The workforce today is changing drastically. Employees need easy access to company files from anywhere, whether working from home or the office. However, poor security practices and uncontrolled access can create serious risks for businesses, including data breaches and compliance issues.
With remote and hybrid teams becoming the norm, it's more critical than ever to implement proper access management that balances user convenience with strong security. Organizations must consider both employee experience and privileged access requirements to protect sensitive information across distributed digital identities.
What is IAM (Identity and Access Management)?
Identity and Access Management (IAM) is a framework that enables organizations to manage digital identities and control user access to critical information and systems. It ensures the right people have appropriate access to technology resources at the right times and for the right reasons.
IAM combines identity management, which focuses on creating and managing user identities, with access management, which controls what resources those identities can access. This comprehensive approach helps organizations maintain security, meet compliance requirements, and streamline user experiences while protecting sensitive data from unauthorized access across on-premises, cloud, and hybrid environments.
We have mentioned digital identities too many times already. However, do you know what’s considered a digital identity?
The Core Concept of Digital Identity
Digital identity represents the online version of who someone is, consisting of all the digital information and attributes that uniquely identify an individual, organization, or device in the digital world. At its core, a digital identity is built from multiple interconnected components that work together to establish and verify identity in online environments.
Primary Components of Digital Identities
Digital identity consists of five fundamental elements that create a complete electronic fingerprint.
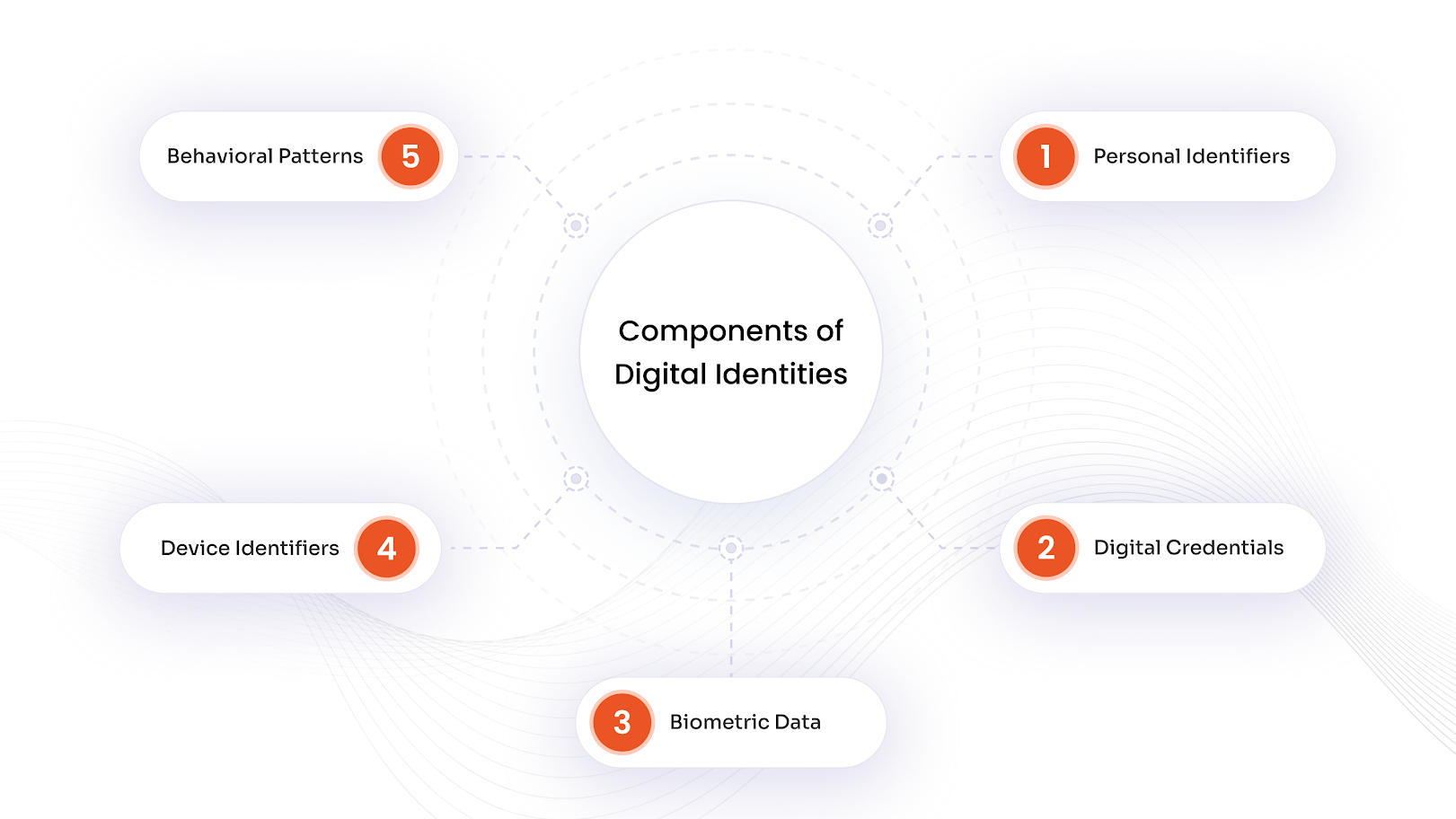
- Personal Identifiers form the foundation, including names, email addresses, usernames, and government-issued identification numbers that distinguish individuals across platforms.
- Digital Credentials encompass the authentication mechanisms like passwords, security tokens, and digital certificates used to verify access.
- Biometric Data provides unique physical characteristics such as fingerprints, facial recognition patterns, and voice prints that serve as secure verification methods due to their inherent uniqueness.
- Device Identifiers include technical markers like IP addresses and device IDs that help systems recognize specific devices and locations.
- Behavioral Patterns capture usage data, browsing history, and interaction patterns that create a unique digital footprint of how individuals engage online.
Challenges Organizations Will Face in the Absence of IAM
With hundreds of digital identities, providing adequate security and the right access is pivotal; however, without IAM, access management will be scattered and may create gaps. More identity and access management risks include:
Data breaches and unauthorized access become major concerns as organizations lack proper mechanisms to verify user identities and control sensitive resource access.
Operational Inefficiencies
Manual user provisioning and de-provisioning processes create significant administrative overhead, delays, and increased operational costs for IT teams managing access rights.
Compliance and Governance Issues
Regulatory compliance becomes nearly impossible without proper identity governance frameworks, creating legal and financial risks from inadequate access controls and audit trails.
Application Sprawl and Integration Challenges
Uncontrolled application sprawl occurs where departments adopt various cloud applications without centralized oversight, creating security gaps and inconsistent authentication policies across platforms.
Difference between Identity Management and Access Management
Identity Management and Access Management work together but serve distinct purposes within cybersecurity frameworks. Identity Management focuses on creating, maintaining, and governing digital identities throughout their entire lifecycle, including user account provisioning, authentication processes, and managing user attributes like roles and groups.
Access Management, on the other hand, controls what authenticated users can actually do by managing permissions, privileges, and authorization policies that determine access to specific resources, applications, and data. While Identity Management answers "who you are" through authentication, Access Management addresses "what you can access" through an authorization mechanism
Difference between IAM and Identity Management
| Aspect | Identity Management | IAM (Identity and Access Management) |
|---|---|---|
| Scope | Focuses solely on managing digital identities, user accounts, and authentication processes | Combines both identity management and access management into a comprehensive security framework |
| Functionality | Limited to user lifecycle management, authentication, and identity verification | Includes identity management plus access control, authorization, permissions management, and governance |
| Components | User provisioning, authentication methods, identity attributes, and profile management | Identity management, access management, single sign-on, multi-factor authentication, and policy enforcement |
| Security Focus | Prevents unauthorized access through proper identity verification and account management | Provides end-to-end security by controlling both who can access systems and what they can do once authenticated |
| Implementation | Typically deployed as part of a broader security strategy | Serves as a complete security solution, integrating multiple identity and access controls |
4 Components of Identity and Access Management
User Authentication
IAM systems enable authentication solutions to verify the identity of users, devices, and applications before granting access, using methods like passwords, multi-factor authentication, biometrics, and certificates to prevent unauthorized entry and identity fraud.
User Authorization
Once authenticated, IAM defines what resources users can access and which actions they can perform. Role-based and rule-based access controls ensure that users only access data relevant to their job responsibilities, reducing insider threats.
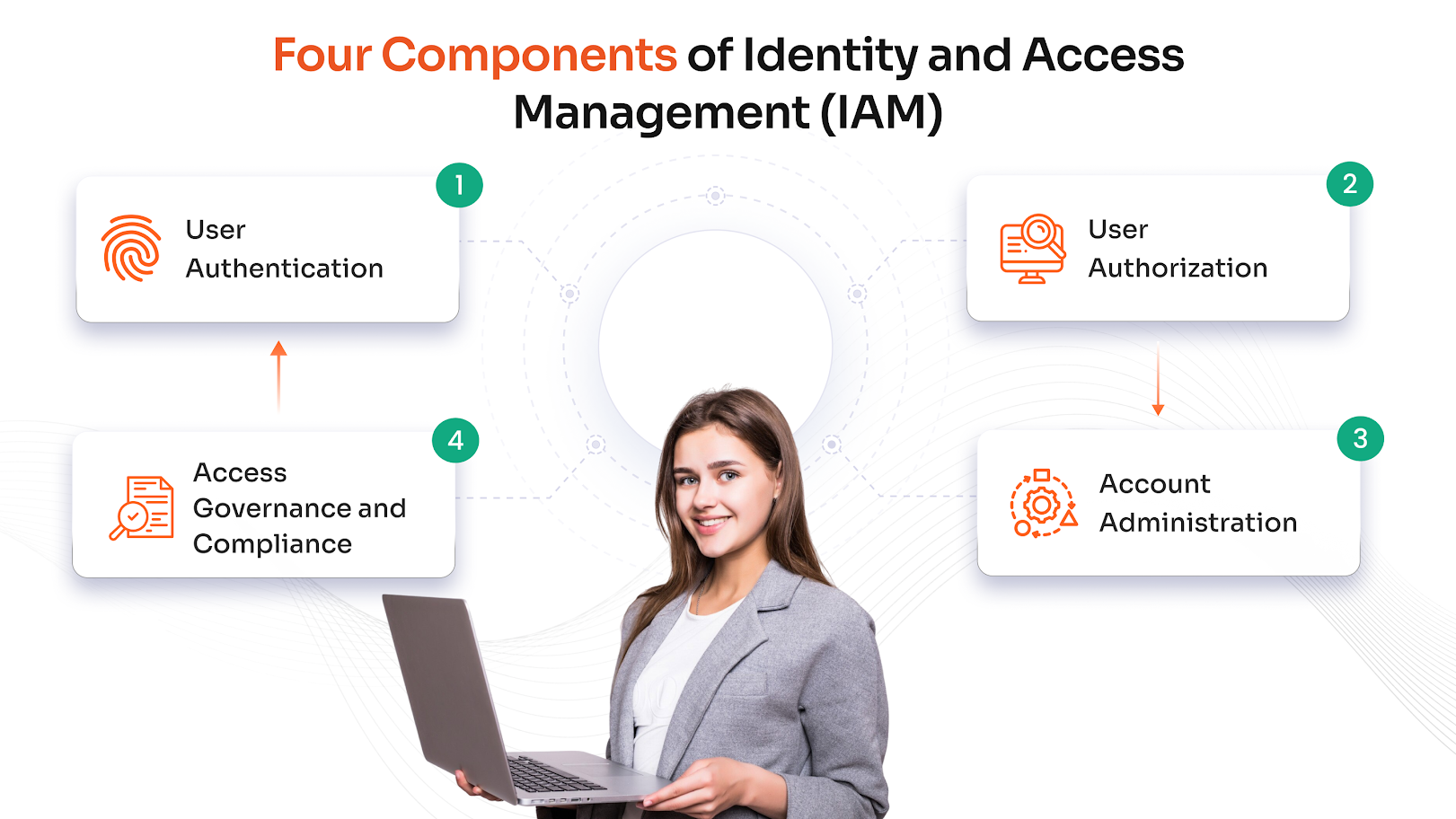
Account Administration
IAM automates the creation, modification, and removal of user accounts. It adjusts permissions automatically as users change departments or leave the organization, minimizing manual errors and preventing access creep.
Access Governance and Compliance
IAM continuously monitors, records, and audits user activities across systems, supporting regulatory compliance and policy enforcement by providing detailed access logs and reports for investigations and audits.
Benefits of Identity and Access Management
1. Enhances Security
IAM enforces strict authentication and authorization, reducing vulnerabilities from weak or shared passwords and minimizing data breach risks across applications and infrastructure.
2. Supports Regulatory Compliance
With centralized auditing and reporting capabilities, IAM helps organizations meet standards like GDPR, HIPAA, and SOX, providing proof of adequate control over sensitive data access.
3. Streamlines User Experience
Single sign-on and automated account management simplify access for employees, contractors, and partners, increasing productivity and reducing IT support requests.
4. Reduces Insider Threats
IAM enforces least privilege principles, automatically adjusting or revoking access when roles change or users leave, helping prevent unauthorized actions from current or former staff.
5. Enables Zero Trust Security
IAM supports the Zero Trust model by verifying every access request and enforcing granular, session-based authorizations, ensuring that no user or device is trusted by default.
6. Facilitates Digital Transformation
As organizations adopt cloud, hybrid, and multi-device environments, IAM provides scalable, automated controls for managing access securely across platforms and locations.
Four Pillars of IAM
Identity Governance and Administration (IGA)
This pillar focuses on managing digital identities and their lifecycle within an organization. It includes processes like user provisioning, deprovisioning, access certification, and role management. IGA ensures that users have the right access at the right time and helps organizations maintain compliance with regulatory standards by automating audits and access reviews.
Access Management (AM)
Access Management controls how users authenticate and gain access to systems, applications, and data. It includes technologies like Single Sign-On (SSO), Multi-Factor Authentication (MFA), and Role-Based Access Control (RBAC). The goal is to provide secure, seamless access while minimizing friction for users and protecting sensitive resources from unauthorized access.
Privileged Access Management (PAM)
Privileged Access Management secures accounts with elevated permissions, such as system administrators or executives. These accounts are high-value targets for attackers, so PAM enforces strict controls, session monitoring, and just-in-time access. It helps prevent misuse of privileges and ensures accountability through detailed logging and oversight.
Directory Services and Identity Repositories
This pillar provides the foundational infrastructure for storing and managing user identities. Directory services like Active Directory or LDAP serve as centralized repositories that authenticate users and enforce access policies. They support integration across various platforms and ensure consistent identity data across the enterprise.
How does Identity & Access Management work?
IAM works by ensuring that the right individuals and systems have appropriate access to resources, at the right time and for the right reasons. It combines technologies, policies, and processes to manage digital identities and control access across an organization.
Identity Creation and Management
IAM begins with the creation of digital identities for users, devices, or applications. These identities are stored in a centralized directory and include attributes such as name, role, department, and access level.
The system ensures that each identity is unique and accurately reflects the user's responsibilities. Identity management also involves updating user information as roles change and removing identities when users leave the organization.
Authentication
Authentication is the process of verifying that a user is who they claim to be. IAM systems use various MFA methods such as passwords, biometrics, smart cards, or multi-factor authentication (MFA) to confirm identity. MFA adds an extra layer of security by requiring two or more verification factors. This step is critical to prevent unauthorized access and protect sensitive data from breaches.
Authorization
Once a user is authenticated, IAM determines what resources they are allowed to access. Authorization is based on predefined policies, roles, or attributes. For example, a finance manager may have access to budgeting software but not to HR records. IAM enforces these rules to ensure users only interact with systems and data relevant to their role, reducing the risk of internal misuse.
Access Control Enforcement
IAM applies access control mechanisms to enforce authorization decisions. These controls include role-based access control (RBAC), attribute-based access control (ABAC), and the principle of least privilege. By limiting access to only what is necessary, IAM minimizes exposure to sensitive information and helps prevent accidental or malicious actions.
Monitoring and Auditing
IAM systems continuously monitor user activity and log access events. This data is used to detect unusual behavior, investigate incidents, and ensure compliance with regulations. Auditing capabilities allow organizations to review who accessed what, when, and how, providing transparency and accountability across the digital environment.
Integration with Applications
IAM integrates with various applications, platforms, and services using standard protocols such as SAML, OAuth, and OpenID Connect. This enables seamless access across cloud and on-premises environments while maintaining consistent security policies. Integration ensures that IAM can support diverse systems without compromising performance or user experience.
Example: IAM in a Healthcare Organization
Imagine a large hospital network using an IAM system to manage access across its digital infrastructure, electronic health records (EHR), billing systems, diagnostic tools, and patient portals.
Potential Challenge
- Doctors need access to patient records and diagnostic systems.
- Nurses require access to medication schedules and care plans.
- Billing staff must access insurance and payment systems.
- IT admins manage backend systems but should not view patient data.
IAM Solving All the Challenges
Identity Creation: When a new employee joins, HR triggers an automated workflow that creates a digital identity in the IAM system.
Role Assignment: Based on job title, the IAM system assigns roles (e.g., Doctor, Nurse, Billing).
Access Provisioning: Each role has predefined access rights. Doctors get read/write access to EHRs, nurses get read-only access, and billing staff get access to financial systems.
Authentication: Employees log in using Single Sign-On (SSO) and Multi-Factor Authentication (MFA) to verify their identity.
Authorization: IAM checks their role and grants access only to permitted systems.
Monitoring: All access is logged. If a billing staff member tries to access patient records, the system blocks it and flags the attempt.
Deprovisioning: When someone leaves, IAM automatically revokes access across all systems.
This ensures security, compliance, and operational efficiency, all without manual intervention.
Distinct IAM Technologies
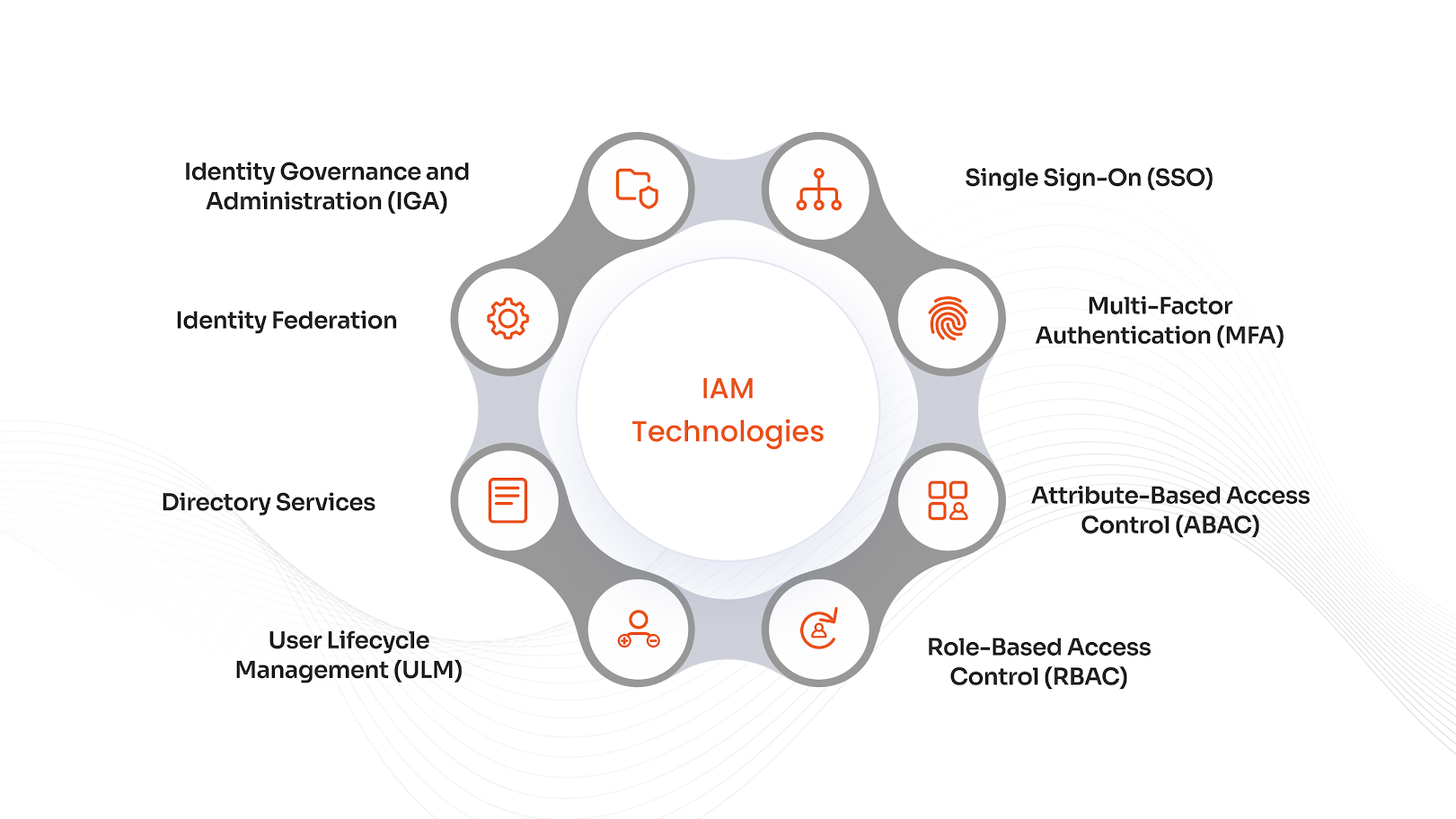
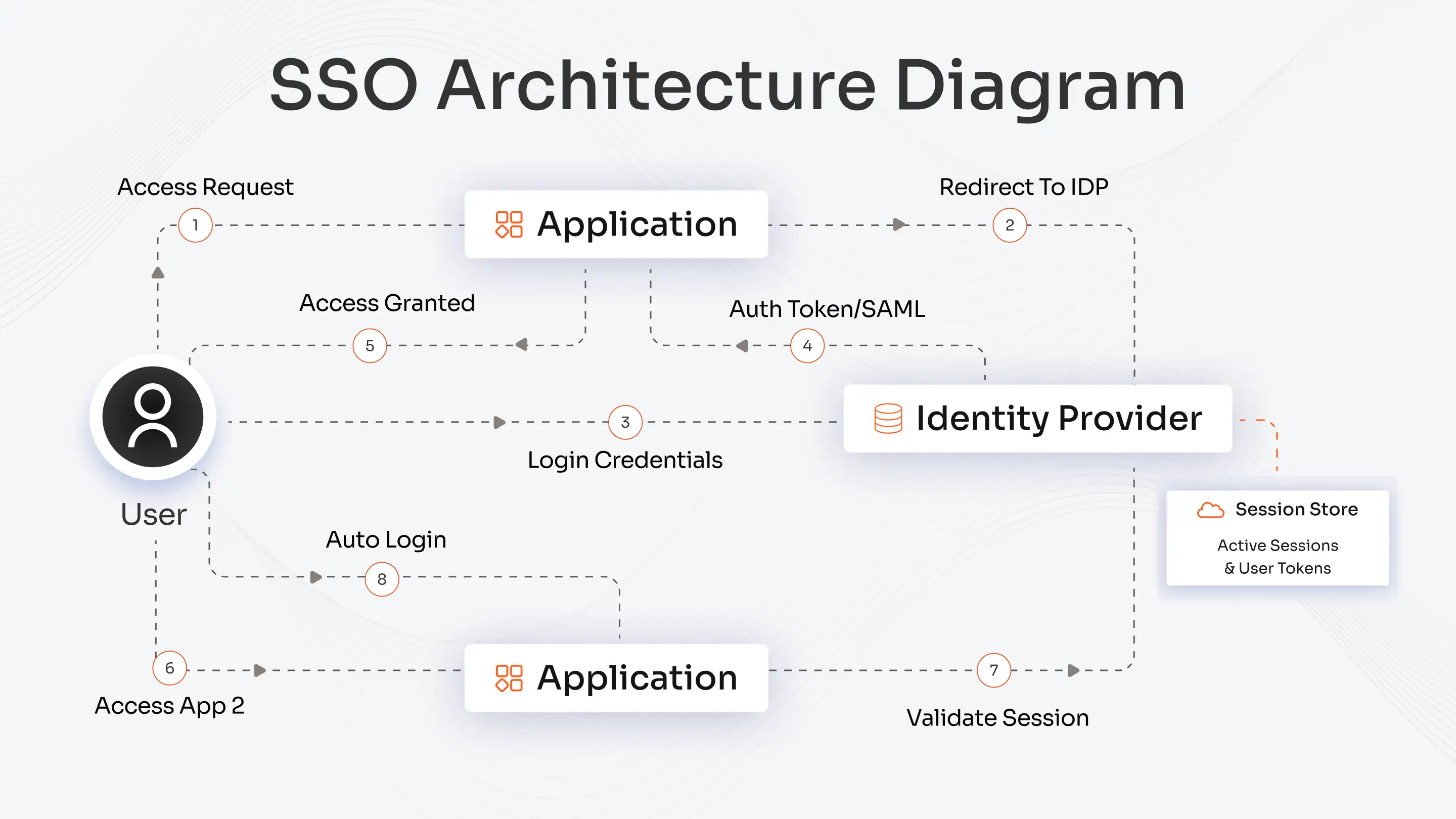
Single Sign-On (SSO)
SSO allows users to authenticate once and gain access to multiple applications without re-entering credentials. It simplifies user experience and reduces password fatigue while maintaining centralized control over access.
Multi-Factor Authentication (MFA)
MFA strengthens security by requiring two or more verification factors through different MFA methods, such as passwords, biometrics, or tokens, before granting access. It significantly reduces the risk of unauthorized access due to compromised credentials.
Attribute-Based Access Control (ABAC)
ABAC grants access based on user attributes like department, location, or clearance level. It enables dynamic, context-aware access decisions and supports fine-grained policy enforcement.
Role-Based Access Control (RBAC)
RBAC assigns permissions based on predefined roles (e.g., HR Manager, Developer). Separation of Duties (SoD) ensures that no single user has conflicting responsibilities, reducing the risk of fraud or error in sensitive operations.
User Lifecycle Management
This automates the creation, modification, and removal of user accounts. It ensures users have appropriate access from onboarding to offboarding, minimizing manual errors and improving operational efficiency.
Directory Services
Directory services like Active Directory or LDAP store and manage identity data. They serve as the backbone for authentication and authorization, supporting integration across systems and enforcing consistent policies.
Identity Federation
Identity Federation enables users from different organizations to access shared resources using their own credentials. Identity brokering facilitates trust between identity providers, supporting secure B2B and cross-domain collaboration.
Identity Governance and Administration (IGA)
IGA provides oversight and control over identity-related processes. It includes access reviews, role management, and policy enforcement, helping organizations meet compliance requirements and reduce risk through automation and visibility.
Types of IAM Based on Identities
Identity and Access Management (IAM) can be broadly categorized based on the types of identities it manages. The two primary types are Workforce IAM and Customer IAM (CIAM), each serving distinct purposes and user bases.
Workforce Identity and Access Management
Workforce IAM focuses on managing internal identities, that is, the employees, contractors, and other organizational stakeholders. It ensures that users have appropriate access to enterprise systems based on their roles and responsibilities.
Features typically include Single Sign-On (SSO), Multi-Factor Authentication (MFA), Role-Based Access Control (RBAC), and lifecycle management. Workforce IAM is tightly integrated with HR systems and IT infrastructure to automate onboarding, role changes, and offboarding.
Customer Identity and Access Management (CIAM)
CIAM is designed for external users such as customers, partners, and vendors. It emphasizes scalability, user experience, and data privacy. Unlike workforce IAM, CIAM must support millions of users with diverse devices and unpredictable traffic patterns.
It includes features like social login, progressive profiling, consent management, and personalized access. Customer IAM platforms often integrate with marketing and analytics tools to enhance customer engagement while maintaining strong security and regulatory compliance.
Deployment Options for IAM
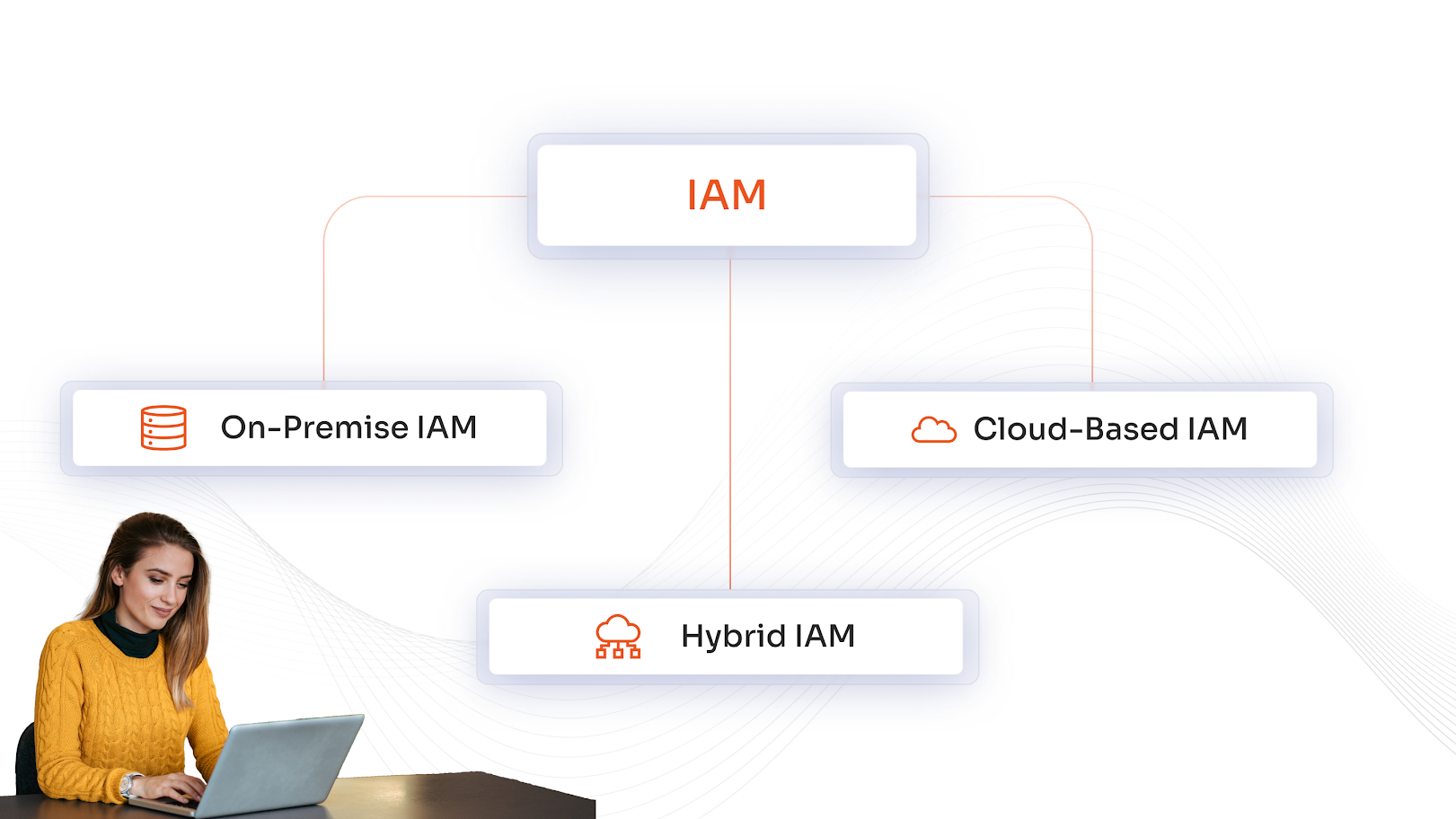
On-Premise IAM
The systems are hosted within an organization’s own infrastructure. This offers full control over data, customization, and compliance, but requires significant IT resources for maintenance and scalability.
Cloud-Based IAM
Cloud IAM is delivered as a service by third-party providers. It offers rapid deployment, scalability, and reduced infrastructure costs. Ideal for organizations with remote workforces or cloud-first strategies.
Hybrid IAM
This combines on-premise and cloud IAM capabilities. This model supports legacy systems while leveraging cloud flexibility, making it suitable for organizations transitioning to modern architectures or managing diverse environments.
Identity and Access Management Tools
A wide range of vendors offers IAM tools, each providing specialized capabilities to manage identities, enforce access policies, and support compliance. These solutions vary in scope from enterprise-grade platforms that handle workforce and customer identities to lightweight tools focused on specific functions like authentication or directory services.
Choosing the right IAM vendor depends on your organization’s size, infrastructure, and security requirements. For a curated list of leading IAM vendors and their offerings, explore the link below.
Different IAM Protocols
SAML (Security Assertion Markup Language)
SAML is an XML-based protocol used primarily for SSO in enterprise web applications. It enables identity providers (IdPs) to authenticate users and pass secure assertions to service providers (SPs), allowing users to access multiple applications with a single login. SAML is widely adopted in corporate environments due to its maturity, strong security features like digital signatures, and support for attribute-based access control.
OAuth 2.0
OAuth is an authorization framework that allows third-party applications to access user data without exposing credentials. It’s commonly used in scenarios where users grant limited access to their resources, such as allowing a calendar app to view events from a Google account. OAuth doesn’t handle authentication directly, but is often paired with OpenID Connect for that purpose. It’s ideal for API security and delegated access across mobile and web platforms.
OpenID Connect (OIDC)
OIDC is an authentication layer built on top of OAuth 2.0. It adds identity verification using ID tokens formatted as JSON Web Tokens (JWT). OIDC enables secure login flows for consumer-facing applications and supports features like user info endpoints and session management. It’s widely used for social logins and modern web authentication due to its simplicity and scalability.
SCIM (System for Cross-domain Identity Management)
SCIM is a protocol designed for automating user provisioning and deprovisioning across cloud-based applications. It standardizes how identity data is exchanged between systems, making it easier to manage user lifecycles. SCIM is especially useful in large organizations where users frequently join, change roles, or leave, and access needs to be updated across multiple platforms.
LDAP (Lightweight Directory Access Protocol)
LDAP is a protocol used to access and manage directory services, such as Active Directory. It allows applications to query and modify identity data stored in centralized directories. LDAP is foundational to many traditional IAM systems and supports authentication, group management, and policy enforcement. While older than other protocols, it remains essential for on-premise identity infrastructure.
Regulatory Compliance IAM Achieves
FISMA (Federal Information Security Management Act)
IAM supports FISMA by ensuring that federal systems implement access controls, identity verification, and continuous monitoring. It helps agencies maintain secure access to government data and comply with NIST guidelines.
GDPR (General Data Protection Regulation)
Identity management enables organizations to enforce data minimization, consent management, and access restrictions for personal data. It supports GDPR’s principles of privacy by design and accountability by controlling who can access EU citizens’ data and under what conditions.
HIPAA (Health Insurance Portability and Accountability Act)
In healthcare, IAM ensures that only authorized personnel have access to protected health information (PHI). It supports HIPAA’s security rule by enforcing authentication, role-based access, and audit logging to safeguard patient data.

ISO/IEC 27001
IAM contributes to ISO 27001 compliance by implementing access control policies, managing user identities, and supporting risk management practices. It helps organizations maintain the confidentiality, integrity, and availability of information assets.
PCI DSS (Payment Card Industry Data Security Standard)
IAM helps secure cardholder data by enforcing strong access controls, multi-factor authentication, and user activity logging. It supports PCI DSS requirements for restricting access to sensitive payment systems and maintaining audit trails.
SOX (Sarbanes-Oxley Act)
SOX compliance in IAM ensures that financial systems are accessed only by authorized users. It helps enforce segregation of duties, monitor privileged access, and maintain logs for financial reporting integrity.
NIST Cybersecurity Framework (CSF)
IAM aligns with the NIST CSF by supporting identity management, access control, and continuous monitoring. It helps organizations identify, protect, detect, respond to, and recover from cybersecurity threats through structured identity governance.
Choosing the right IAM Solution
Assess Organizational Needs
Begin by identifying the types of identities you need to manage the workforce, customers, partners, or devices. Consider the scale of your operations, the complexity of your IT infrastructure, and the sensitivity of the data you handle. These factors will influence whether you need a lightweight IAM tool or a comprehensive enterprise-grade platform.
Evaluate Deployment Models
IAM solutions can be deployed on-premise, in the cloud, or in hybrid environments. On-premise offers full control but requires significant resources. Cloud-based IAM provides scalability and ease of integration, while hybrid models are ideal for organizations transitioning from legacy systems.
Consider Integration and Compatibility
Ensure the solution supports wide app integration with your existing applications, directories, and cloud services. Compatibility with protocols like SAML, OAuth, OpenID Connect, and SCIM is essential for seamless authentication and provisioning across platforms.
Prioritize Security and Compliance Features
Look for features such as Multi-Factor Authentication (MFA), Role-Based Access Control (RBAC), audit logging, and identity governance. These capabilities help enforce security policies and support compliance with standards like GDPR, HIPAA, and ISO 27001.
Analyze Vendor Reputation and Support
Research vendor reliability, customer reviews, and support offerings. A vendor with a strong track record in IAM and responsive support can make a significant difference in deployment success and long-term value.
Simplified Identity Management with miniOrange
Flexible Integrations and Deployment
miniOrange IAM supports cloud, hybrid, and legacy environments. It integrates using modern protocols like SAML and OAuth, while also connecting with older systems through LDAP and RADIUS. This ensures consistent identity control across your entire infrastructure.
Complete miniOrange IAM Solution
The platform combines Single Sign-On (SSO), Multi-Factor Authentication (MFA), and Customer IAM (CIAM) in one solution. This reduces the need for multiple vendors and simplifies access management for both employees and customers.
Built-In Compliance Support
miniOrange helps meet regulations like GDPR, HIPAA, and SOX with automated logging, consent tracking, and access reviews. It reduces manual effort and keeps your organization audit-ready.
Easy to Deploy and Scale
With low-code setup, pre-built connectors, and intuitive controls, miniOrange IAM solution speeds up deployment and scales easily. It fits businesses of all sizes without adding complexity.
Identity and Access Management Best Practices
The following IAM best practices will allow you to keep your systems and resources secure and centralized.
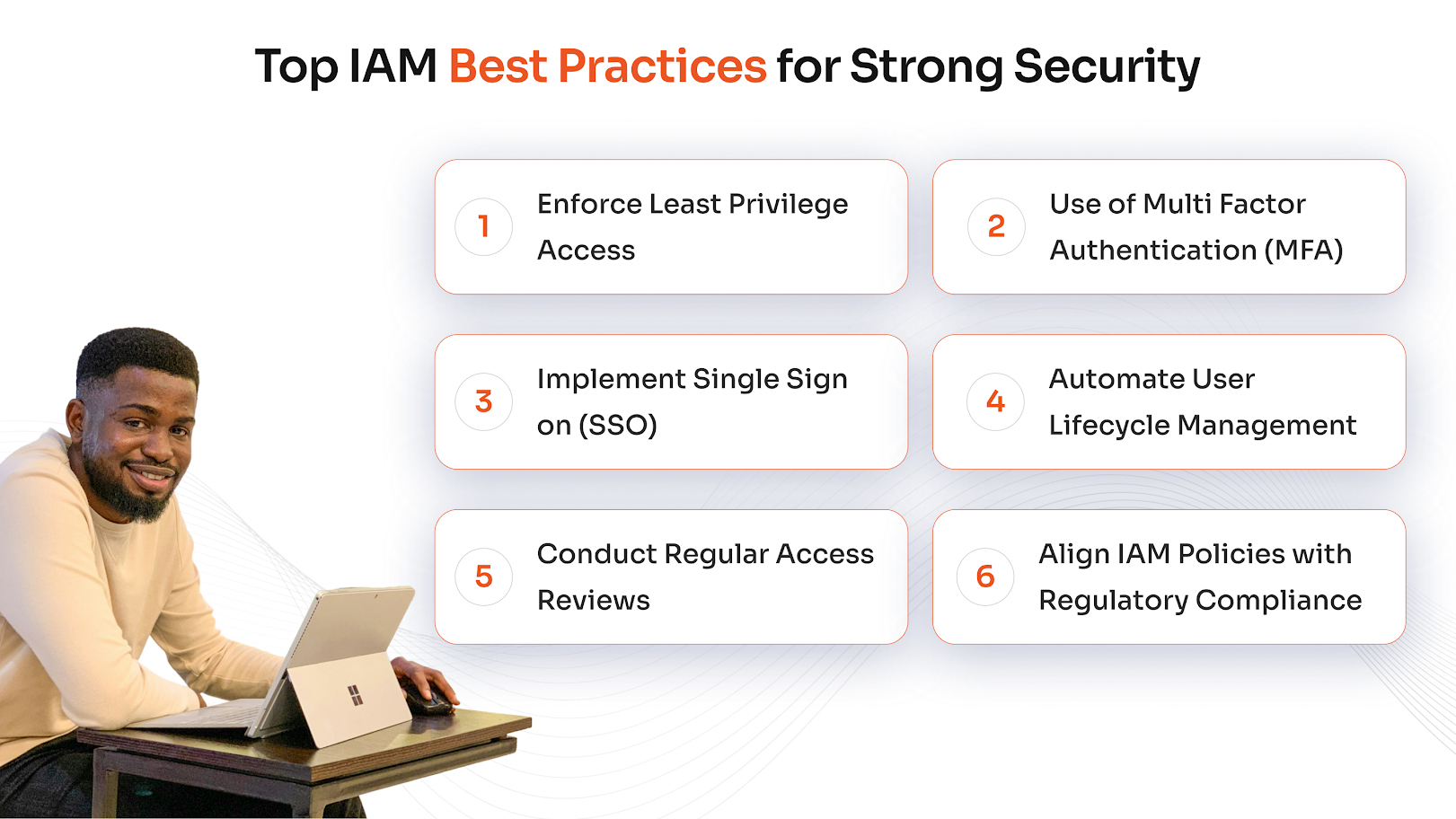
Enforce Least Privilege Access
Grant users only the access necessary to perform their job functions. This minimizes the risk of data exposure and limits the impact of compromised accounts. Regular access reviews and automated role adjustments help maintain a secure and efficient access model.
Use Multi-Factor Authentication (MFA)
MFA adds a critical layer of security by requiring users to verify their identity through multiple factors such as passwords, biometrics, or tokens. It significantly reduces the risk of unauthorized access due to stolen or weak credentials.
Implement Single Sign-On (SSO)
SSO allows users to access multiple applications with a single set of credentials. It simplifies the login experience, reduces password fatigue, and centralizes authentication management. SSO also improves visibility into user activity across systems.
Automate User Lifecycle Management
Automating provisioning, role changes, and deprovisioning ensures timely and accurate access control. Integration with HR systems enables real-time updates when employees join, change roles, or leave the organization. This reduces manual errors and strengthens compliance.
Conduct Regular Access Reviews
Periodic audits of user access help identify outdated or excessive permissions. These reviews are essential for maintaining compliance, detecting insider threats, and ensuring that access aligns with current job responsibilities.
Align IAM Policies with Regulatory Requirements
IAM policies should reflect the requirements of relevant regulations such as GDPR, HIPAA, SOX, and FISMA. Document procedures, enforce access controls, and maintain audit logs to demonstrate compliance. A well-governed IAM program supports legal obligations and builds trust with stakeholders.
Our Thoughts
As businesses adopt cloud-first models, remote workforces, and customer-centric platforms, IAM becomes essential for managing trust, ensuring compliance, and delivering seamless user experiences. The challenge lies in balancing robust security with usability, and future-proofing systems to adapt to evolving technologies and regulations. A well-implemented IAM strategy not only protects sensitive data but also empowers users, streamlines operations, and builds a foundation of accountability and resilience.
Glossary
Authentication
The process of verifying a user's identity before granting access to systems or data.
Authorization
Determines what resources a verified user is allowed to access based on roles or attributes.
Single Sign-On (SSO)
A method that allows users to log in once and access multiple applications without re-entering credentials.
Multi-Factor Authentication (MFA)
A security mechanism that requires two or more forms of verification to confirm a user's identity.
Role-Based Access Control (RBAC)
An access control model that assigns permissions based on predefined roles within an organization.
Attribute-Based Access Control (ABAC)
Access decisions are made based on user attributes such as department, location, or clearance level.
SCIM (System for Cross-domain Identity Management)
A protocol used to automate user provisioning and deprovisioning across systems.
LDAP (Lightweight Directory Access Protocol)
A protocol for accessing and managing directory services, commonly used for storing identity data.
Identity Governance and Administration (IGA)
Processes and tools that manage identity lifecycle, access reviews, and policy enforcement to ensure compliance.
Federated Identity
Allows users to access systems across organizational boundaries using a single identity managed by a trusted provider.




Leave a Comment