What is IDaaS?
Identity-as-a-Service (IDaaS) is an Identity and Access Management (IAM) solution for cloud apps or in other words, a Cloud Identity Provider (IDP) that provides a secure and scalable way for growing organizations to manage their employees, stakeholders, and customers’ identities and provisioning to various applications and resources.
“As a Service” typically means that a third-party provider is rendering a specific service for businesses. For example, you might be aware of “software as a service” which means that a third-party provider is rendering service via their software similarly, IDaaS means that a third-party IDP (Identity Provider) or IAM (Identity and Access Management) delivers Identity Management and User Provisioning services.
IDaaS solutions offer a range of services such as Single Sign-On (SSO), Multi-Factor Authentication (MFA), User Provisioning/De-Provisioning, and User Lifecycle Management. With IDaaS, your employees, stakeholders, and customers can securely access various applications and resources of your businesses or products. It also enables access management to sensitive data and applications to enhance security and ensure compliance with various regulations and policies.
When did IDaaS Emerge?
IDaaS (Identity-as-a-Service) emerged as a concept and solution in the field of identity and access management (IAM) in the late 2000s. The exact date of its emergence can be attributed to around 2008-2009 when the term “IDaaS” began to gain popularity and solutions started to emerge in the market.
During this time, organizations were increasingly moving their IT infrastructure and services to the cloud, and there was a growing need for cloud identity management solutions where an IDaaS provider manages & delivers complete IAM services for cloud apps. Slowly, IDaaS in cloud computing became popular, and now it is used by most modern businesses.
How Does IDaaS Work?
IDaaS typically includes several core components, including a user directory, authentication, provisioning services, Identity Governance (IGA), and administration tools. The user directory is a central repository that stores information about users who could be your organization’s employees, stakeholders, and customers. The information which is stored can be the usernames, passwords, and access permissions.
Authentication and User Provisioning services provide the means for users to securely log in to the organization’s applications and access the required resources, while Identity Governance (IGA) and administration tools enable administrators to manage user identities, roles, and permissions.
IDaaS works by providing a standardized way for applications and services to interact with the user directory, authentication, and provisioning services. This is typically achieved through the use of industry-standard protocols and APIs, such as SAML, OpenID Connect, and OAuth.
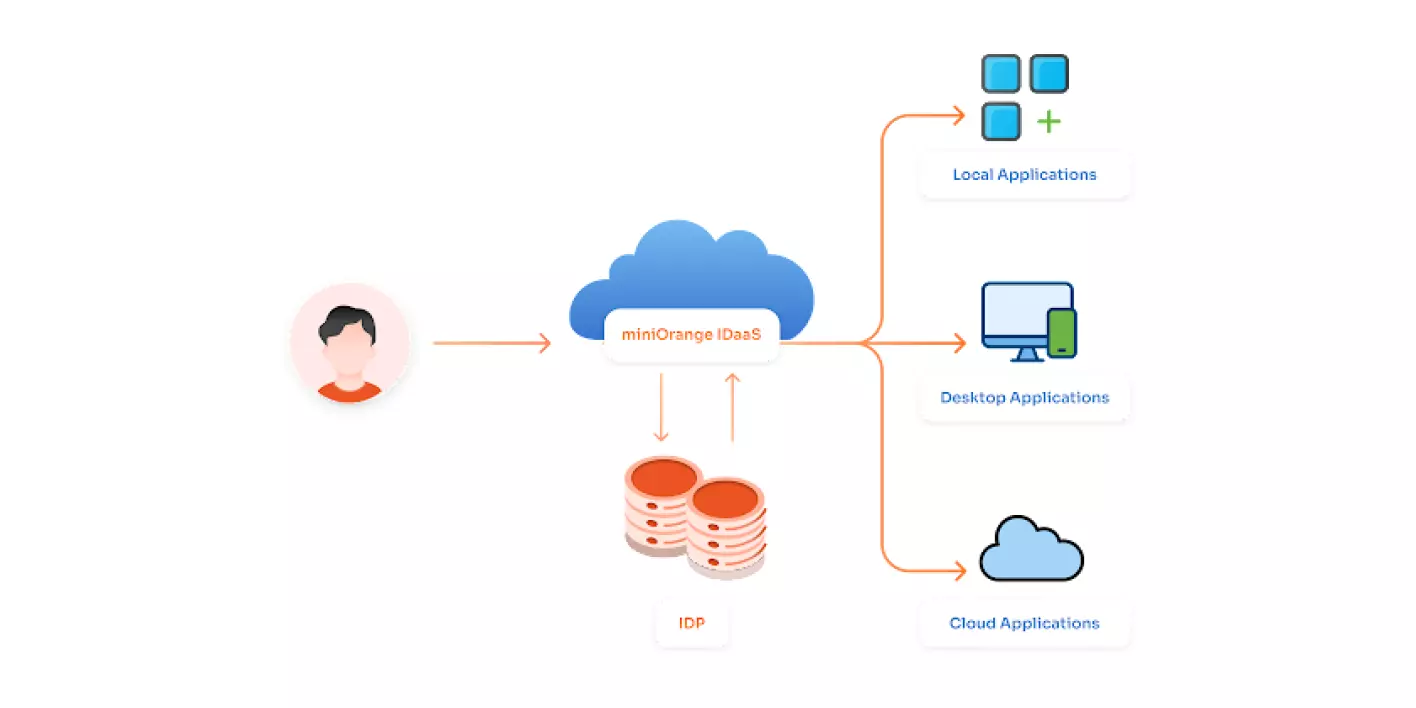
When a user tries to access an application, the application sends a request to the IDaaS platform to authenticate the user and determine the level of access permissions they have been granted. The IDaaS platform then checks the user’s credentials against the user directory, and if the user is authenticated, returns a token that the application can use to authorize the user’s access.
IDaaS or Identity-as-a-Service Platforms like miniOrange offer a convenient and secure way for organizations and businesses to manage user identities and provisioning across multiple applications and services while reducing the burden of managing their own Identity & Access Management infrastructure.
When you buy an IDaaS membership, your organization gets an API and/or a centralized configuration portal. You may use either to link your app suite with the service provider’s identity products and deliver capabilities like Single Sign-On (SSO), Social Login, Adaptive Authentication, and more. This is a smart way to optimize costs associated with authentication and identity management.
What are the Benefits of IDaaS?
- Decreased costs: Using a cloud-based IDaaS solution reduces the need for expensive equipment, skilled IT professionals, and continuing training, letting your IT team focus on day-to-day operations.
- Better user experiences: Users may log in with a single set of credentials using single sign-on and multi-factor authentication, which lowers friction and helps with password resets.
- Improved income and client loyalty: A positive first impression generated by a simple login experience leads to increased client interactions and purchases.
- Risk reduction: It helps you avoid data breaches, which may cost your company millions of dollars. Also, the hassle of maintaining an Identity-based Security infrastructure is saved when you subscribe to an IDaaS platform.
- Increased security: Corrupt individuals with compromised credentials will be unable to enter your system and steal data if you outsource your IAM Services to IDaaS providers.
- Adaptable to your requirements: Cloud-based subscription services are flexible enough to adapt to shifting customer bases, such as an inflow of new consumers for special events or promotions.
What are the key features of IDaaS?
- SSO: Employees, partners, and customers can access all SaaS, mobile, and enterprise apps with a single login utilizing corporate credentials via Single Sign-On.
- Identity Management: User identities are stored and managed by an IDP. An Identity Provider may verify user identities using username-password combinations and other variables, or it may simply give a list of customer identities for verification by another service provider.
- User Provisioning: Customer data is synchronized with online and corporate apps thanks to SCIM compatibility and connection with on-premises provisioning.
- Multi-Factor Authentication (MFA): Adaptive authentication methods—options to ratchet up as risk grows, depending on situational changes, user behavior, or application sensitivity—are commonly included in MFA.
- Directory Services: While most businesses choose to link IDaaS with their current client databases, they may choose to employ a cloud Directory Service to assist customers and/or partners.
- Privileged Access Management (PAM): PAM is a set of policies, practices, and technologies that enable organizations to control and monitor access to critical systems, applications, and data by privileged users.
What is Identity Management?
Identity management refers to the processes and capabilities provided by the IDaaS solution to manage and control digital identities. Organizations can leverage the capabilities provided by the IDaaS provider to manage user identities, authentication, and access to resources. This includes features like User Provisioning, SSO, MFA, Identity Lifecycle Management, Access Control and Authorization, Identity Governance, Self-Service Features, etc.
What is Identity Governance?
Identity governance, also known as Identity Governance and Administration (IGA), refers to the processes, policies, and technologies that organizations implement to manage and govern user identities and their access to resources. It focuses on ensuring that the right individuals have the appropriate levels of access to the right resources, while also maintaining security, compliance, and accountability.
Identity Governance involves the following key aspects like Identity Lifecycle Management, Role-Based Access Control (RBAC), Access Certification and Review, Policy Enforcement, Audit, and Compliance. The miniOrange IDaaS solution provides Identity governance as one of the features.
Types of IDaaS
IDaaS can be classified into two broad categories based on their feature sets:
- Basic: Suitable for cloud-first, small-to-medium-sized businesses that primarily want SSO for their cloud-based apps. This is best for businesses that have very little onsite/legacy infrastructure.
- Enterprise: This kind is ideal for bigger organizations with a variety of linked systems. Enterprise solutions offer a significantly broader feature set and can often support a much wider range of operational use cases. Their clients often have a combination of multi-cloud and on-premises infrastructure, necessitating a wide range of APIs for integration. To meet the specialized needs of the business customer, service providers may have to tailor their IDaaS offerings.
Is IDaaS different from IAM & IDP?
IDaaS (Identity-as-a-Service), IAM (Identity and Access Management) and IDP (Identity Providers) are related concepts. But there are some fundamental differences. Like:
IAM Services refer to the processes, policies, and technologies used to manage user identities and their access to resources within an organization’s IT infrastructure. IAM solutions typically include features like User Provisioning, authentication, and access control. IDP, on the other hand, is a component of IAM that is responsible for verifying a user’s identity and providing access to resources based on that identity. An IDP may use various Authentication methods such as Username/Password, Multi-Factor Authentication, or Biometric Authentication to verify the user’s identity. IDaaS is a cloud-based service that provides identity management and authentication capabilities to organizations. IDaaS solutions are delivered as a service, typically through a subscription model, and can be used to manage user identities across multiple applications and services.
“IDaaS can be referred to as SaaS-based IAM services.”
So while IAM services refer to the broader concept of managing user identities and access, IDP is a component of IAM and focuses on verifying user identity whereas IDaaS is a specific type of solution that provides identity management as a service. IDaaS solutions often incorporate IAM functionality as part of their service offerings. miniOrange provides both IDaaS & IAM solutions to cater to the varying security needs of different kinds of organizations.
Why do Enterprises Require Cloud Identity Management Solution?
Cloud providers have the responsibility to regularly update systems and prevent breaches in IDaaS. Since security is a fundamental element of their business, these cloud providers keep up with the latest threats and technologies, frequently update their network, manage patches and updates, and use qualified security people to monitor solutions. Due to all of this, Identity-as-a-Service makes the risk of data breaches significantly reduced.
Here are some of the key reasons why Enterprises require Cloud Identity Management Solutions:
- Scalability: Identity & Access Management solutions for cloud apps can scale to meet the needs of growing enterprises, providing greater flexibility and agility than on-premises solutions.
- Cost-effectiveness: Cloud-based solutions can be more cost-effective than traditional on-premise solutions, as they often require less upfront investment and are more efficient to maintain.
- Remote work: The rise of remote work has made it more challenging to manage and secure identities across distributed networks. Cloud-based solutions can provide a centralized platform for identity management, reducing the risk of security breaches.
- Compliance: Many enterprises are subject to strict regulatory requirements regarding data privacy and security. Cloud-based identity security solutions can help ensure compliance with these regulations.
- Integration: Cloud-based identity security solutions can integrate with other cloud-based services, such as SaaS applications, to provide a more comprehensive and streamlined approach to identity management.
- Threat detection: They can provide real-time threat detection and response, enabling enterprises to quickly identify and respond to potential security threats.
Conclusion
In today’s fast-paced cyber environment, it’s critical for businesses to implement security solutions. It’s even more critical to pick the right Identity and Access Management (IAM) solution for establishing and managing your employees, stakeholders, customers, and clients’ authentication and provisioning. miniOrange offers a variety of IAM solutions that are both efficient and safe. However, before deciding on a cloud security solution provider, ensure that they securely manage your data and give the most basic technical assistance at a reasonable cost. You may sign up for a month of miniOrange business free trial to check out our IAM solutions and make better, more informed decisions.
Author