2026 is here, and cybersecurity is defined by a critical paradox: despite widespread MFA adoption, credential-based breaches continue to surge. Traditional multi-factor authentication, static, friction-heavy, and often disconnected, no longer stands up to sophisticated threats, such as AI-powered phishing, MFA fatigue attacks, and prompt bombing campaigns, which exploit user behavior rather than technical vulnerabilities.
2026 marks a pivotal turning point. Regulatory frameworks worldwide are mandating stronger authentication controls, from the EU's DORA to updated PCI DSS 4.0 requirements. Cyber insurers now require advanced MFA as a coverage prerequisite. Meanwhile, technological maturity in passwordless authentication, AI-driven risk assessment, and quantum-resistant cryptography has reached critical mass.
The fundamental shift? Moving from static, point-in-time verification to continuous, context-aware authentication. Organizations aren't just asking "Who are you?" at login, they're continuously evaluating "Should you still have access?" based on behavior, location, device health, and real-time risk signals. This transformation isn't optional; it's essential for security, compliance, and competitive survival in an increasingly complex digital ecosystem.
Let’s understand the future trends in MFA.
Adaptive MFA: Context-Aware Security
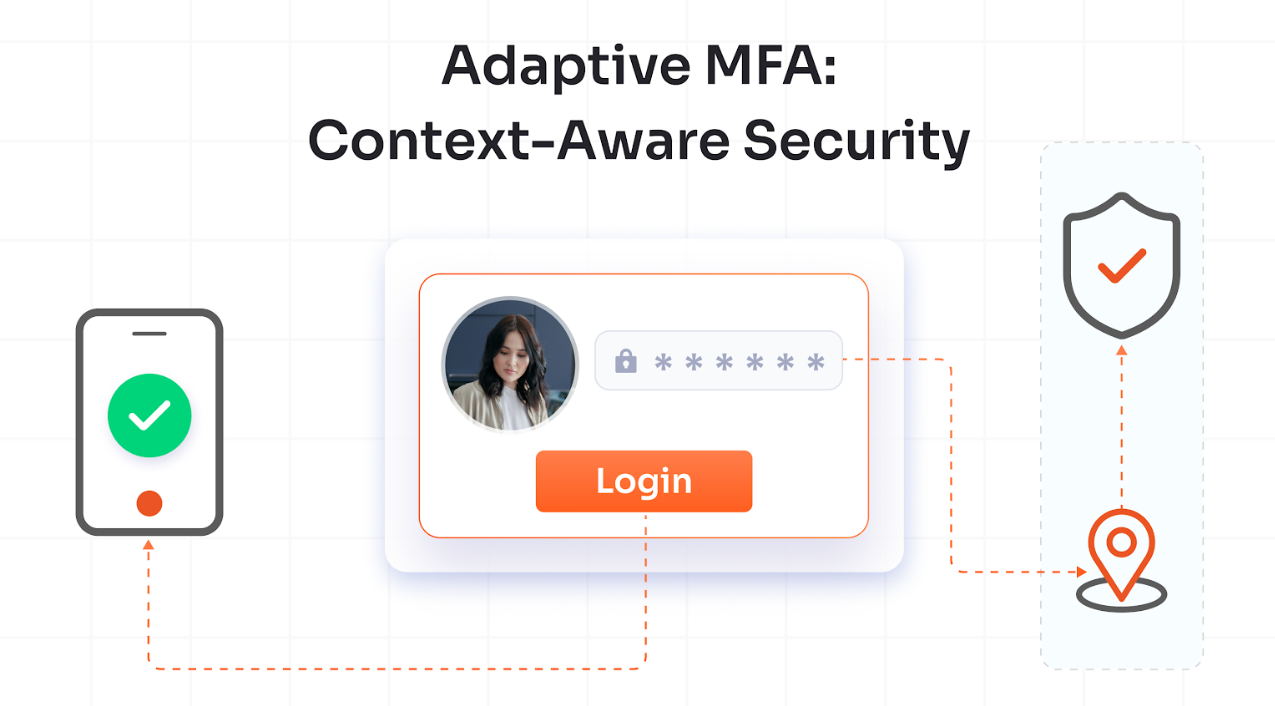
Adaptive authentication represents a fundamental shift from binary authentication decisions to dynamic, risk-based verification. Instead of applying the same authentication requirements to every login attempt, adaptive systems continuously evaluate contextual signals, i.e., device fingerprints, geolocation, network characteristics, time of access, and behavioral patterns to calculate real-time risk scores. A user logging in from their registered device during business hours might breeze through with minimal friction, while an unusual login from a new location triggers step-up authentication with additional verification layers.
This intelligence extends beyond the initial login moment. Modern adaptive MFA implementations incorporate continuous authentication, monitoring user behavior throughout the session. Unusual mouse movements, irregular typing patterns, or attempts to access sensitive resources can trigger re-authentication challenges mid-session. This approach aligns perfectly with Zero Trust principles, where trust is never assumed, and verification happens continuously.
Decentralized Identities (DID): User-Owned Authentication
Decentralized identities are revolutionizing the fundamental model of digital authentication by putting users in control of their own identity data. Built on blockchain and distributed ledger technologies, DIDs eliminate centralized identity providers as single points of failure and give individuals portable, verifiable credentials they control directly. Instead of organizations storing your identity data in vulnerable databases, you maintain cryptographic proofs of identity attributes that can be selectively shared and verified without exposing underlying personal information.
The implications for MFA are profound. DIDs enable true self-sovereign identity where authentication doesn't depend on corporate directories or third-party identity providers. Users can authenticate across multiple services using the same decentralized identifier, while cryptographic signatures ensure verification without password transmission. This approach largely reduces honeypot risks; there's no central database for attackers to compromise.
Quantum Computing: The Double-Edged Sword
Quantum computing presents both an existential threat and an opportunity for MFA systems. Current cryptographic algorithms underlying authentication will become vulnerable when sufficiently powerful quantum computers emerge. Security experts estimate that "Q-Day," when quantum computers can break current encryption, may arrive within the next 5-10 years, meaning organizations must begin preparing now for post-quantum cryptography (PQC).
The threat is immediate in a surprising way: adversaries are already conducting "harvest now, decrypt later" attacks, collecting encrypted authentication data today to decrypt once quantum capabilities mature. This makes quantum-resistant MFA not a future concern but a present imperative, particularly for organizations handling sensitive data with long confidentiality requirements.
The opportunity lies in quantum-enhanced security. Quantum random number generation provides true randomness for cryptographic keys, dramatically strengthening authentication security. Quantum key distribution (QKD) enables theoretically unbreakable secure communication channels. Forward-thinking organizations are already piloting hybrid cryptographic systems that combine classical and quantum-resistant algorithms, ensuring their MFA infrastructure remains safe through the quantum transition while maintaining backward compatibility with existing systems.
Passwordless Authentication: Beyond Passwords
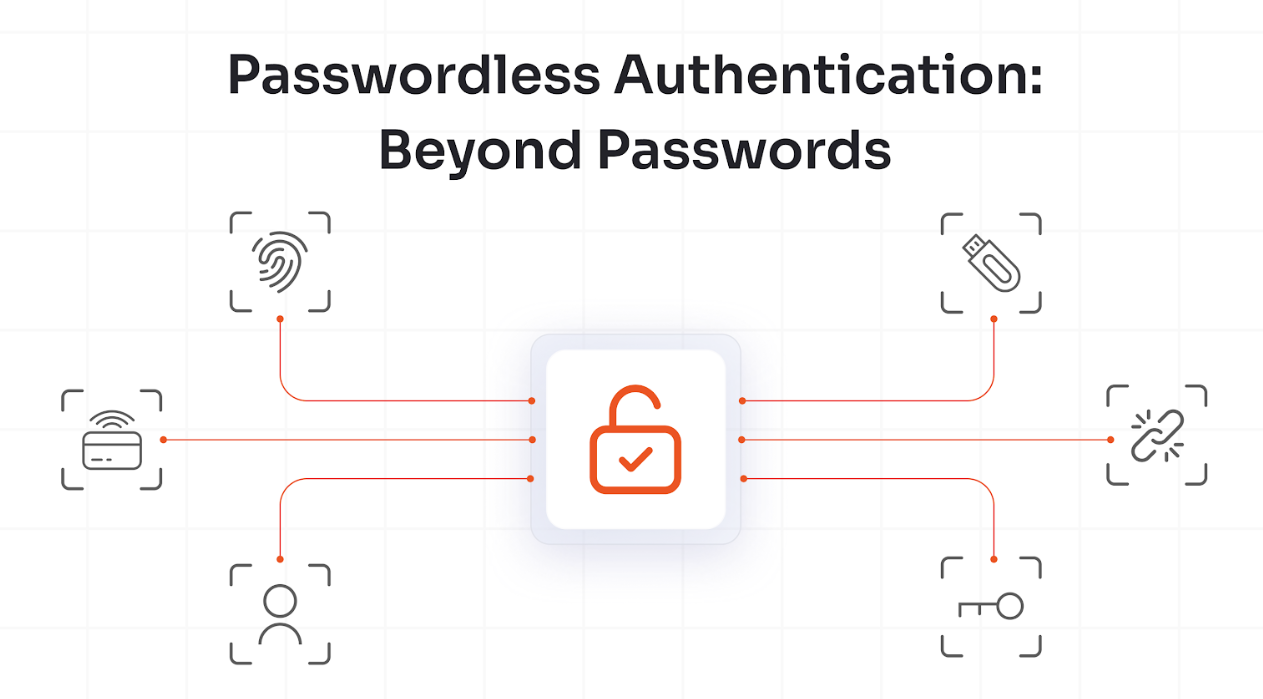
Passwordless authentication has evolved from an aspirational concept to a mainstream reality in 2026, driven by the maturity of FIDO2 and WebAuthn standards. The fundamental shift eliminates passwords, replacing them with cryptographic key pairs where the private key never leaves the user's device. Passkeys, synchronized across devices through encrypted cloud services, have become the consumer-facing implementation that major platforms, including Apple, Google, and Microsoft, have standardized. This creates seamless cross-platform authentication experiences that users prefer over traditional passwords.
The security benefits are compelling: passkeys are phishing-resistant by design since they're bound to specific domains and can't be tricked into authenticating against malicious sites. There's no shared secret for attackers to steal from databases, eliminating credential stuffing and password spray attacks. Users experience faster logins without password complexity requirements, forgotten password flows, or periodic reset mandates that plague traditional systems.
AI/ML-Powered MFA: Intelligent Security
Artificial intelligence and machine learning are shaping MFA from reactive security controls into predictive defense systems that anticipate and prevent threats before they materialize. Modern AI-powered MFA analyzes thousands of behavioral signals, typing cadence, mouse movement patterns, navigation habits, device usage times, and application interaction sequences to build unique behavioral profiles for each user. These systems detect anomalies with remarkable precision, identifying compromised accounts even when attackers possess valid credentials and complete MFA challenges.
The intelligence extends to fraud prevention through real-time risk scoring. Machine learning models correlate authentication attempts against global threat intelligence, identifying patterns associated with credential stuffing campaigns, bot-driven attacks, and account takeover attempts. When the system detects suspicious activity, it can automatically escalate authentication requirements, trigger security alerts, or even block access while initiating investigation workflows, all happening in milliseconds without human intervention.
Privacy and ethics remain critical considerations. Leading implementations use federated learning approaches that improve models without centralizing sensitive behavioral data. Explainability features help security teams understand why the AI made specific authentication decisions, crucial for compliance and incident investigation. The key insight driving the adoption is that AI doesn't replace human judgment in authentication. It augments the human factor, handling the pattern recognition at scale that humans simply cannot perform while escalating edge cases that require contextual human decision-making.
MFA for IoT Systems: Securing Connected Devices
IoT authentication presents unique challenges that traditional MFA approaches cannot address. Connected devices from industrial sensors to smart home appliances often lack screens for displaying codes, keyboards for input, or sufficient processing power for complex cryptographic operations. Yet these devices increasingly control critical infrastructure, sensitive data, and even physical safety systems, making authentication failures potentially catastrophic. The IoT security challenge isn't just protecting access; it's doing so within severe resource constraints.
Lightweight cryptographic protocols are emerging specifically for IoT contexts. Solutions like certificate-based device authentication, hardware security modules (HSMs) embedded in IoT chipsets, and physically unclonable functions (PUFs) that leverage manufacturing variations for unique device identification enable strong authentication without overwhelming limited processors.
Industry-specific approaches are evolving rapidly. Industrial IoT deployments combine device certificates with network segmentation and anomaly detection, ensuring compromised sensors can't pivot to critical systems. Healthcare IoT implementations prioritize patient safety alongside security, using continuous authentication that monitors device behavior for signs of compromise without interrupting life-critical functions.
Smart home solutions balance security with user experience, leveraging smartphone-based authentication that users already trust while implementing device-to-device authentication protocols that don't require human intervention for routine operations. The convergence point treats IoT authentication not as isolated device security but as ecosystem-level identity management.
Cloud-First MFA: Native Cloud Security
Cloud-first MFA represents a fundamental architectural shift from traditional on-premise authentication infrastructure to scalable, API-driven platforms designed for modern distributed workforces. Organizations are abandoning expensive hardware deployments and maintenance burdens in favor of MFA-as-a-Service solutions that provide instant scalability across thousands of users without upfront infrastructure investments. These cloud-native platforms eliminate the complexity of managing authentication servers, patching systems, and planning capacity upgrades; authentication becomes an instantly available utility rather than a technical project.
The strategic advantage lies in deep integration with major cloud ecosystems. Cloud-first MFA solutions natively integrate with Microsoft Azure, AWS, and Google Cloud, creating unified identity management across entire enterprise environments. This enables seamless authentication flows whether users access SaaS applications, cloud infrastructure, or hybrid resources. API-first architectures allow developers to embed authentication into microservices and containerized applications with minimal code, supporting modern DevOps practices and cloud-native application development patterns.
Global deployment becomes dramatically simpler with cloud-first approaches. Distributed teams access corporate resources securely from anywhere without VPN bottlenecks or regional authentication servers. Multi-cloud and hybrid environment challenges persist; organizations must manage identity across disparate cloud providers while maintaining consistent security policies, but cloud-first platforms increasingly offer centralized policy management and automated governance to control this complexity.
MFA for SMBs: Democratizing Enterprise Security
Small and medium-sized businesses face a critical security dilemma in 2026. They're increasingly targeted by cybercriminals who view them as easier prey, yet only 45% have implemented advanced MFA compared to 57% of larger enterprises. SMB MFA adoption remains significantly below enterprise levels, with small organizations showing just 27-34% MFA implementation rates. This vulnerability gap has devastating consequences, as a single breach can destroy customer trust and business operations for SMBs lacking the resources to recover that larger organizations possess.
The barriers to adoption are being systematically dismantled. MFA-as-a-Service providers now offer affordable, easy-to-deploy solutions specifically designed for non-technical teams with limited IT staff. These platforms eliminate complex configurations in favor of guided setup wizards, pre-configured security policies, and simplified user management interfaces.
Managed Service Providers (MSPs) are emerging as critical enablers, offering bundled authentication services that combine MFA with password management and identity management at price points SMBs can afford. The economics have fundamentally shifted; cloud-based solutions with usage-based pricing mean even the smallest businesses can implement enterprise-grade authentication without capital expenditure.
Biometric Authentication: Next-Generation Verification
Biometric authentication in 2026 extends far beyond traditional fingerprint scanning into sophisticated multimodal systems that combine multiple verification methods for unprecedented security and accuracy. Modern facial recognition incorporates 3D depth mapping, infrared blood flow detection, and micro-expression analysis to defeat spoofing attempts that fooled earlier 2D systems.
Behavioral biometrics represent perhaps the most revolutionary development, analyzing how users interact with devices rather than what they physically are. Systems measure keystroke dynamics, gesture patterns, gait recognition via smartphone sensors, and even cognitive biometrics that analyze decision-making patterns. These behavioral markers provide continuous authentication throughout sessions rather than one-time verification, detecting account takeover even when attackers possess valid credentials.
However, significant challenges temper the enthusiasm. Privacy concerns and regulatory frameworks like GDPR create complex compliance requirements around biometric data collection, storage, and usage. The path forward lies in privacy-preserving implementations that store biometric templates locally on user devices rather than centralized databases, and adaptive authentication that dynamically selects verification methods based on risk scores, requiring stronger biometric proof only when suspicious patterns emerge.
Employee Training and Awareness: The Human Factor
The most sophisticated MFA technology fails when users don't understand how to use it properly or why it matters. MFA fatigue, where users become desensitized to authentication prompts and automatically approve requests without verification, has emerged as a critical vulnerability exploited through prompt bombing attacks.
Attackers flood users with authentication notifications until exhausted employees accidentally approve access just to stop the interruptions. This human vulnerability demonstrates that technology alone cannot secure authentication; organizational culture and user education are equally essential security controls.
Effective training programs in 2026 go beyond compliance checkboxes to create genuine security awareness. Best practices include contextual education that explains specific threats employees face rather than generic security lectures, using real-world breach examples from similar organizations to make risks tangible. Gamification strategies, security challenges, simulated phishing tests with immediate feedback, and recognition programs for security-conscious behavior drive engagement far more effectively than mandatory annual training modules.
Users who understand that MFA prevents account compromise that could expose their personal communications are more vigilant than those who view it as IT-imposed friction. Onboarding processes should introduce MFA as a benefit and enabler, not a burden. Regular communication about emerging threats, clear escalation paths when users suspect compromise, and leadership modeling secure authentication behaviors all contribute to organizational resilience.
Convergence and Integration
The fragmented identity security landscape is rapidly consolidating into unified platforms that integrate MFA, identity governance, privileged access management, and threat detection within single ecosystems. These trends work synergistically as adaptive MFA uses AI/ML-powered risk scoring to dynamically select authentication methods, passwordless passkeys for routine access, biometric verification for sensitive operations, and quantum-resistant cryptography for long-term protection. Cloud-first architectures provide scalable infrastructure accessible to SMBs and enterprises, while organizations move toward comprehensive platforms governing all access under unified, policy-driven frameworks.
MFA for Secured Future
Organizations must recognize that authentication has evolved from a technical control to a foundational business enabler, where identity serves as the new security perimeter. Modern MFA implementations reduce credential-based incidents by 80-90% and eliminate 30-50% of helpdesk burden from password resets. Strategic planning should prioritize cloud-first MFA, passwordless authentication, AI-powered analytics, and quantum-readiness preparation. Organizations modernizing identity security in 2026 will protect against current threats while positioning for future challenges, while those delaying face increasing vulnerability and compliance risks.




Leave a Comment