Need Help? We are right here!
Search Results:
×Identity management in cybersecurity is the process of controlling who has access to what within an organization. It involves authenticating users, authorizing access, and managing user information to ensure security and compliance. An Identity Management (IdM) ecosystem is a framework of policies and technologies that ensure the right users have access to the right resources.
This process verifies the identity of users attempting to access a system. It ensures that only legitimate users can log in by requiring credentials such as Passwords, Biometrics, or Multi-factor Authentication.
Once authenticated, users are granted permissions based on their roles and responsibilities. This component ensures that users can only access the resources and perform the actions they are authorized for, maintaining security and compliance.
This involves managing user accounts, roles, and access policies. It includes tasks such as creating and deleting user accounts, assigning roles, and updating permissions. Effective administration ensures that access controls are up-to-date and aligned with organizational policies.
This component tracks and analyzes user activities within the system. It provides detailed logs and reports on who accessed what, when, and how. Auditing and reporting are crucial for detecting suspicious activities, ensuring compliance with regulations, and maintaining overall security.
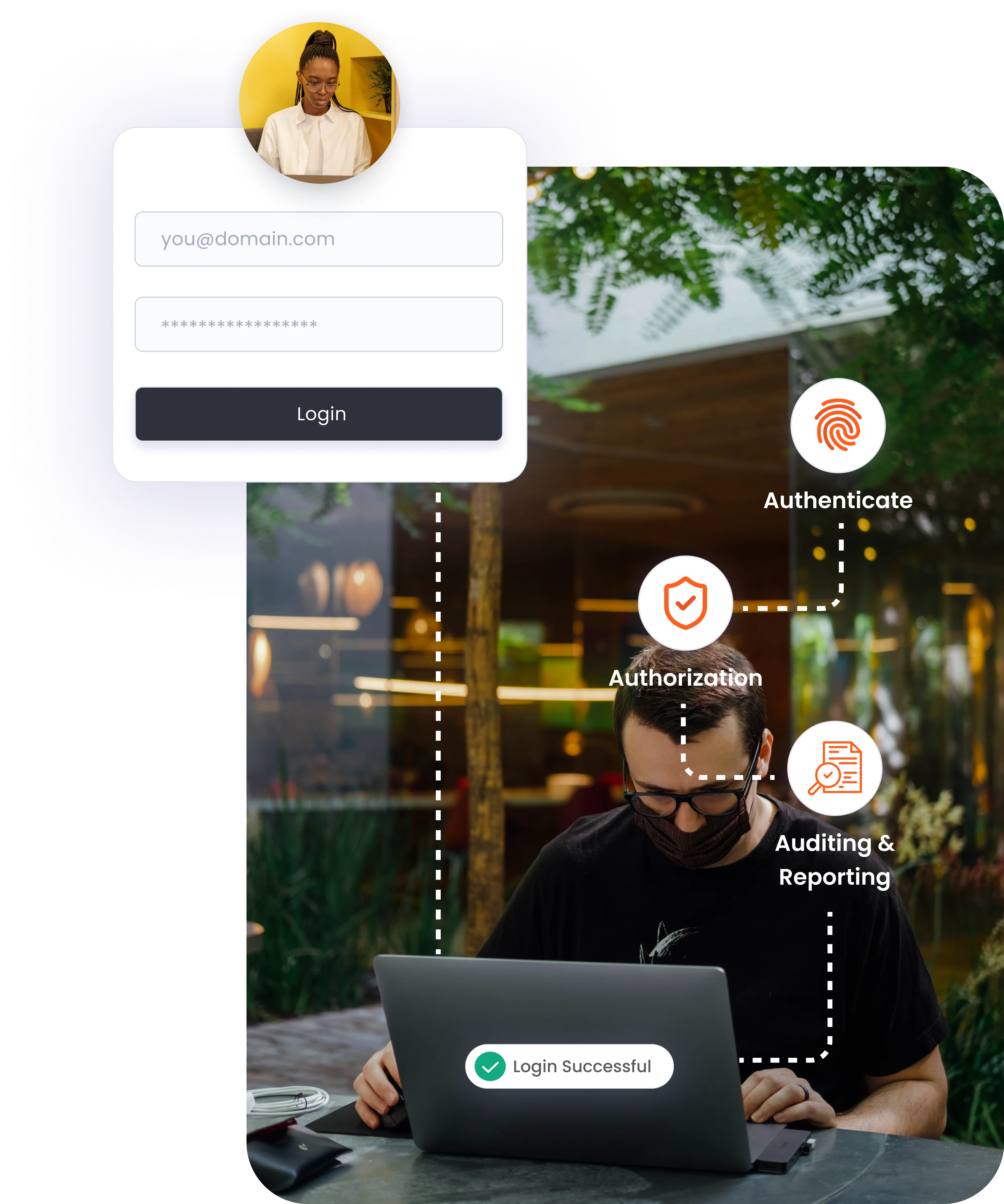
IAM tools and technologies help organizations achieve their security goals and adhere to the set security policies. These ensure seamless access to applications and data, reducing the risk of unauthorized access and improving user productivity.
Single sign-on lets users log in once to access multiple applications without re-entering credentials. This improves user experience and reduces password fatigue. In-house applications and sites (e.g., PHP, Java) that struggle with protocol support (SAML, OAuth, and LDAP) can enable it using miniOrange SSO connectors.
MFA lets users provide two or more verification factors to gain access. This adds an extra layer of security and reduces the risk of unauthorized access. Use over 15+ MFA methods like authenticator apps, OTP over SMS, email, hardware token, email magic link, push notifications to verify user identity. Protocol support for in-house applications and sites is added with the help of MFA connectors.
Identity lifecycle management (ILM) manages user identities from creation to deactivation. This ensures appropriate access rights at all times, enhancing security and compliance. User synchronization connectors enable protocol support for in-house applications and sites built in PHP, Java and more.
Identity management (IdM) strengthens security, ensures compliance, improves operational efficiency, boosts user satisfaction, and reduces costs. It helps organizations to keep their security up-to-date and gain a competitive advantage.
Identity management ensures only authorized users access sensitive information, reducing the risk of data breaches.
IdM provides detailed access logs and audit trails to help comply with regulations and avoid fines.
IdM streamlines user access and permissions, boosting productivity and reducing manual processes.
IdM simplifies login processes and SSO, reducing password fatigue and increasing employee satisfaction.
IdM automates identity management, lowering administrative costs and minimizing security incident risks.
Adapts to organizational growth and changes in user roles with user groups, maintaining effective security measures.
Identity solutions from miniOrange can be easily deployed in your organization's existing environment.
