Generate Security Reports for SOC Teams to Monitor Google Workspace Activity
Learn how to gain visibility and control over user activity and file access in Google Workspace with real-time security reports. Get actionable insights, continuous monitoring, and automated policies to protect sensitive data and ensure compliance with industry standards.
As Google Workspace becomes a central tool for collaboration in today’s hybrid and remote work environment, securing your organization's data is more crucial than ever. Without the right monitoring and reporting capabilities, sensitive business information can be exposed to unauthorized access, increasing the risk of data breaches and compliance violations.
While Google offers some built-in security features, they often lack the real-time visibility, dynamic control, and granular enforcement required to fully secure your data. Our solution fills this gap by providing robust auditing and reporting tools across Google Workspace to ensure comprehensive protection.
Let’s explore how to enhance security by leveraging advanced auditing features, proactive monitoring, and automated reporting to keep your Google Workspace environment safe and compliant.
Configuring Security Reports for SOC Teams in Google Workspace
Step 1: Sign Up and Access the miniOrange CASB Dashboard
- Click here to log in to CASB Dashboard.
- (Don't have an account? No worries, click here to create a new account.)
- Go to your miniOrange CASB dashboard.
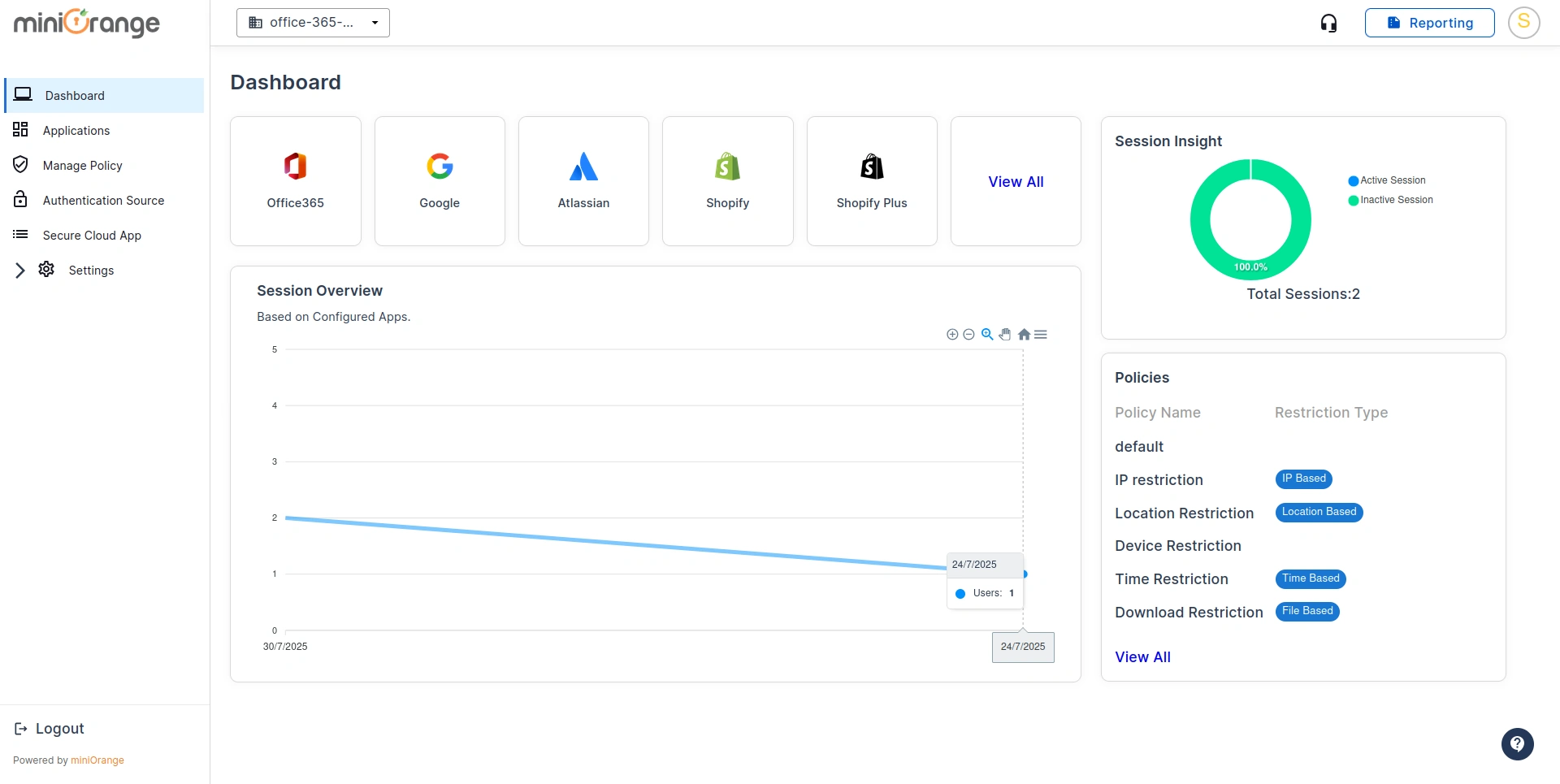
Step 2: Setup Reporting Dashboard
- Click on the Reporting button in the Top Right Corner.

- You are now on the CASB Reporting Dashboard.
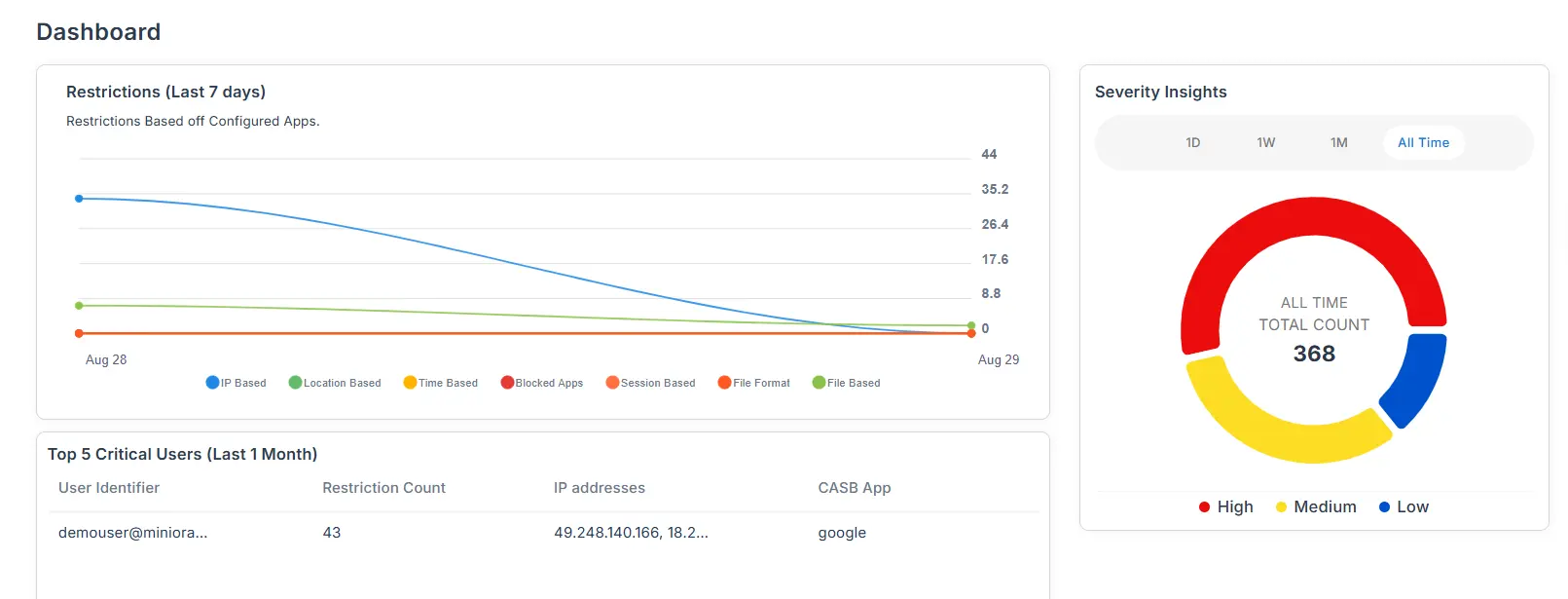
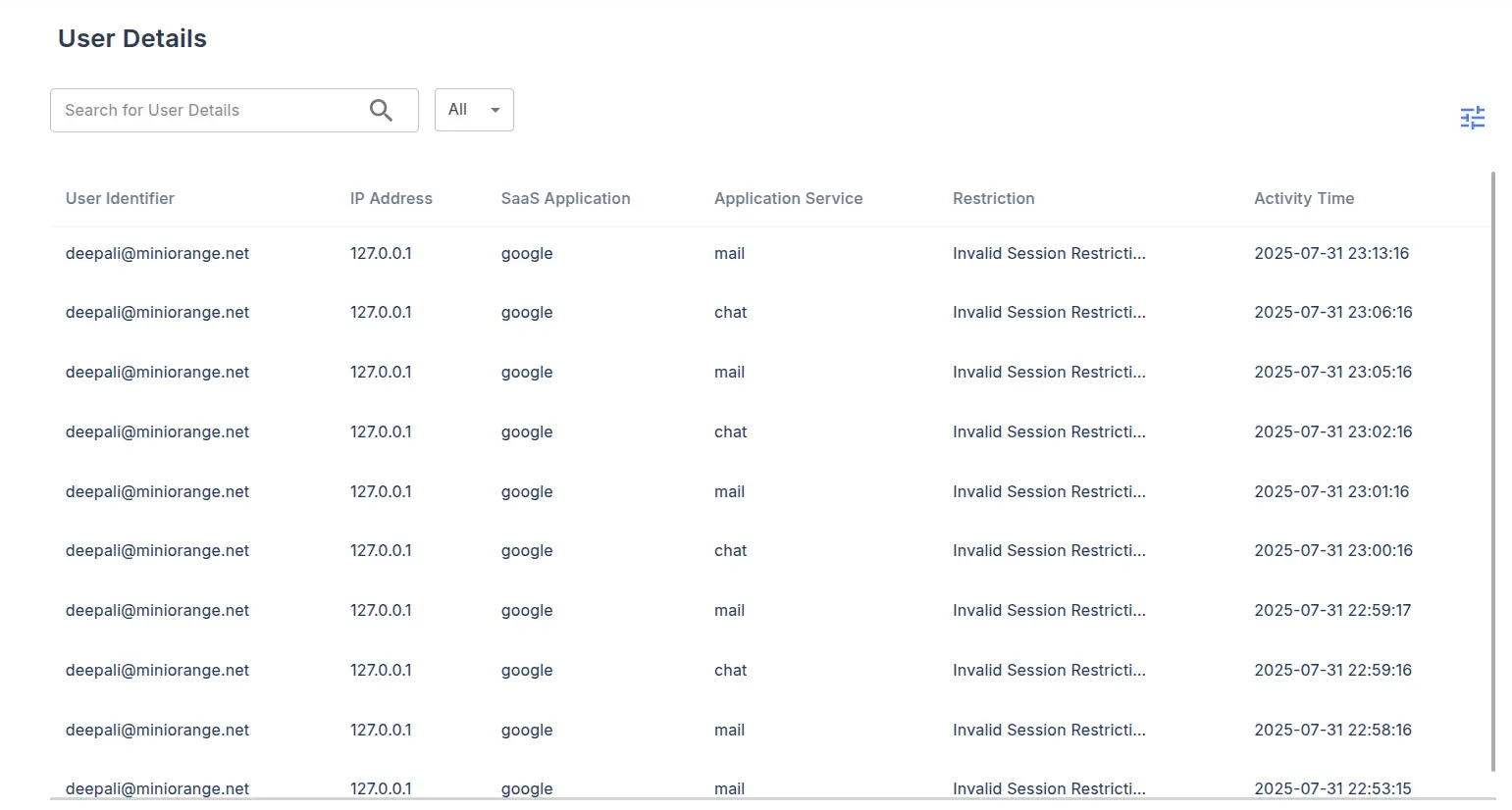
- Under the User Details.
- Configured Applications.
- Application Insights.

- Application Restriction Details.
Why Audit Logs, User Sessions, and File Access Are Critical for SOC Teams?
For SOC (Security Operations Center) teams, real-time logs, user sessions, and file access are not just tools — they are essential for maintaining security and preventing data breaches. In the fast-paced environment of Google Workspace, understanding user behavior and detecting irregularities quickly is critical for reducing risks, staying compliant, and ensuring that sensitive business data remains protected.
Audit Logs: Immediate Detection of Threats
- Real-time logs are the backbone of proactive security. Without them, SOC teams can’t detect suspicious activity or unauthorized access until it’s too late. These logs provide a snapshot of every action taken within Google Workspace, helping security teams spot potential threats in real-time.
- Without access to real-time logs, incidents like unauthorized login attempts or unusual file-sharing patterns could easily go unnoticed, increasing the likelihood of a breach.
User Sessions: Identifying Anomalies and Suspicious Access
- Tracking user sessions is key to understanding when, where, and how employees are interacting with Google Workspace. Unusual logins, devices, or locations can be signs of potential threats like account takeovers or insider breaches.
- Without session tracking, a SOC team could miss signs of malicious activity, such as an employee logging in from an unfamiliar IP address or accessing sensitive data outside of normal working hours.
File Access: Protecting Sensitive Business Data
- Every time a file is accessed, edited, or shared in Google Workspace, there’s a risk that sensitive business information could be exposed to unauthorized users. Monitoring file access is critical to preventing data leaks and breaches.
- Without visibility into who is accessing and sharing files, businesses risk confidential information being exposed, shared with unauthorized parties, or altered by unapproved users. Real-time file access monitoring gives SOC teams the ability to protect intellectual property, financial data, and compliance-sensitive documents.
The Importance of Real-Time Visibility
- Without real-time logs, user session tracking, and file access monitoring, SOC teams are left blind to potential threats until they escalate. These security measures provide essential visibility into who is accessing data, from where, and when, giving security teams the insights they need to respond quickly and prevent costly breaches.
Key Benefits of Using Audit-Ready Reports for Monitoring and Security
Audit-ready reports are a critical tool for organizations looking to enhance security and streamline monitoring within Google Workspace. These reports provide comprehensive visibility into user actions, file access, and system events, helping businesses stay secure while maintaining compliance. With miniOrange CASB, your audit logs are automatically generated and ready for review at any time, offering enhanced protection without interrupting workflow.
Key Benefits of Audit-Ready Reports
- Compliance Ready – Meet industry regulations like GDPR, HIPAA, nLPD, DORA, ITAR, PCI DSS, SAMA, or SOC 2 with easily accessible, organized audit reports that track user activity and file access.
- Security Risk Monitoring – Detect suspicious activity quickly by analyzing detailed user logs and identifying abnormal behaviors like unauthorized logins or file sharing.
- Visibility and Accountability – Track every action within Google Workspace, ensuring transparency and accountability for employees, contractors, and third parties.
- Quick Incident Response – Respond faster to security incidents by accessing a detailed record of user activity, allowing you to understand the scope and source of potential breaches.
- Active Risk Mitigation – Regularly review audit logs to identify emerging trends or recurring issues, giving you the insight to address vulnerabilities before they escalate.
- Centralized Reporting for Admins – Gain centralized control and visibility over all activities within Google Workspace, with easy access to logs and reporting tools for administrators.
With miniOrange CASB, audit-ready reports are automatically generated, making compliance management simpler and security monitoring more efficient. These reports offer your business peace of mind, knowing that sensitive data and activities are consistently tracked and ready for review whenever needed.
Real World Scenario: Ensuring Data Integrity and Compliance for SOC Teams in Google Workspace
A company uses Google Workspace apps like Gmail, Drive, Calendar, Docs, and Meet to store, collaborate, and manage sensitive business data. With remote teams, third-party contractors, and employees working on personal devices, the organization struggles to maintain visibility over who’s accessing sensitive data and whether compliance standards are being met. Without proper controls, data integrity could be compromised, and non-compliance could lead to serious legal and financial consequences.
Problem Statement:
- Traditional security policies in Google Workspace often fall short of ensuring that only authorized users and secure devices can access critical data. Employees might use personal phones or laptops without security checks, and contractors could access company data from devices that don’t meet compliance standards.
- Without the ability to monitor this, confidential information can easily be exposed or shared inappropriately. This opens the door to data leaks, unauthorized file access, and violations of compliance standards like GDPR or HIPAA.
Solution:
miniOrange CASB steps in to provide a solution by offering a robust set of tools to ensure both data integrity and compliance in Google Workspace.
When employees or contractors try to access sensitive business data, miniOrange CASB provides real-time monitoring that allows the security team to track exactly who is accessing what data, from which device, and at what time. If an employee attempts to log in from an unapproved device, the system immediately flags the activity, giving the SOC team a chance to prevent potential breaches or compliance issues before they escalate.
miniOrange CASB also offers granular control over who can access specific files and data. This means sensitive documents stored in Google Drive or Gmail can only be viewed or edited by those who are authorized, reducing the risk of accidental or malicious data exposure.
For SOC teams, miniOrange CASB makes audits easy by automatically generating detailed reports of user actions. These reports are audit-ready, helping companies demonstrate compliance with important regulations such as GDPR, HIPAA, or SOC 2, without the need for manual tracking.
With miniOrange CASB, the security of Google Workspace is never in question. It ensures that only authorized devices and users can access sensitive data, while giving security teams the tools they need to keep track of every action and enforce compliance policies automatically.
Best Practices for Managing and Analyzing Security Reports for Google Workspace
Here are the best practices for managing and analyzing security reports for Google Workspace.
- Set Clear Objectives for Security Reporting
Define specific goals for security reports, such as monitoring login activity or compliance checks. This helps prioritize important data, spot vulnerabilities early, and ensure regulatory alignment.
- Automate Report Generation
Automate report generation to ensure consistent, timely, and accurate security data. This saves time, reduces errors, and keeps your team focused on critical security events without manual delays.
- Categorize and Prioritize Security Events
Not all security incidents are equal. Categorizing events allows you to focus on high-risk issues first, improving response times and preventing minor issues from becoming major threats.
- Regularly Review and Update Security Policies
Continuously review and update your security policies based on the data from reports. This helps identify policy gaps, ensure compliance with current standards, and address emerging threats quickly.
- Train and Educate Your Team on Report Analysis
Ensure your security team is trained to interpret security reports correctly. This empowers them to act on potential threats in real-time and respond effectively to minimize risks.
- Implement Continuous Monitoring and Alerts
Set up continuous monitoring and instant alerts to detect threats as they happen. This allows for immediate action and quick mitigation of potential security breaches or policy violations.
Summary
Managing and analyzing security reports is crucial for keeping Google Workspace secure and compliant. By following best practices like automating report generation, prioritizing security events, and continuously monitoring user activity, businesses can stay ahead of potential threats. Regularly reviewing security policies and educating teams ensures that your organization remains prepared to address emerging risks while meeting compliance requirements. With the right tools in place, SOC teams can effectively protect sensitive data and respond swiftly to security incidents.
External References








