Social engineering attacks human trust through psychological methods, which enable attackers to access protected systems that have strong security protocols. Security systems face their biggest threat from human beings because people will continue to be the main security risk during 2025. The Unit 42 division of Palo Alto Networks states that social engineering attacks now account for 36% of total data breaches because attackers use AI to generate deceptive content, which they spread across email and chat platforms and social media platforms.
Attackers in the present day employ deepfakes together with multi-stage phishing tactics, which duplicate actual business procedures. Organizations need to improve their user training programs and monitoring systems and defense protocols because social engineering awareness serves as their essential cybersecurity requirement.
This article sheds light on how social engineering scams happen, the driving force behind them, their types, how to protect enterprises from social engineering attacks and how miniOrange can be considered helpful for the same.
Mechanics of Social Engineering Attacks
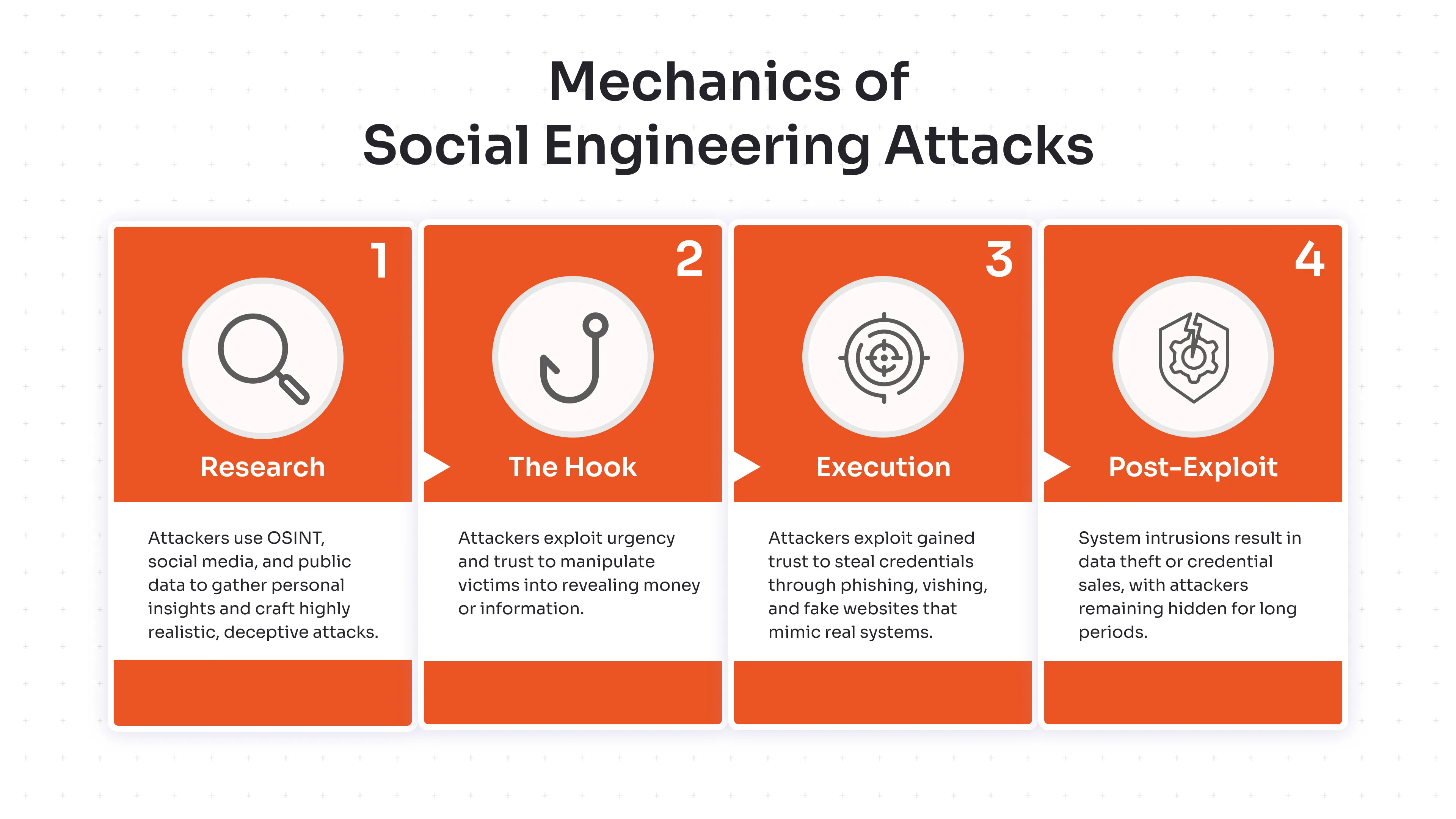
Social engineering attacks use deceptive methods that depend on human trust to achieve their goals. The successful execution of social engineering attacks requires attackers to complete four essential stages, which include research followed by hook and execution and post-exploit phases. Organizations can detect warning signs of attacks through understanding the attack mechanics that occur before damage happens. You may wonder how exactly these deadly social engineering attacks happen and what the steps involved in them are.
1. Research (Reconnaissance):
Attackers perform intelligence gathering by using Open-Source Intelligence (OSINT) and social media profiles and public databases. Attackers use the collected target information along with relationship maps and communication patterns to build authentic-looking traps. Attackers find sufficient personal data about victims to create realistic attacks for which the victims can fall.
2. The Hook:
Attackers use psychological triggers, which include urgency, fear, and curiosity, to lure their victims into taking action. The most common social engineering attacks include fake LinkedIn job advertisements and fake password reset notifications and fake emails that impersonate CEOs. The target falls victim to emotional manipulation on the basis of fake trust, which causes them to act in favor of attackers without checking the authenticity and mostly helps attackers with monetary or information gains.
3. Execution:
Attackers exploit the trust they have gained to get into their critical information, such as user credentials, distribute malicious files, and intercept authentication codes. Users fall victim to phishing, vishing, and watering hole attacks, which take them to fake websites that need them to enter their real credentials that the attackers later steal and get into their real systems.
4. Post-Exploit:
System intrusions by attackers lead to two common outcomes. Attackers either steal vital system data to keep access for future attacks, or they sell stolen user credentials on dark web marketplaces. The attackers stay hidden between systems because their digital tracks stay hidden for long periods of time.
The present state of advanced technology has increased the danger level of cyber attacks beyond what they used to be. Attackers combine AI technology with deepfakes to generate fake content that looks authentic through their advanced attack techniques. People now face increased challenges in detection because they receive genuine messages alongside fake content that appears authentic.
The dark web uses watering hole attacks to target websites that professionals from particular industries visit frequently for their attacks.
Teams gain the ability to defend against attacks through complete understanding of attack mechanics, which enables them to develop multiple security layers and train employees to recognize manipulation tactics before attackers launch their attacks.
Why Do Attackers Carry Out Social Engineering Scams?
Social engineering scams succeed because human weaknesses consistently overcome the security measures that technology provides. The attackers use psychological tactics to manipulate victims through fear and trust and impulsive behavior, which results in data disclosure and link activation. Social engineering attacks use psychological triggers, which force victims to follow instructions without thinking logically.
Key Psychological Triggers in Social Engineering Attacks:
- Authority: Scammers create fake CEO and IT support and official impersonations to force victims into following orders without any doubt. Users who carry out cyberattacks follow orders from what they think are official sources without checking the true identity of these sources.
- Urgency: Alerts like “Act now or lose access” spark panic in social engineering psychological manipulation. Victims skip checks under time pressure.
- Reciprocity: Free offers or favors create obligation, pushing info sharing. This classic trigger fuels phishing success rates.
- Fear: Threats of breaches or fines force hasty actions. Fear amplifies risks in human behavior during cyberattacks.
- Familiarity: Spoofed emails from “trusted” contacts lower defenses. Familiarity builds false security in social engineering scams.
- Event-Tied Exploits: Attacks timed to tax deadlines or sales events feel real. Contextual relevance boosts compliance in psychological manipulation.
Spotting social engineering psychological triggers empowers teams to fight back. Train staff to pause, verify, and question. Turn human behavior in cyberattacks into your strongest shield against scams. Stay vigilant for safer digital habits.
Types of Social Engineering Attacks
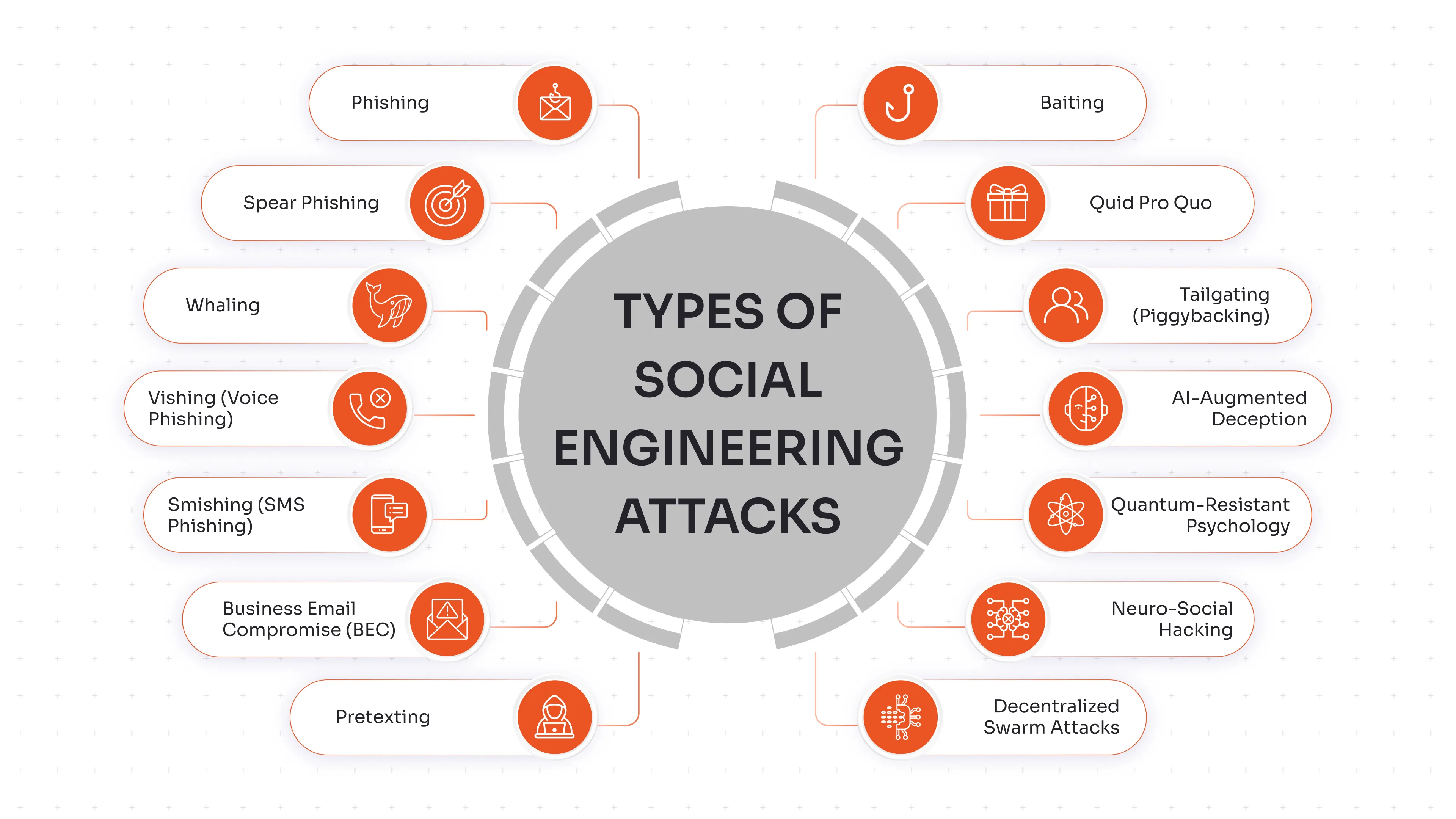
Social engineering remains the top cyber threat in 2025, accounting for over 70% of global data breaches according to Verizon’s Data Breach Investigations Report. Attackers now blend AI, psychology, and personalization to bypass traditional defenses and exploit human trust faster than ever.
Phishing
Attackers use fake emails and websites that duplicate official brand logos to trick users into revealing their personal data through phishing scams. The attackers generate instant stress through fake account alerts and password reset messages, which force users to visit dangerous websites by clicking on their links. Users need to verify sender information before clicking links, while anti-phishing protection should be enabled to stop phishing attacks. More examples are explained here phishing attacks.
Spear Phishing
Spear phishing attacks focus on particular people through information that attackers obtain from LinkedIn and Twitter platforms. Attackers create fake messages that appear to be from coworkers about critical contract updates. Organizations need to train their staff about OSINT threats while enforcing MFA and establishing alternative verification methods to stop spear phishing attacks.
Whaling
The whaling attack method focuses on high-level business personnel through fake corporate emergencies, which include merger announcements and legal proceedings. Organizations need to create executive-level phishing simulation programs and financial approval systems and official channel verification requirements for sensitive requests to stop attackers who use authority and urgency for credential sharing and fund transfer requests.
Vishing (Voice Phishing)
Attackers use fake caller IDs and robocalls to create fake bank and IT department identities. The attackers use fake account freeze warnings to force victims into revealing their PINs and OTPs. All unexpected calls that request confidential information need employees to exercise caution because they should disconnect right away and verify the call through the official number before taking any further steps.
Smishing (SMS Phishing)
Smishing attacks use user trust in text messages to display fake alerts that pretend to show package delivery issues and payment verification needs. The malicious links in these texts lead to malware installation or credential theft. Users need to stay away from links sent by unfamiliar messages because their mobile antivirus software operates and mobile device management systems track SMS activities to detect security threats.
Business Email Compromise (BEC)
BEC attacks use fake executive emails and domain names to authorize fake wire transfer requests. Attackers now use artificial intelligence to develop new impersonation methods, which enable them to duplicate both writing patterns and personal authentication elements. Organizations need to prevent BEC attacks through the implementation of DMARC and SPF and DKIM and by creating wire transfer approval systems and executive request verification through phone calls.
Pretexting
Pretexting works through fabricated identities like “IRS auditors” or “security officers” to build false trust. Attackers manipulate conversations using detailed background knowledge to trick targets into sharing confidential data. Defend by verifying identities through secondary channels, minimizing data exposure on social media, and enforcing call-back or verification protocols.
Baiting
Users download infected USBs and promotional content because they want to explore while believing it contains payroll or bonus information. The malware execution on these devices allows attackers to move between different network segments. Three security measures enable organizations to prevent baiting attacks by blocking external media access, teaching staff to avoid inserting unknown devices and enabling endpoint protection systems to detect unauthorized program execution.
Quid Pro Quo
Cybercriminals use quid pro quo attacks by presenting themselves as technical support who provide free virus scanning services and software update services. Victims share their login details with unauthorized parties who then obtain distant access to the system. Verify all your support requests from the IT department while using admin controls and remote access to watch systems to detect any suspicious logins.
Tailgating (Piggybacking)
Unauthorized people use the practice of tailgating to enter restricted areas by following authorized personnel who use fake badges or display politeness. Physical access breaches often go unnoticed. Prevent it through employee awareness, badge-based door systems, and on-site monitoring that requires authentication for every individual entering restricted zones.
AI-Augmented Deception
Generative AI now enables deepfake videos and cloned voices that simulate executives in real time, making vishing almost indistinguishable from legitimate calls. Attackers use deepfakes to bypass voice recognition systems. Combat this with liveness detection, callback verification policies, and AI-driven fraud detection that analyzes facial and audio integrity.
Quantum-Resistant Psychology
Attackers exploit “quantum decryption” fear by tricking crypto investors into revealing keys under the illusion of emergency quantum hacks. These scams thrive on tech hype and panic. Prevent them through awareness training emphasizing that quantum threats are decades away, verifying communication sources, and using hardware wallets to secure digital assets.
Neuro-Social Hacking
The technology of neuro-social hacking depends on brain-computer interfaces, which read neural signals to control automatic human actions. The attacker generates fake alerts, which trigger victims to take dangerous actions right away. As BCIs evolve, apply isolation policies for neural devices, monitor behavioral anomalies, and conduct cybersecurity testing specific to neurotech systems.
Decentralized Swarm Attacks
These attacks use coordinated Web3 bots or AR/NFT campaigns to manipulate users during physical or virtual events. Swarms exploit digital trust to breach IoT or smart city perimeters. Prevent them by enforcing geofenced access control, monitoring blockchain anomalies, and verifying event credentials through decentralized identity frameworks.
Read Types of Cyber Security Attacks
Rising Trends in Social Engineering
Social engineering attacks now use sophisticated psychological and technical methods to target people and businesses through multiple attack vectors, which go beyond traditional email scams and deceptive links. Social engineering attacks now cause more than $2.77 billion in worldwide damage each year, according to recent studies, which show these attacks bring the most financial gain to cybercriminals.
Key trends in social engineering scams include:
- AI-driven personalization: Attackers employ artificial intelligence to create deceptive messages that duplicate employee communication styles for developing scams that show near-perfect imitation of authentic messages.
- SEO poisoning: Cybercriminals use search engine result manipulation to place dangerous links at the top of search results, which leads users to websites that steal information or distribute malicious software.
- Non-phishing scams: The number of help desk and IT support scams continues to rise because attackers establish fake technical profiles to obtain employee passwords and MFA token reset information.
- Multi-vector operations: Threat actors conduct multi-channel attacks through phone calls and text messages and emails and fake websites to create authentic-looking campaigns, which increase attack believability and detection difficulty.
Organizations need to create defense systems that will counter the increasing complexity of social engineering attacks. Organizations should focus on three main security measures, which include ongoing security awareness training, Zero Trust access controls and AI-based anomaly detection systems.
The combination of technological defenses with employee education about social engineering attacks creates an effective protection system against cyber threats.
Case Studies of Social Engineering Attacks
Social engineering attacks use human trust to create financial devastation through impersonation and urgent tactics, which overcome technological security systems. The actual incidents showed new attack methods that demonstrate organizations must keep their training and verification protocols active at all times. The schemes lead to yearly financial losses of billions of dollars for business operations.
CEO Fraud (Business Email Compromise)
The attackers create fake executive email accounts to make finance staff transfer money through urgent requests. The 2024 IC3 report from the FBI shows BEC attacks resulted in more than $2.7 billion in losses, which contributed to $16.6 billion in total cyber fraud.
One firm lost $956,342 to a fake real estate closing email, proving how authority blinds even cautious teams.
Supply Chain Attacks
Hackers target vendor emails to push malware through trusted invoices. Ivanti's 2024 report found social engineering matches software flaws as top entry points, with 32% of warehouse attacks starting this way. Phishing developers or suppliers lets attackers inject code across partner networks.
Scattered Spider and Workday Breaches
This group uses SIM swaps, vishing, and fake helpdesk calls to steal MFA codes from Okta and Workday users. They escalate to exfiltrate HR data and deploy ransomware via SSO abuse. Recent tactics include fake Okta sites during calls, amplifying fears of ShinyHunters alliances.
Brand Impersonations (Amazon, PayPal)
Scammers clone sites and emails for Amazon and PayPal to snag credentials. FTC data shows 34,000 Amazon scam reports in 2023, with Amazon hitting 80% of brand phishing in late 2025 Black Friday surges. PayPal ranks high too, often via fake transaction alerts or overpayment tricks
These cases demand layered defenses like AI-driven email checks and phishing drills to turn vulnerabilities into strengths.
How to Detect and Mitigate Social Engineering for Enterprises?
Top strategies to prevent social engineering attacks focus on training people, hardening identity controls, and layering new tech like AI and quantum-safe security on top of Zero Trust. This section keeps it practical so a security lead can turn it into an internal playbook.
Train People To Spot Red Flags
Run mandatory, role-based awareness training that covers phishing, pretexting, deepfake voice calls, tailgating, and help desk scams. Use simulated phishing, gamified quizzes, and monthly threat newsletters so employees instinctively question urgency, fear, or “secret” requests.
Teach staff to verify unusual requests through out-of-band channels like a known phone number or internal chat, not by replying to the same email or message. Build a simple “stop, verify, report” script and make managers model that behavior in daily work.
Enforce MFA, SSO, And Zero Trust
Make phishing-resistant MFA mandatory for all external access, admin actions, and high-value apps so stolen passwords alone cannot grant access. Use a Zero Trust model that validates user identity, device posture, and context on every request instead of trusting a single login or network segment.
Expose applications through a secure SSO solution such as miniOrange, so users authenticate once with strong MFA from a trusted MFA provider and access only authorized apps under unified policies and logging. Combine this with just-in-time access and approval workflows for sensitive actions that social engineers love to target.
Deploy Filters, AI, And Deepfake Detection
Use advanced email and messaging security that sandboxes links and attachments, blocks spoofed domains, and flags lookalike senders before users even see them. Add AI-powered deepfake detectors that scan voice, video, and images for manipulation artifacts and behavioral anomalies to counter deepfake-enabled scams.
Integrate deepfake detection APIs or gateways into conferencing, contact center, and approval workflows so finance or HR teams get real-time warnings on suspicious calls or videos. Treat any high-value change request that arrives via newly used channels or synthetic-looking media as a trigger for extra verification.
Go Quantum Safe With Key Management
Plan for “harvest now, decrypt later” attackers by introducing quantum-safe cryptography for long-lived credentials, backups, and identity systems. Use quantum-safe or crypto-agile key management backed by hardware security modules so you can rotate away from vulnerable algorithms without breaking IAM.
Protect group keys, API credentials, and machine identities with lattice-based or other post-quantum schemes where feasible, especially for privileged access and high-impact automation. Document a crypto agility roadmap so your IAM stack does not become the weakest link once practical quantum attacks arrive.
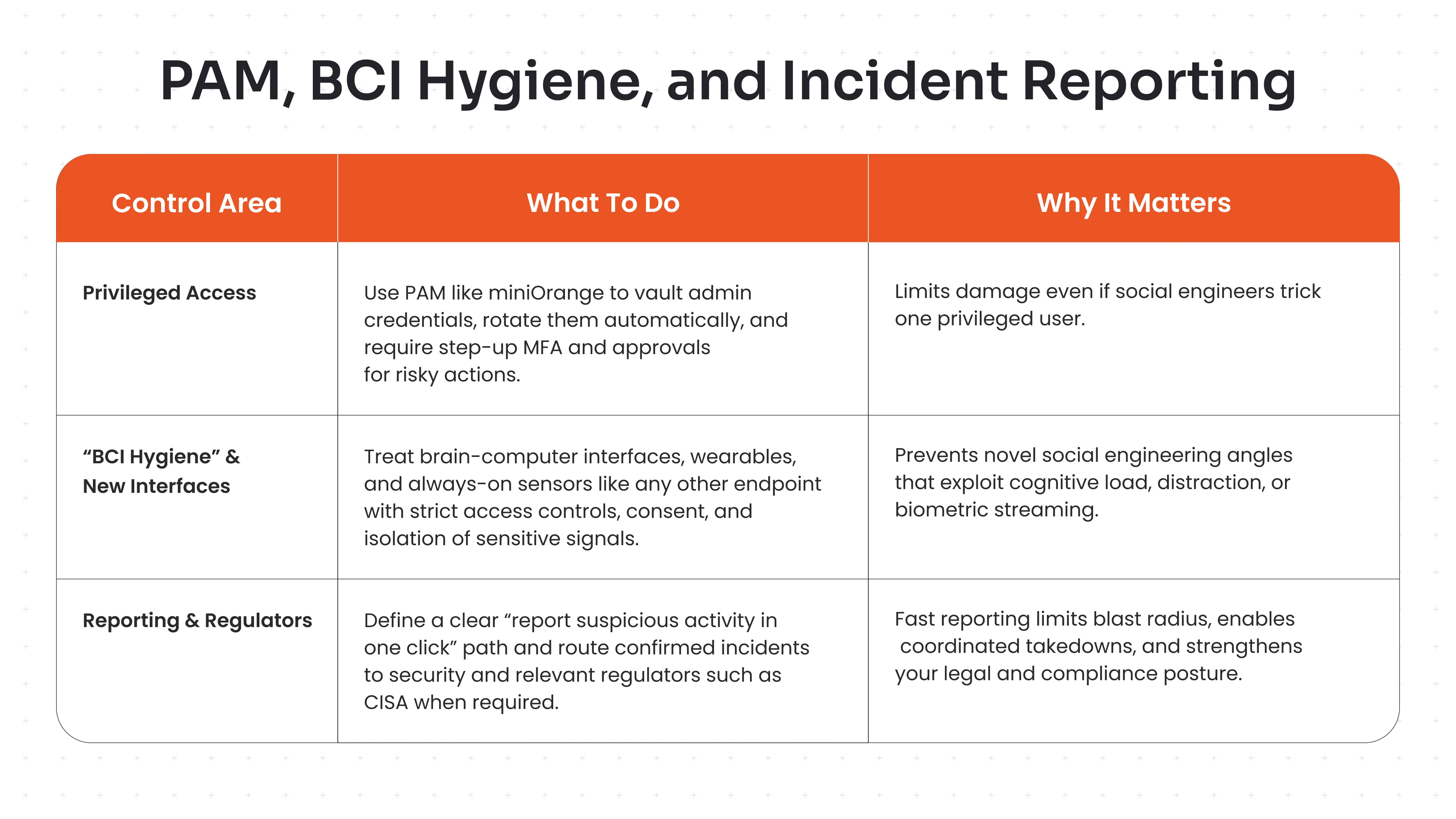
Add PAM, BCI Hygiene, and Incident Reporting
How Does IAM Help with Preventing Social Engineering Scams?
IAM systems function as protective mechanisms that control user access permissions and authentication methods to stop social engineering scams.
- Social engineering scams use deceptive tactics to obtain user credentials, which attackers then use to bypass security systems and access systems without permission. The Identity and Access Management (IAM) security framework authenticates users while determining their system access rights.
- IAM systems protect organizations through three main security features, which defend against social engineering attacks.
- The system requires users to authenticate through multiple authentication methods such as SSO and MFA, which use biometric data together with one-time passwords and authenticator apps to protect against password theft attacks.
- The system provides users with only the required permissions that correspond to their assigned roles to reduce attack surfaces.
- The system monitors user login activities to detect abnormal behavior, which triggers adaptive authentication and risk-based authentication security controls to prevent unauthorized system access.
- The system provides users with simple identity verification processes through its centralized management system, which blocks attackers from using unmanaged or abandoned accounts.
- The system sends security alerts to users through notifications, which help them detect and avoid phishing attacks.
The security features work together to minimize the impact of social engineering attacks that target employees and stolen credentials. A properly designed IAM system turns employee errors into security risks which organizations can manage to protect their data assets.
Your organization needs to start its protection work immediately. Experience how intelligent identity security systems block social engineering attacks effectively with miniOrange free IAM trial.
Schedule a free IAM demo with our engineers. Contact us today.
FAQs
What is an example of a social engineering attack?
A common example is phishing, where attackers send fake emails (often from banks) to trick users into entering their login details.
What are the most common signs of social engineering attacks?
Unexpected links or attachments, urgent messages demanding quick action, and offers that seem too good to be true.
What are the red flags for social engineering?
Suspicious sender addresses, spelling or grammar errors, and unexpected requests for personal or work information through email, calls, or social media.




Leave a Comment