Need Help? We are right here!
Search Results:
×Separation of Duties (SoD) in PAM is a principle in cybersecurity that divides control of privileged user accounts over important tasks like setting up, approving, and deploying. It ensures responsibilities are distributed so that a person does not have too much control over privileged accounts. This simple check-and-balance lowers the risk of insider threats, human error, and abuse of privilege and makes people more responsible and audits go more smoothly.
miniOrange’s PAM brings SoD to life with role-based policies, just-in-time access, and dual approvals that separate who requests and who authorizes. You can get rock-solid SoD without slowing down your team by adding password vaulting, session recording, and time-limited delegation.







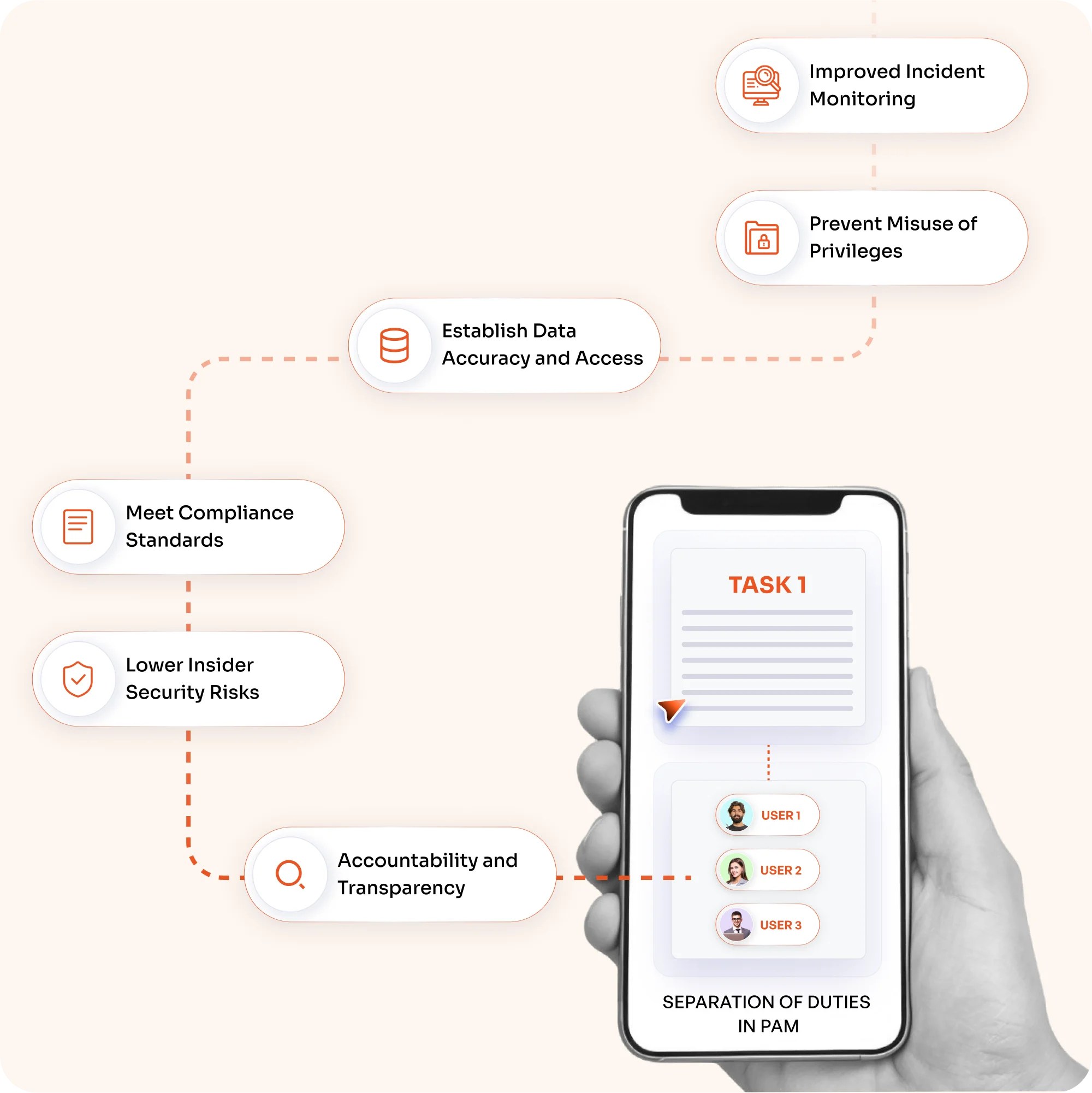
The goal is to promote transparency and accountability, ensuring that all individuals are aware of their responsibilities and actively monitor their progress.
Reduce the risk of insider threats by keeping highly sensitive duties and privileges separate.
You can meet compliance standards with built-in checks and audit trails.
Keep data safe and accessible by giving different teams control over it.
Stop people from abusing their privileges by using multi-approval workflows.
Keep detailed logs of all activities and send alerts in real time to make incident monitoring better.
miniOrange PAM delivers industry-specific access controls to prevent conflicts and maintain compliance.
Examples of how segregation of duties is implemented in PAM across various industries include.
IT and SaaS give system administrators, developers, and DevOps engineers more access, which lets them safely manage and audit infrastructure.
In an emergency, give healthcare workers limited, verifiable access to important systems like EHRs. This will make sure that patient care doesn't get delayed and that rules are still followed.
Use multi factor authentication for high-risk financial transactions to lower the risk of fraud and make sure that everyone is responsible through approval chains that can be tracked.
Make sure that only authorized people can access important operational technology, like SCADA, by giving them secure access to industrial control systems.
Give out and control access to critical systems needing strict identity checks to ensure only the people who have been cleared access sensitive information related to national security.
Continuously monitor and record privileged user sessions in order to identify issues, stop insider threats, and examine digital forensics.
