Need Help? We are right here!
Search Results:
×






Passwordless authentication works by replacing passwords with alternative authentication methods. Typically, these authentication methods can be categorized into either possession or inherence.
These passwordless authentication methods are a subset of multi-factor authentication (MFA), and can be used to secure VPNs, Windows, Linux, macOS, confidential accounts, and more.
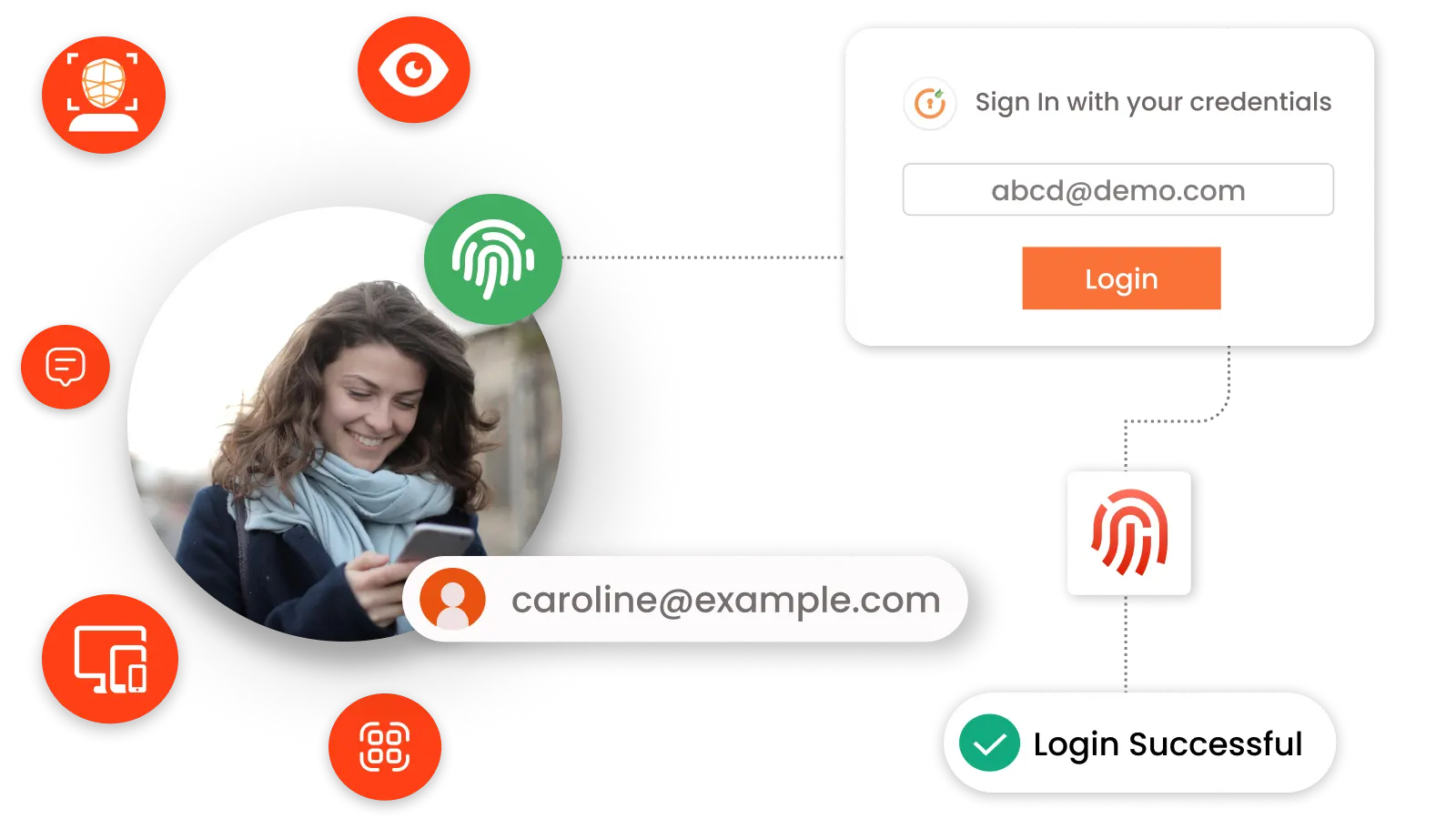
Passwordless authentication solutions leverage various technologies to verify a user's identity without requiring a password. Here’s a brief overview of how miniOrange passwordless authentication works:
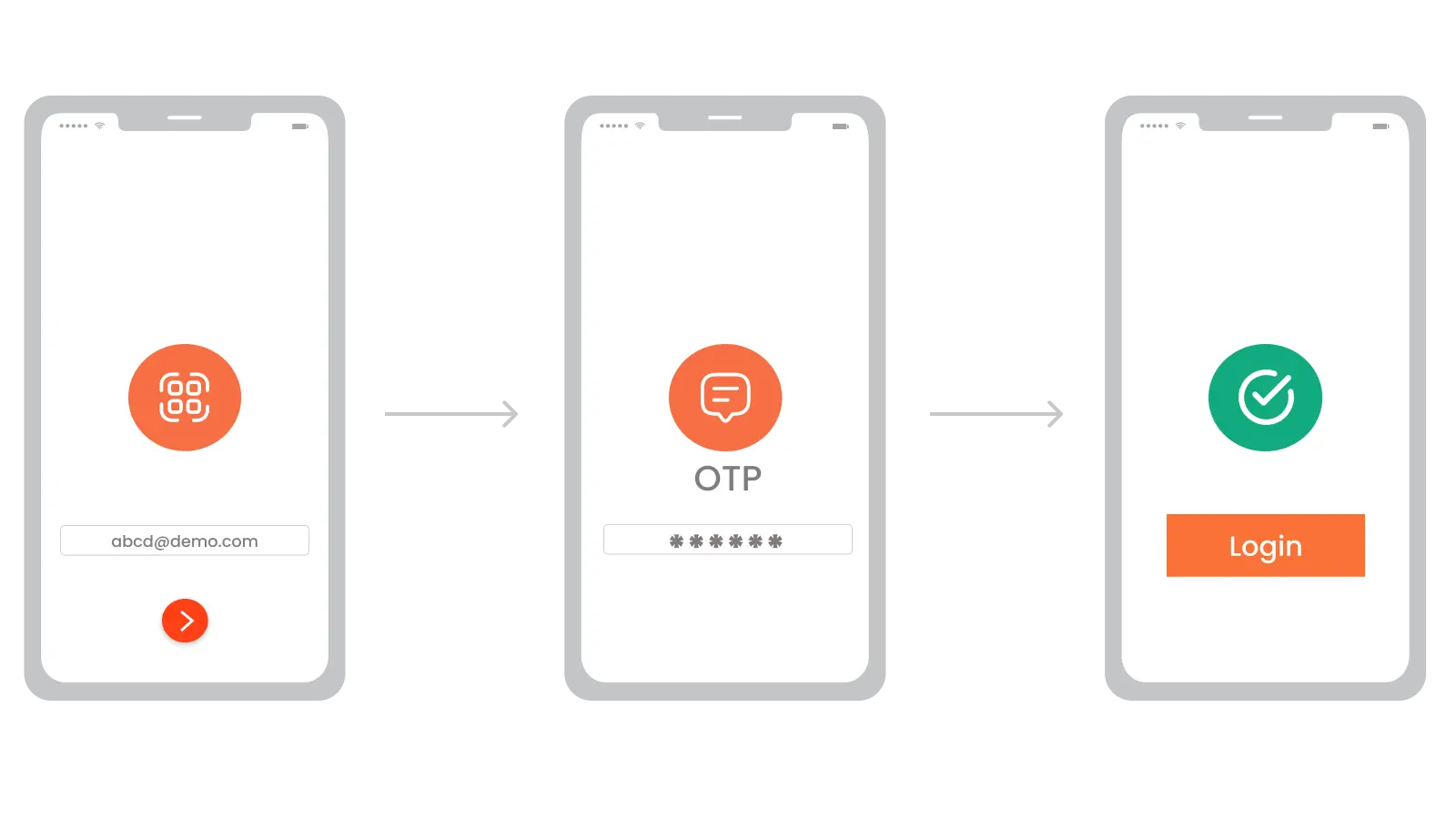
The user registers their device (e.g., smartphone) or sets up biometric data with miniOrange.
When logging in, the user selects passwordless authentication.
miniOrange sends a verification method based on the user's setup, such as:
miniOrange verifies the authentication response.
If the response is valid, miniOrange grants access; otherwise, access is denied.
Identity solutions from miniOrange can be easily deployed in your organization's existing environment.
Amplify productivity and take away the login hassles by securing accounts, resources, and devices with the best passwordless authentication solutions.
Authentication is done via a TOTP code generated on Authenticator apps (Google/Microsoft/Authy) or through a push notification via miniOrange Authenticator.
Using their existing social media account (Facebook, Instagram, etc.) credentials, users can seamlessly login and gain access.
Users enter their email into the login box instead of using their password. They will receive an email with a login link or Magic link to access the account.
Using FIDO2 security keys, users can easily authenticate via passwordless login. FIDO2 is a more secure passwordless login method.
Individuals’ physical attributes, such as fingerprints and retina scans, are studied and saved in a database, and the same data is confirmed during user authentication.
The end-user will receive a one-time code via SMS/Email. After entering this code, the user will be authenticated in the application.
Uses MFA like biometrics, OTPs, and tokens to prevent fraud, credential theft, and unauthorized access to sensitive financial data.
Simplifies logins at checkout using MFA, reducing cart abandonment and enhancing customer experience without complex passwords.
MFA ensures smooth employee onboarding and secure access to sensitive enterprise data, boosting user experience and information protection.
Secures EHRs with biometrics, OTPs, or magic links, protecting patient data while speeding up logins for clinicians and staff
Passwordless authentication solutions surpass traditional logins in security by removing passwords entirely, stopping attacks at the entry gates.
Without passwords to steal or guess, attackers lose their most commonly exploited entry point (weak or reused passwords), reducing large-scale data breaches.
Methods such as biometrics, authenticator apps, magic links, etc., ensure only the rightful user’s device can complete authentication, making phishing attacks practically ineffective.
With no password database to compromise and no credentials for attackers to reuse across sites, passwordless authentication neutralizes credential stuffing attempts.





I can't speak highly enough regarding miniOrange, I am totally satisfied with the process and results in every regard.
5.0

Awesome tech service, Awesome product. Overall Awesome people. This solution is very simple and easy to implement
5.0
Protect all Active Directory logins with MFA Security. Prevent unauthorized access to all servers by enabling MFA.
Secure your Windows RDP logons, RD Gateway & SSH logins with Multi-Factor Authentication.
Enable MFA on your VPN connections Like Fortinet, Cisco, SonicWall, PaloAlto, etc.
Prevent unauthorized access to OWA (Outlook on the Web) & RD Web connections.
Enable SSO/MFA for all Office 365 apps on the cloud (Supporting SAML, OAuth, JWT, etc.)
Secure your Virtual Desktop Infrastructure (VDI) (like Citrix, VMWare, etc.) with MFA solution.
