As the cyber threats increase at a rapid pace, the security and authentication flows should grow with it. Organizations can benefit from proactive authentication frameworks, which provide the right access to the right resources and the right person. This is where the AAA protocols, including RADIUS and TACACS+, hold the most advantage.
RADIUS and TACACS+ are both network authentication protocols, but they serve different purposes: RADIUS focuses on remote access authentication and accounting, while TACACS+ provides granular command-level authorization for network devices. The key difference lies in their approach.
In this guide, miniOrange will compare RADIUS and TACACS+, understand their approaches, explain their strengths, and help you choose the right protocol for your network.
What Are AAA Protocols?
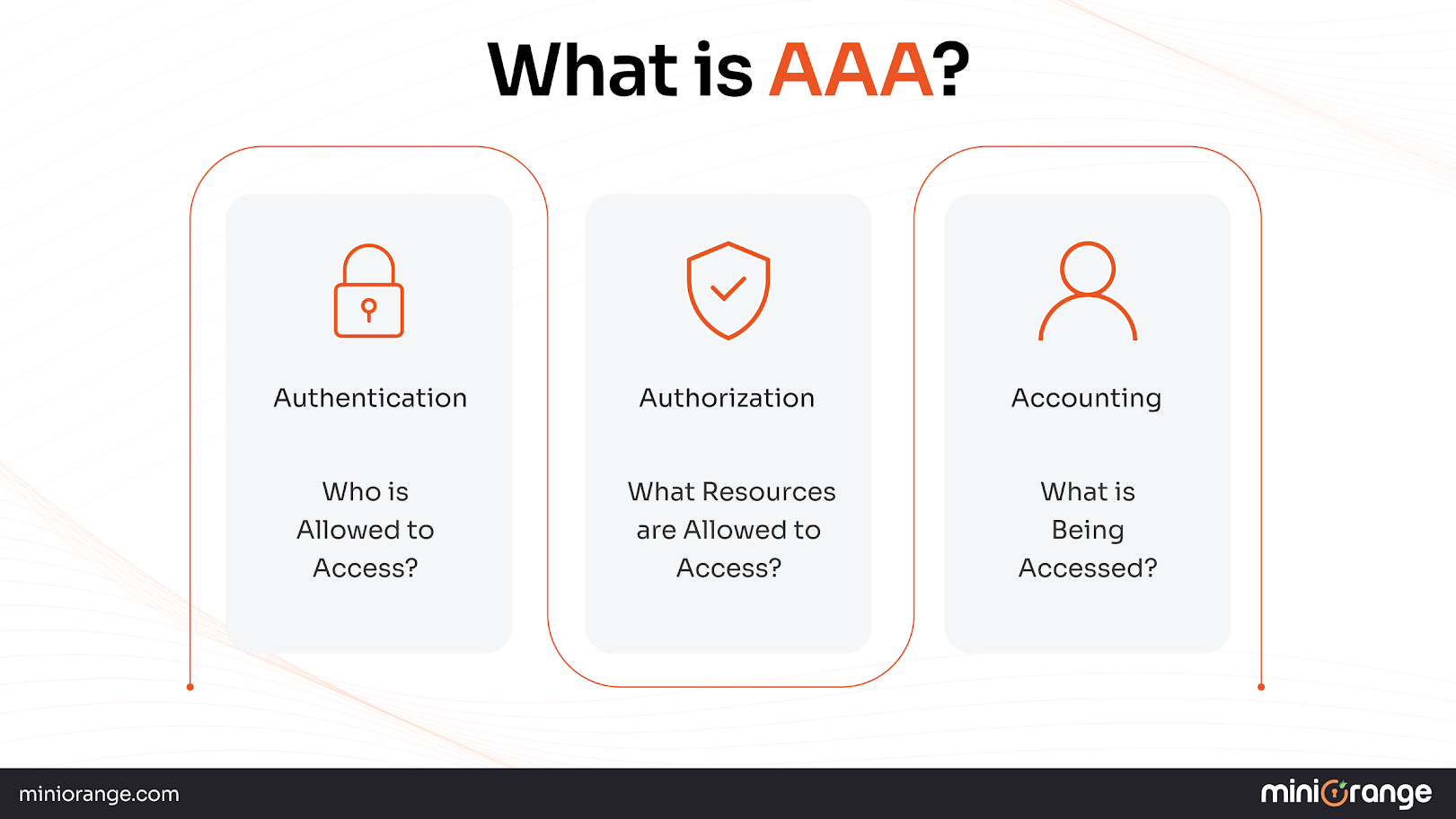
AAA protocols are security frameworks that govern network access through three fundamental processes: Authentication, Authorization, and Accounting. The three fundamental protocols, Authentication, Authorization & Accounting, have significant differences. These protocols ensure that only verified users can access network resources, define what they're permitted to do, and track their activities for security and compliance purposes.
The Three Pillars of AAA
Authentication - Verifies user identity through credentials like usernames, passwords, certificates, or multi-factor authentication before granting network access.
Authorization - Determines what authenticated users can access and which commands they can execute based on their roles and permissions.
Accounting- Logs user activities, session duration, and resource usage for auditing, billing, and compliance monitoring.
Why are AAA Protocols Essential for Enterprise Networks?
Modern enterprise networks rely on complex infrastructure, including routers, switches, firewalls, VPN gateways, and wireless access points. Without proper access control, these critical network devices become vulnerable to unauthorized access, configuration changes, and security breaches. AAA protocols provide centralized management of network access, ensuring that:
- Network administrators have appropriate privileges for their roles
- Device configurations remain secure from unauthorized modifications
- All network access attempts are properly logged and monitored
- Compliance requirements are met through detailed audit trails
- Remote access to network infrastructure is properly controlled
RADIUS and TACACS+ as AAA Protocols
Both RADIUS (Remote Authentication Dial-In User Service) and TACACS+ (Terminal Access Controller Access-Control System Plus) are widely adopted AAA protocols that provide these essential security functions. While they share the same AAA foundation, each protocol takes a different approach to implementing authentication, authorization, and accounting, making them suitable for different network scenarios and security requirements.
What is RADIUS?
RADIUS (Remote Authentication Dial-In User Service) is a networking protocol that provides centralized authentication, authorization, and accounting (AAA) management for users who connect and use network services.
Originally designed for dial-up connections, RADIUS has evolved into a standard AAA protocol used across enterprise networks to control access to routers, switches, wireless networks, VPNs, and other network infrastructure.
RADIUS operates as a client-server protocol where network access servers act as clients, forwarding authentication requests to a central RADIUS server that validates user credentials and defines access permissions.
How RADIUS Works?
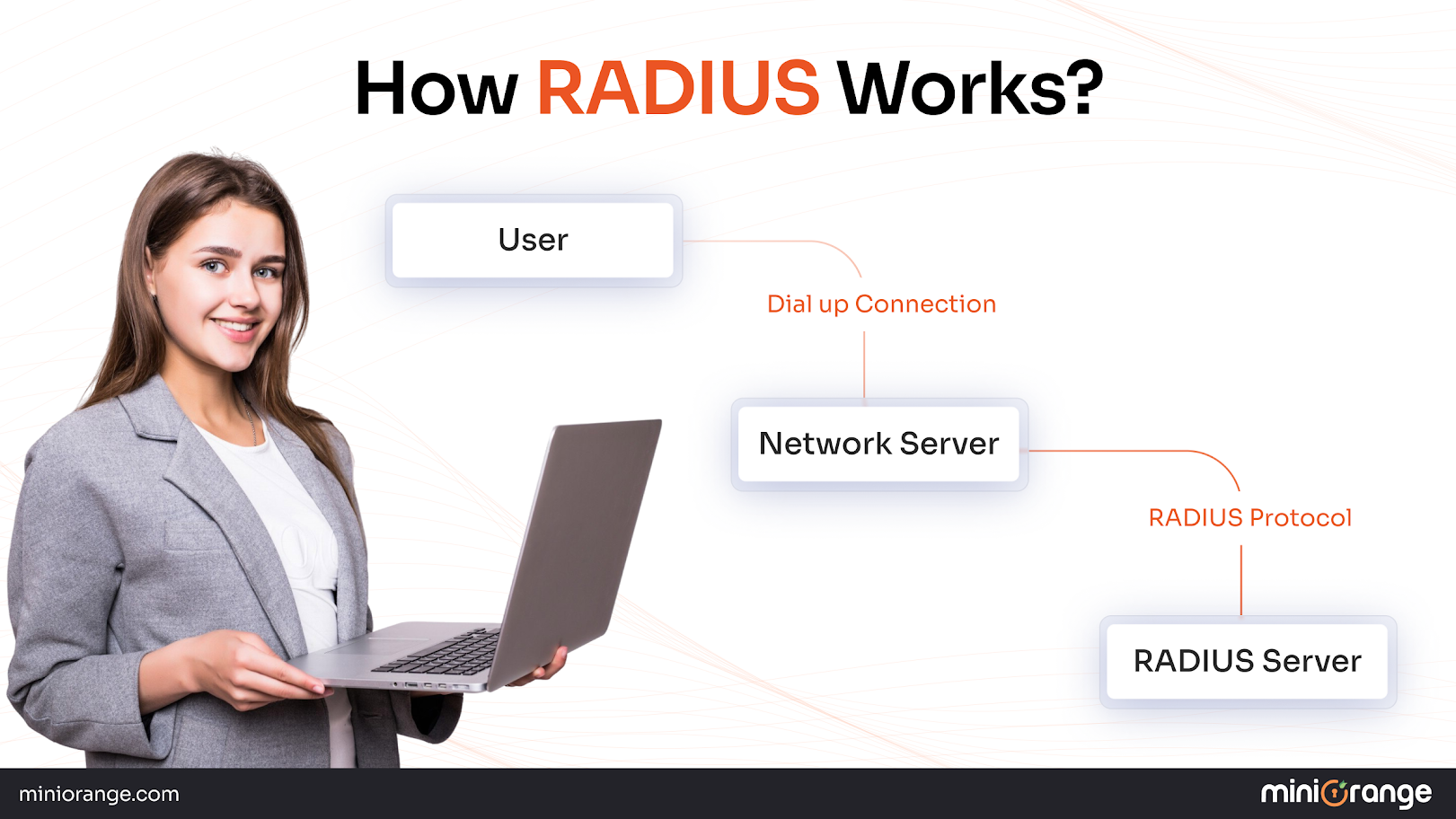
RADIUS follows a client-server model where network devices (NAS - Network Access Servers) act as RADIUS clients, forwarding authentication requests to a centralized RADIUS server. The protocol uses UDP (User Datagram Protocol) for communication, typically on ports 1812 for authentication and 1813 for accounting.
Security is maintained through shared secret encryption, where both the client and server use a pre-configured shared key to encrypt sensitive data like passwords. When a user attempts network access, the NAS sends an Access-Request packet to the RADIUS server, which responds with Accept, Reject, or Challenge messages based on the authentication outcome.
Key Features of RADIUS
- Centralized Authentication - Single point of user credential validation across multiple network devices and services
- Authorization Control - Defines user permissions and access levels through attribute-value pairs (AVPs)
- Comprehensive Accounting - Tracks user sessions, connection time, data usage, and network resource consumption
- High Scalability - Supports thousands of concurrent users and can be deployed across distributed network environments
- Vendor Interoperability- Standardized protocol works with equipment from multiple network hardware vendors
- Proxy Support - Can forward authentication requests to other RADIUS servers for distributed authentication
What is TACACS+ in Networking?
TACACS+ (Terminal Access Controller Access-Control System Plus) is a Cisco-developed AAA protocol designed specifically for network device administration and management. Unlike RADIUS, TACACS/TACACS+ authentication focuses primarily on providing granular administrative access control to network infrastructure equipment such as routers, switches, and firewalls.
TACACS+ separates AAA into distinct processes, allowing network administrators to have fine-grained control over what commands users can execute on network devices, making it ideal for securing network infrastructure management.
How TACACS+ Works?
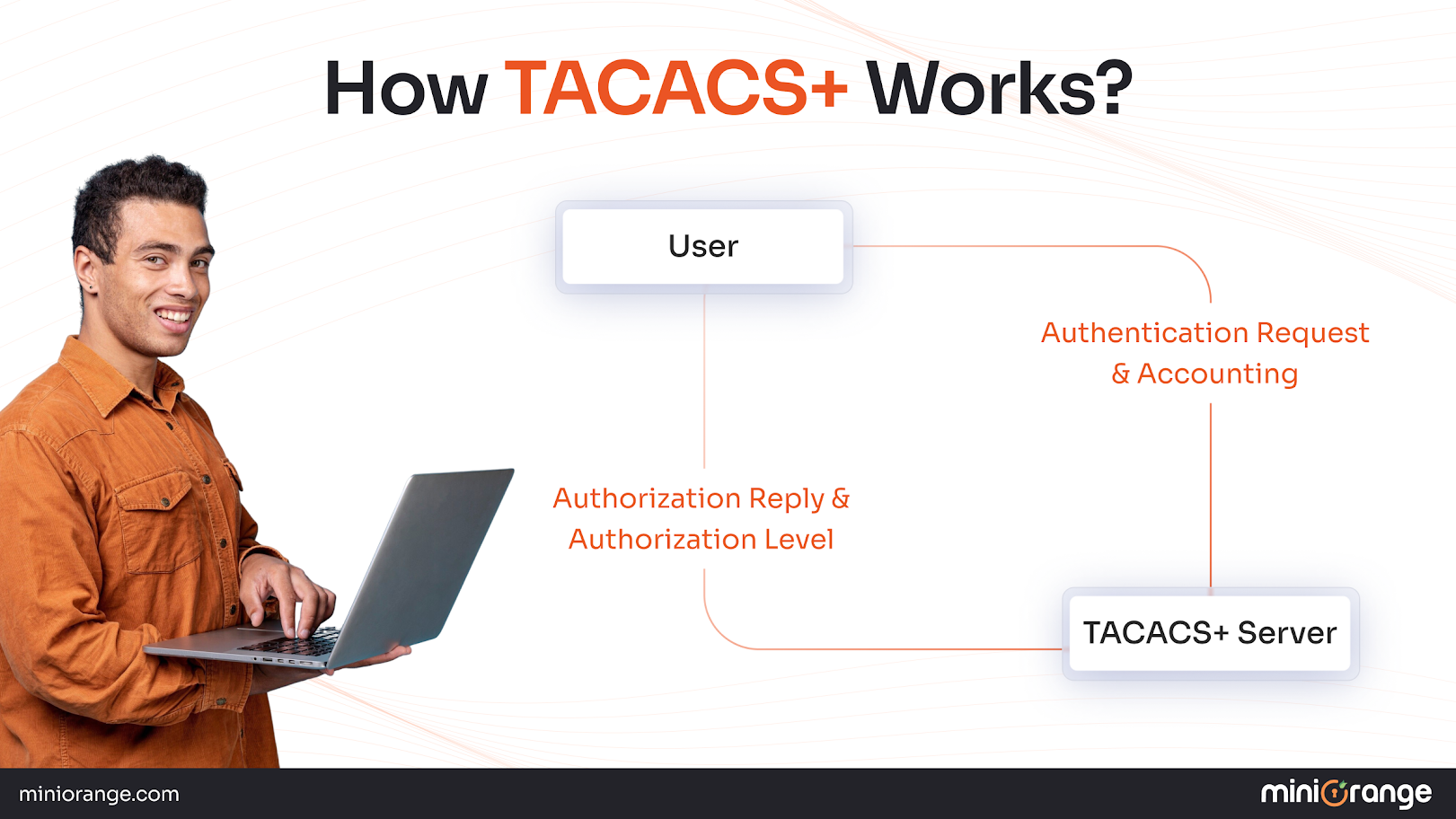
TACACS+ operates using a client-server architecture where network devices act as TACACS+ clients that communicate with a central TACACS+ server. The protocol uses TCP (Transmission Control Protocol) for reliable communication, typically on port 49.
Unlike RADIUS, TACACS+ provides full-packet encryption using a shared secret key, encrypting the entire packet payload rather than just the password field. This enhanced security approach ensures that all communication between the client and server remains confidential, including usernames, commands, and authorization responses.
Key Features of TACACS+
- Separated AAA Functions - AAA operates as independent processes for enhanced flexibility
- Command-Level Authorization - Granular control over individual commands and privilege levels on network devices
- Full Packet Encryption - Complete payload encryption provides superior security compared to partial encryption methods
- TCP Reliability - Uses TCP for guaranteed packet delivery and connection-oriented communication
- Detailed Accounting - Comprehensive logging of administrative commands, configuration changes, and user activities
- Cisco Integration - Native support across Cisco network infrastructure with deep integration capabilities
- Flexible Authorization - Supports complex authorization policies, including time-based and location-based access controls
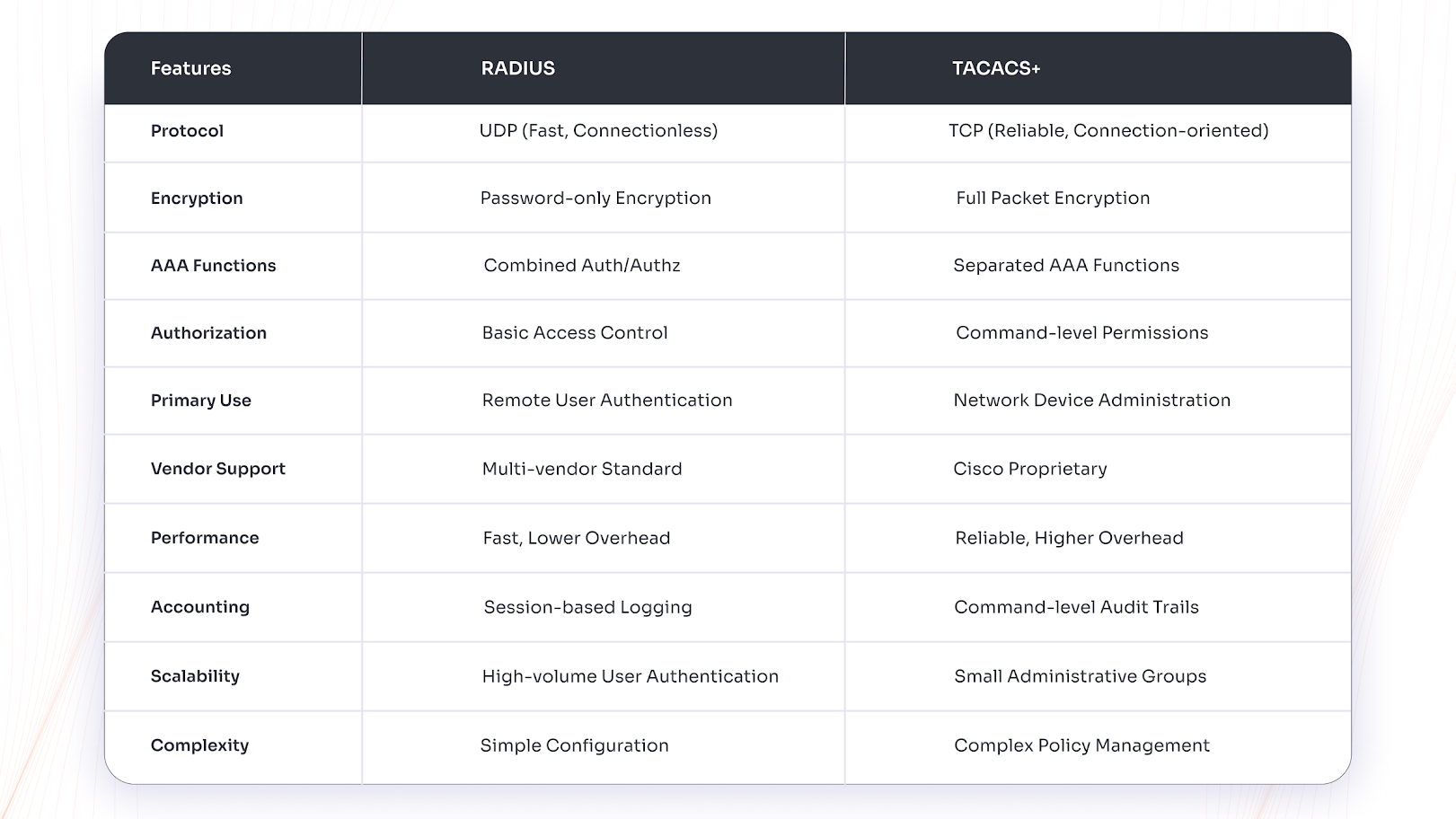
Top 10 Key Differences Between RADIUS and TACACS+
| Feature | RADIUS | TACACS+ |
|---|---|---|
| Transport Protocol | Uses UDP for fast, connectionless communication | Uses TCP for reliable, connection-oriented communication |
| Encryption Security | Encrypts only the password field, leaves other data in plaintext | Provides full packet encryption for complete data protection |
| AAA Function Separation | Combines authentication and authorization in a single process | Separates authentication, authorization, and accounting into distinct functions |
| Authorization Granularity | Basic access control with attribute-value pairs | Command-level authorization with granular permission control |
| Primary Use Case | Designed for remote user access authentication (VPN, Wi-Fi) | Built specifically for network device administration and management |
| Vendor Support | Industry standard supported by all major network vendors | Cisco's proprietary protocol with limited third-party support |
| Network Performance | Faster processing with lower latency, but no delivery guarantee | Reliable delivery with higher overhead and connection management |
| Accounting Capabilities | Session-based accounting for basic usage and billing tracking | Detailed command-level logging for comprehensive audit trails |
| Scalability | Highly scalable for thousands of concurrent user authentications | Optimized for smaller administrative user groups and device management |
| Implementation Complexity | Simple configuration with basic shared secret setup | Complex policy configuration requiring detailed authorization rules |
Which One is Better?
The choice between RADIUS and TACACS+ depends entirely on your specific security requirements and network environment. RADIUS excels in scenarios requiring network access control, such as Wi-Fi authentication, VPN connections, and ISP dial-up services, where its lightweight UDP-based approach and broad vendor support make it the preferred choice. Its simplicity and widespread compatibility across network devices make it ideal for organizations prioritizing ease of deployment and management.
TACACS+ is superior for device administration and privileged access scenarios where granular control and detailed auditing are critical. Its TCP-based reliability, full packet encryption, and separation of authentication, authorization, and accounting (AAA) functions make it the go-to protocol for managing administrative access to routers, switches, and other critical network infrastructure.
Pros and Cons of RADIUS and TACACS+ Protocol
Advantages of TACACS+ over RADIUS
More Granular Access Control
TACACS+ provides command-level authorization, allowing administrators to control exactly which commands users can execute on network devices, including specific arguments and privilege levels.
Full-Packet Encryption
Unlike RADIUS, TACACS+ encrypts the entire packet payload using a shared secret, ensuring complete confidentiality of usernames, commands, and all communication data.
Ideal for Device Management
Purpose-built for network infrastructure administration with deep integration into Cisco devices, offering native support for advanced device management features.
Reliable TCP Transport
TCP-based communication guarantees packet delivery with built-in error correction, flow control, and connection state management for critical authentication transactions.
Separated AAA Functions
Independent authentication, authorization, and accounting processes provide flexibility to customize each function according to specific security requirements.
Advantages of RADIUS over TACACS+
Simpler Deployment
Straightforward configuration with basic shared secret setup and minimal policy management, making it easier to implement and maintain across organizations.
Faster with Less Overhead (UDP)
UDP-based communication eliminates connection establishment overhead, providing faster authentication response times and reduced network latency.
Broader Device/Vendor Support
Industry-standard protocol supported by all major network vendors, ensuring interoperability in multi-vendor environments without compatibility concerns.
Lightweight and Efficient
Minimal resource consumption on both client and server sides, making it suitable for high-volume authentication scenarios with thousands of concurrent users.
Cost-Effective Scalability
Lower processing requirements and simpler architecture enable cost-effective deployment for large-scale user authentication across distributed networks.
When to Use RADIUS vs TACACS+
Choosing between RADIUS and TACACS+ depends on your specific network requirements, security needs, and infrastructure setup.
Use RADIUS in Case
You need authentication for general network access (Wi-Fi, VPN)
RADIUS excels at handling remote user authentication for wireless networks, VPN connections, dial-up access, and internet service provider scenarios where users need network connectivity.
You manage a multi-vendor environment
As an industry-standard protocol, RADIUS works seamlessly across equipment from different vendors, including Cisco, Juniper, HP, Aruba, and others, ensuring interoperability.
You want a lightweight, fast AAA solution
UDP-based communication and minimal processing overhead make RADIUS ideal for high-volume authentication scenarios requiring fast response times and efficient resource utilization.
You have budget constraints
RADIUS implementations are typically more cost-effective due to simpler configuration, lower administrative overhead, and reduced hardware requirements.
You need to scale for large user populations
RADIUS can efficiently handle thousands of concurrent authentication requests, making it perfect for organizations with extensive remote user bases.
Use TACACS+ in Case
You manage network devices and need command-level control
TACACS+ provides granular authorization for network infrastructure, allowing precise control over which commands administrators can execute on routers, switches, and firewalls.
You require full-packet encryption for higher security
Complete payload encryption ensures that all communication between clients and servers remains confidential, meeting strict security requirements for sensitive environments.
You operate a Cisco-centric infrastructure
Native integration with Cisco devices provides advanced features, seamless deployment, and optimal performance in Cisco-dominated network environments.
You need detailed audit trails for compliance
Command-level accounting and comprehensive logging capabilities support regulatory compliance and forensic analysis requirements.
Security takes priority over performance
TCP reliability and enhanced encryption make TACACS+ suitable for environments where security is more critical than authentication speed.
miniOrange AAA Solutions for RADIUS and TACACS+
miniOrange provides a comprehensive authentication solution with AAA support, covering both RADIUS and TACACS+ protocols, enabling organizations to implement robust authentication with the miniOrange MFA solution across their network infrastructure.
Our AAA Solutions Include:
RADIUS Server Implementation
Complete RADIUS server deployment with MFA software for secure user authentication, user management, and integration with existing directory services like Active Directory and LDAP.
TACACS+ Server Solutions
Advanced TACACS+ implementation with granular command authorization, detailed audit logging, and seamless integration with network device management workflows.
Hybrid AAA Environments
Deploy both RADIUS and TACACS+ within the same infrastructure, using RADIUS for user access and TACACS+ for device administration.
Cloud and On-Premise Options
Flexible deployment models, including cloud-hosted, on-premise, and hybrid solutions to meet your organization's specific requirements.
Key Benefits:
- Multi-factor authentication (MFA) support
- Single Sign-On (SSO) integration
- Detailed reporting and analytics
- 24/7 technical support
- Competitive pricing for all organization sizes
Ready to implement robust AAA solutions? Contact our experts for a customized consultation, or explore our pricing options to find the perfect solution for your network security needs.
Conclusion
Both RADIUS and TACACS+ serve essential roles in network security, but they excel in different scenarios. RADIUS remains the go-to choice for user authentication across diverse network environments, offering simplicity, speed, broad vendor support, and compatibility with various methods of authentication. TACACS+ provides superior security and granular control for network device administration, particularly in Cisco-centric infrastructures, and often works well alongside context-based authentication to enforce stricter access policies.
The decision between these protocols shouldn't be viewed as mutually exclusive. Many organizations successfully implement both protocols simultaneously, using RADIUS for user access and TACACS+ for infrastructure management. This hybrid approach leverages the strengths of each protocol while addressing different security requirements within the same network environment.
FAQs
What are the disadvantages of TACACS+?
TACACS+ has higher implementation complexity, increased processing overhead due to TCP transport, limited vendor support outside Cisco ecosystems, and higher resource consumption compared to RADIUS. It's also not suitable for high-volume user authentication scenarios.
Is TACACS still used?
Yes, TACACS+ (the plus version) is widely used for network device administration, especially in enterprise environments with Cisco infrastructure. The original TACACS protocol is largely obsolete, but TACACS+ remains actively deployed for secure network management.
Which is more secure?
TACACS+ is generally more secure due to full-packet encryption, separated AAA functions, and TCP reliability. RADIUS only encrypts passwords, leaving other data in plaintext. However, both can be secured with proper implementation and additional security measures.
Can I use both RADIUS and TACACS+ together?
Yes, many organizations use both protocols simultaneously. RADIUS for user authentication (VPN, Wi-Fi) and TACACS+ for network device administration. This hybrid approach leverages each protocol's strengths for different network security requirements.
Does RADIUS do AAA?
Yes, RADIUS provides Authentication, Authorization, and Accounting (AAA) services. However, it combines authentication and authorization in a single process, unlike TACACS+, which separates all three functions independently.




Leave a Comment