Passwords are the first step to securing any account, resources, and databases. But, they’re now easily crackable due to the advent of Artificial Intelligence (AI). According to data released in 2023, it takes only a minute to crack 51% of the common passwords with the help of AI.
AI and automation act as a double-edged sword because they not only help defend against malicious entities through AI-powered IAM solutions but also aid hackers in launching brute-force and social-engineering attacks faster than ever before.
In this article, we will reflect on brute force attacks, understand how they work, and what the potential types of brute force attacks are. We will also look at the impact of these attacks, preventive measures, and the role of miniOrange in securing organizations against these attacks.
What is a Brute Force Attack?
Brute force is a trial-and-error hacking tactic, where bad actors try to gain unauthorized access to accounts and resources by trying every possible combination of usernames and passwords, until a correct one is found. Millions of combinations are tested and tried, using automated tools and artificial intelligence.
According to the Cloud Threat Intelligence report by Google Cloud, in 2022, the most common attack vectors used for cloud providers were brute force of cloud services that are exposed to the internet and have a default or a weak password.
Brute force attacks surged significantly due to the rise in novel working models (remote and hybrid) because organizations turned to flexible HR management systems, VPNs, and work emails with easy-to-decipher passwords, and zero awareness of cybersecurity protocols.
However, with an increase in cybercriminal activities, organizations are turning to Zero Trust Architecture (ZTA) approaches and implementing Multi-Factor Authentication (MFA) software, Single Sign-On (SSO), Risk-Based Authentication (RBA), and adaptive authentication to safeguard themselves against malicious entities.
miniOrange offers a comprehensive suite of Identity and Access Management (IAM) solutions, designed to protect your organization against brute force attacks and other types of threats.
How Brute Force Attacks Work?
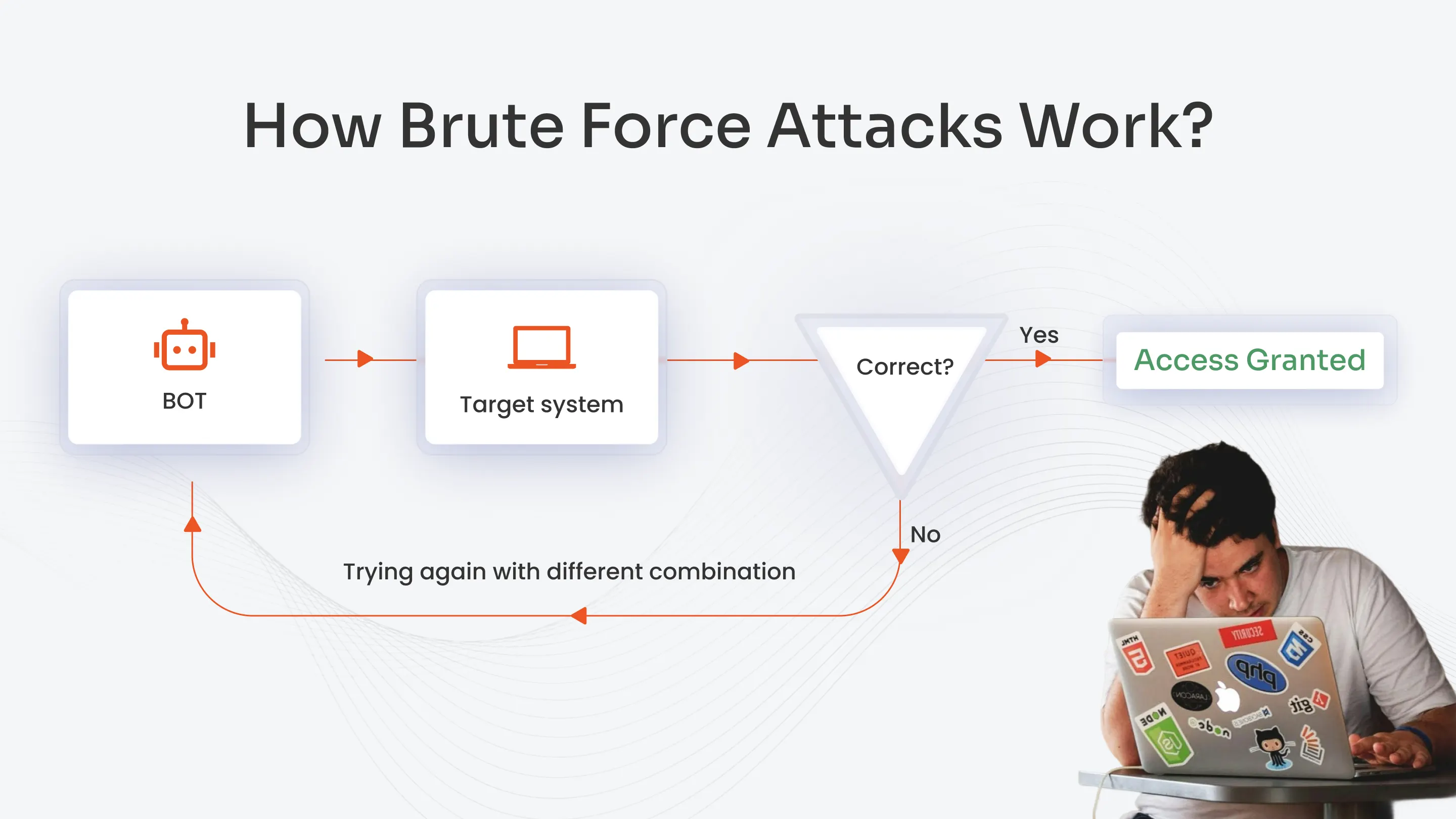
Brute force attacks make use of automation and computing to bypass the authentication systems. Here’s how the brute force attacks usually work:
- Identifying a Target: Threat entities select a login page, an encryption system, or an authentication API to target.
- Collecting Information: Then, they collect information about username and password structures, and any other leaked credentials of the target.
- Automating Attack: Threat entities generate and test innumerable credential combinations via AI and automation tools.
- Compromising Accounts: Once valid credentials are discovered, the hackers gain the same level of access as the account holder, resulting in data breaches, fraud, scams, and lateral movement throughout the organization’s network.
This is the most basic way a brute force attack works. The speed of attack can vary, depending on the complexity of credentials and password policies.
Traditional vs. Automated Brute Force Attack
Here is a brief comparison between traditional and automated brute force attacks.
| Element | Traditional Brute Force Attack | Automated Brute Force Attack |
|---|---|---|
| Speed of Attack | Quite slow, as limited due to human input or simple scripting | Very fast, as thousands to millions of attempts can be covered within minutes |
| Method | Manual based | Specialized tools are used to speed up the process |
| Scope | Targets 1-2 credentials at a time | Targets multiple accounts simultaneously |
| Error Rate | Very high due to the human error factor | Extremely low due to the usage of automation |
| Complexity | Simple | Complex as advanced algorithms are used |
| Detection | Very easy to detect due to fewer attempts and a slower rate | Harder to spot, and a high rate may trigger security controls |
What are the Types of Brute Force Attacks?
The brute force attack is an umbrella term that includes varied password-cracking techniques that are explained below.
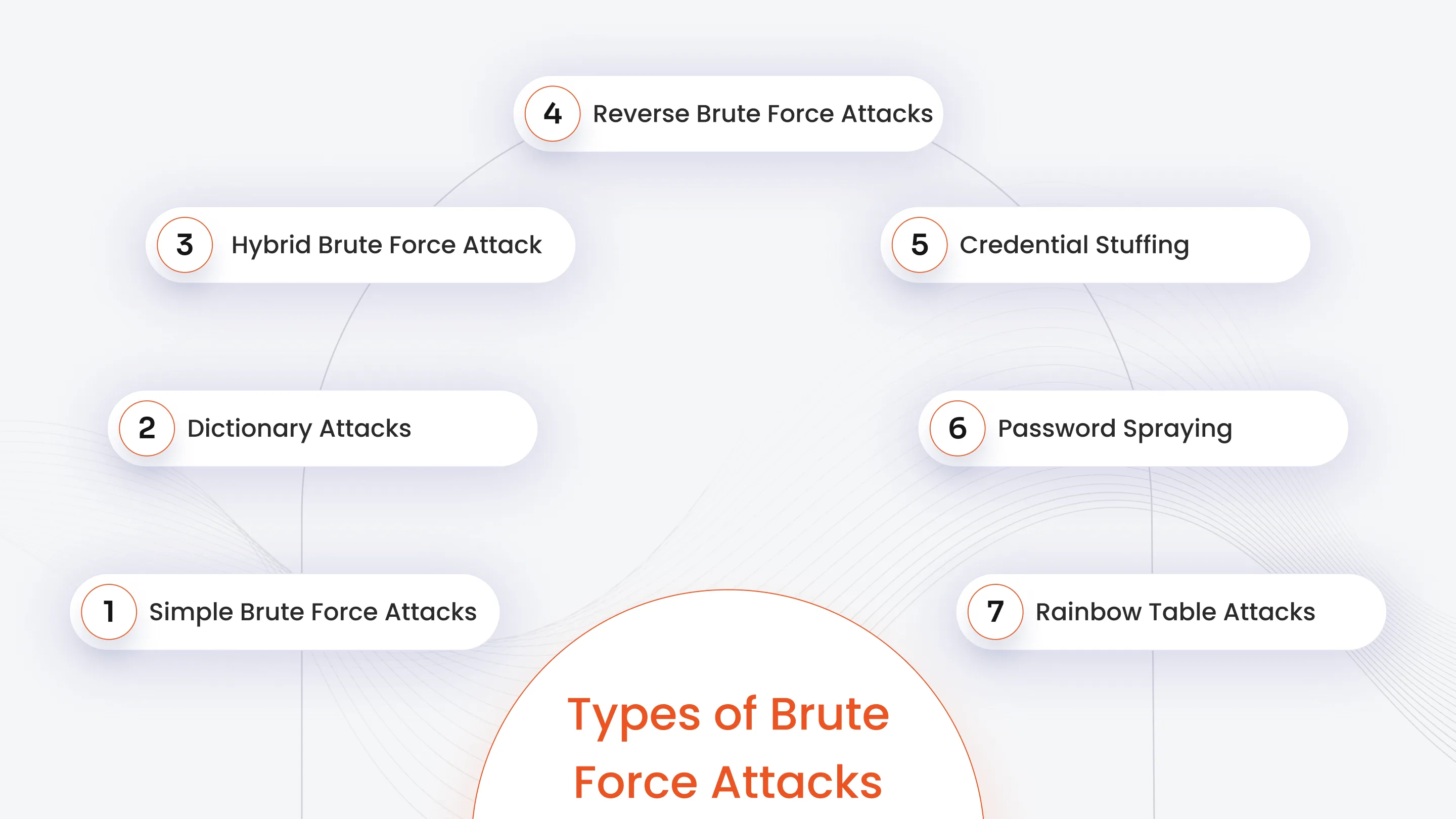
1. Simple Brute Force Attacks
In the case of simple brute force attacks, threat entities simply guess the passwords based on the knowledge they have about the target, without the help of any automated or AI tools.
With this type of attack, an extremely simple password can be guessed within minutes, for example, ‘admin@123.’
2. Dictionary Attacks
Dictionary attack is a technique of cracking a password of a computer, account, resources, or a network by systematically entering a predefined word list. This type of attack can be used to find the key to decrypt a file, document, or message.
A dictionary attack works on the assumption that users tend to use a basic list of passwords, based on name, region, birthdays, family names, words from a dictionary, or common phrases (password@123).
3. Hybrid Brute Force Attack
A hybrid attack is a combination of a simple brute force attack and a dictionary attack. The threat entities start out by listing out common phrases or words (dictionary attack) and then add variations like special characters, numbers, or capitalizations to guess the password and username (simple brute force attack).
4. Reverse Brute Force Attacks
A reverse brute force attack involves starting with a known password, which is often obtained from darknet markets or data breaches. This password is used to find the username it belongs to. This is an effective tactic when hackers have access to commonly used passwords.
5. Credential Stuffing
Through the credential stuffing method, malicious players leverage credential combinations that are acquired via previous breaches. These credentials are tested against various websites and systems until one is cracked.
Here’s how credential stuffing works: Pairs of compromised credentials are added to a botnet that automates the process of testing credentials on various websites.
6. Password Spraying
The password spraying technique involves using a list of a few common passwords against a huge number of usernames.
For example, a malicious entity may use one password (Password123) against several accounts on an app to avert account lockouts that may happen due to brute forcing a single account with several passwords.
7. Rainbow Table Attacks
The rainbow table attacks make use of a special table (rainbow table) to break open the password hashes in a database.
So, an app doesn’t store passwords in plaintext; rather, they are encrypted using hashes. When a user logs into an account, the passwords are converted to hashes, and they are compared with the hashes stored on the server for a match. If matched, the user is granted access to the application.
Here, the rainbow table is a precomputed table that includes password hash values for every plaintext used during the user authentication process. If a malicious entity accesses password hashes, then they can crack all the passwords speedily.
What are the Motives Behind Brute Force Attacks?
Brute force attacks take longer than other forms of cybersecurity attacks, but they can leave lasting repercussions. Here are possible motives behind brute force attacks:
- Spread Malware: Hackers may want to create complete havoc within a system by spreading malware via SMS or email. This can lead to a wider launch of attacks within an organization.
- To Steal Personal Information: Access to a user’s personal account offers a treasure trove of data, from ID card details and bank accounts to private medical information. This data is often used to damage reputation, conduct financial fraud, and commit identity theft.
- Hijack Systems: Attackers aim for broader level threats using a botnet, known as Distributed Denial-of-Service (DDoS) attacks, to overpower an organization’s systems.
These are just over-the-top motives, but there is scope for hackers to think beyond them. The current motives give us an opportunity to counter these attacks via MFA methods such as biometric authentication, push notifications, magic links, and more.
Real-World Examples of Brute Force Attack
1. Dell Data Breach (2024)
In April 2024, information on over 49 million Dell customers from 2017 to 2024 was leaked on the dark web and was available for purchase. Attackers brute-forced Dell’s online portal to access sensitive data. After this, they conducted social engineering attacks, posing as a Dell reseller or partner, to verify the data.
2. T-Mobile Breach (2021)
In August 2021, T-Mobile US faced a major data breach, where over 40 million former and prospective customers were impacted, along with 7.8 million postpaid customers. This breach exposed social security numbers, names, birthdates, and driver’s license details.
3. Alibaba (2016)
The Alibaba e-commerce site Taobao faced a credential stuffing attack due to weak passwords, resulting in the exposure of 20 million accounts. The fallout of the technical support team for this attack led to a dip in Alibaba’s US-based stocks.
How to Protect Against Brute Force Attacks?

Here’s a list of practical ways to protect yourself and your organization from potential brute force attacks. The list offers preventive measures for users and organizations. Also, these measures can be used for both users and organizations, but have been bifurcated for better understanding.
For Users
Users can make use of the following methods to defend themselves against password-based attacks.
1. Use Strong, Complex Passwords
Mandate strong, complex passwords that are difficult to guess. An effective password contains:
- 12-16 character length
- A combination of uppercase and lowercase, numbers, and special characters
- No predictable words or phrases
2. Implement Account Lockout Policies
Easily limit the number of failed login attempts before automatically locking away an account to deter threat entities from making infinite guesses.
Practical steps include locking accounts after 3 to 5 failed attempts, offering users a safe account recovery method, and enforcing delays between login attempts.
3. Enable Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) is considered the most effective defense technique against brute force attacks, where users are required to offer two or more authentication factors, which are as follows:
- Something they know, e.g. password or a PIN
- Something they have, e.g. security key, code, or a device
- Something they are, e.g., a facial recognition, iris scan, or fingerprint scan.
Apart from this, adaptive MFA is used to augment protection levels through flexible, dynamic authentication requirements, based on the risk factors, such as geolocation, user behavior, device, IP address, or time of day.
Take a deep dive into the crux of phishing-resistant MFA
4. Get Rid of Old Accounts
Disable or completely remove old or unused accounts to decrease the number of possible entry points for brute-force attacks.
For Organizations
Organizations can start protecting their data, resources, and accounts by implementing one or more of the following preventive measures.
1. Limit Login Attempts
As discussed above, this method can block the number of times a user can attempt to log in to their accounts. This is a necessary tactic to stop malicious attackers from guessing credentials an infinite number of times.
2. Deploy CAPTCHA
CAPTCHA is a necessary method to differentiate between automated bots and human users. Implementation of CAPTCHA after failed attempts can substantially decrease the efficacy of automated brute force attacks and minimize their impact on the legitimate users.
3. Detecting Brute Force in Real-Time
Enable continuous monitoring to easily spot and respond to brute force threats. This could include blocking malicious IP addresses via threat intelligence and setting up an intrusion detection system. Furthermore, enforce Security Information and Event Management (SIEM) solutions for attack detection.
4. Rate Limiting and IP Blocking
Easily monitor suspicious behavior and restrict account access for the same by blocking IP addresses that display brute force attacks. Also, limit the number of requests from a single IP address. Secure authentication endpoints with rate limits and set up restrictions based on geographical locations.
5. Salted Password Hashing
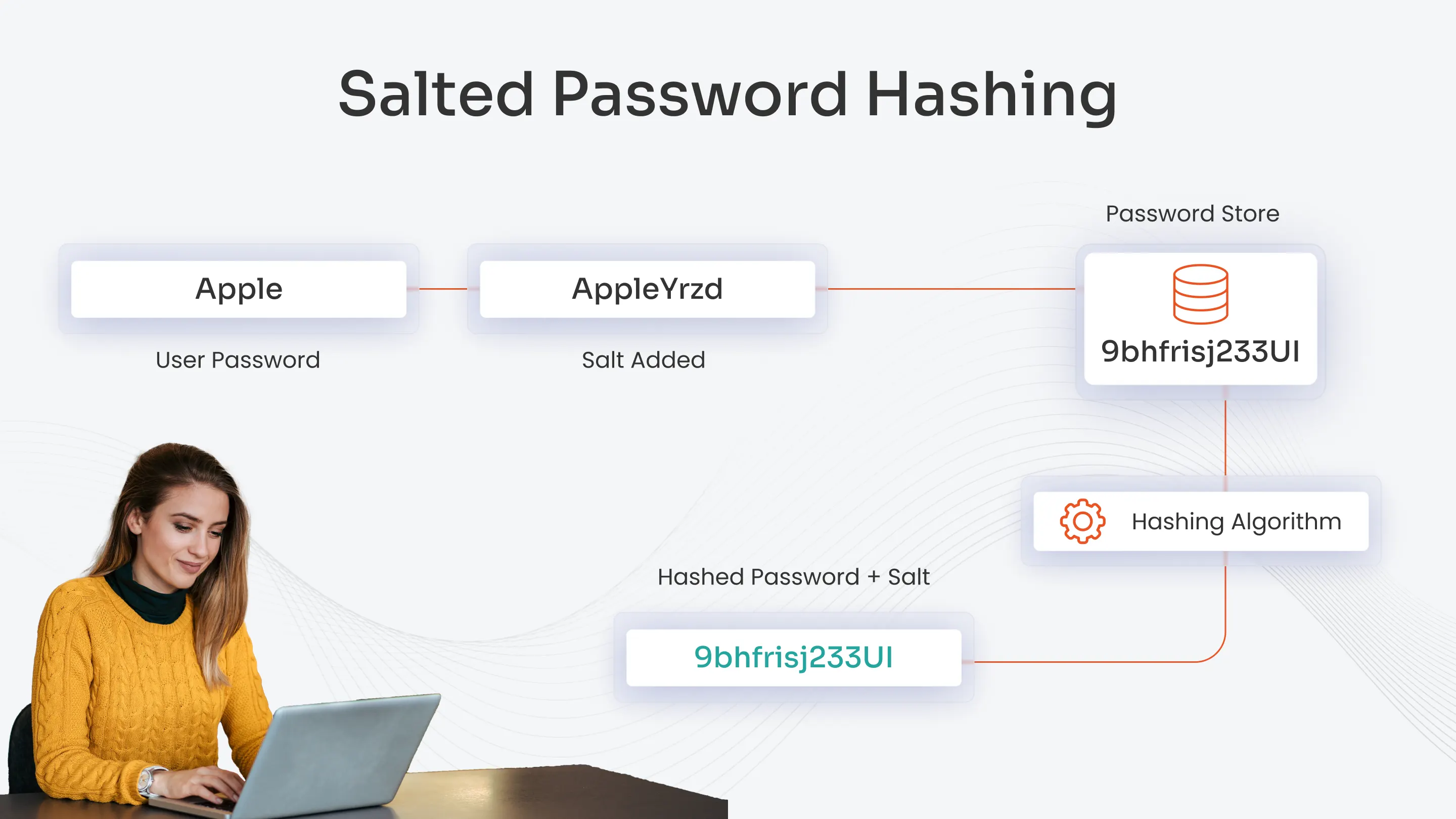
Salted password hashing is used to ameliorate password security by adding extra layers of randomness to the hashing procedure.
Salt is a randomly created string that is added to a password before it is hashed, and the process is called salting. This ensures that every password hash is unique (even for identical passwords) and prevents hackers from using rainbow tables to break the passwords.
6. Apply the Principle of Least Privilege (PoLP)
The PoLP works on the principle of offering users only specific privileges or permissions required to perform certain tasks. Once the task is accomplished, these privileges can be taken away (in case it is confidential) or kept the same. This way, the damage done by the hackers stays limited to certain users only.
7. Cyber Awareness and Training
Cyberawareness is a key step towards preventing malicious attacks. Educate employees about generating and handling strong passwords, along with spotting phishing, social engineering attacks, ransomware, Man-in-the-Middle attacks, and more.
Teach them about the importance of not reusing passwords across different services, and practical ways to report security breaches.
8. Passwordless Authentication
Consider implementing passwordless authentication methods to prevent brute force threats altogether.
Passwordless authentication includes hardware security keys, biometric authentication, magic links, authenticator apps, and more.
Learn more about the authentication solutions
Staying Ahead of Brute Force Attacks with miniOrange Products
miniOrange offers a comprehensive suite of cybersecurity solutions developed to protect against malicious threats, including brute force attacks. Leverage miniOrange’s advanced expertise and technologies to increase your chances of defending against threat entities.
miniOrange’s IAM products (SSO, MFA, PAM, 2FA, and more) are well-equipped to handle incidents via adaptive access controls, reporting and auditing, password policies, and more.
Connect with miniOrange to understand how we can help you mitigate risks associated with cybersecurity attacks in the long run, including our competitive pricing options. You can also test our products by availing a 30-day free trial.
FAQs
How to detect a brute force attack?
Indicators of a brute force attack are high volume of failed login attempts, repeated account lockouts, logins outside business hours, and attempts from unusual IP addresses.
What is the difference between a dictionary and a brute force attack?
Dictionary attacks make use of predefined words to crack a password, whereas brute force attacks do not use a predefined list, but rather run through random combinations of letters and symbols to hack into an account.
Are cloud services vulnerable to brute force attacks?
Yes, cloud services are vulnerable to brute force attacks, and hackers target them via API endpoints, security misconfigurations, and gaining control over cloud management consoles.
How quickly can a brute force attack decipher a password?
With the help of AI, it can take anywhere between minutes to months to crack a password.
What are the strategies used for enterprise brute force attack protection?
Enterprise brute force attack protection methods include the implementation of CAPTCHA, strong password policies, MFA methodologies, IP address restrictions, and adherence to Zero Trust Architecture (ZTA) principles.
What are the commonly used brute force attack tools?
Commonly used brute force attack tools are John the Ripper, Aircrack-ng, Hashcat, Ncrack, Rainbow Crack, and many more.




Leave a Comment