Identity-based attacks have become the most frequent gateway for cybercriminals to breach enterprise defenses, exploiting user credentials and digital identities instead of traditional software flaws. As businesses expand into the cloud and adopt hybrid IT, every identity, whether human or machine, becomes a potential entry point for attackers, making robust identity security more crucial than ever.
With miniOrange, learn the definition, types, the greater impact, and so much more in detail.
What Are Identity Threats?
Identity threats are security challenges or malicious tactics targeting digital identities, such as usernames, passwords, session tokens, and access permissions. Rather than exploiting vulnerabilities in software or devices, these threats focus on the misuse or compromise of legitimate access credentials to infiltrate systems undetected.
Types of Identity Threats
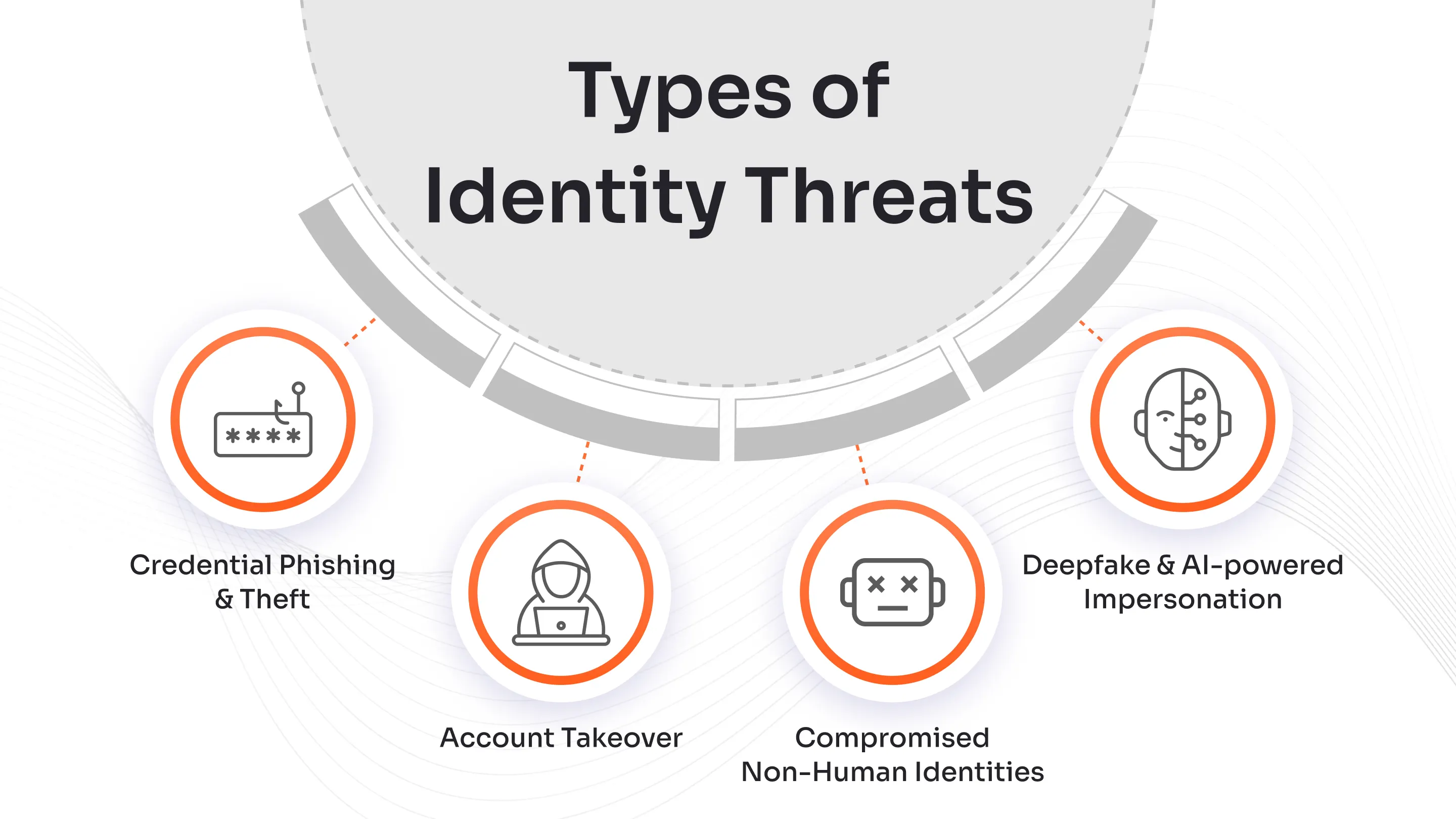
Credential Phishing and Theft: Using deceptive emails, fake websites, or social engineering to harvest login details and authentication codes.
Account Takeover: Hijacking user or service accounts via stolen or leaked credentials, often obtained from phishing or dark web sources.
Compromised Non-Human Identities: Targeting service accounts, bots, or application keys and tokens, which often have elevated or persistent privileges.
Deepfake and AI-powered Impersonation: Leveraging voice cloning or AI-generated videos to mimic executives or trusted contacts, deceiving employees and security systems.
Human vs. Non-Human Identities
Human Identities: Include individual users, employees, third-party contractors, and partners authenticated through usernames, passwords, MFA, or biometrics.
Non-Human Identities: Refer to system accounts, API keys, machine identities, bots, and applications, which play critical roles in automation and cloud integrations and are often neglected in security best practices.
Why Identity Threats Are Critical
As businesses accelerate digital modernization, the attack surface expands with every cloud workload, SaaS app, or automated API. Identity threats can bypass perimeter-based defenses, granting attackers deep access and making detection challenging. Poorly managed identities are now frequently the weakest link, allowing threat actors into enterprise networks.
What Is an Identity-Based Attack?
An identity-based attack is a cyberattack that leverages stolen, forged, or abused credentials to gain unauthorized access to data or systems. Rather than try to break through firewalls or exploit system vulnerabilities, attackers simply “log in” using credentials acquired from phishing, password reuse, credential stuffing, or more advanced tactics like pass-the-hash and golden ticket attacks.
How They Work
Attackers begin by targeting user identities, such as login credentials, to break into a system. They commonly use methods like phishing to trick users into revealing their usernames and passwords or purchase stolen credentials from dark web markets and data breaches.
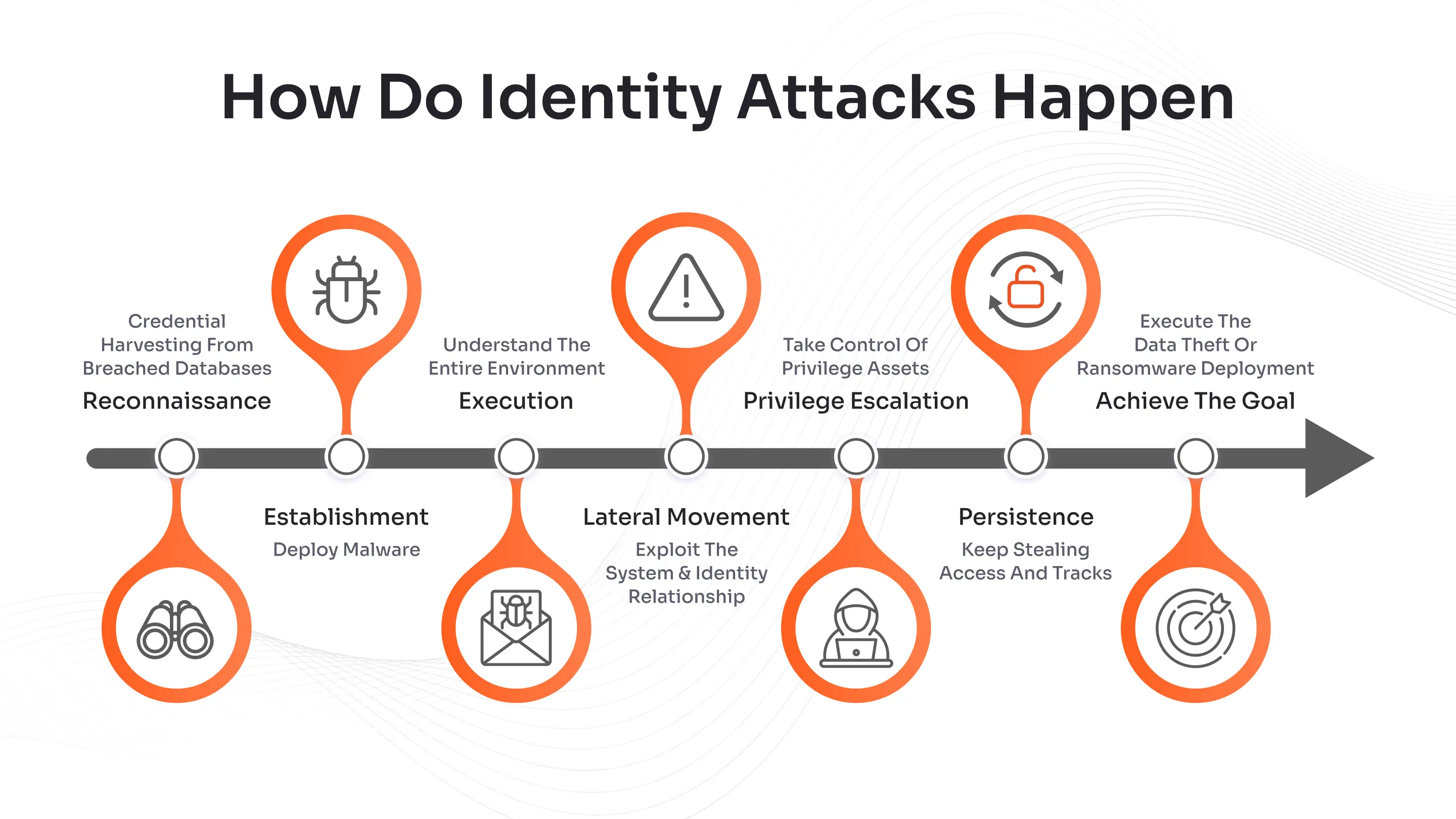
The attack typically follows a multi-stage process known as the Identity Attack Chain:
Initial Compromise: Attackers obtain valid credentials through phishing, social engineering, reconnaissance, or credential harvesting from breached databases.
Establishment and Execution: Once inside, they deploy malware or execute code to establish a foothold and gain deeper visibility into the environment.
Lateral Movement and Privilege Escalation: Attackers exploit relationships between systems and identities to move across the network, accessing privileged accounts and elevating permissions until they control critical assets.
Persistence and Action on Objectives: With elevated privileges, attackers can cover their tracks, maintain long-term access, and execute their goals, whether data theft, ransomware deployment, or espionage.
Key Objectives of Attackers
Impersonation of Legitimate Users Attackers use compromised credentials to assume the identity of employees, executives, or partners, blending in with legitimate users to avoid detection.
Privilege Escalation They exploit permission gaps, misconfigured IAM policies, or chained privileges to elevate their access, moving from basic accounts to admin or root-level control, sometimes via overlooked non-human accounts or service tokens.
Lateral Movement
Once inside, adversaries move through cloud or networked environments, hopping from one compromised account or system to another to reach sensitive data, critical infrastructure, or backup systems.
Stealth and Persistence
Leveraging valid credentials and normal access patterns, attackers remain undetected as they execute their objectives, including data theft, ransomware deployment, or supply chain attacks.
Disabling Security Controls
Attackers may target IAM systems themselves, disable MFA, tamper with logging, or compromise backup credentials, increasing the scope and impact of their attack.
Why These Attacks Are Hard to Detect
Identity-based attacks are stealthy because activities originate from "authorized" accounts with valid credentials, making suspicious behavior appear legitimate. Traditional security tools (like firewalls and antivirus software) are not built to spot malicious activity disguised as normal user actions. This makes robust IAM controls, activity monitoring, and behavioral analytics essential for modern defense.
Common Types of Identity-Based Attacks
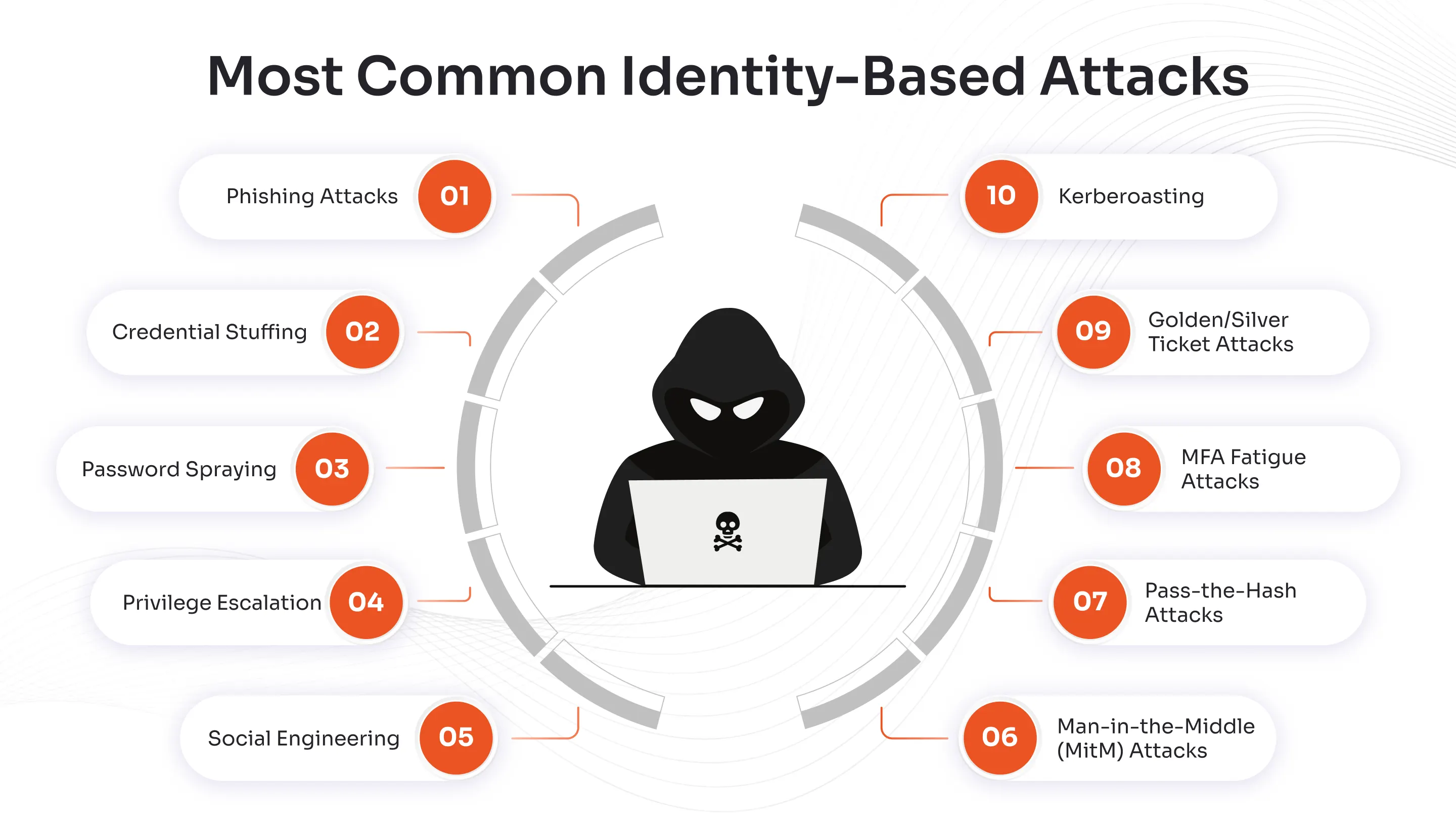
Identity-based attacks come in many forms, each exploiting weaknesses in authentication, access management, or human behavior. Understanding these attack methods is essential for building effective defense strategies.
Phishing
Phishing attacks remain one of the most prevalent and effective identity-based attack vectors. Attackers use deceptive emails, fake websites, or messages impersonating trusted organizations to trick users into revealing login credentials, personal information, or financial data.
These campaigns often leverage urgency or fear, such as warnings about account suspension or security breaches, to manipulate victims into acting without scrutiny. Modern phishing has evolved to include spear-phishing (highly targeted messages) and vishing (voice phishing), making detection increasingly difficult.
Credential Stuffing
Credential stuffing is a brute-force technique that uses lists of stolen username-password pairs obtained from previous data breaches to automate login attempts across multiple websites and services. Attackers exploit users' tendency to reuse passwords across platforms, allowing them to hijack accounts at scale with minimal effort.
Automated bots can test thousands of credentials per minute, making this a highly efficient attack method. Organizations with weak account monitoring are particularly vulnerable to credential stuffing campaigns.
Password Spraying
Unlike brute-force attacks that target a single account with many passwords, password spraying takes the opposite approach. Attackers systematically try a few common or default passwords, such as "Password123" or "Welcome2024", against numerous user accounts across an organization.
This method avoids triggering account lockout policies and flies under the radar of traditional security systems. By exploiting weak password policies and poor password hygiene, attackers can gain initial access without raising alarms.
Privilege Escalation
After compromising a low-level account, attackers don't stop there. Privilege escalation involves exploiting system misconfigurations, software vulnerabilities, or permission gaps to gain elevated access rights.
The goal is to move from a standard user account to administrative or root-level control, granting access to sensitive resources and the ability to cause greater damage. Privilege escalation can be vertical (moving to higher privilege levels) or horizontal (accessing accounts with similar privileges but different permissions). This technique is often combined with other attacks like Pass-the-Hash or Kerberoasting.
Social Engineering
Social engineering attacks manipulate human emotions like fear, urgency, greed, or curiosity to deceive employees into divulging sensitive information, clicking on malicious links, or performing actions that compromise security.
Unlike technical exploits, social engineering targets the human element, which is often the weakest link in security chains. These attacks can take many forms, including pretexting (creating false scenarios), baiting (offering something enticing), and tailgating (physically following someone into restricted areas). Social engineering often serves as the foundation for other identity-based attacks, such as obtaining initial credentials for further exploitation.
Man-in-the-Middle (MitM) Attacks
In a Man-in-the-Middle attack, the attacker secretly intercepts and monitors communication between two parties, typically on unsecured or compromised networks, to steal sensitive data like login credentials, session tokens, or financial information without either party's knowledge.
MitM attacks commonly occur on public Wi-Fi networks, where attackers can position themselves between users and legitimate services. Once intercepted, credentials can be used immediately or stored for later attacks. Session hijacking, where attackers steal active session tokens, is a common variant of MitM attacks.
Pass-the-Hash Attacks
Pass-the-Hash is a sophisticated technique where attackers steal cryptographic hashes of user passwords stored in system memory and reuse them to authenticate on other networked systems without needing to crack the actual plaintext password.
This enables lateral movement within Windows-based environments, allowing attackers to access multiple systems using a single compromised credential. Since the hash itself serves as proof of identity, defenders must implement additional protections beyond password complexity.
MFA Fatigue Attacks
Even multi-factor authentication isn't immune to attack. In MFA fatigue attacks, cybercriminals bombard a user's device with repeated multi-factor authentication prompts, banking on user frustration or confusion to approve one authentication request inadvertently.
This social engineering technique exploits human psychology rather than technical vulnerabilities. Attackers typically already possess valid credentials and simply need the victim to approve the second factor. Some sophisticated variants include calling the victim while sending prompts to increase pressure.
Golden/Silver Ticket Attacks
These advanced attacks involve compromising core authentication systems like Microsoft Active Directory to forge Kerberos authentication tokens. Golden Ticket attacks target the domain's Key Distribution Center to create tickets granting extensive domain-wide access, while Silver Ticket attacks forge service-specific tickets.
Both methods grant attackers access without needing actual user passwords and enable long-term persistence within networks. These attacks are particularly dangerous because they allow adversaries to maintain access even after password resets.
Kerberoasting
Kerberoasting is a technique that targets service account credentials within Active Directory environments. Attackers request encrypted service tickets from Active Directory for accounts with Service Principal Names (SPNs), then crack these tickets offline using brute-force methods to obtain plaintext service account passwords. Since service accounts often have elevated privileges and rarely have their passwords changed, they make attractive targets for patient adversaries.
MFA Bypass Attacks
As multi-factor authentication becomes more widespread, attackers have developed sophisticated methods to circumvent these controls. MFA bypass attacks include exploiting session cookies, token theft, adversary-in-the-middle techniques, and social engineering that tricks users into approving fraudulent authentication requests.
Some attacks target implementation flaws in MFA systems themselves, while others exploit the gap between when authentication occurs and when sessions expire. These techniques undermine additional security layers that organizations rely on for protection.
Secure your systems against every type of cybersecurity attack with ease.
The Impact of Identity Attacks
The consequences of successful identity-based attacks are severe and wide-reaching:
Financial Loss: Organizations face direct costs from theft or fraud, along with substantial expenses from remediation, legal actions, and incident response.
Data Leaks: Attackers often exfiltrate sensitive customer, employee, or intellectual property data, causing compliance violations and loss of competitive advantage.
Regulatory Penalties: Breaches involving personal or regulated data trigger investigations and fines under laws like GDPR, HIPAA, and other industry mandates, escalating financial repercussions.
Reputational Damage: Loss of trust is immediate; customers, partners, and investors may lose confidence, impacting brand reputation and future business opportunities.
Operational Disruption: Attackers may disable critical systems, lock resources with ransomware, or sabotage infrastructure, leading to downtime, lost productivity, and impaired service delivery.
These impacts highlight why prioritizing identity security is now a central pillar of modern cybersecurity strategy.
Identity-Based Attack Prevention
Defending against identity-based attacks requires a multi-layered approach that focuses on the identity itself rather than just the network perimeter. Organizations must implement proactive controls like MFA software, continuous monitoring, and user education to build resilient defenses.
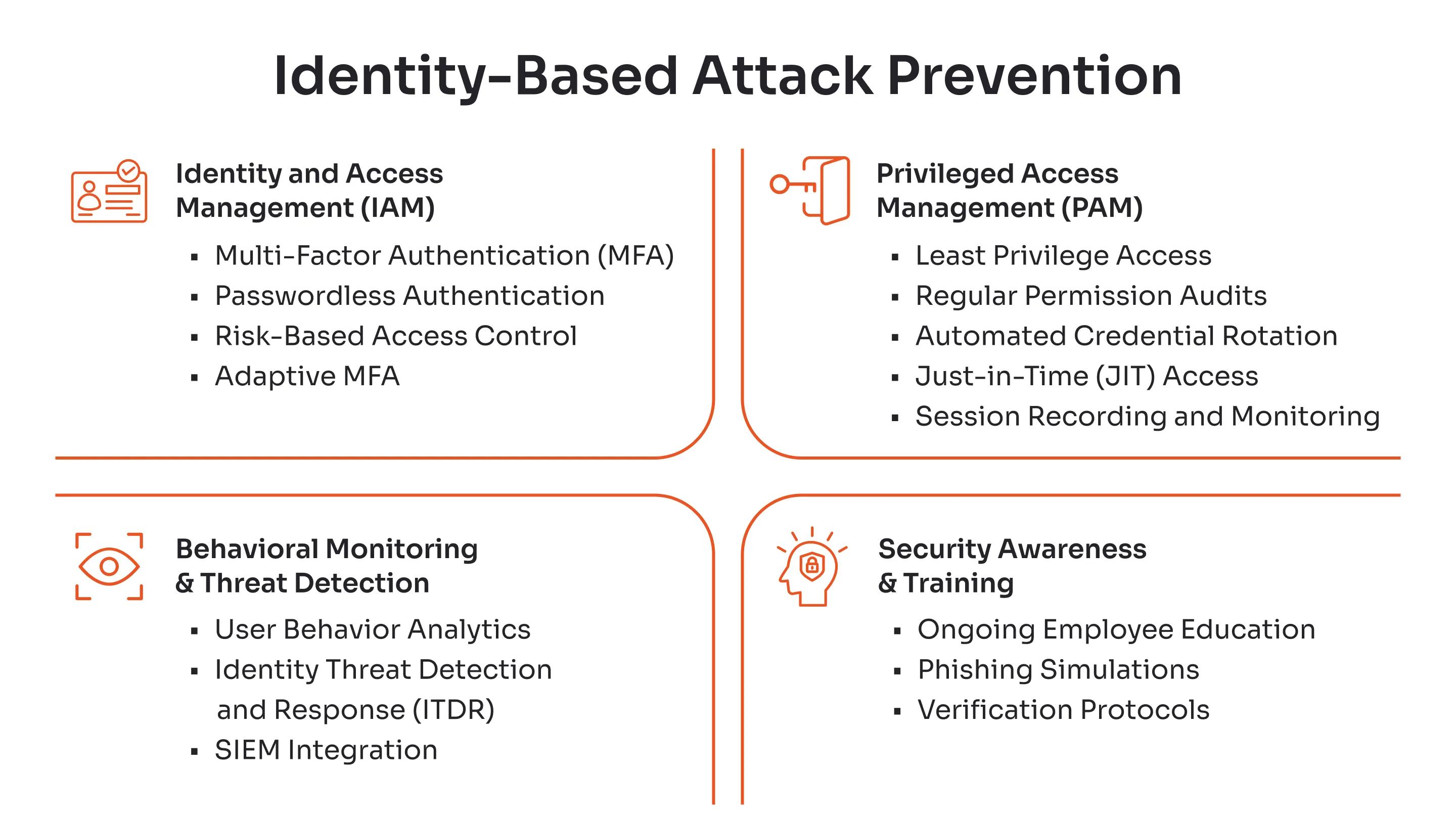
Strong Authentication Methods
Multi-Factor Authentication (MFA)
MFA significantly raises the bar for attackers by requiring a second form of verification beyond passwords. However, organizations should use resilient, phishing-resistant MFA options like authenticator apps, passkeys, or FIDO2 hardware security keys instead of less secure SMS-based codes, which are vulnerable to SIM swapping and interception.
Passwordless Authentication
Where possible, eliminate reliance on passwords entirely by using biometrics, passkeys, or WebAuthn standards. This removes the most common attack vector while improving user experience.
Risk-Based Conditional Access
Complement MFA with conditional access policies that evaluate sign-in requests using additional identity-driven signals like IP address location, device health status, and user behavior patterns. These adaptive policies can automatically block or challenge suspicious access attempts.
Zero Trust Architecture
Core Principles
The Zero Trust model operates on the principle of "never trust, always verify," requiring continuous authentication and authorization for every access request, regardless of location or network. This framework helps prevent lateral movement by enforcing context-aware access controls and requiring re-authentication for sensitive operations.
Zero Trust Network Access (ZTNA)
Transition from legacy remote access VPNs to ZTNA solutions for all remote connections. This ensures granular, policy-based access control and prevents unauthorized lateral movement.
Just-in-Time (JIT) Access
Implement JIT access elevation for high-sensitivity operations, requiring re-authentication and additional approval for privileged actions. This time-bound access minimizes the window of opportunity for attackers.
Access Control and Privilege Management
Least Privilege Access
Grant users the minimum necessary permissions to perform their job functions. This principle of least privilege (PoLP) limits lateral movement and contains the potential damage if an account is compromised.
Regular Permission Audits
Conduct automated, quarterly audits of user entitlements to verify least-privilege access, especially for service accounts and high-privilege roles. Remove unnecessary admin rights and visualize privilege sprawl using identity heatmaps.
Automated Credential Rotation
Implement automatic credential rotation for service accounts and API keys to reduce the risk of long-term credential compromise.
Privileged Access Management (PAM)
Secure Credential Storage
Protect sensitive credentials and API keys in dedicated key vaults. Scan code repositories regularly to detect hard-coded or mishandled secrets.
Session Recording and Monitoring
Record privileged sessions to maintain audit trails and detect suspicious activities in real time. PAM tools provide secure credential vaulting, session monitoring, and automated workflows that reduce the attack surface for critical accounts.
Behavioral Monitoring and Threat Detection
User Behavior Analytics
Use behavioral analytics and AI/ML tools to establish normal activity baselines and detect anomalies such as login attempts from unusual locations (impossible travel), access to resources a user doesn't typically use, or sudden privilege changes that may indicate account takeover.
Identity Threat Detection and Response (ITDR)
Deploy ITDR solutions to discover identity vulnerabilities and detect and respond to identity-based attacks in real time with automated remediation. These platforms provide continuous monitoring of identity systems and can automatically respond to threats.
SIEM Integration
Integrate IAM telemetry into security information and event management (SIEM) systems and threat detection platforms for comprehensive visibility across your security stack.
Password Security Best Practices
Strong Password Policies
While moving toward passwordless authentication, organizations still rely on passwords and should enforce robust policies. Encourage the use of long, unique passphrases (16+ characters) and password managers. Check credentials against known breach lists and enforce regular password updates for privileged accounts.
Account Lockout Mechanisms
Implement account lockout policies after multiple failed login attempts to defend against brute-force and password spraying attacks.
Security Awareness and Training
Ongoing Employee Education
The human element plays a vital role in the success of identity-based attacks, making employees the front line of defense. Provide ongoing cybersecurity awareness training to help employees recognize phishing attempts, social engineering tactics, and other identity-based threats.
Phishing Simulations
Run realistic attack simulations, including phishing messages via email and collaboration platforms like Microsoft Teams, to test employee readiness and reinforce training.
Verification Protocols
Train employees to verify unusual requests through independent communication channels, especially those involving sensitive data or financial transactions. Teach them never to provide passwords or codes over SMS or instant messaging.
Identity Threat Trends and Future Outlook
Identity-based attacks are growing in sophistication, making use of AI-powered phishing, deepfakes, and automated malware to evade detection and bypass traditional defenses. AI is now actively used by both attackers and defenders: adversaries automate credential theft and social engineering, while security teams apply AI for real-time anomaly detection and identity analytics. As the attack surface grows, continuous improvement in IAM architecture and policies is crucial to mitigate emerging threats.
Conclusion
Strong identity security is critical as attackers increasingly exploit credentials, machine identities, and human error. Organizations should prioritize robust authentication, Zero Trust, behavioral monitoring, and regular user training to defend against evolving identity-based threats. By dynamically refining Identity management controls and staying alert to new attack techniques, security teams can reduce risk, limit business impact, and protect valuable data assets.
FAQs
What is an identity-based attack?
An identity-based attack is when attackers steal or misuse user credentials like passwords or tokens to access systems. Instead of exploiting technical flaws, they act as legitimate users, making the attack harder to detect.
What is an example of an identity threat?
A common identity threat is phishing, where attackers trick people into giving up login details. Once they have the credentials, they can access accounts, gain privileges, and potentially compromise more systems.
What is the best way to protect your identity?
The best way to protect your identity is to use strong security controls like MFA, monitor account activity, and stay aware of phishing attempts. Keep passwords and security settings updated to reduce risk.




Leave a Comment