Today, the internet hosts more than 1.98 billion websites, and nearly one-third of businesses depend entirely on digital platforms to function. This incredible growth creates new opportunities for organizations, but it also gives hackers a wider playing field.
Cybercriminals scan for weak spots and attack vulnerable websites everywhere, regardless of industry or size. They use anything from phishing schemes and DDoS attacks to automated bots, exploiting any security gaps they find. Implementing phishing-resistant MFA adds an additional layer of protection by preventing attackers from gaining access even if credentials are stolen through phishing attempts.
That’s why website protection must be a top priority. miniOrange offers 16 practical security tips designed to keep hackers out and safeguard your website. You can put these recommendations into practice and significantly lower your risk of cyber threats.
What Are Hackers Trying to Get on Your Website?
At first glance, it might seem like hackers are just out to cause chaos. Some are. But most have a clear goal. They're after something valuable: data, money, control, or the means to cause disruption. The better you understand what they’re targeting, the better your chances of staying ahead.
Sensitive Personal & Customer Data
Nearly every website stores some kind of user data. Could be email addresses or payment info. In some cases, full names, home addresses, or login credentials. Even modest sites can hold more than you’d expect.
Take an online store. It probably keeps customer profiles, shipping details, and saved card numbers. A membership platform might hold private messages or encrypted passwords. Hackers know how to pull value from all of it. They resell it, use it to impersonate people, or launch highly targeted scams.
Administrative Access to Your Website’s Backend
If a hacker gets into your admin panel, they’re in control. They can edit your content, insert malicious scripts, lock you out, or quietly redirect visitors to scam sites.
None of this takes long. One quick change to your homepage, and suddenly you're hosting a phishing operation. Fixing the damage is hard enough. Rebuilding trust after something like that is even more difficult.
Illegal Usage of Website Resources & Bandwidth
Sometimes the hacker isn’t after your audience or your data. They want your infrastructure. Once inside, they might use your server to send spam, store illegal files, or launch attacks on other websites.
You might not notice right away. But your site starts to lag. Your hosting bill spikes. Eventually, search engines may blacklist your domain. All because someone used your site as a tool without your knowledge.
Direct Financial Exploitation
If your website handles payments, attackers may go after transaction data or try to skim money directly. Others take a more aggressive approach. They install ransomware, encrypt your entire site, and demand payment to unlock it.
This is no longer reserved for high-profile corporations. In fact, small and medium businesses are more frequently targeted because they’re less likely to have mature incident response protocols in place.
Why is Website Security Important?
Security shapes how a business runs. Not just in the background, but at every level, from customer experience to legal compliance to operational continuity. It’s less about “stopping hackers” and more about preserving control over your systems and your reputation.
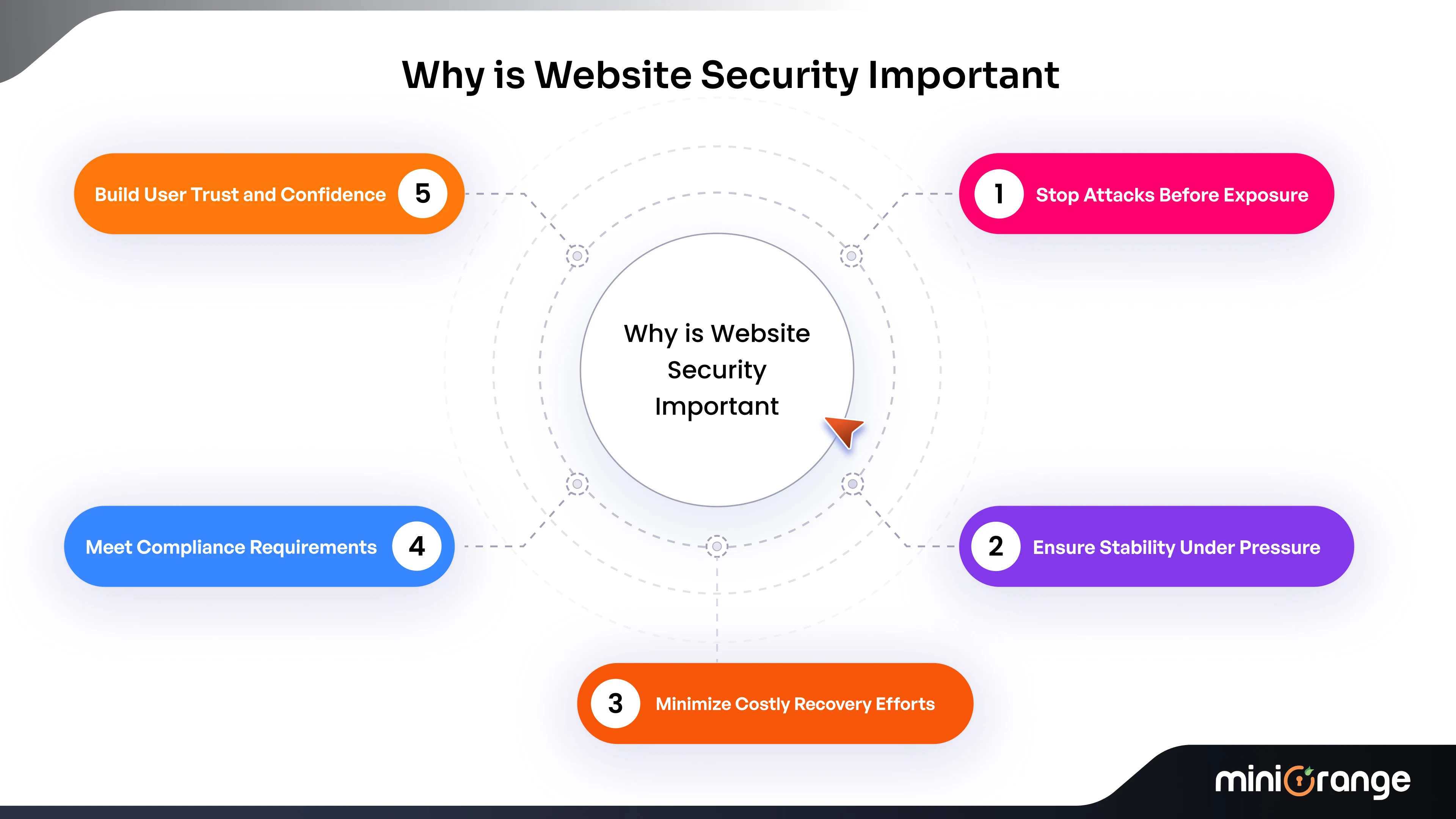
Here’s what robust security architecture actually enables:
- Containment Before Exposure: Strong defensive layers reduce the window of opportunity. Attacks are intercepted early, before data is exposed or services are disrupted.
- Stability Under Pressure: A secure system resists degradation. That means no unexplained crashes, slowdowns, or disappearing data during peak hours.
- Reduced Recovery Overhead: Prevention costs money, yes. But response and recovery cost far more, not just financially but in time, credibility, and regulatory risk.
- Standards Alignment: Whether you're under GDPR, CCPA, HIPAA, or PCI DSS, security is central to compliance. Falling short puts more than just customer data at risk.
- Trust That Isn’t Performative: Users don't always understand your backend architecture, but they recognize reliability. A secure site doesn't just function better. It feels better to use.
By prioritizing website security, you create a foundation for long-term success, one that keeps your business, your customers, and your reputation safe.
16 Critical Ways to Secure Your Website

If you're looking for how to protect your website from hackers, these 16 steps cover the most important areas to focus on for better security.
1. Regularly Update Your Website and Software
When systems fall behind, vulnerabilities tend to accumulate quietly. Hackers know this and often rely on outdated components to find a way in. Content management systems, plugins, themes, and external libraries all need regular attention. Apply security patches without delay. If you inherit a legacy stack, review it for abandoned code. Static components can still introduce dynamic risk.
2. Implement a Strong Password Policy
Weak passwords are a liability regardless of how sophisticated the rest of your stack may be. Don’t assume users will choose strong credentials without being required to. Define clear password complexity rules. Block obvious or previously compromised combinations. For admin-level access, raise the bar higher. Wherever possible, back up password enforcement with session management policies that log out idle users and prevent re-use of credentials across roles.
3. Install SSL and Harden the Application Layer
SSL certificates are now a baseline expectation for any public-facing site. They provide encrypted transport, but the protection stops there unless you add more controls. Application-layer firewalls and behavioral security plugins can catch patterns that indicate a breach attempt. Monitor login activity, limit failed attempts, and block traffic from known malicious IP ranges. Encryption is one part of the picture. The rest comes from active monitoring and defensive depth.
4. Perform Frequent User Access Reviews
Over time, access lists grow bloated. Contributors leave. Freelancers wrap projects. Developers rotate in and out. Every account that remains active creates an opportunity for misuse or compromise. Set a fixed cadence for access reviews. Monthly or quarterly is usually sufficient. Remove stale accounts and reassess roles. For sensitive environments, introduce the principle of least privilege and apply it without exception.
5. Enable Advanced Authentication Methods
Authentication refers to the process of confirming that a user is who they say they are. Going beyond a simple password, advanced methods like the miniOrange MFA methods add another layer of security by requiring a second form of verification, such as a code sent to your phone. For example, if an employee’s password is compromised, MFA ensures the attacker can’t log in without the extra verification step.
6. Always Use HTTPS Protocol
HTTPS should apply to every page, not just login forms or payment portals. Serving content securely improves user trust, helps with search engine ranking, and protects session data in transit. Configure your server to redirect all HTTP requests to HTTPS. Add a strict transport security (HSTS) header so browsers remember to enforce the encrypted connection on future visits.
7. Be Wary of Instructions in Suspicious Emails
Most compromises involving email begin with trust. A message arrives that looks familiar or urgent, asking you to reset a password, update a plugin, or click a link that points somewhere it shouldn’t. These attacks aren’t new, but they continue to work. Never act on unexpected email requests without independent confirmation. If a message claims to be from your hosting provider or admin team, contact them directly through verified channels before you respond.
8. Manage Uploaded Content Carefully
Allowing users to upload files introduces significant risk unless tightly controlled. Malicious actors often attempt to disguise executable code inside images, PDFs, or other file types. Limit what types of files are accepted. Validate MIME types server-side. Store uploads in directories that cannot be executed by the web server. Run malware scans before any file becomes accessible. These measures won’t eliminate the risk entirely, but they will reduce exposure and improve your ability to respond quickly if something slips through.
9. Maintain Regular Website Backups
Eventually, something will go wrong. When it does, having a recent backup that actually works can save you a lot of time and money. Don’t just back up once and forget about it. Automate the process. Back up both the site files and the database. Store copies off the server, ideally in a secure cloud location or offline system you can trust. And actually test your backups now and then. Too many companies don’t realize theirs are broken until it’s too late.
10. Conduct Daily Malware Scans
Malware doesn’t usually show up with sirens and flashing lights. A lot of it hides quietly, changes little things, and spreads slowly. You won’t notice it until your search rankings tank or users start getting warnings. Daily scans are not overkill. Set them up and let them run in the background. Good tools will flag abrupt changes, strange code, or file behavior that doesn’t look normal. You want to catch this stuff early, not when your site has already been flagged or blacklisted.
11. Activate Two-Factor Authentication (2FA)
If someone guesses or steals your password, that should not be enough to get in. Two-factor authentication (2FA) adds a simple but powerful layer of protection. A six-digit code from your phone or a hardware token can stop most attacks cold. Use it for anything important: admin panels, hosting accounts, database access. Try to avoid SMS if you can, since it's easier to compromise. An app-based method or physical device is better.
Find Out What Sets 2FA Apart from MFA
12. Select Trusted Web Hosting Providers
Your host is more than just where your files live. It’s part of your security setup, whether you realize it or not. A weak host means weak isolation, slow patching, and support that disappears when things go wrong. Look for providers that talk openly about how they handle security. Things like regular software updates, isolated environments, DDoS mitigation, and responsive support are requirements. If a host seems vague or too good to be true, keep looking.
13. Configure Strict File Permissions
Bad file permissions can ruin everything. If directories are writable when they shouldn’t be, attackers can drop malicious code into your site with almost no resistance. You don’t need to lock everything down blindly, but you do need to be intentional. Scripts should only run where they’re supposed to. Upload directories should never be executable. Review your settings regularly, especially after big updates or plugin installs. If something doesn’t need write access, take it away.
14. Schedule Regular Security Testing
Security tools are useful, but they’re not a guarantee. If you haven’t tested your site under pressure, you don’t really know how well it holds up. Run vulnerability scans regularly to catch common issues. Go further and schedule actual penetration tests. External testers will find things your team probably missed. When they send you a report, fix what’s in it. Don’t sit on the results and assume it’s fine just because no one has breached the website yet.
15. Leverage Dedicated Website Security Tools
A decent security plugin can stop some of the obvious stuff. A good one goes further. It watches traffic patterns, logs events, blocks brute force attempts, and alerts you when something odd is happening. Choose tools that give you visibility into what’s going on under the hood, not just surface-level reporting. Set aside time to review the logs. These tools are most useful when you’re actually paying attention to what they’re telling you.
16. Limit Plugins to Only What You Need
Plugins are useful, but each one adds more code, complexity, and potential vulnerabilities. If you don’t need it, remove it. Don’t just deactivate it, uninstall it completely. Stick to well-supported plugins from developers you can research. If the author doesn’t update regularly or you can’t find their support docs, that’s a red flag. Review your plugins a few times a year. Get rid of anything unused. The simpler your setup, the harder it is to break.
How to Secure Your Website from Common Hacking Methods

Before you can protect a site, you need to understand how people try to break into it. Most attackers don’t use fancy, futuristic techniques. They go for what works, and what works is often surprisingly simple. These are some of the more common hacking methods, and what you can actually do to stop them.
SQL Injection
This one’s been around forever, and it still works on plenty of websites. An attacker finds a field such as a search box, login form, or contact input, and slips in a command disguised as user input. If the backend isn’t properly handling that input, the database runs the command. That might mean revealing user data or taking over the entire site.
The fix isn’t complicated. Use parameterized queries. Sanitize input properly. Avoid building SQL queries with raw user data. And keep your stack updated. Vulnerabilities often get patched quickly, but only if you're actually applying the patches.
Cross-Site Scripting (XSS)
XSS is when someone injects a script into a page, and that script runs in another user’s browser. It usually shows up in comment sections, form fields, and any place user-generated content is displayed. A clever attacker can steal cookies, hijack sessions, or even rewrite part of the interface to trick people into giving up more information.
To prevent it, filter and escape user input, especially anything that ends up rendered in the browser. HTML, JavaScript, even URLs. If your framework provides built-in protections, use them as intended. Don’t bypass them just because they make your code a bit longer.
Brute Force Attacks
This isn’t sophisticated, but hackers still use brute force attacks to break into websites. Automated bots try every password combination they can until one hits. If your site allows unlimited attempts, or if admin accounts are using simple, predictable passwords, they’ll get in eventually.
Start by enforcing strong password rules. Add login attempt limits and require multi-factor authentication wherever possible. You don’t need to stop the attacker from guessing. You just need to make sure guessing never works.
DDoS Attacks
DDoS is less about getting in and more about taking you offline. The attacker floods your server with traffic until it buckles, or until real users can’t load anything. Most small and mid-size websites don’t have the resources to handle a full-scale DDoS on their own.
That’s where your host and DNS provider come in. Choose infrastructure that includes mitigation tools, not just uptime promises. And if your site is high-visibility or mission-critical, invest in proper DDoS protection. Because the cost of downtime can add up fast.
Zero-Day Vulnerabilities
A zero-day is a flaw in software that no one knows about yet, except the attacker. Since there's no fix available when they strike, these exploits are hard to guard against directly.
But you can still reduce risk. Don’t run outdated software. Limit what each user or process can do. Use monitoring tools that flag suspicious behavior. And stay plugged in to security advisories. The sooner a fix comes out, the sooner you should be applying it.
Explore the Top Cybersecurity Threats You Should Know
Best Practices to Stay Hacking Proof
Staying safe online doesn’t have to be complicated, small, smart habits make a big difference. Here’s how you can help your team and your business keep threats out.
Train Everyone on Cyber Hygiene
Get everyone involved by sharing easy tips to spot scams and keep information secure. Regular, fun reminders and quick training sessions help everyone play their part in helping prevent cyber attacks.
Use a Handy Security Checklist
A simple checklist keeps your security game strong. Jot down the basics, update apps, check who has access, and keep backups current. Checking off these steps regularly means you’re always ready for whatever comes your way.
Test Your Security Defenses Often
Don’t wait for trouble to find you. Try out your security with quick tests and drills. Spotting weak spots early means you can fix them fast and stay one step ahead of hackers.
How miniOrange Helps Secure Your Website
Keeping your website safe is a top priority for every organization. As your trusted security software solution partner, miniOrange offers powerful IAM solutions that manage user access, protect sensitive data, and guard against common cybersecurity risks.
Prevent Hacking with Multi-Factor Authentication (MFA)
miniOrange MFA solution improves your login experience by demanding more than just a password. In addition to their usual credentials, users must also complete a second step, such as entering a code from their phone, responding to a notification, or using a fingerprint. Because of this extra layer, unauthorized access becomes much more difficult. As online cybersecurity threats continue to rise, the importance of MFA grows even stronger. To further enhance security, miniOrange Adaptive MFA monitors user activity and only requests additional verification when unusual behavior is detected.
Ensure Secure Login Access with Single Sign-On (SSO)
miniOrange SSO simplifies access for users by allowing them to log in once and reach all connected platforms. As a result, users no longer need to remember multiple passwords, which reduces the risk of password-related issues. In turn, IT teams gain better oversight of login activity. Ultimately, users benefit from a smoother and more secure experience.
Protect Admin & Critical Systems with PAM
To ensure sensitive website data is also well protected, miniOrange PAM helps you control and monitor access to important systems. With this solution, you can assign specific roles, track user actions, and restrict high-level access to authorized personnel only.
If you are ready to step up your security game, start your free 30-day trial with miniOrange and see how easy it can be to protect your website with smarter cybersecurity solutions.
Conclusion
Staying secure online doesn’t always mean adding more steps. It means choosing smarter ones. IAM tools like biometric authentication and push notifications help verify users quickly and safely. You don’t have to stick to one method either. With different types of MFA, you can choose what fits best, whether that’s a fingerprint, a one-time code, or a simple tap on a phone.
Security should feel like part of the experience, not an obstacle. When done right, it protects your website and keeps things smooth for the people who matter most, your users. If you want to learn more about the best website security options for your business, talk to our experts.
FAQs
What Protects Websites From Hackers?
Strong passwords, secure hosting, regular updates, and firewalls help. Adding MFA for admin access also lowers the chances of unauthorized entry.
How Do I Secure My Website?
Audit your plugins and themes, remove anything unused, keep everything updated, and limit access to only those who need it. Use MFA for extra protection where it matters most.
Is HTTPS Enough To Protect My Site?
No. HTTPS protects data during transmission, but not your login pages or server-side vulnerabilities. It's important to pair it with other security measures like access control and regular monitoring.
What Website Gets Hacked the Most?
Sites using outdated software or weak login protection are frequent targets. WordPress is often affected due to its large user base and plugin exposure.
What Are The Top Tools To Secure Your Website?
Look into malware scanners, backup tools, firewalls, and access security options like SSO for smoother logins or PAM for sensitive account protection.



Leave a Comment