With the boost of hybrid and remote work models, organizations are rethinking how this is changing the security needs and the gaps that are created. While VPNs have been the cornerstone of remote access security for decades, ZTNA is emerging as the preferred solution for modern enterprises.
miniOrange has been effective in helping organizations navigate this transition with extensive ZTNA solutions that deliver enhanced security, improved user experience, and better cloud integration.
This guide examines the key differences between ZTNA and VPN technologies and provides insights to help you choose the right security solution for your organization.
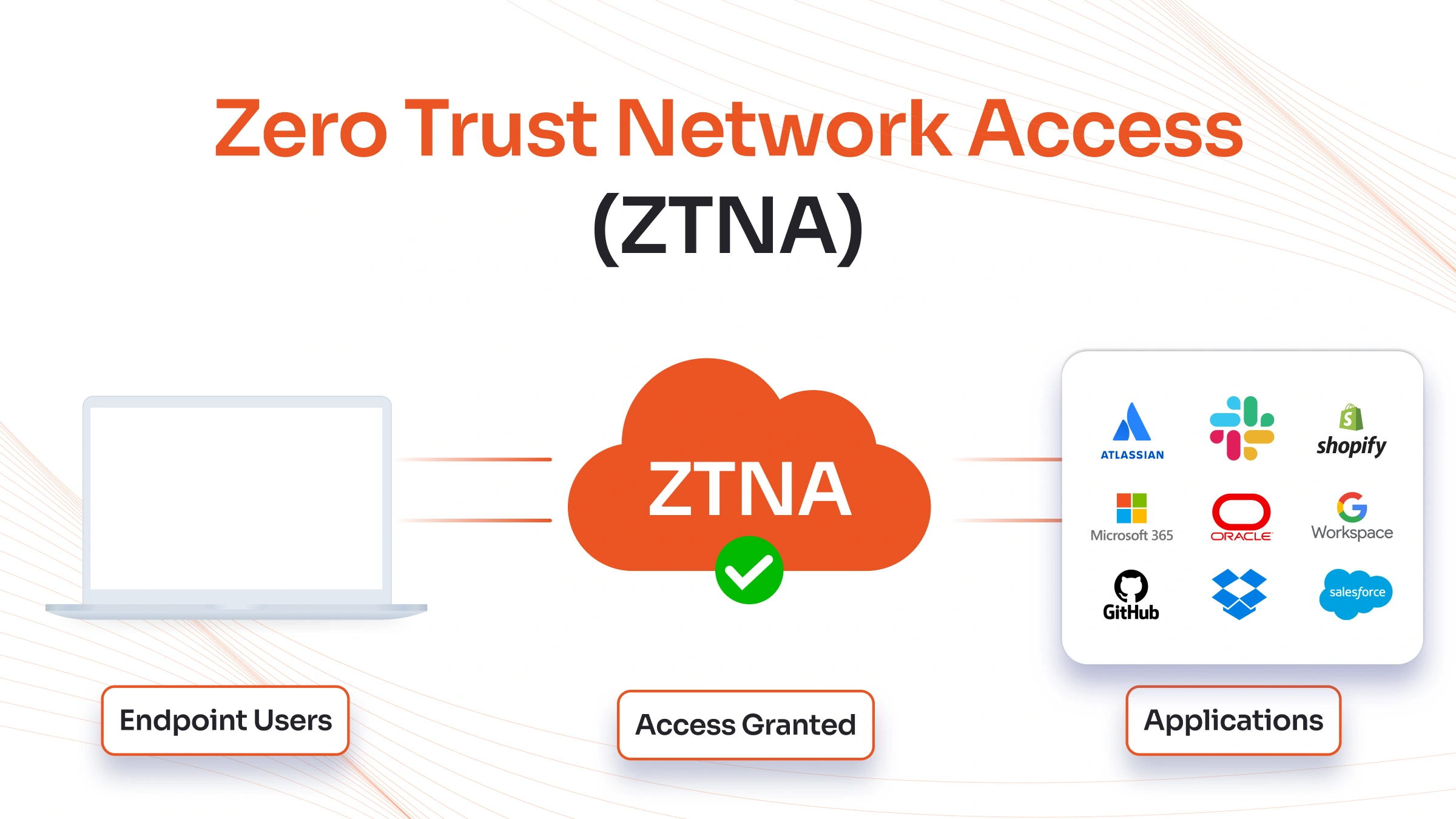
What is Zero Trust Network Access (ZTNA)?
ZTNA represents a comprehensive security framework that eliminates implicit trust from network architectures. Rather than assuming that users and devices within the network perimeter are safe, ZTNA treats every access request as potentially hostile and requires explicit verification before granting access to resources.
Core Principles of ZTNA
Never Trust, Always Verify: This foundational principle means that no user, device, application, or network flow is trusted by default. Every access request triggers a verification process that evaluates multiple factors, including user credentials, device compliance, location, time of access, and behavioral patterns.
Least Privilege Access: Users and devices receive the minimum level of access necessary to perform their intended functions. This principle operates at multiple levels: users only access applications they need, applications only access data they require, and network segments only communicate when necessary.
Assume Breach: ZTNA architectures operate under the assumption that adversaries have already gained some level of access to the environment. This mindset drives defensive strategies that focus on containing threats, detecting unusual behavior, and preventing lateral movement.
Verify Explicitly: All access decisions must be based on a detailed evaluation of available data points. This includes not just traditional authentication factors like passwords and tokens, but also device health status, network location, application sensitivity, and user behavior analytics.
Apply Least Privilege Principles: Access permissions are granted on a need-to-know basis and are continuously evaluated and adjusted. This dynamic approach means that user privileges can be automatically modified based on role changes, project requirements, or security incidents.
How ZTNA Works
1. Identity Verification Beyond Passwords
ZTNA begins with strong identity authentication, typically requiring Multi-Factor Authentication (MFA). This includes:
- Biometrics (fingerprint, facial recognition)
- Hardware tokens (YubiKeys, smart cards)
- Mobile authenticators (OTP apps like Google Authenticator or miniOrange Authenticator)
2. Device Trust and Posture Checks
Before granting access, ZTNA evaluates the security posture of the device:
- Is the OS up-to-date?
- Is antivirus software running?
- Is disk encryption enabled?
- Are there signs of malware?
Devices that fail these checks may be restricted or granted limited access until they comply with policy.
3. Context-Aware Access Control
ZTNA doesn’t just ask who you are. It asks where, when, and how:
- Location-based rules: Block or challenge logins from high-risk geographies.
- Time-based rules: Restrict access to business hours or maintenance windows.
- Network-based rules: Treat public Wi-Fi differently from corporate LAN.
This dynamic policy enforcement reduces the risk of unauthorized access from compromised environments.
4. Behavioral Analytics and Anomaly Detection
ZTNA continuously monitors user behavior to establish a baseline of normal activity.
- Usual login times and locations
- Frequently accessed apps
- Typical data usage patterns
If a user suddenly downloads large volumes of data at 3 a.m. from an unknown device, ZTNA can trigger alerts, require re-authentication, or block access until verified.
5. Application-Level Micro-Segmentation
Unlike VPNs that open the entire network, ZTNA creates individual encrypted tunnels to specific applications:
- Users only see and access what they’re authorized for.
- Lateral movement across the network is blocked.
- Sensitive resources remain invisible to unauthorized users.
ZTNA Architecture Components
Identity Provider (IdP) Integration: ZTNA solutions integrate with existing identity management systems to leverage established user directories and authentication mechanisms. This integration ensures consistent identity policies across all applications and services while maintaining centralized user management.
Policy Decision Point (PDP): The PDP evaluates all access requests against configured policies and makes allow/deny decisions. This component considers user identity, device status, requested resource, environmental context, and risk factors to make informed access decisions.
Policy Enforcement Point (PEP): PEPs act as gatekeepers that enforce access decisions made by the PDP. These components are distributed throughout the network and application infrastructure to ensure that policy enforcement occurs as close to resources as possible.
Secure Connector/Gateway: These components establish encrypted connections between users and authorized resources. Unlike VPN gateways that provide broad network access, ZTNA connectors create application-specific tunnels that limit access scope and improve security.
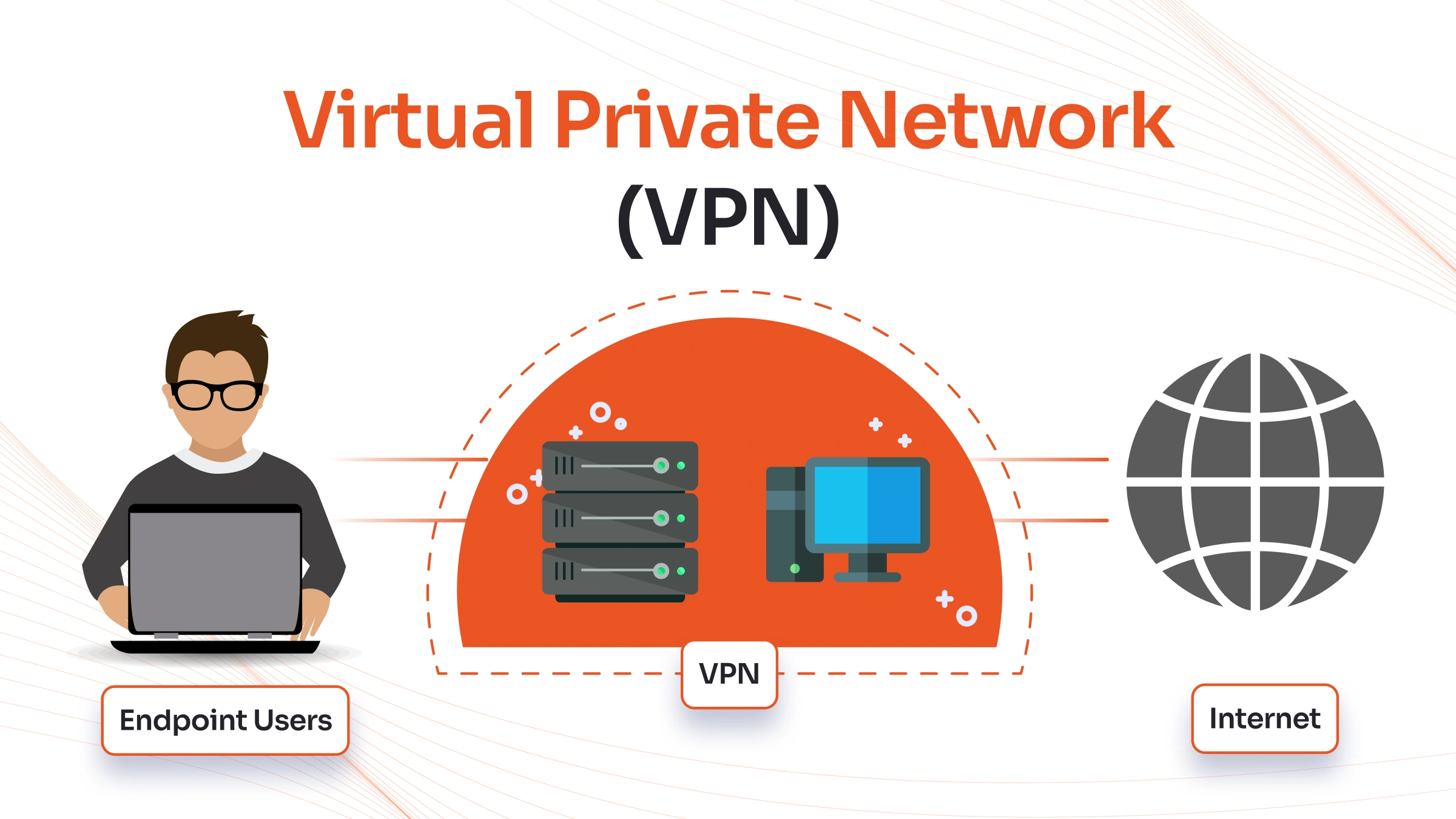
What is a VPN (Virtual Private Network)?
A Virtual Private Network creates a secure, encrypted tunnel between a user's device and a private network, enabling secure remote access to corporate resources over untrusted networks like the internet. VPNs have been the primary remote access solution for organizations worldwide, providing a cost-effective method to extend network boundaries to remote users and branch offices.
Core Principles of VPN
Perimeter Security Model: VPNs operate on the fundamental assumption that the internal corporate network represents a trusted zone, while external networks are untrusted. This binary security model creates a clear distinction between "inside" and "outside" the network perimeter. Once users successfully authenticate and establish a VPN connection, they are granted access to internal network resources as if they were physically present within the corporate office.
Encryption in Transit: All data transmitted through the VPN tunnel undergoes strong encryption to protect it from interception, eavesdropping, and tampering. VPNs typically employ industry-standard encryption protocols such as IPSec (Internet Protocol Security), SSL/TLS (Secure Sockets Layer/Transport Layer Security), or proprietary encryption methods.
Network Extension: VPNs effectively extend the corporate network infrastructure to remote locations by creating logical connections over physical internet infrastructure. This extension allows remote users to access internal servers, file shares, applications, and other network resources as if they were directly connected to the corporate LAN.
How VPNs Work
Authentication Process: VPN authentication typically involves multiple steps to verify user identity and authorize network access. The process usually begins with username and password credentials, which may be validated against local user databases, Active Directory, LDAP directories, or other identity management systems.
Tunnel Establishment: Once authentication is successful, the VPN client and server negotiate encryption parameters and establish a secure tunnel. This negotiation process includes selecting encryption algorithms, key exchange methods, and communication protocols that both endpoints support.
IP Address Assignment: Connected users typically receive internal IP addresses from the corporate network's address space, making their devices appear as if they are physically connected to the internal network. This addressing scheme enables access to internal resources that may be configured to only accept connections from corporate IP ranges.
VPN Architecture Types
Site-to-Site VPNs: These implementations create permanent encrypted connections between different network locations, such as branch offices and headquarters. Site-to-site VPNs enable seamless communication between geographically distributed networks without requiring individual user connections.
Remote Access VPNs: This configuration supports individual users connecting from various locations to access corporate network resources. Remote access VPNs are the most common implementation for supporting remote workers and mobile employees.
Client-Based VPNs: These solutions require installation of VPN client software on user devices, providing full control over connection establishment, authentication, and encryption settings. Client-based VPNs typically offer the most comprehensive security features and administrative control.
Clientless VPNs: Also known as SSL VPNs or web-based VPNs, these solutions provide access to specific applications or resources through web browsers without requiring client software installation. Clientless VPNs offer convenience and simplified deployment but may have limited functionality compared to client-based solutions.
Why ZTNA is Replacing VPNs
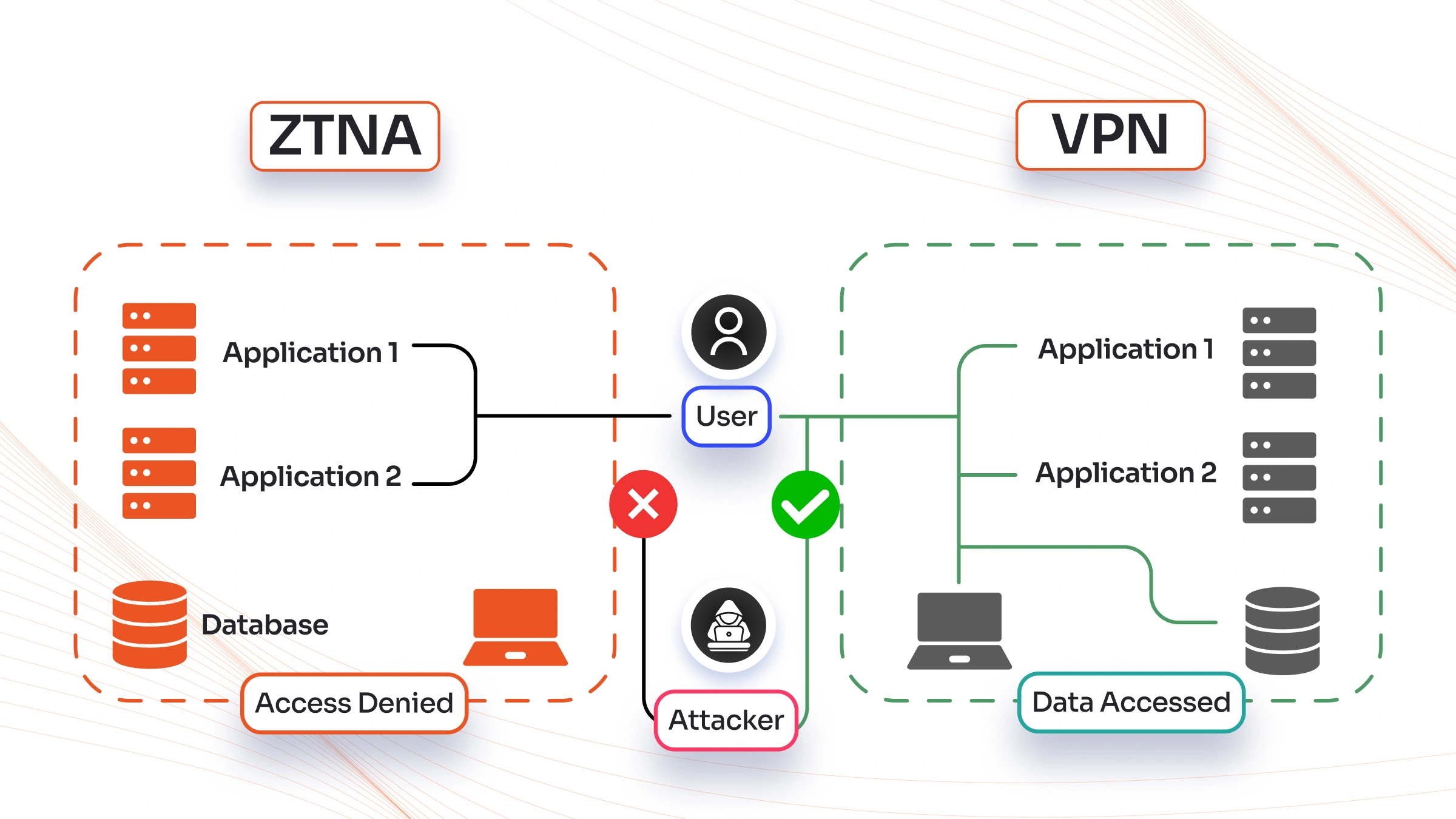
The primary change from VPNs to ZTNA is driven by the vital shift in how businesses operate. Several key factors are speeding this transition:
Cloud-First Transformation
Modern organizations increasingly rely on Software-as-a-Service (SaaS) applications, Infrastructure-as-a-Service (IaaS) platforms, and hybrid cloud architectures. Traditional VPNs force all traffic through corporate data centers, creating inefficient "tromboning" or "backhauling" scenarios where cloud-bound traffic must first route through on-premises infrastructure before reaching its final destination.
Advanced Persistent Threat Evolution
Cybercriminals have evolved their tactics to exploit the inherent trust assumptions of perimeter-based security models. Advanced Persistent Threats (APTs) often involve initial compromise through social engineering, phishing, or other techniques that bypass perimeter defenses. Once inside the network through VPN access, attackers can leverage broad network permissions to conduct inspection, escalate privileges, and move laterally to access high-value targets.
Regulatory Compliance Evolution
Industries subject to strict regulatory requirements are finding that VPN-based access models make it difficult to demonstrate compliance with data protection and privacy regulations. Regulations such as GDPR, HIPAA, PCI DSS, and SOX require organizations to implement granular access controls, maintain detailed audit trails, and demonstrate that sensitive data access is limited to authorized individuals for legitimate business purposes.
Scalability and Performance Demands
VPN scalability is fundamentally constrained by the processing capacity of centralized gateway devices. Adding capacity typically requires significant hardware investments and complex configuration changes. ZTNA solutions, built on cloud-native architectures, can scale elastically to accommodate varying user loads without requiring upfront capacity planning or hardware procurement.
Key Differences: ZTNA vs VPN
| Aspect | ZTNA | VPN |
|---|---|---|
| Security Model | Based on Zero Trust: “Never trust, always verify.” Every access request is evaluated in real time. | Perimeter-based: Once authenticated, users are trusted within the network. |
| Authentication & Authorization | Enforces strong MFA, continuous identity verification, and role-based access control (RBAC). | Typically uses single sign-on or basic credentials; limited authorization granularity. |
| Access Control | Application-specific access with least-privilege enforcement. Users only access what they need. | Network-level access; users can often move laterally once connected. |
| Architecture | Distributed, software-defined perimeter that adapts to cloud and hybrid environments. | Centralized gateway model; traffic is routed through VPN servers. |
| User Experience | Seamless, direct-to-app access with minimal latency. | Can introduce latency due to full-tunnel routing and backhauling. |
| Scalability | Cloud-native, easily scales with user and app growth. | Limited by hardware capacity and server load. |
| Visibility | Provides granular, real-time monitoring at the application level. | Offers network-level visibility but lacks app-specific insights. |
| Threat Response | Enables real-time adaptive access control and anomaly detection. | Requires manual policy updates and lacks behavioral analytics. |
| Compliance Support | Built-in audit logs, access reports, and policy enforcement for regulations like GDPR, HIPAA. | Often needs third-party tools for compliance tracking. |
ZTNA vs VPN – Benefits and Limitations
Both ZTNA and VPN have their own set of advantages and disadvantages. However, to make a decision as to what to choose for your business, it is important to understand them.
ZTNA Benefits
- Enhanced Security Posture: Continuous verification and least-privilege access significantly reduce cybersecurity attack surfaces
- Improved User Experience: Direct access to cloud resources eliminates VPN-related latency and connection issues
- Scalable Architecture: Cloud-native design supports unlimited users without infrastructure constraints
- Granular Control: Application-level access policies provide precise control over resource access
- Better Visibility: Strong monitoring and analytics enable proactive threat detection
- Compliance-Ready: Built-in audit trails and reporting support regulatory requirements
ZTNA Limitations
- Implementation Complexity: Initial deployment requires careful planning and potentially significant architectural changes
- Learning Curve: IT teams need training on Zero Trust principles and ZTNA management tools
- Cost Considerations: While often more cost-effective long-term, initial implementation may require significant investment
- Legacy System Integration: Older applications may require modifications to work effectively with ZTNA solutions
VPN Benefits
- Proven Technology: Decades of deployment experience and well-understood implementation processes
- Simple Deployment: Relatively straightforward setup and configuration for basic use cases
- Universal Compatibility: Works with virtually any application or service without modification
- Cost-Effective for Small Deployments: Can be economical for organizations with limited remote access needs.
VPN Limitations
- Security Vulnerabilities: Broad network access increases risk of lateral movement and data breaches
- Performance Issues: Centralized architecture can create bottlenecks and degrade user experience
- Scalability Constraints: Hardware-based solutions have fixed capacity limits
- Cloud Access Inefficiencies: Backhauling cloud traffic through corporate networks wastes bandwidth and increases latency
- Limited Visibility: Coarse-grained monitoring makes it difficult to detect and respond to threats
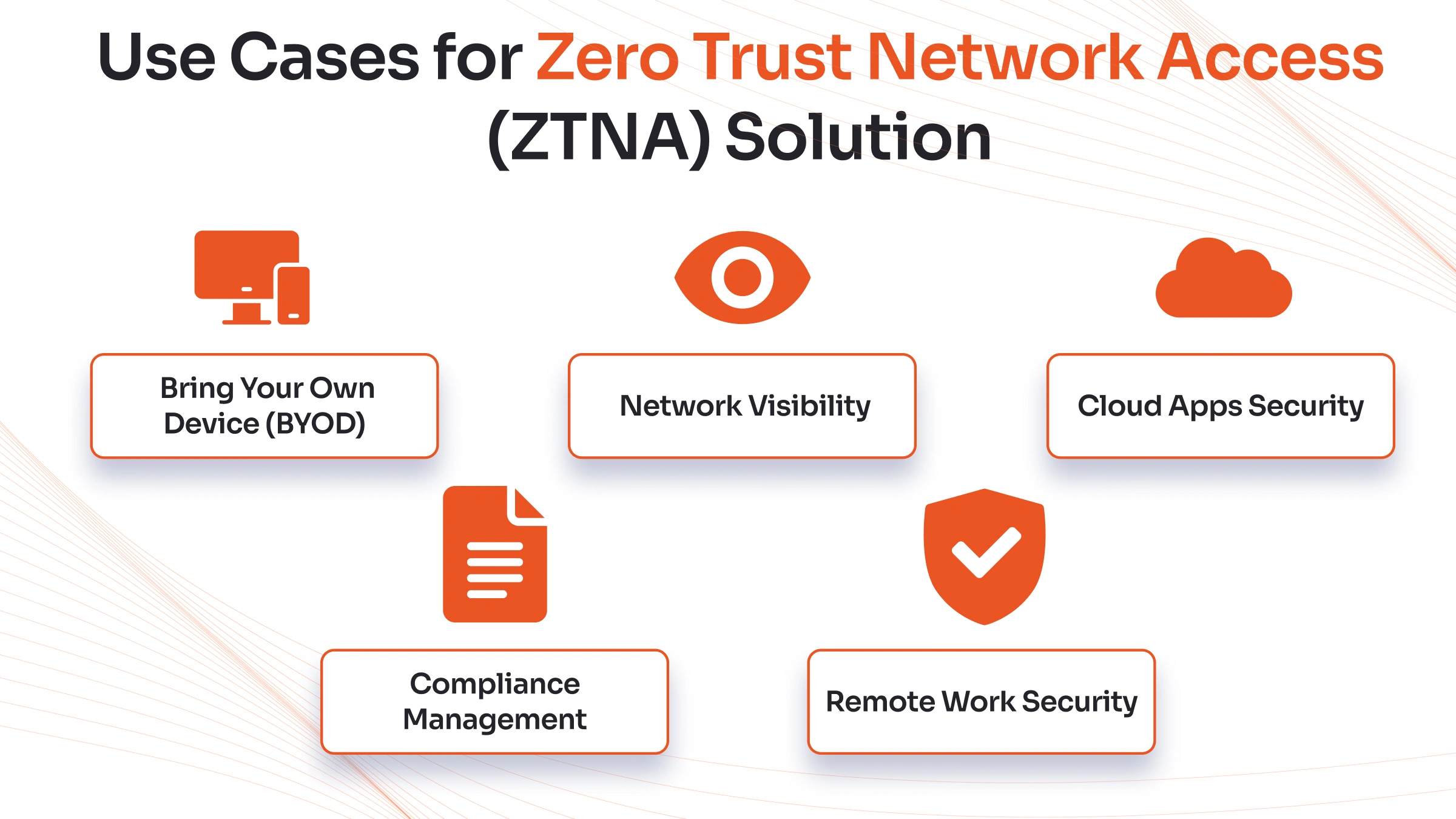
Top Use Cases for ZTNA Solutions
ZTNA's use cases extend beyond basic security improvements to promote operational efficiency, cost optimization, and strategic business enablement.
Remote Work Security
The distributed workforce requires secure access to corporate resources from various locations and devices. ZTNA solutions provide consistent security policies regardless of user location, ensuring that remote employees have secure remote access to necessary applications without compromising organizational security posture.
Cloud Apps Security
Organizations leveraging multiple SaaS applications benefit from ZTNA's ability to provide secure, direct access to cloud services. This approach eliminates the need to route cloud traffic through corporate networks, improving performance while maintaining security controls.
Bring Your Own Device (BYOD)
ZTNA solutions excel at managing access from personal devices by implementing device trust assessments and application-level controls. This capability enables organizations to support BYOD policies without exposing corporate networks to unmanaged device risks.
Network Visibility
Effortless monitoring and analytics capabilities provide unprecedented visibility into user behavior and resource access patterns. This visibility enables proactive threat detection and supports data-driven security decisions.
Compliance Management
Granular access controls and detailed audit trails simplify compliance with regulatory requirements such as GDPR, HIPAA, and SOX. Automated reporting capabilities reduce the administrative burden of compliance management while providing evidence of adherence to security standards.
When to Choose VPN or ZTNA?
Choose VPN when:
- Your organization has a small, stable remote workforce
- Legacy applications cannot be easily modified or replaced
- Budget constraints require minimal upfront investment
- Your security requirements are primarily focused on basic encryption and access control (MFA VPN)
Choose ZTNA when:
- Your organization supports a large or growing remote workforce
- Cloud applications constitute a significant portion of your IT infrastructure
- You require granular access controls and transparent monitoring
- Compliance requirements demand detailed audit trails and reporting
- You want to implement a forward-looking security strategy that supports business growth
How miniOrange Implements Zero Trust
Identity-Centric Architecture
miniOrange starts by strengthening identity verification through seamless integration with existing directories. Its authentication solution and adaptive security model layers in biometrics, mobile authenticators, and real-time risk scoring to dynamically adjust verification requirements. This enables both high security and uninterrupted productivity.
Intelligent Device Trust Framework
Every access request is evaluated in part by the device’s security posture. miniOrange performs assessments such as OS compliance, encryption status, and the presence of antivirus protection. Whether the device is managed or unmanaged, its trustworthiness directly influences access decisions.
Behavioral Risk Analytics
miniOrange continuously observes behavioral signals to build user activity baselines. When deviations, like off-hours access or unusual file activity, occur, the system automatically recalibrates access privileges or triggers alerts. This protects against insider threats and compromised accounts without disrupting normal operations.
Cloud-Native Flexibility
Built on a globally distributed cloud-native architecture, miniOrange ensures reliability and low-latency access for users across geographies. It integrates seamlessly with AWS, Azure, and GCP, allowing organizations to apply consistent Zero Trust policies across hybrid or multi-cloud environments.
Features of miniOrange ZTNA Solution
Adaptive Multi-Factor Authentication (MFA)
miniOrange, as your security software solution partner, uses adaptive MFA that adapts based on real-time risk, factoring in location, device trust, and user behavior. Low-risk logins may require minimal verification, while high-risk attempts trigger stronger methods like biometrics or tokens. With support for over 15+ authentication methods, it balances security with user convenience.
Single Sign-On (SSO) Integration
The miniOrange SSO offers capabilities across 6000+ pre-integrated apps, including SaaS, legacy, and custom systems. Users authenticate once to securely access all resources, reducing password fatigue and improving productivity. This centralized access model also simplifies policy enforcement and auditing.
Privileged Access Management (PAM)
miniOrange PAM enforces strict controls for high-privilege accounts through just-in-time access and session monitoring. Admin actions are recorded for audit trails, and real-time alerts flag suspicious behavior. Password vaulting and rotation eliminate shared credentials while maintaining compliance with internal policies.
Cloud Application Security
miniOrange integrates natively with platforms like Microsoft 365, Google Workspace, and Salesforce to enforce consistent policies. CASB features provide visibility into shadow IT, data loss prevention, and compliance risks. Encryption, residency controls, and policy enforcement protect sensitive cloud data.
Real-Time Risk Assessment and Response
With risk-based authentication, access decisions are guided by dynamic risk scores based on user behavior, device posture, and environmental context. The system can automatically adjust access, prompt re-authentication, or block suspicious activity. SIEM integration enables coordinated threat response and incident management.
Conclusion
The evolution from VPN to ZTNA represents a critical shift that extends beyond technology selection to encompass organizational security philosophy and future readiness. While VPNs remain viable for specific use cases, ZTNA's alignment with modern business requirements makes it the preferred choice for forward-thinking organizations.
ZTNA's security model, enhanced user experience, and cloud-native architecture position it as the foundation for sustainable cybersecurity strategies. Organizations implementing ZTNA solutions like miniOrange's platform for SSO, ULM, and MFA products gain not only superior security capabilities but also operational efficiency and competitive advantages in an increasingly digital business environment.
FAQs
What are the disadvantages of ZTNA?
ZTNA implementations can be complex and require significant upfront planning and investment. Organizations may face challenges integrating legacy applications that weren't designed for Zero Trust architectures. Additionally, the learning curve for IT teams transitioning from traditional network security models can be steep, requiring training and potentially external consulting services.
Will Zero Trust replace VPN?
While ZTNA is increasingly replacing VPNs in many organizations, complete replacement depends on specific use cases and organizational requirements. VPNs may continue to serve niche applications, particularly for legacy systems or simple remote access scenarios. However, the trend strongly favors the adoption of ZTNA for enterprise security strategies.
What is the purpose of ZTNA?
ZTNA's primary purpose is to provide secure, granular access to applications and resources based on verified user and device identity. It aims to eliminate the implicit trust assumptions of traditional network security models by continuously verifying every access request and implementing the principle of least privilege.
Is Zero Trust better than VPN?
Zero Trust is generally superior to VPN for modern enterprise security requirements due to its granular access controls, better cloud integration, enhanced visibility, and adaptive security capabilities. However, "better" depends on specific organizational needs, existing infrastructure, and security requirements.
How does ZTNA improve compliance?
ZTNA enhances compliance through detailed audit trails, granular access controls, and monitoring capabilities. These features provide the documentation and evidence required for regulatory compliance while automating many compliance-related processes, reducing administrative burden, and ensuring consistent adherence to security standards.



Leave a Comment