Need Help? We are right here!
Search Results:
×Premium Customers
Integrations
Available for you







I can't speak highly enough regarding miniOrange, I am totally satisfied with the process and results in every regard.
5.0

Awesome tech service, Awesome product. Overall Awesome people. This solutions is very simple and easy to implement
5.0
Atlassian CASB is a cloud security solution that protects your business applications like Jira, Confluence, Bitbucket, Trello and other services from unauthorized access and data breaches. With the Atlassian CASB integration, you gain in-depth visibility into user activities, monitor risky behaviors, and dynamically revokes access to users and Atlassian apps when necessary depending on change in user’s Network IP, Location, Device in use, Time, and User’s role.
Enable Atlassian App download restrictions to limit file downloads to authorized users and admins to prevent data breaches with Atlassian CASB security.
Allow access to your Atlassian apps when they are on a whitelisted network IP, and revoke their access when it changes in real-time to prevent user access from outside the company network.
Encrypt all data on Atlassian apps, whether it’s data at rest or in transit to ensure compliance policies are met and prevent potential data breaches with a CASB.
Continuously monitor and alert your SOC teams about unauthorized data access attempts, enabling swift action against internal attacks by revoking user access.
Get detailed reports and analysis of user activity with your Atlassian apps to help your SOC team comprehend security threats and reduce system downtime.
Assign risk scores to users based on their activity with Atlassian Cloud apps, enabling proactive security with strong restrictions and revoking access when thresholds are exceeded.
Our DLP integration prevents unauthorized data downloads to devices and mitigates threats like sensitive data exploitation in Jira, Confluence, Bitbucket, Trello and more, ensuring robust protection against data breaches.
Our Atlassian CASB solution protects your organization by detecting malware or ransomware attacks, instantly isolating affected Atlassian applications to contain and resolve threats effectively.
Shadow IT means using software/hardware that the SOC team has not approved. Our Atlassian CASB Enterprise solution identifies and prevents such unauthorized software and hardware from being used in the organization.
Our Atlassian CASB integration ensures complete app data protection by proactively detecting and mitigating threats, reducing the risk of data breaches.
Easily monitors user activity on Atlassian app suite like Jira, Confluence, Bitbucket, Trello and more, down to the most granular level, enabling better control and management.
Enables granular access control for individual user groups and Atlassian cloud apps to prevent unauthorized user access and safeguard the data stored on the apps.
Adapts to the growing needs of an organization and supports scalability without compromising security.
We at miniOrange also offer other Atlassian Cloud and DC products that can be integrated individually or alongside our Atlassian CASB Enterprise security solution.
CASB solutions from miniOrange can be easily deployed in your organization's existing environment.
Imagine a company that relies heavily on Atlassian applications like Jira and Confluence for collaboration and project management. However, the company is struggling with unauthorized access attempts by employees to sensitive information, which could lead to regulatory fines, loss of customer trust, and operational disruptions.
With miniOrange Atlassian CASB integration, the company can monitor all user access attempts in real time and alert the SOC team the moment unauthorized access is detected, enabling swift action to prevent any potential breach. This way, the company can ensure its enterprise cloud data is safe and follows industry standards such as GDPR, ITAR, HIPAA, and SOC.
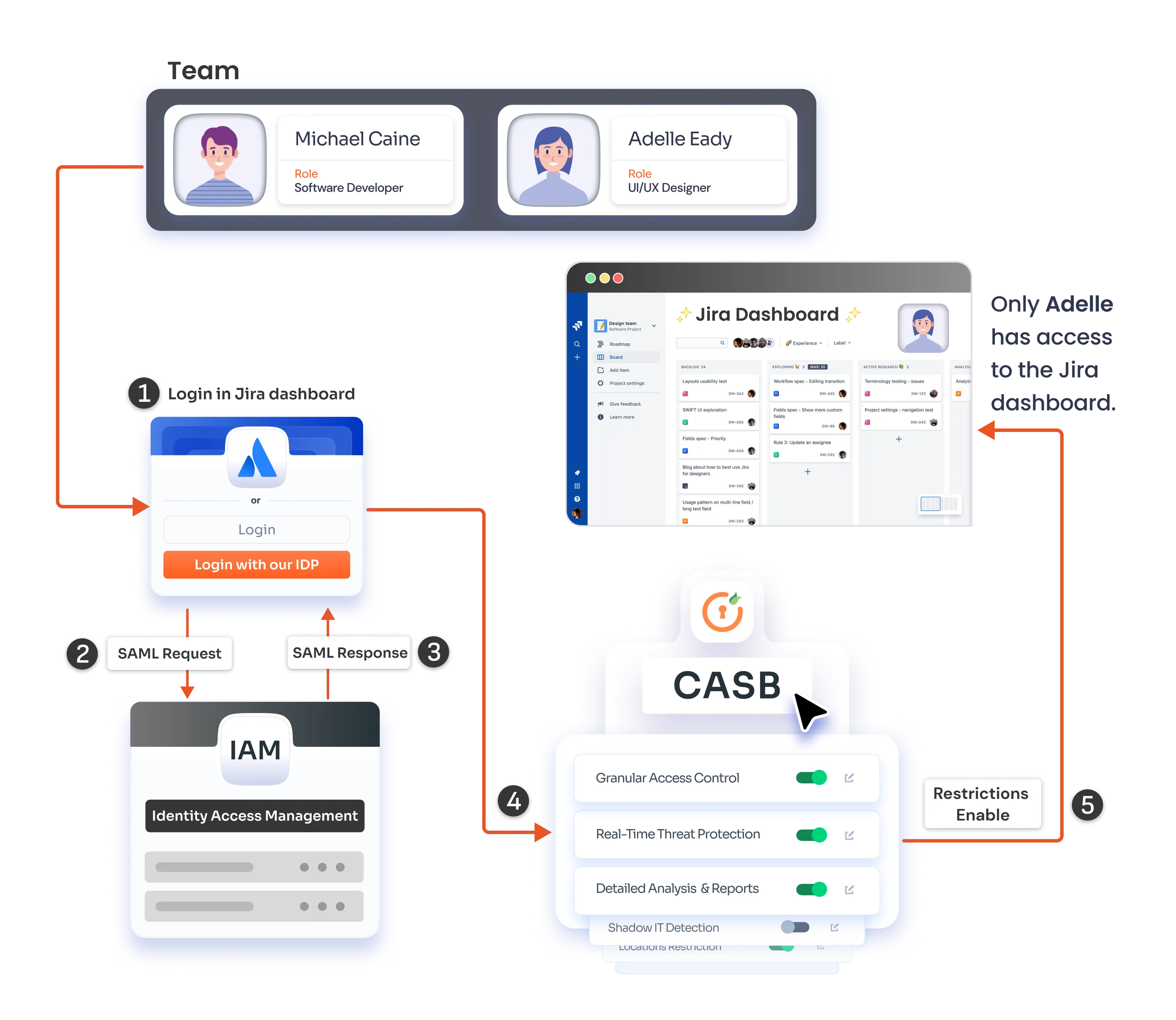
Atlassian Cloud Access Security Broker (CASB) is a security solution tailored for Atlassian Cloud Apps like Confluence and Jira, enhancing security and compliance through strong data control and user access restrictions.
Atlassian CASB monitors user activities, identifies risks, and applies security policies to prevent unauthorized access or potential data breaches on Atlassian cloud apps.
Integrating miniOrange CASB with Atlassian apps is simple to set up and configure. Learn how by clicking this link.
Contact us at info@xecurify.com, and we'll connect with you to discuss your Atlassian CASB needs.
Atlassian CASB provides detailed insight gathering, Shadow IT detection, and malware mitigation, and actively controls data flow to prevent breaches and ensure compliance.
Thank you for your response. We will get back to you soon.
Please enter your enterprise email-id.
