How to Restrict Access to MS Office 365 Data to Whitelisted Office Network IPs?
As businesses migrate their operations to the cloud, securing access to critical platforms like Microsoft 365 becomes a top priority. Traditional security measures are insufficient to protect sensitive company data in today's cloud-centric world.
While Microsoft 365 offers some built-in security features, these often need to be enhanced with additional layers of protection to ensure that only trusted users from approved network IPs and VPNs can access sensitive data. This is where office network IP whitelisting and network access control become essential for securing MS Office 365 data.
By restricting access to Microsoft 365 data based on whitelisted office network IPs and VPNs, businesses can significantly lower the risk of unauthorized access and data breaches. This method provides an extra layer of security, ensuring that only trusted networks can interact with your organization’s business data on Microsoft 365.
In this section, we’ll explore how to implement IP whitelisting and VPN-based network access controls for Microsoft 365, and how these strategies can fortify your organization's security defenses.
How to setup miniOrange CASB for real-time IP Restrictions on MS Office 365?
Step 1: Sign Up and Access the miniOrange CASB Dashboard
- Click here to log in to CASB Dashboard.
- (Don't have an account? No worries, click here to create a new account.)
- Go to your miniOrange CASB dashboard.
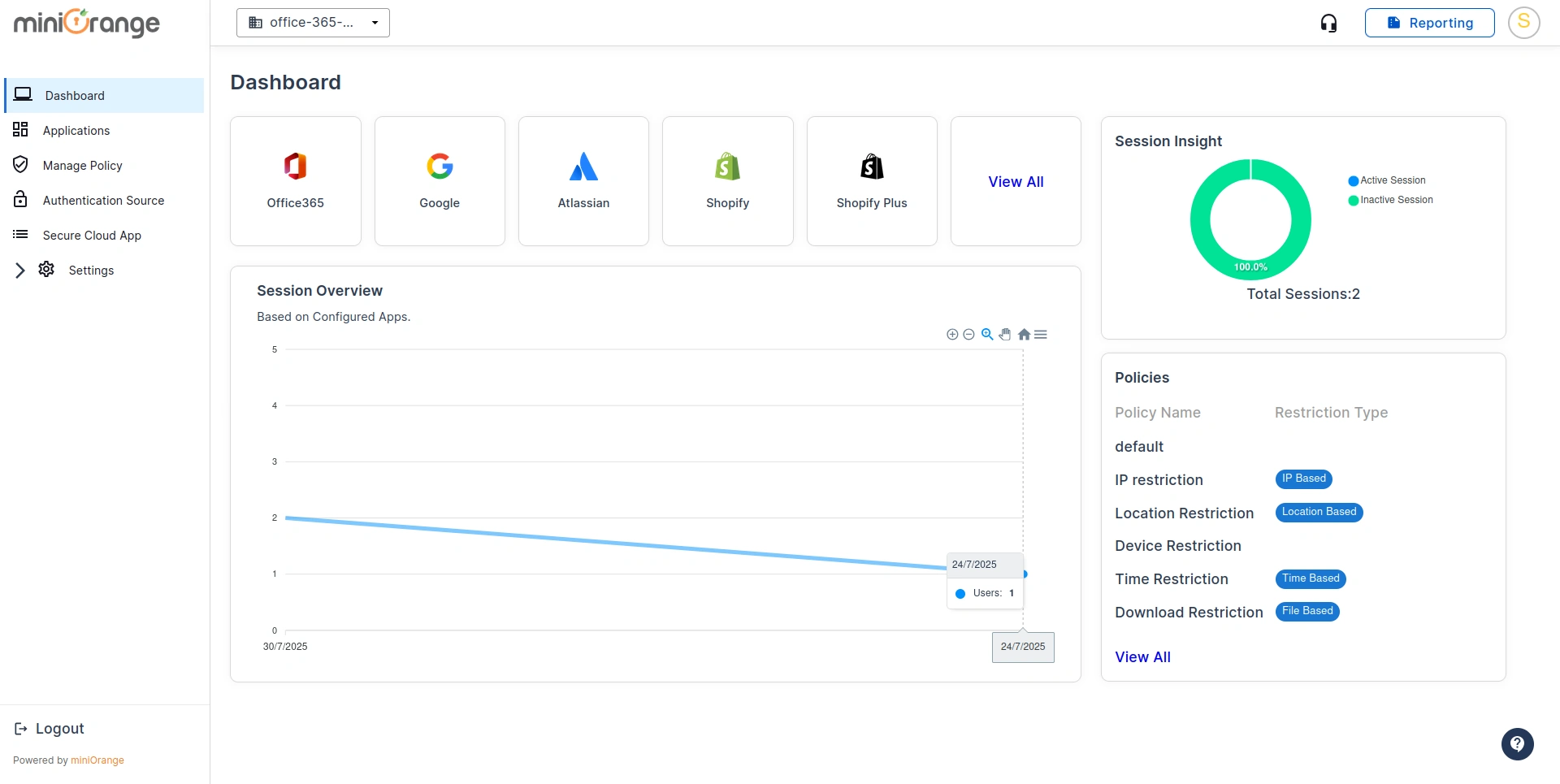
Step 2: Enable Real-Time IP Restriction for Microsoft Office 365
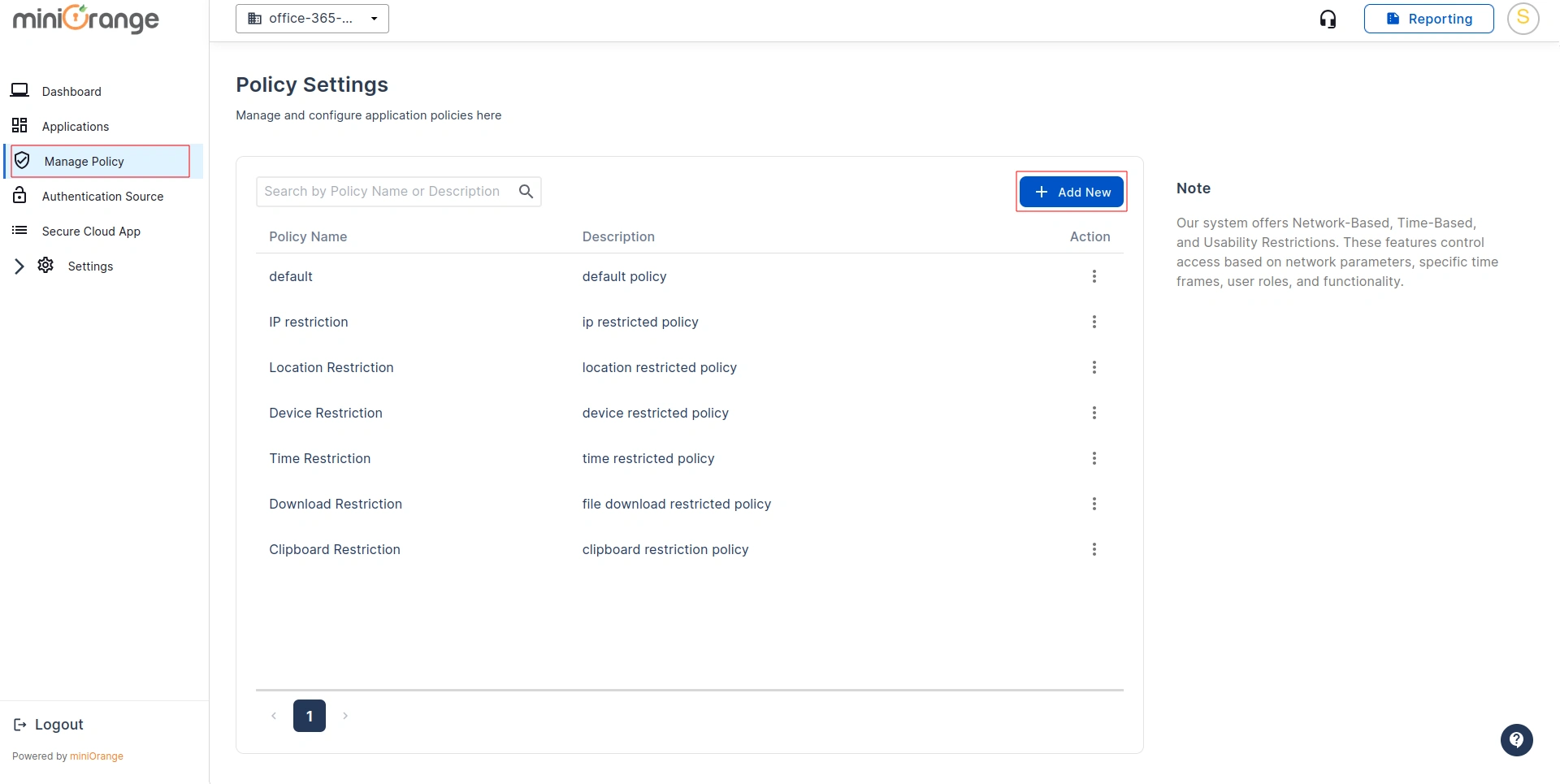
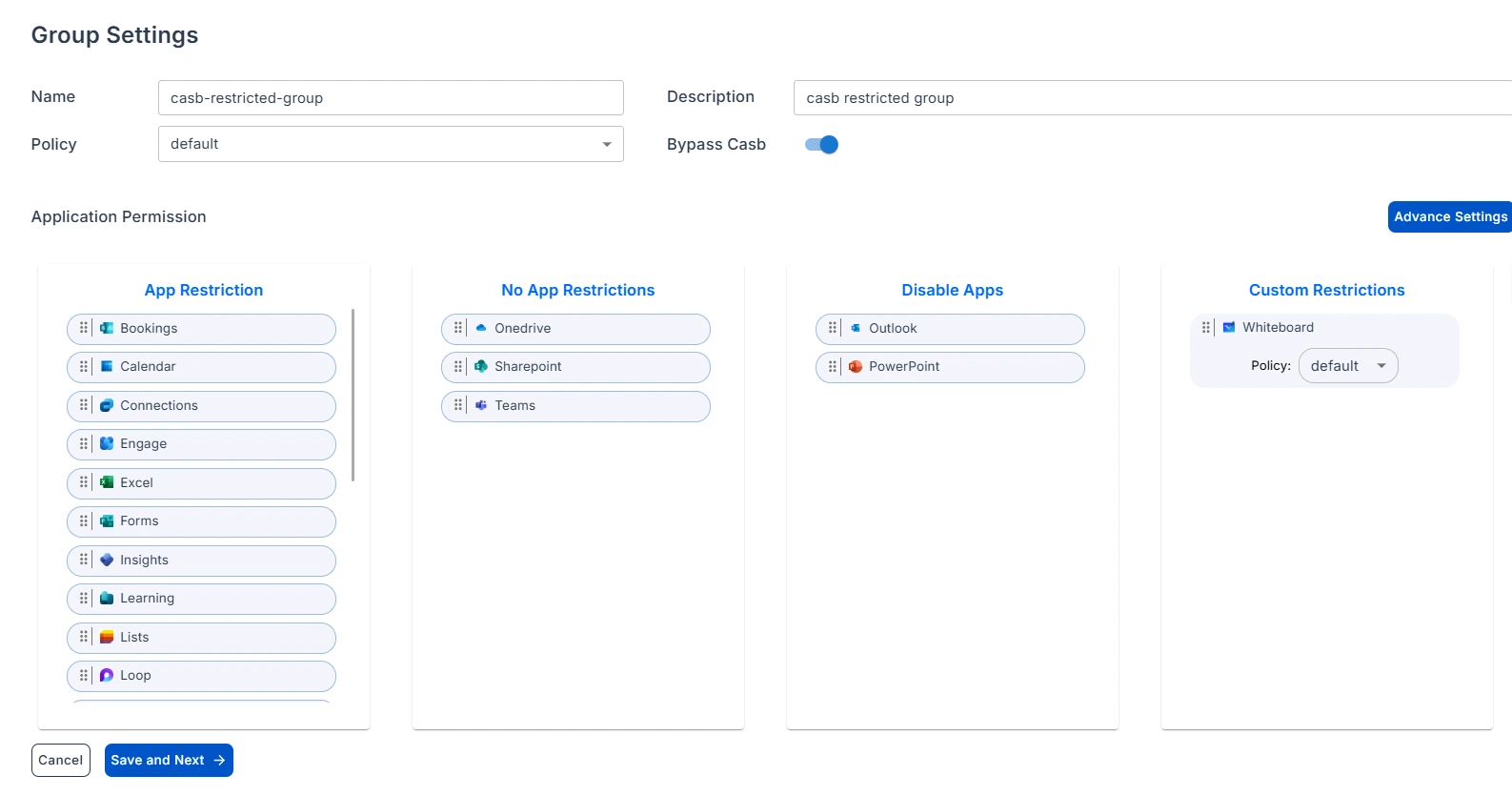
- Go to Manage Policy and create or select a policy with a clear name and description.
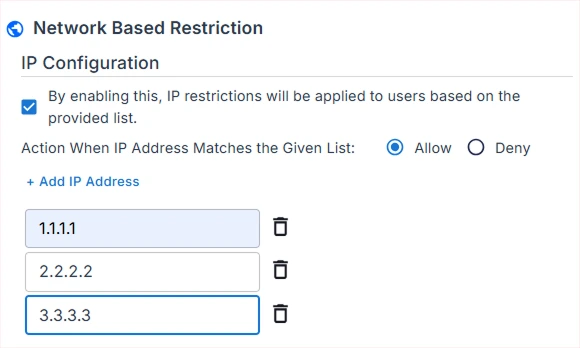
- By enabling this IP Restriction feature, you are restricting access to users based on their IP addresses.
- Once configured, attach the policy to a user group of your configured application under the Applications Section to ensure the restrictions are enforced for the intended users.
Why Are IP Restrictions Important for MS Office 365 Security?
Implementing Network IP restrictions for Microsoft Office 365 is crucial for ensuring that only when users are on the trusted office networks can they access sensitive business data. Without proper network access controls, organizations expose themselves to significant security risks, especially when sensitive data is accessed from unknown or unauthorized networks.
Here’s why IP restrictions are essential for securing Microsoft 365:
- Prevent Unauthorized Access: IP restrictions ensure that only users from trusted office networks or authorized VPNs can access Microsoft 365 apps like Outlook, OneDrive, SharePoint, and Teams. By blocking access from unknown sources or unauthorized networks, you minimize the risk of unauthorized user access to business-critical data.
- Boost Data Security: Even if an account is compromised, the attacker would still need to access Microsoft 365 from an approved IP address. This additional layer of security helps protect sensitive business information, preventing unauthorized access even if login credentials are exposed.
- Compliance Ready: Many industries are subject to strict data protection regulations, such as GDPR, HIPAA, SOC 2, and others. By restricting access to whitelisted IPs, organizations can help meet these compliance requirements, ensuring that only authorized networks are accessing sensitive data and maintaining audit logs for regulatory purposes.
- Mitigate Insider Threats: Insider threats pose significant risks to an organization. Whether from malicious actors or compromised internal users, IP restrictions limit access, making it more difficult for unauthorized internal users or compromised devices to reach sensitive data. This reduces the chance of accidental or intentional data exposure.
- Improved Data Monitoring and Control: By enforcing network access control, it becomes easier to monitor who is accessing Microsoft 365 and from where. You can track login attempts, identify suspicious activity, and respond quickly if any potential security breaches occur, adding an essential layer of visibility and control over your data security.
How miniOrange CASB Restricts Data Access to Whitelisted IPs and VPNs Compared to MS 365?
Securing access to Microsoft 365 data is essential for businesses that want to protect sensitive information and ensure that only trusted users can access their cloud environment. While Microsoft 365 provides basic security features, miniOrange CASB takes this a step further by offering more precise, customizable controls to restrict data access to whitelisted IPs and VPNs.
Here’s how miniOrange CASB enhances security by restricting access to Microsoft 365 data:
1. Real-Time IP Restriction
- Microsoft 365 Native: Microsoft 365 allows for basic IP-based restrictions in its higher-tier plans, but it lacks real-time enforcement and may not apply precise access controls for all types of users and locations.
- miniOrange CASB: With miniOrange CASB, you can enforce real-time IP restrictions to ensure that only users connecting from trusted IP ranges or authorized VPNs can access Microsoft 365 services. You can whitelist specific office networks, ensuring that data is only accessible from approved locations, minimizing the risk of unauthorized access.
2. Granular Policy Enforcement
- Microsoft 365 Native: While Microsoft 365 offers basic conditional access policies, customization is often limited, and security controls may not fully account for complex business needs such as device health, geolocation, or specific roles.
- miniOrange CASB: miniOrange CASB provides granular control by allowing organizations to create advanced access policies that account for device health, geolocation, user roles, and other factors. You can ensure that sensitive data is only accessible under specific, pre-defined conditions, significantly reducing exposure to threats.
3. Real-Time Access Monitoring
- Microsoft 365 Native: Microsoft 365 provides basic logging and alerts for IP-based access attempts, but real-time visibility into user activity and the sharing of data is limited, making it harder to detect suspicious behavior.
- miniOrange CASB: miniOrange CASB offers real-time monitoring of user activity, including detailed logs of login attempts, unauthorized access, and changes to access policies. Admins receive instant alerts on any suspicious activity, enabling them to respond quickly and ensure that only authorized users are accessing critical data.
4. Seamless User Experience
- Microsoft 365 Native: Implementing IP and VPN restrictions in Microsoft 365 can sometimes cause disruptions, particularly for remote users or teams accessing from dynamic IP addresses. These restrictions might hinder collaboration or access for legitimate users.
- miniOrange CASB: miniOrange CASB strikes a balance between security and usability. By enforcing IP and VPN-based policies, miniOrange ensures that only trusted users can access Microsoft 365, all while minimizing disruptions to legitimate users. This seamless integration allows teams to collaborate effectively without compromising on security.
Real-World Scenario: Securing MS Office 365 with Real-Time IP Restrictions Using miniOrange CASB
A company relies on Microsoft 365 apps like Outlook, OneDrive, SharePoint, Teams, and more to store and collaborate on critical business data. As the workforce grows and employees work from various locations, managing security policies and ensuring that only authorized users can access sensitive data becomes increasingly challenging. Unauthorized access from untrusted networks poses a significant risk to business data integrity.
Problem Statement:
- Traditional security measures fail to detect and prevent user access from unknown or untrusted IP addresses to Microsoft 365 apps. This becomes especially problematic for remote workers or employees using unsecured devices to access critical company data, leaving sensitive information vulnerable to potential breaches.
Solution:
miniOrange CASB provides network access control for Microsoft 365, ensuring that only users connecting from trusted IP addresses or authorized VPNs can access business-critical applications.
- Real-Time Detection: Suspicious activity—such as login attempts from untrusted IP addresses—is detected promptly. When such activity is detected, miniOrange CASB triggers an alert to the Security Operations Center (SOC) team for immediate investigation.
- Detailed Visibility: With enhanced real-time monitoring, IT administrators gain detailed insights into who is accessing Microsoft 365 data and from where. This allows them to analyze user access patterns and identify potential security threats before they escalate.
- Strengthening Security Measures: With miniOrange CASB, organizations can continually assess their IP-based security policies and adjust them to mitigate risks. This proactive approach helps protect Microsoft 365 data from unauthorized users and strengthens the overall security posture.
Summary
Securing Microsoft 365 data is crucial for businesses that rely on cloud-based productivity tools for collaboration and storage. With the growing risk of unauthorized access from untrusted networks, implementing IP restrictions and VPN controls is essential to protecting sensitive information.
By leveraging miniOrange CASB, organizations can enforce real-time IP restrictions, ensuring that only users from trusted IP addresses or approved VPNs can access Microsoft 365 data. This enhances security, prevents unauthorized access, and helps maintain compliance with industry regulations.
External References





