Reverse Proxy
18 posts

Reverse Proxy
ITAR Compliance for Cloud Services with CASB
Feb 17, 2026

Reverse Proxy
Shopify User Session Management
Apr 17, 2025

Reverse Proxy
Protect Your Business Data & Emails on Office 365
Mar 18, 2025
Reverse Proxy
How To Restrict Shopify Store Access to Third-Party Vendors?
Jul 8, 2024
Reverse Proxy
CASB for Salesforce Data Security, Compliance, and User Visibility
Jun 6, 2024
Reverse Proxy
Microsoft 365 CASB for Sharepoint for Business Data Security and Compliance
Nov 1, 2023

Reverse Proxy
ServiceNow CASB Cloud Security for Compliance and Granular Access Control
Nov 1, 2023
Reverse Proxy
AWS services CASB security solution to secure your AWS Environment
Sep 4, 2023

Reverse Proxy
How to set up WordPress role based access control to secure site folders?
Aug 22, 2023

Reverse Proxy
Enable Group-based access to Gmail using the Google Workspace CASB security solution
Aug 22, 2023

Reverse Proxy
Google app TTL restrictions using Google Workspace CASB security
Aug 22, 2023

Reverse Proxy
Securing Microsoft Teams with the miniOrange MS 365 CASB cloud security solution
Aug 22, 2023
Reverse Proxy
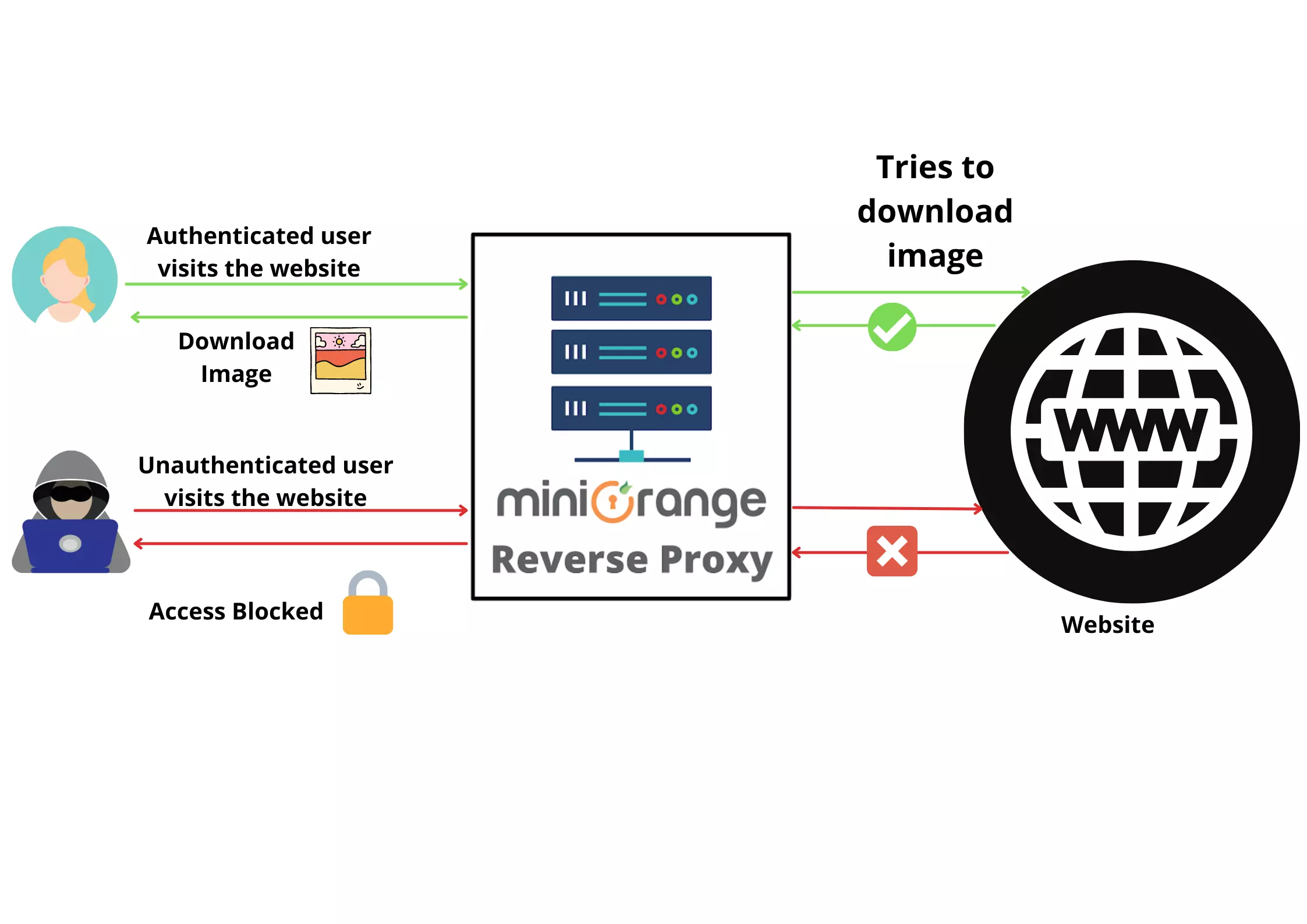
How to protect images from copying online by unauthorized users?
Aug 22, 2023
Reverse Proxy
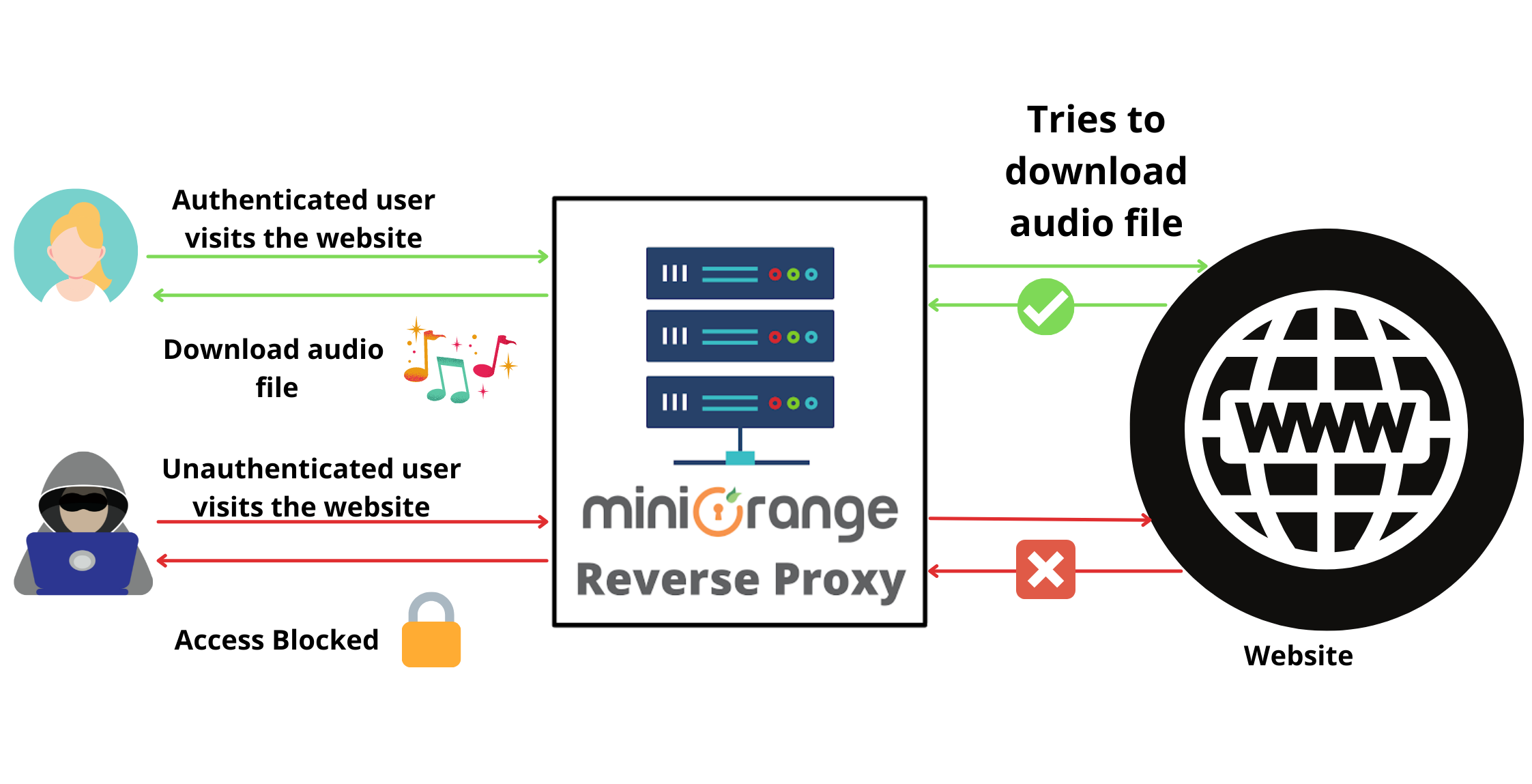
How to secure your audio files online from downloading?
Aug 22, 2023
Reverse Proxy
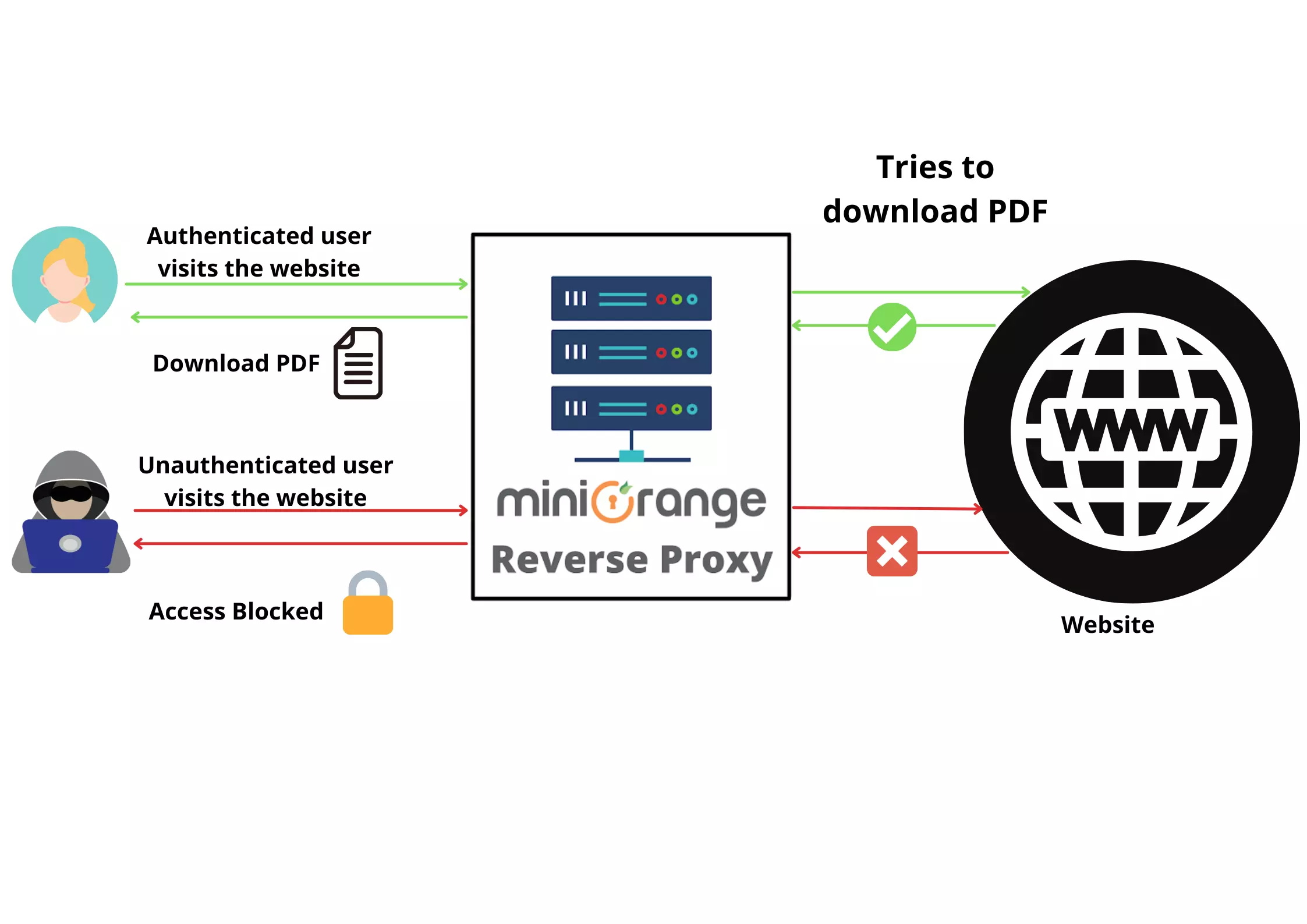
How to protect PDF copying online from unauthorized users?
Aug 22, 2023
Reverse Proxy
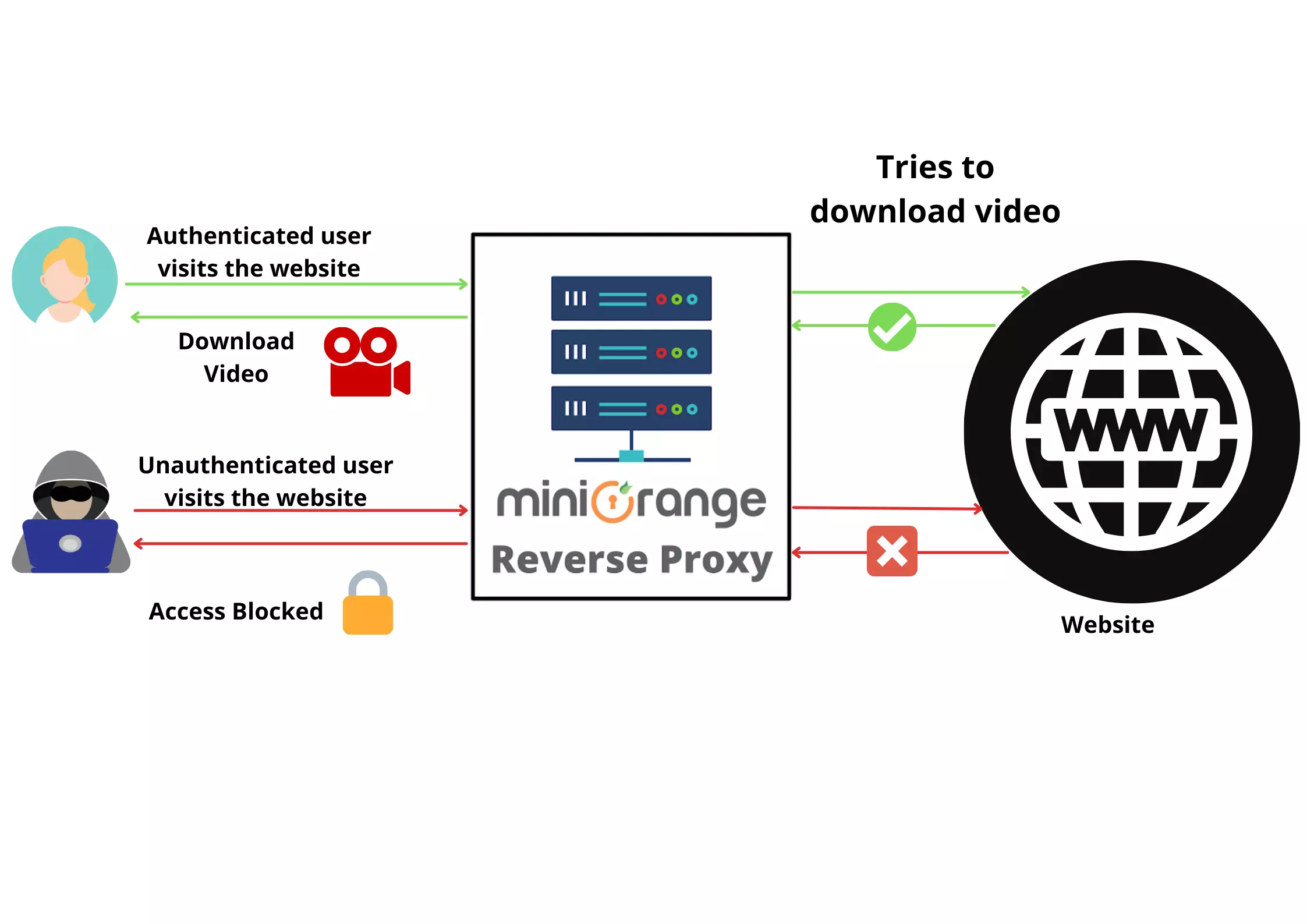
How to Protect video downloads online from users?
Aug 22, 2023
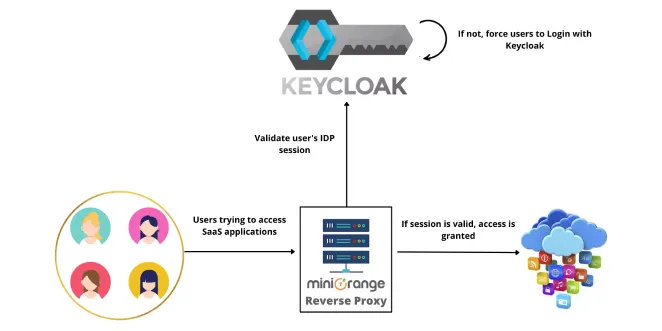
Reverse Proxy
Keycloak authentication with Reverse Proxy | Auth Proxy
Aug 22, 2023

Reverse Proxy
Cloud Application Security using Access Control with Reverse Proxy
Aug 22, 2023