Need Help? We are right here!
Search Results:
×Agentless Privilege Access Management (PAM) is a security solution that allows organizations to manage, monitor, and control privileged access without installing agents on their target systems.
Agentless PAM solutions offer a hassle-free deployment process, simplifying implementation while saving time and resources. By eliminating the need for PAM agents, organizations can mitigate risks associated with agent vulnerabilities, ensuring a more secure privileged access management environment.
Agentless PAM solutions provide a streamlined approach to managing and securing privileged access, by leveraging existing protocols and authentication methods, these solutions simplify deployment and management, as they eliminate the need for endpoint installations. This agentless approach not only enhances scalability, allowing organizations to adapt seamlessly to changing infrastructures but also reduces system impact, avoiding potential interoperability issues associated with multiple agents. This makes agentless PAM an efficient and effective choice for modern cloud environments.







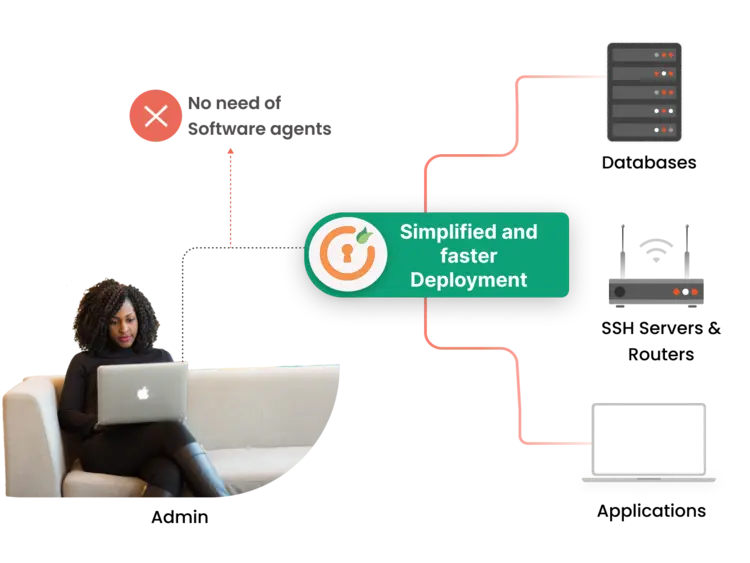
Our solution eliminates the need for installing software agents on each endpoint, streamlining deployment and saving valuable time and resources. There's no requirement for agents or connectors to connect to databases, SSH servers, routers, or applications.
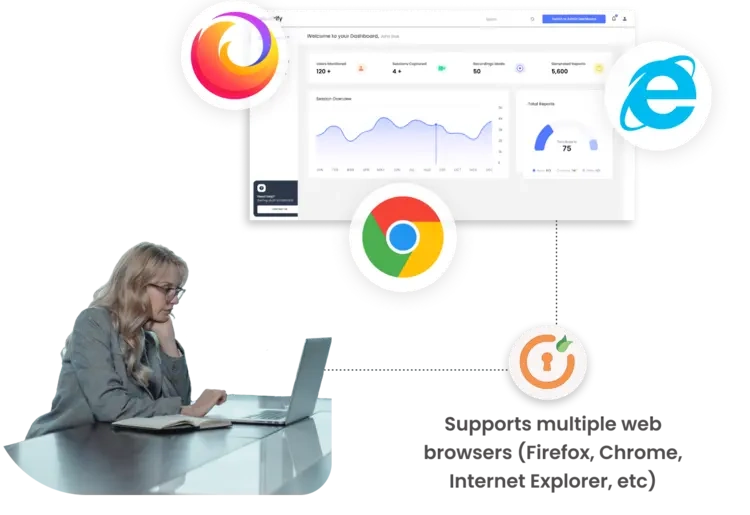
The solution is compatible with various web browsers, including Firefox, Chrome, Internet Explorer, and others, ensuring flexibility and compatibility for end-users.
After this time frame ends, the elevated privileges are automatically withdrawn.
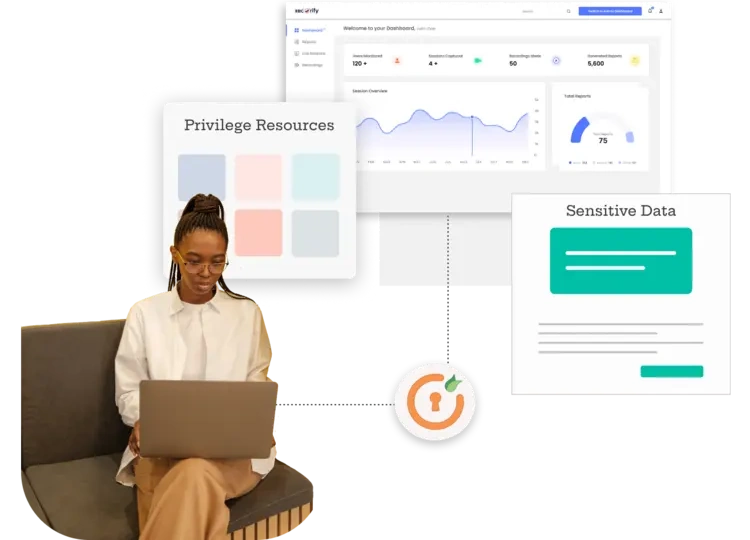
Users can access privileged resources without dedicated client applications, providing enhanced in-browser user convenience and a seamless experience.
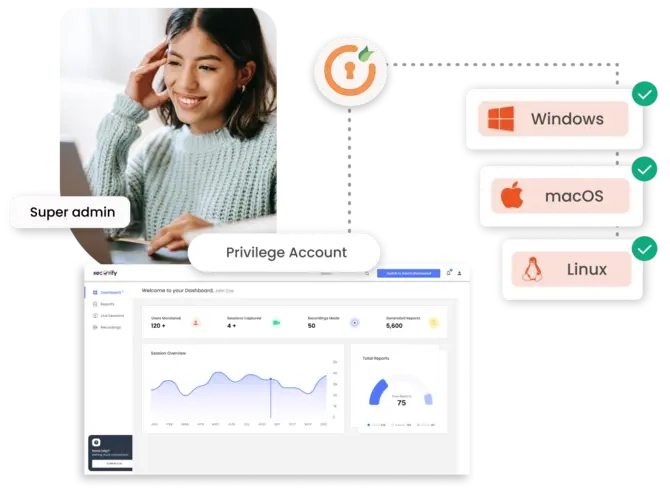
It supports a wide range of operating systems, enabling organizations to manage privileged access across diverse IT environments. Users can access the solution from Windows, Linux, or macOS desktops without any plugins or agents.
With no need to install software agents on individual endpoints, the deployment process becomes hassle-free. This reduces the complexity of implementation, saving time and resources for organizations.
The elimination of software agents on endpoints reduces licensing costs and maintenance expenses, making the solution cost-effective in the long run.
By removing the dependency on PAM agents, the attack surface is reduced, mitigating the risks associated with agent vulnerabilities. It ensures a more secure privileged access management environment.
enables organizations to swiftly deploy within any IT environment, free from complex setup or configuration demands. The agentless nature of the solution ensures user convenience, granting users access to privileged resources without the need for dedicated client applications..
Agentless PAM eliminates the need to manage and maintain PAM agents on each endpoint. This leads to reduced administrative overhead and makes the management of privileged access more efficient.





I can't speak highly enough regarding miniOrange, I am totally satisfied with the process and results in every regard.
5.0

Awesome tech service, Awesome product. Overall Awesome people. This solution is very simple and easy to implement
5.0
Agent-based PAM solutions involve deploying software agents on each user device that accesses cloud resources. These agents ensure robust security by enforcing strict access controls and monitoring at the endpoint level. Key benefits include enhanced security, a kill switch for immediate session termination in case of a breach, the use of passkey-like technology for authentication, and the ability to operate offline, enforcing policies even when the system is disconnected.
On the other hand, agentless PAM solutions manage and secure privileged access without installing software agents on each system. They leverage existing protocols and authentication methods, making deployment and management easier. This approach also enhances scalability, allowing organizations to adapt seamlessly to infrastructure changes, and reduces system impact by avoiding potential interoperability issues with multiple agents.
Overall, agent-based solutions offer robust endpoint security and offline capabilities, while agentless solutions provide ease of deployment, scalability, and reduced system impact.
