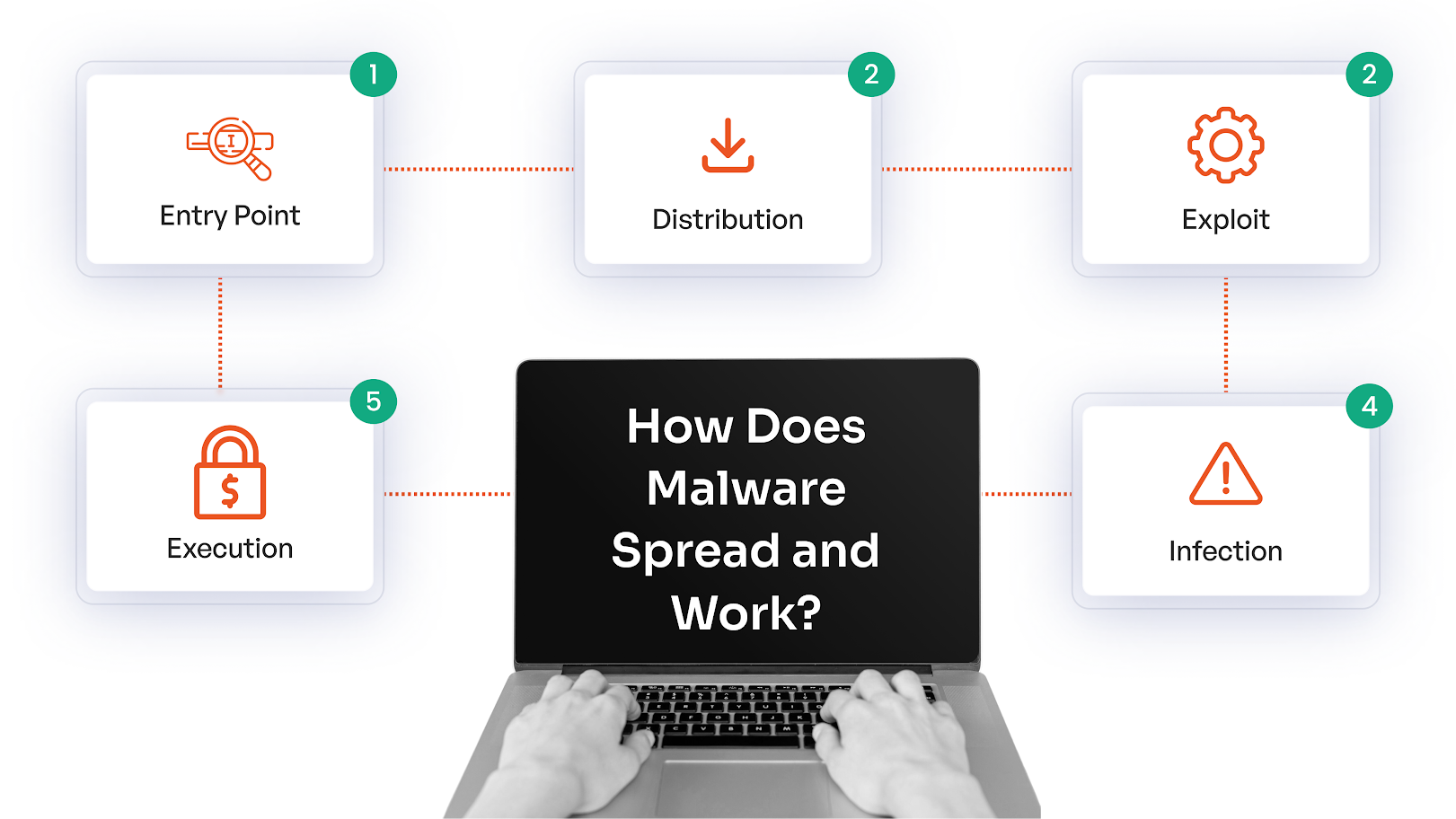
Malicious software is transferred through human errors, unpatched vulnerabilities, and systems that have not been patched for some time. People, with malevolent intent, create believable deception and send it through the common online places that your work group frequents.
- Some deceptive emails try to trick you into clicking links for phishing or infecting you with files. If a website has a vulnerability, it can place malicious software on your device simply by surfing on it without you noticing it. This can occur on unsafe websites or on sites that may impersonate something else.
- Malicious software can also be embedded in free software, cracked tools, software either sold or known to come from a source of which you are uninformed, or untrusted applications.
- A very easy way to share viruses is through USB thumb drives and external hard drives between computers.
- Hackers can access systems remotely by using easily guessed passwords used for remote connection or virtual private networking accounts. Once they are into the accounts, they can easily embed malicious software in the system.
- Vulnerabilities exist because older software types, including operating systems, web browsers, and software that have been long unpaid for or are slow to deliver patches, serve as a source of quick access for an attacker.
Malicious software is often shared via people who are lax on how to be secure or who are unaware of how to practice safe behavior online. Understanding security, keeping software updated, and applying different layers of protection to systems will significantly reduce the chance for a computer virus.
Signs Your Device is Infected with Malware
Harmful software usually hides, yet your device frequently gives clues something is wrong. Spotting these issues quickly lets you limit harm before they get worse.
- If your computer or phone starts running slowly, a virus might be using all the power.
- Often, your computer stops working or becomes stuck, indicating a potentially harmful issue.
- Strange boxes appearing on your screen, bothersome advertisements, false warnings, or unfamiliar browser features often signal a computer virus.
- High network activity could indicate a problem. Malware often sends unwanted data without your knowledge and could lead to an unexpectedly high data plan bill.
- If your phone drains the battery or feels hot, it could indicate your device has some hidden apps running.
- If you notice sudden changes, such as new apps showing up, settings changing, or files missing, it could indicate a problem with assigned program functions.
- If your antivirus turns off by itself, a virus is probably the cause.
If you notice any of these signs, the sooner you pay attention to it, the sooner you can take preventative measures to protect your device before someone takes control of it.
Devices Vulnerable to Malware
Harmful software like malware could infect devices connected to the internet. People with bad intentions find openings, old programs, or mistakes people make to break in. Computers and smartphones are often targeted, as they are used frequently.
- Computers, whether portable models or those used at desks, face risk because people frequently get files, explore online content, or select questionable connections.
- Phones and tablets keep your private info, bank apps, and emails safe. Harmful software frequently lurks inside phony applications or comes with risky file downloads.
- Servers represent important targets. If an adversary breaks in at just one server, this could reveal information on many people using the systems. This calls for the need for strong protection.
- IoT-based smart home gadgets, like cameras, routers, and fitness trackers, usually don’t have adequate protection. This lets computer criminals get in easily.
- Stores use sales or PoS systems; these systems get targeted often to gain credit card details.
Devices accessing the internet need current updates, virus safeguards, and secure settings to stay safe.
Impact of Malware and How Cyberattackers Exploit it
Malware is one of the most menacing tools in a hacker's toolkit because it can sit in common view and create total havoc. Once malware enters a network, it can:
- Steal sensitive data;
- Disrupt workflow;
- Spy on users; and,
- Give hackers backdoor access to otherwise secure systems.
API (application programming interface) for enterprise applications often leaves every infected device as a portal for a larger breach.
Attackers leverage malware by:
- Embedding it in phishing emails, through malicious links, or with software downloads;
- Exploiting unpatched vulnerabilities in enterprise applications (e.g., Oracle EBS);
- Bypassing weak authentication and using malware to escalate privilege; and,
- Deploying ransomware to lock down data to compel ransom payments.
The costs are staggering: the average cost of a malware attack is in the millions of dollars and includes recovery, downtime, and reputational harm. In the world of advanced persistent threats (APTs), malware can not be ignored.
Know how to Prevent Cybersecurity Threats with MFA Solutions
Types of Malware

There are various types of malware; each presents its own challenges and issues with regard to the systems and data within. What follows are common types, defined in a general sense.
1. Viruses: Viruses are types of malicious code that can attach themselves to other files or programs. Then, if and when the designated file or program is run, any infected file will spread to other files or systems. Many viruses are designed to delete entire systems or files and/or slow down the performance of the device.
2. Worms: Worms are self-replicating programs that jump from system to system through a network without human involvement. Worms replicate themselves very quickly, using bandwidth and degrading the performance and stability of the system.
3. Trojans: Trojan malware is a type of malicious application that looks like a trustworthy application, but actually creates back doors into the network or steals data.
4. Spyware: This software will monitor the user behind the scenes. It can record user behaviors or collect user secure information for an attacker to report back.
5. Adware: Adware is intrusive advertising software that places advertising in front of a user and slows down performance of the device. In addition, adware also has versions that will report back without the user knowing.
6. Ransomware: Files are locked or encrypted, and after the user has access to the files back, the attacker asks for funds to return the user's ability to access the file, and whether the file is actually released is up to the attacker. Ransomware continues to be one of the most damaging cyber threats against businesses these days.
7. Rootkit: Rootkits run deep into the operating system, and they allow an attacker to hide the activity of malicious codes from regular security tools.
8. Keylogger: A keylogger is a program that records every key the user typed on his keyboard. A hacker may use keyloggers to gain access to a user's login, a user's message, or even access to secure financial information.
9. Bot/botnets: These are devices that were compromised and now serve as a "zombie" device. Bots act on their own or coalesce with other bots in a large-scale attack. An attacker may target individual devices or simply attack all of the observed bots in a DDoS attack.
Notable Malware Examples
Certain highly destructive, damaging cyberattacks from the past can be attributed to malware deploying monetary and operational damages. The ILOVEYOU virus was sent out in the year 2000 as an email attachment and infected millions of computers, creating headaches for various types of businesses around the globe within days of being introduced as a computer virus.
By the same token, the WannaCry Ransomware event in 2017 infected hospitals, banks, and government systems, holding your information for ransom in Bitcoin, traded or otherwise, and caused havoc in 150 countries. Not long after that, at the same time frame, was the second malware example, NotPetya, which created damages in the billions as part of the logistics, global shipping, and pharmaceuticals. It becomes even more sophisticated when you consider Stuxnet, which was first discovered in 2010, to authorize a physical attack on critical infrastructure, specifically targeting Iranian nuclear sites.
Last but not least, Emotet was identified as one of the most damaging botnets, ultimately spreading banking Trojans throughout enterprises until law enforcement agencies around the world came together to dismantle Emotet in early 2021. These examples highlight that malware is a consumable and scalable type of cyberattack and that technologically based advanced threats are not exclusive to the enterprise level, nor is there a business or sector not at risk of being attacked.
Discover Man-in-the-Middle (MITM) Attack in Cybersecurity
Protecting Against Malware
Malware remains one of the largest vulnerabilities facing companies of all sizes. Malware can either target sensitive information, affect productivity, or consume your human and financial resources. Protecting against malware necessitates a holistic approach that is rooted in detection, prevention and advanced protection. If it were to be identified on your systems, there are advanced protection strategies available.
Detecting, Responding to, and Removing Malware
Malware can become established quickly and the longer it takes to detect and respond, the greater the damage you are likely to incur. Take a proactive stance as decreasing costs and downtime.
Effective ways to detect and remove malware are:
- Use endpoint detection and response (EDR) tools to detect signs of abnormal behavior in real time.
- Engage in regular vulnerability tests to detect vulnerabilities before attackers take advantage of them.
- Isolate infected systems and stop the lateral movement of the malware across your system.
- Use updated antivirus and/or threat removal tools for fast remediation.
- Recover affected systems with clean, verified, and fully operational backups, which also guarantees that affected systems may be restored to function without retaining remnants of the infection.
The goal of detection and responding swiftly after detecting the event and after synthetic detection of an infection is important to limiting reputational and financial harm.
Preventing Malware Attacks
When it comes to malware, prevention is your best defense. Malware attacks are most successful due to outdated software, poor user awareness, and weak controls.
Core prevention measures include the following:
- Patching software regularly to patch vulnerabilities as soon as each software is available.
- Regular employee training to identify phishing, suspicious links, and unsafe downloads.
- Securing the environment with the help of MFA authentication, which will provide more control around your system's access even if passwords are stolen.
- Having a least-privilege access policy will drop the chances of an exploit, making sure that employees only have access to what they need to do their jobs.
- Filter email and internet content regularly to stop malicious attachments and sites before your users can access them.
With solid prevention measures in place, you will also reduce recovery time and the money your organization will need to spend recovering.
Protecting Your Network from Malware
While prevention measures in place may deter an attack, attackers are constantly testing your network for exploitable weaknesses. A layered network defense will deter malware from spreading.
Best practices to protect the network include:
- Segmentation of the network to isolate a zone for any of the most sensitive data if a breach occurs (the aim is to get the breach contained as much as possible).
- Firewalls and intrusion detection systems that monitor and flag suspicious traffic.
- Secure remote or VPN access for your employees to protect data while working from home or with other 3rd-party connections.
- Zero trust principles regularly verify who the user is and the trustworthiness of the device being utilized.
- Continuously monitor and assess network traffic (burgeoning and renowned increasingly) for anomalies before they blossom into an incident.
Securing the network as the first line of defense from cybersecurity breaches and exploitations will make it harder for malware to move freely and lessen the chance to exploit any sensitive assets.
Benefits of Advanced Malware Protection
Traditional antivirus alone will not be enough to protect against today’s breaches and advanced persistent threats. Advanced protection incorporates automation, artificial intelligence, and analytics for thorough and efficient protection.
Benefits of advanced protection include:
- Automated detection and remediation of threats, so zero-day attacks can be mitigated while they are in progress.
- Behavior-based analysis because advanced protection will allow analysts a cure for the detection of newly detected malware strains before they belong to definitions.
- Reduction of time your business is exposed to the revenue and reputational impact of a cybersecurity breach.
- Regulatory compliance monitoring and reporting that advanced protection affords.
- Increases trust of stakeholders and a business’s reputation, as they will see security as a component of a business’s reputation as something that is valued.
- Deploying advanced solutions will build in a safety net for advanced security while they continue to expand toward tomorrow and long-term resilience.
Combatting malware is a process, not just a moment, and not just monitoring at a specific point in time. The ideal place to discover is at the inception, to prevent with the best security, and to protect data at rest or in motion both in your network and in the cloud. Together, all of this amounts to trust, data protection, and business continuity in a world where threats are getting aggressive and sophisticated using AI.
Getting Started with Top-Notch Security Against Malware
At the end of the day, while it is often about malware protection, your environment is only one obsolescence away from total compromise to identity and access management. Preventing malware from taking an action before it does any damage is essential and identity and access management software is the way to go. Single sign-on and multi-factor authentication provide safeguards against malware in your unguarded territory. Whether it is your app, web app, switches and routers, or VPN and RDP, we got you covered with anything and everything under one single roof. Challenge the cyberattackers with superior protection every single day.
Let us protect your systems with custom security solutions. Get in touch with miniOrange to start. Connect with a miniOrange security advisor to generate a customized security program for your organization.
FAQs
How are people targeted by malware?
Malware usually finds its way to a target via phishing emails, malign advertisements, compromised sites, malign downloads, or infected USB drives; tricking a victim into clicking on links, download files or otherwise disclosing credentials.
What is the most common malware attack?
The malware attack that has fallen back on is a computer virus. It usually happens when a user opens a malign attachment or has downloaded malware; the virus replicates itself and spreads to other files and systems.
How to get rid of malware?
The best way to delete malware is to disconnect from the internet, go into safe mode, delete suspicious files and browser extensions, and run a reputable antivirus/malware removal to scan, contain, and delete identified threats.



Leave a Comment