An OTP is one of the quintessential steps for logging in today in almost every account. Humans tend to forget their passwords a lot and to reset one they use either an SMS OTP, email OTP or voice OTP. Else you are using OTP as the first form of authentication eliminating the need to remember passwords altogether. It needs the user to access their SMS, email or a dedicated authenticator app for logging in.
In 2023, 1.3 trillion SMS OTPs have been sent and this number keeps increasing. The demand for OTP in Europe has risen because of the latest regulations imposed by the EU’s Artificial Intelligence Act on protecting user privacy of their biometric data. This prohibits the use of biometric authentication techniques as an MFA method in this region. Therefore, OTP is a reliable solution for such regions.
This article focuses on defining what an OTP is, OTP authentication, its types, its working, benefits, best practices in OTP security and how miniOrange as your security software solution partner helps you achieve OTP security with multi-factor authentication. It explores the nuances of TOTP and HOTP.
What is OTP Authentication?
OTP stands for one-time password. It is a single use code that is sent to your device that you can enter while logging in to your applications to authenticate your identity. It works on possession-based factors in multi-factor authentication.
When you are using your regular password, these are static credentials that end up exposing you to phishing, brute force, credential stuffing and replay attacks. However, OTPs are dynamic and they get changed every time you log in and expire after a set period of time such as a few seconds or minutes.
These are relatable to the moving staircases in Hogwarts Castle where the stairs shift and rotate unpredictably. In practical scenarios, the OTPs leave a very steep window for attackers to work with.
An OTP is defined as a unique, short-lived code that systems generate and send you for a single login or transaction, and it expires quickly to keep your account secure. OTP authentication is a security method where systems generate and send you a unique, short-lived code for each login or transaction; you enter that code to verify it’s you and keep your account secure.
Types of OTPs and Delivery Methods
Here are the main types of OTPs and ways to send them that you can use to protect each login or transaction with a dynamic verification code.
1. SMS OTP Verification
SMS OTP verification is a way to send a short, unique numeric code to your mobile phone via text message. You enter that code to verify a single login or transaction and keep your account safe. It's easy to use and one of the most common ways to do multi-factor authentication.
2. Time-based one-time password (TOTP)
A time-based one-time password (TOTP) is one way to protect your data. Authenticator apps make a number code that changes every few seconds and is in sync with the clock. You enter that code within a short time frame to prove your identity without having to rely on network delivery. The miniOrange authenticator is one of the most reliable authenticators that lets you log in from anywhere without an internet connection.
3. HMAC-based one-time password (HOTP)
HMAC-based one-time password (HOTP) uses a shared secret key and a counter that goes up by one every time you ask for authentication. You enter the code that was made each time you ask for authentication to complete a secure action.
4. Email OTP Verification
Email OTP Verification is a way for systems to send you a unique, time-limited code to your email inbox. You then retrieve and enter that code to prove your identity for a specific login or transaction and add an extra layer of security.
An OTP ensures your logins are safe and protected and can be used as the first factor when logging in using single sign on to enhance security and user experience. To ensure strong protection, pick the OTP variant and delivery method that best meet your security needs and the needs of your users.
Learn how different methods of authentication safeguard user identities.
How to Put Dynamic Authentication into Your Business Use Case?
When you focus on the OTP part, your risk-based authentication is easier because it only gives out codes that can be used once when certain risk criteria are met. Risk based logins are a part of adaptive MFA authentication. Here is how you can apply that for your business:
- Link things that could be dangerous, like a new device fingerprint, a strange geolocation, or a big money transaction, to OTP triggers. Consider context-based authentication in such a case.
- You can send messages by SMS gateways, transactional email, or push notifications.
- Ensure the OTPs are safe by using TOTP or HOTP methods or a cryptographically random number generator.
- Put limitations on the maximum number of retries, a time-to-live of 5 to 10 minutes, and a length of 6 to 8 digits.
- You can add the OTP service to your IAM platform without having to rebuild basic flows by using its API or a small microservice.
- Test with a small group of people to see how long it takes to deliver, how many people use the code, and do they trust it.
- Track important metrics like the success rate, average delivery time, and drop-off points. You should also change the risk levels and code settings all the time.
- Automate escalation if OTP validation keeps failing. Risk alerts keep coming up, add more steps to check the problem or have someone look into it.
By changing OTP triggers, distribution methods, and monitoring, you can make an authentication pipeline that is always in balance and changes based on real-time risk. It is interesting to note how one time passwords work in the upcoming section.
How Does OTP Authentication Work?
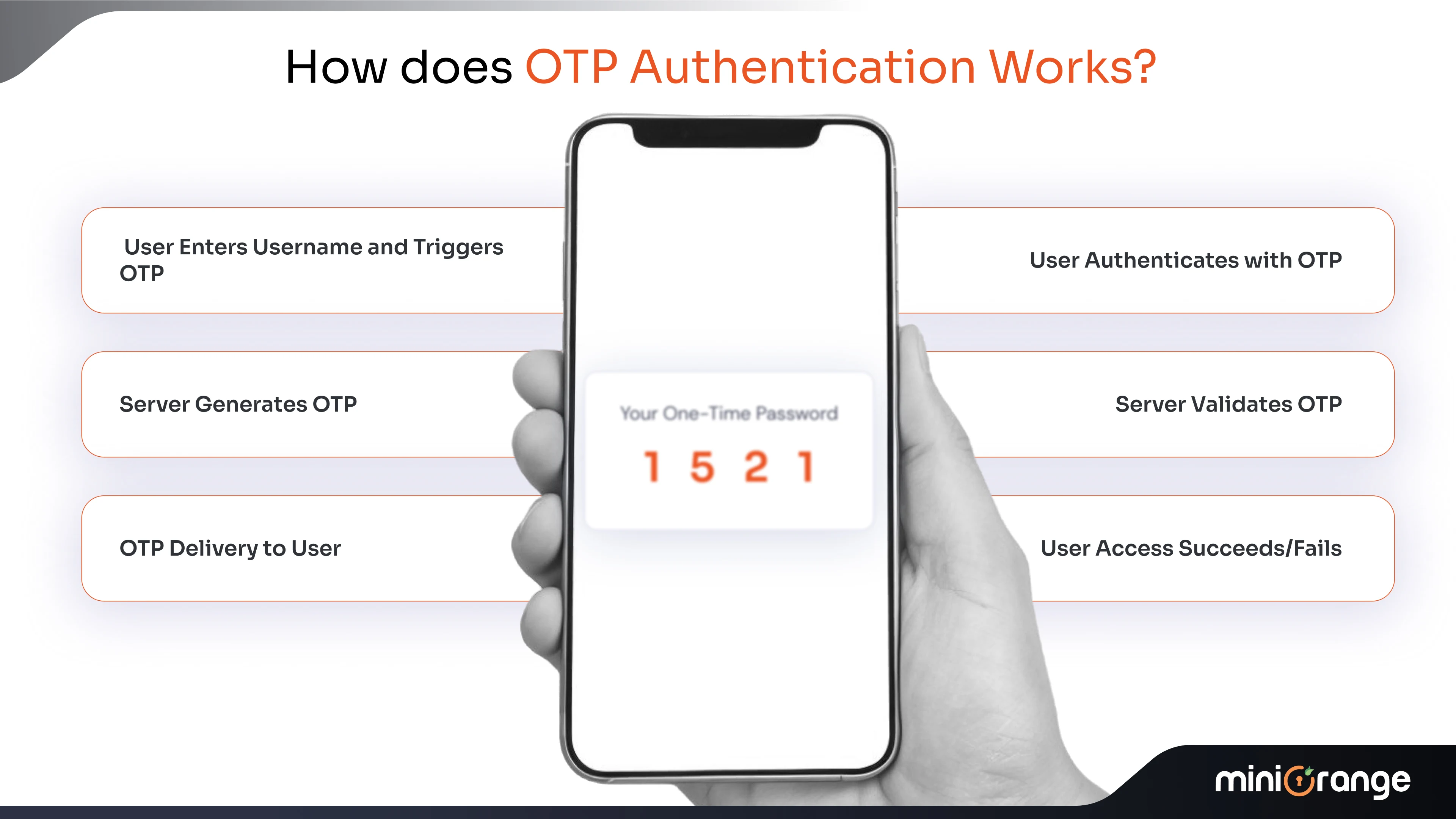
Utilizing a secret code to get into your digital fortress, which then disappears in seconds, that's what OTP (One-Time Password) authentication is all about. It adds a layer of protection that changes and doesn't stay long, which makes static credentials feel outdated. It is one of the most popular authentication solutions for enterprises.
1. User Enters Username and Triggers OTP
You begin by entering your username on a login screen or starting a transaction that is exceedingly dangerous. This action starts the OTP flow in the system.
2. Server Generates OTP
With the help of cryptographic algorithms like HMAC based OTP (HOTP) or time based OTP (TOTP), the backend securely generates a one time passcode or single use code. This OTP is limited by time intervals and number of transactions or events triggered.
3. OTP Delivery to User
You can acquire your OTP by text message, email, an authenticator app, or a push notification. You may put these channels up based on how hazardous they are and what the user desires.
4. User Authenticates with OTP
You enter the OTP you got into the authentication interface. It can only be used for a short duration, usually between 30 and 60 seconds.
5. Server Validates OTP
The server checks to determine if the OTP you typed in is the right one. It also checks the delivery's integrity and the time limit.
6. User Access Succeeds/Fails
If the OTP matches and is within the time limit, you can access. You have to try again or use another approach if the time runs out if the information doesn't match.
Benefits of OTP Authentication
OTP authentication for your business is not just a compliance necessity but an effective defending mechanism against the rising cyberattack covering the most prominent types of cyberattacks, when utilized the best practices. Here's what OTP authentication can offer your business:
Enhanced login security
The implementation of OTP provides organizations with an additional security measure which extends beyond traditional password authentication.
Protection against phishing and replay attacks
The attackers must obtain both your static credentials and the dynamic OTP to gain access even if your static credentials are compromised.
Compliance with MFA standards
The implementation of OTP-based methods fulfills the Multi-Factor Authentication (MFA) standards which are defined by regulations for an MFA software. Organizations can build stronger trust relationships while preventing expensive penalties through this approach.
Explore multi-factor authentication and strengthen access control across platforms.
What are the OTP Performance Metrics?
- OTP Delivery Rate: Percentage of sent OTPs that arrive successfully.
- OTP Conversion Rate: Percentage of delivered OTPs that result in successful validation.
- Latency: Time from OTP generation to delivery; critical for user experience.
- Failure Analysis: Breakdown of failed deliveries by channel (SMS vs email) and cause (network vs user error).
OTP Security Best Practices and Tips to Avoid OTP Misuse
To keep your OTPs truly effective and secure:
1. Avoid SMS OTP for High-Risk Logins:
Don’t rely on SMS codes for sensitive logins—switch to authenticator apps or hardware tokens instead.
2. Enable Multi-Factor Authentication (MFA):
Always layer OTPs within a robust MFA strategy so a stolen code alone can’t unlock your account.
3. Monitor for Phishing Attacks:
Keep a tab on OTP request patterns, train your team to spot phishing tricks, and flag any suspicious activity immediately.
How to Administer OTP Policies Effectively?
Stringent OTP policies need to be present because of the risks that run into having compromised OTP systems. Here are the most effective OTP policy administration steps for securing your OTP based logins:
1. Choose Safe Delivery Channels: You can send messages by SMS, email, or authenticator apps, but you should think about how safe you need to be and what your customers like.
2. Set Expiration Times: Make sure that OTPs only work for a short time (30 to 120 seconds) so that someone is less likely to take advantage of you.
3. Limit Retry Attempts: To stop brute-force attacks, limit how many times a user can enter the wrong OTP.
4. Encrypt OTP Data: Use encryption to protect OTPs from other people when you store and send them.
5. Watch for Unusual Activity: Check for any OTP requests from different time zones. locations, IPs addresses and location.
6. Use Multi-factor Authentication: For extra security, log in with one-time passwords (OTPs) and other methods.
7. Provide users with backup options: If the user cannot receive their OTP as a primary factor for authentication, give them options to login through a hardware token, recovery codes as backups.
8. Make Your Users Aware: Show users how to tell when someone is trying to steal their OTPs and not give them up.
9. Make Sure the System Is Reliable: Regularly test the processes for sending and validating OTPs to make sure they work as they should.
10. Obey the Regulatory Guidelines: Make sure that the OTP rules are in line with the compliance and the laws that protect data
By following these guidelines, you can protect your authentication process and keep both your users and your data secure.
Advanced OTP Security Considerations
Protecting your system from unauthorized access attempts and cyberattacks of all types needs constant vigilance and active mitigation strategies. Here are a few considerations:
Attack Vectors
- SIM Swap and SS7 Exploits: Attackers redirect SMS OTPs via mobile network protocol vulnerabilities.
- Man-in-the-Middle (MITM) Attacks: Intercept OTP links or codes over insecure channels.
- Phishing and OTP spamming: Malicious pages extract OTPs in real time by proxying authentication flows.
- Brute Force: Automated attempts at OTP guessing if rate limiting is insufficient.
Techniques to Mitigate
- Deprecate SMS OTP for highest-security contexts; favor soft tokens or hardware MFA.
- Incorporate device fingerprinting, IP geolocation checks, and anomaly detection for OTP validation.
- Use short, single-use URLs rather than codes for transaction-specific OTP flows.
- Enforce revocation and dynamic blacklisting on repeated OTP guessing attempts; lock accounts after threshold.
How Does miniOrange Help with OTP Security?
miniOrange gives you everything you need to protect your OTPs during your MFA logins, work better and be stronger in security. miniOrange keeps your one-time passwords safe, reliable, and easy to use by using strong infrastructure, flexible delivery options, and policies that can change.
1. Comprehensive OTP Management
miniOrange brings together all your hassles of OTP generation, storage, and validation through a well-protected cloud-based platform. This approach eases you from the burden of maintaining your own cryptographic servers and keeps your OTP secrets protected by industry-grade encryption. All transaction logs and audit trails are stored in high security, giving you a full view of essential metrics OTP usage and potential anomalies.
- Secure generation algorithm that meets NIST standards
- Encrypted transmission and storage of OTP secrets
- Real-time monitoring and in depth reporting
2. Flexible Delivery Channels
Users expect choice when receiving OTPs. miniOrange supports multiple delivery methods out of the box, letting you tailor the user experience:
1. SMS and voice call OTPs for broad device compatibility
2. Email OTPs for lower-risk transactions
3. Push-notification tokens via a mobile app for seamless authentication
Each channel includes built-in rate limiting and retry logic to minimize delays and prevent abuse.
3. Adaptive Security Policies
Not all OTP use cases carry the same risk. miniOrange’s policy engine lets you adjust OTP behavior based on contextual factors:
- Geolocation checks to block high-risk regions
- Time-based policies that expire codes faster during suspicious activity
- Device-fingerprinting to ensure OTPs reach recognized devices
By layering these risk signals, miniOrange levels up its strong security alongside maintaining a smooth user journey.
4. Easy integration and growth
miniOrange works well with your current identity systems, such as LDAP, Active Directory, OAuth, SAML, or custom APIs. You can get started in just a few easy steps:
1. Set up SAML/OAuth endpoints or install the miniOrange SDK
2. Set your OTP delivery preferences in the admin console.
3. Map user attributes and test with sandbox credentials
miniOrange's auto-scaling infrastructure makes sure that OTPs are always sent, even when there are a lot of authentication requests.
5. Enterprise Grade Compliance Support
miniOrange helps you follow the rules by giving you:
- GDPR and CCPA data privacy controls
- Data centers that have been certified by SOC 2 and ISO 27001
- Help and professional services are available 24/7 for custom deployments
No matter what field you work in, like finance, healthcare, or education, you can trust miniOrange to meet your security and compliance needs.
With miniOrange IAM, OTP security is more than just one level of safety. It turns into a shield that changes and adapts to keep your users safe without making things harder for them.
Getting Started with OTP Security for Your Enterprise
With the popularity of SMS based OTPs, there is a huge spike in OTP interception and SIM-swapping attacks. This might sound like SMS OTP not reliable in critical use cases. However, understanding the difference between 2FA and MFA, the OTP generation algorithms like TOTP, HOTP and challenge response and using the best practices in OTP helps you protect every login, transaction and register flow.
Consider OTP security solutions as a part of miniOrange’s multi-factor authentication suite with more than 15 MFA methods. Essentially offering quickly expiring codes on your devices through SMS, email and authenticator apps. Prevent adversaries from getting into your systems and compromising your security. Learn the best practices for OTP authentication with miniOrange and create a comprehensive threat prevention program with our IAM suite Explore our IAM pricing. Consult today at info@xecurify.com or contact us.
FAQs
What is the difference between TOTP and HOTP?
TOTP codes are based on the current time and only last for a short period (typically 30 seconds). HOTP codes are based on a counter and don't expire until they are used, hence TOTP codes are often more secure.
How do I locate an OTP password?
You can get OTP codes by text message, email, an authenticator software (like Google Authenticator), a hardware token, or a printed backup code.
What does a one-time password look like?
A one-time password is a code made up of numbers (often letters and numbers) that is only good for one use and expires shortly.
Are one-time passwords completely secure?
No, OTPs are safer than static passwords, but they can still be stolen through phishing, SIM swapping, or interception attempts.
How do you create one-time passwords?
You can get OTPs from software (such authenticator applications), hardware tokens, or your bank or service provider. They are given to you by SMS or email.
How do you remove one-time passwords?
You can switch off OTPs by deleting the authenticator app or calling your service provider's support and asking them to turn off OTP for your account.
Can a Do Not Disturb (DND) setting block the delivery of OTP SMS messages
Yes, the Do Not Disturb (DND) settings can sometimes block OTP SMS texts from getting through. This is especially true if your service provider doesn't call the message "transactional" or "service implicit." You should send transactional and OTP messages because DND usually lets them through. But if the settings are wrong or the messages are sent to the wrong group, they might not go to numbers that have DND turned on. In such cases, opt for authenticator apps for reliable OTP deliveries anywhere throughout the world without the additional cost of international roaming to receive the SMS OTPs.



Leave a Comment