As traditional perimeter defenses fail in today's fast-paced, distributed environments, zero trust security is quickly changing the way we protect our computers. Recent research shows that companies that use Zero trust safeguards can cut the damage from breaches by up to 50% and stop attackers from moving laterally. The model, based on continuous identity verification, multi-factor authentication, and micro-segmentation, makes sure that every user, device, and identity and access management request is checked in real time. This is important because remote work is making cyber exposure rise by more than 300%, and cloud usage is at all-time highs.
More and more security leaders are using tools like miniOrange to make zero trust work. Data shows that almost 70% of people who use zero trust see better threat containment. miniOrange improves security with context-based authentication and strong MFA. This detailed, flexible method not only protects important assets, but it also makes things easier for users, creating a new benchmark for proactive cybersecurity.
What is Zero Trust?
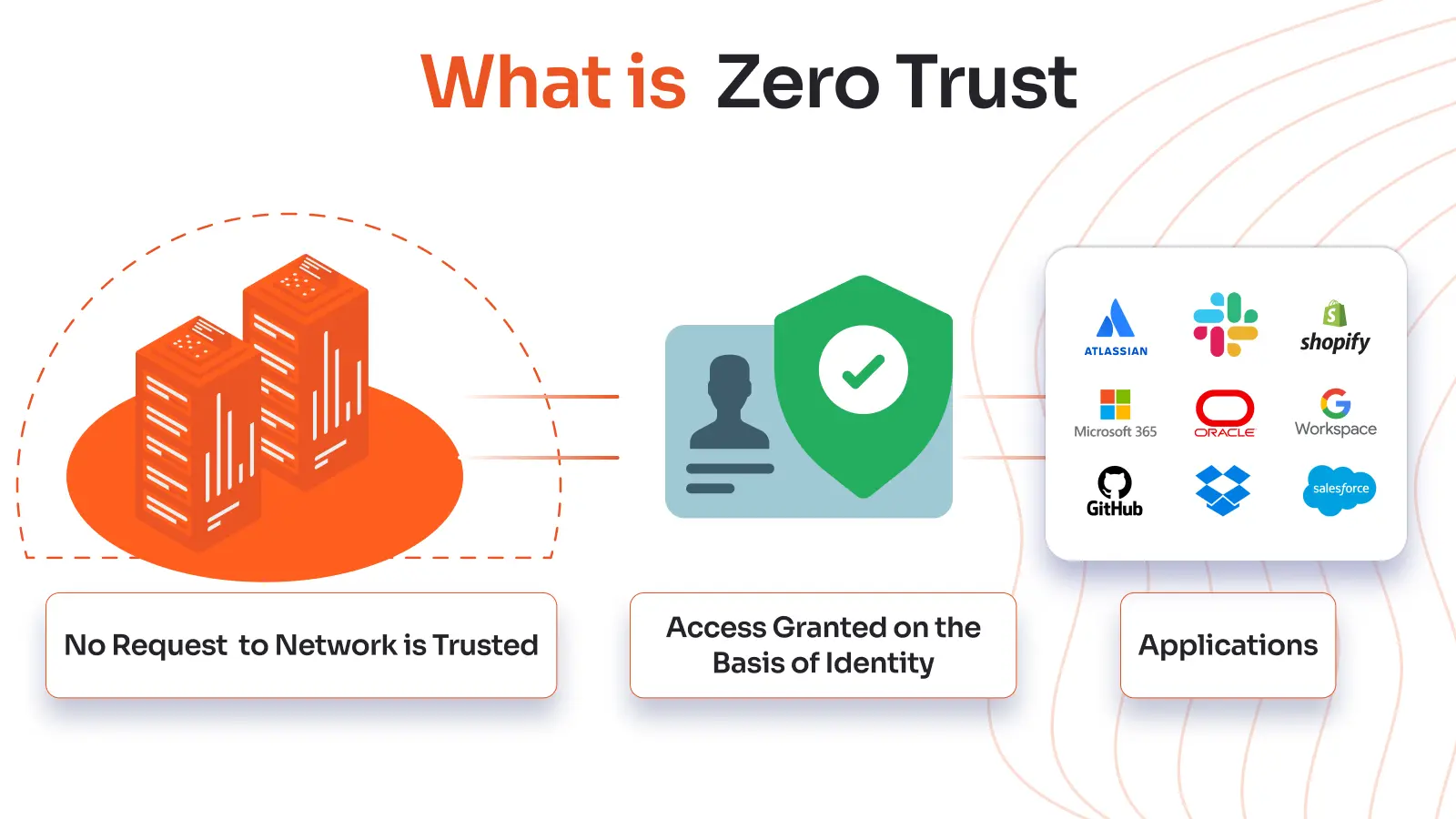
Zero trust is a security approach that assumes that every request for access could be exploited. It gets rid of the built-in weakness of implicit trust by making sure that every interaction is checked.
- Trust as a Weakness
The paradigm presumes that no user, device, or endpoint possesses intrinsic safety. It sees trust as a risk that needs to be tested all the time.
- Check before Access
Before someone can use a resource, their identification must be thoroughly checked for every request. This strategy makes sure that only verified people can get in.
- Prevention of Lateral Movement
Micro-segmentation limits access to important resources. It lessens the effects of breaches by keeping possible risks in check.
Zero trust lowers the chances of a breach and limits harm by getting rid of default permissions. It changes security by putting identity and context at the center of decisions about who can access what.
How Does Zero Trust Work?

No matter where you are on the network, zero trust sees every access request as untrusted. It secures resources by using constant verification, strong authentication, and policy enforcement that changes over time.
- Strict Verification and MFA
Before access is authorized, each user and device must go through a stringent identity check. Advanced MFA, like the miniOrange MFA product, provides more than one layer of verification to make things safer. Various MFA methods are available to login conveniently.
- Engine for Enforcing Security Policies
A central engine checks the posture of the device and the identity of the user for every query. The engine keeps an eye on session activity all the time and uses threat intelligence to enforce strict rules.
- Risk-Based Access (RBA) Sessions
Real-time risk evaluations of each session or simply risk-based access (RBA) are used to make access decisions. This method stops lateral movement and limits the damage caused by breaches by giving permits on the fly.
- Micro-Segmentation of Important Assets
The concept protects the most important networks, data, and applications by putting up separate perimeters around them. These perimeters work like firewalls, letting only confirmed, legitimate traffic access sensitive resources.
Zero trust changes the way we think about security by getting rid of implicit trust and requiring constant validation. It helps businesses lower the risk of breaches and protect their assets in the ever-changing digital world of today.
Why Do We Need Zero Trust?
Zero trust changes the way we think about security by getting rid of broad trust assumptions. It substitutes static perimeters with verification that changes based on the situation for every access.
- Legacy Perimeter Security
VPNs and firewalls are used by legacy systems to protect a static network barrier, which gives all internal users full access. This model doesn't function when threats come from inside the trustworthy network.
- Implicit Trust and Vulnerabilities
Traditional methods assume that all users in the network are trustworthy, which ignores dangers from within the network or stolen credentials. This kind of open access lets attackers go sideways and steal important items.
- Shift to Remote Work
The growing usage of remote work breaks down the traditional network boundary, making resources available to networks that can't be trusted. Remote connections make traditional defenses less effective and add new security problems.
- Need for Granular Access Control
Zero trust limits access based on identity, device, and context by using micro-segmentation and constant verification. A concentrated approach with granular access control reduces the likelihood of breaches occurring and simplifies the process of addressing them when they do happen.
Zero trust gets around old problems by putting in place proactive, adaptable security solutions that fit with how people work today. In a constantly changing and distributed digital world, Zero Trust Architecture (ZTA) aids businesses in safeguarding crucial assets like privileged users through PAM.
What is Zero Trust Architecture (ZTA)?
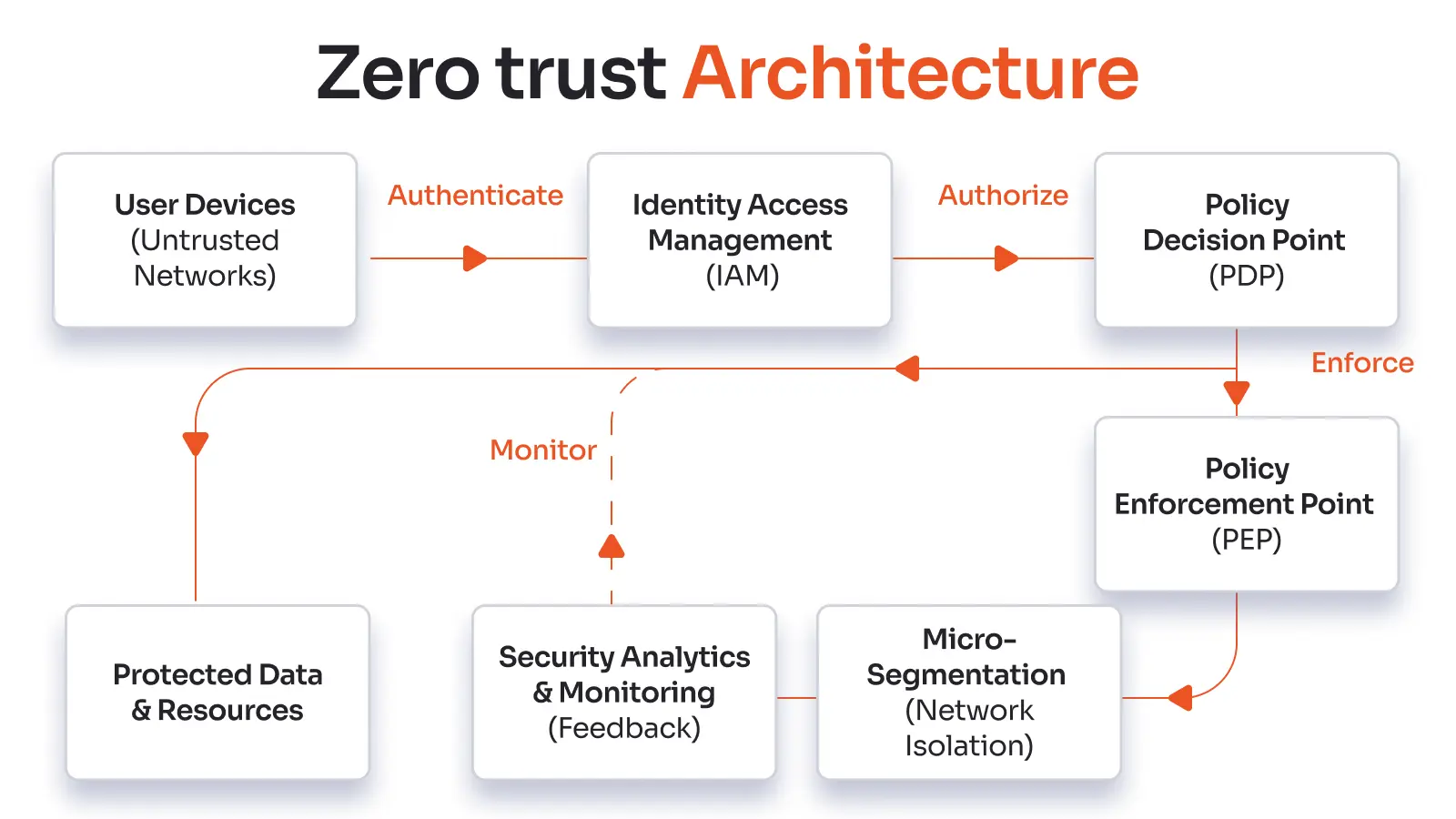
Zero Trust Architecture (ZTA) is a strategic framework that rejects implicit trust and authenticates each access attempt. It changes based on risk to protect users, devices, apps, and data in different contexts. ZTA's main purpose is to protect important assets by enforcing stringent segmentation and fine-grained policy management. It uses the principle of least privilege.
- Enforcement Based on Identity
We check each request with real-time context checks and multifactor authentication. Identity is the new security perimeter that dynamically enforces least-privilege access.
- Validation of Device Posture
Devices must meet compliance standards, which include being patched, encrypted, and given permission. Risky endpoints are marked or denied access to keep the system clean.
- Micro-segmentation of networks
There are logical units of important assets, programs, and data called ‘protected surfaces’ in networks. A perimeter surrounds each protected surface and only allows known, legitimate traffic to pass through.
- Control of Access to Resources
Policies that take into account user roles and behavior protect applications and workloads. This level of control reduces attack targets and prevents lateral movement.
- Telemetry and Data Security
Data is encrypted and constantly logged and monitored. Telemetry enables real-time problem detection and dynamic policy changes.
Zero trust architecture moves security from fixed boundaries to flexible, breach-proof enforcement. It gives businesses the power to deal with risks and work safely in hybrid and cloud-native environments.
Zero Trust Maturity Model
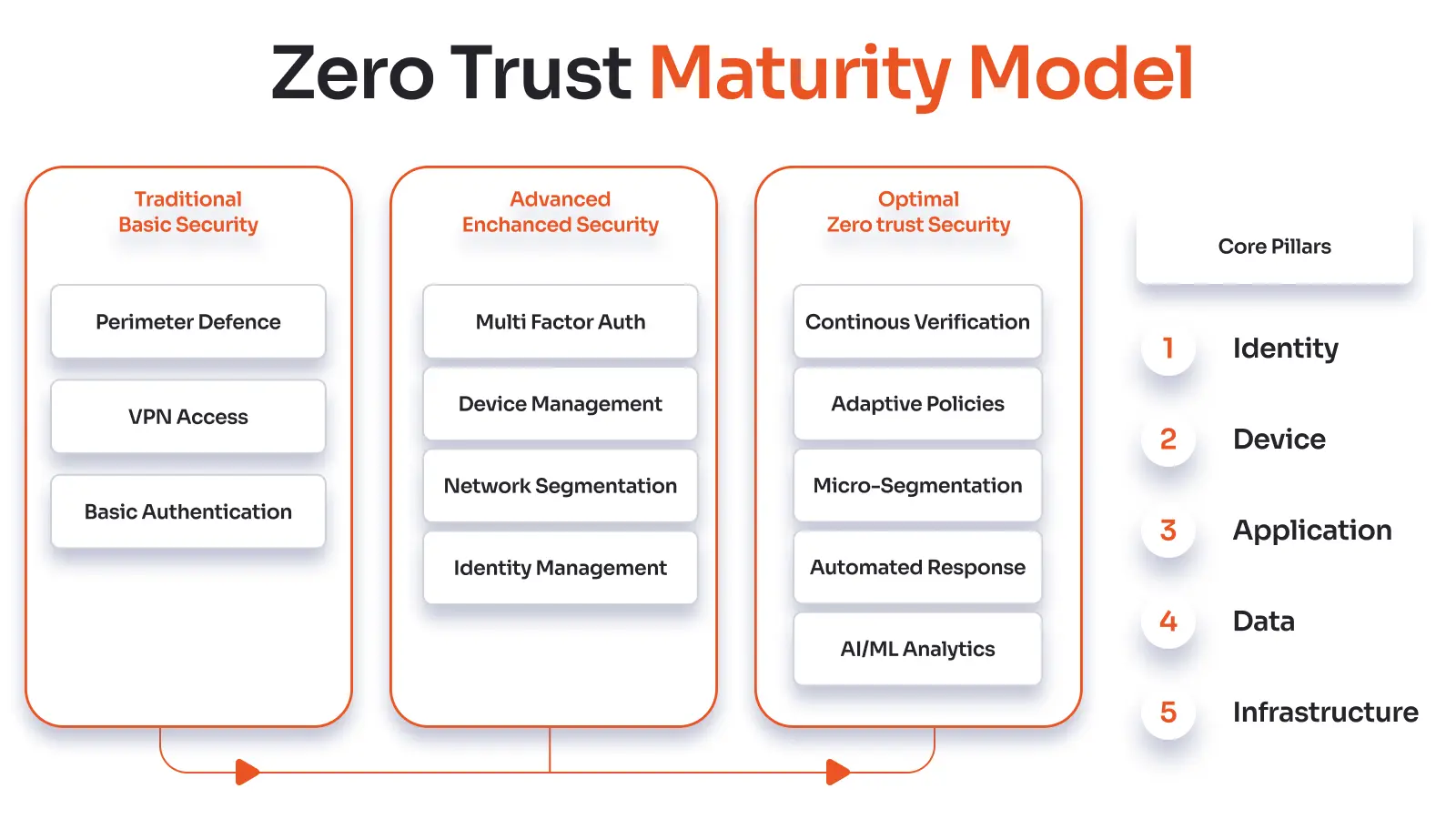
The Zero Trust Maturity Model gives businesses a clear way to improve their cybersecurity. It helps make sure that technology, procedures, and policies all follow Zero Trust principles, no matter how ready they are.
- Traditional (Initial):
Organizations use security that is based on the perimeter and trust that is built into the network. Controls are broken up, and access decisions don't often take into account the identity or device context.
- Advanced (Developing):
Enterprises begin to use multifactor authentication, basic device compliance, and network segmentation. Policies are starting to show risk-based thinking, yet enforcement can still be done by hand or not always be the same.
- Best (Mature):
Security is dynamic because of real-time context, ongoing validation, and telemetry. Automated, adaptive procedures protect well-defined, micro-segmented surfaces.
- Adaptive (Continuous Improvement):
Organizations become more resilient by using AI-driven insights, automated threat response, and predictive analytics. Zero Trust becomes a part of the culture of the business, which allows for self-healing and scalable cybersecurity.
The maturity model helps businesses assess their current state and plan their next steps. It encourages a proactive, risk-aligned way to protect assets in both hybrid and cloud-native contexts.
Zero Trust Benefits
Companies that use a zero trust approach change the way they protect their data by strictly restricting who can access it and constantly assessing risk. This proactive approach builds a strong infrastructure that can handle new threats while also being flexible for business.

Better Security Posture
By establishing tight identity checks and access controls, organizations make their defenses stronger. Constant monitoring and security procedures that can change quickly make sure that possible threats are dealt with quickly.
Less Attack Surface
Zero trust limits exposure by only letting verified users in under certain conditions. This controlled environment effectively limits the paths that attackers could use, which greatly lowers the dangers.
Improved Compliance and Governance
A zero trust framework sets clear rules for managing data and resources, which makes it easier to follow the rules. It makes audits easier by giving clear and centralized control over who may access what.
More Visibility and Control
Centralized tools give you real-time information about what users are doing and what is happening on the network throughout the whole enterprise. This better oversight lets you quickly respond to problems, which makes overall control stronger.
Support for Remote Work and Cloud Migration
Zero trust goes beyond physical boundaries to provide seamless security for remote workers and cloud-based businesses. Strong access restrictions that work from anywhere keep strong security standards no matter where users connect.
Organizations that adopt a zero trust strategy have a complete security posture that protects them from attacks and helps them meet changing business needs. The first step towards achieving zero trust is to prevent cyberattacks with the help of multi-factor authentication. The entire framework makes a safe space that welcomes new ideas and keeps them safe at all times.
Zero Trust Challenges and How to Overcome Them
Zero trust makes businesses constantly review and improve their security plans. It needs to be constantly evaluated and improved to keep up with emerging threats and advances in technology.
Help from Management and Users
To get people to accept the zero trust paradigm, organizations need strong support from both leaders and workers. Active champions at all levels help policies work together and create a culture of shared accountability.
Devices are growing quickly
The rise in connected devices makes endpoints more vulnerable; therefore, they need constant monitoring and strong security measures. Real-time analytics and automated enforcement tools make it easy to swiftly secure any new entry points.
Growth of Applications
Because there are so many new apps, it's important to keep track of and monitor them to manage new risks. Centralized management solutions make it easier to keep an eye on things and make sure that security measures are applied consistently.
Legacy System Integration
It is difficult to combine older systems with newer zero trust frameworks, and this can only be done through careful planning. A phased integration strategy reduces disturbance while gradually updating key functions.
User Experience and Productivity Concerns
It is important to put in place strict security measures that don't get in the way of daily tasks and productivity. Protocols that are based on the needs of users make sure that strong protection improves operational efficiency instead of getting in the way of it.
Implementation Complexity and Cost
Setting up a zero trust architecture takes a lot of planning, technical know-how, and money, which must be weighed against the long-term security benefits. Investing in scalable solutions and skilled advice turns problems into long-term, strategic value.
Cultural Change Management
To move to a zero trust mindset, the culture of the organization needs to change so that everyone is open to making things better and taking security measures. A supportive environment that keeps people interested and committed is created by thorough training and clear communication.
Organizations may build a strong and flexible security framework that protects against possible threats and helps businesses run smoothly by working together to solve these problems.
What Are the Five Pillars of Zero Trust?
Zero trust security is a new way of doing things that doesn't assume trust and checks every request. It keeps checking that users and devices are who they say they are to reduce security holes. Companies use this method to preserve important assets and keep digital spaces safe.
1. Identity
Zero trust is based on identity. It makes sure that each user is who they say they are before they can get to things, which is wise. Strong authentication systems keep anyone who shouldn't be able to get to your information from doing so.
2. Devices
We verify and test each gadget to make sure it is safe. This control keeps the network safe by stopping compromised or unmanaged endpoints from putting it at risk.
3. Networks
Network segmentation and strong access rules make it hard for people to move across the system.
To keep the digital world safe and strong, each link is checked on its own.
4. Workloads and Applications
People are continually monitoring workloads and applications to make sure that every interaction is safe.
Due to stringent monitoring and security checks, individuals cannot exploit poor services.
5. Information
Encryption, access controls, and regular monitoring are the major methods of keeping data safe. Taking proactive steps ensures that private information remains confidential and does not change.
These pillars create a robust plan to uplift your defenses and enrich cybersecurity today. They give companies the tools they need to protect their essential assets and manage risk.
Zero Trust History
Zero trust came about because standard perimeter-based security has a lot of holes in it. Studies from around 2010 showed that implicit trust in internal networks made it possible for people to migrate sideways and pose insider threats. This led experts to change their minds on trust, seeing it as a risk instead of a benefit.
As digital transformation sped up with the rise of remote work and cloud computing, zero trust became a flexible foundation. It now uses continuous verification, multi-factor authentication, and micro-segmentation to make sure that every access request is properly authenticated. This provides strong, flexible protection across distributed systems.
How to Use Zero Trust Framework for Your Business?
Never trust a user or device by default; always confirm identity and permissions before allowing access. This is known as zero trust. In order to minimize damage in the event of a breach, it constantly analyzes all interactions and micro-segments resources. A few strategies for firms to take advantage of zero trust are as follows:
- Adopt the “never trust, always verify” mindset
Every access request—inside or outside your network—must be authenticated and authorized before granting any access.
- Define your protect surfaces
List the critical data, key applications, sensitive services, and high-value identities (users, devices, and APIs) that require security.
- Map transaction flows
Map exactly how data moves between users, apps and services, so you know where to insert your controls.
- Micro-segment your environment
Break your network into tiny zones (e.g., per app or department) to stop attackers from roaming freely if they breach one segment.
- Enforce strong identity verification
Implement robust IAM with SSO, MFA and, where possible, passwordless authentication; every login must prove who and what you are.
- Grant least-privilege access
Give each user or device only the permissions needed for its role and nothing more so even compromised accounts do minimal damage.
- Monitor, log and continuously improve
Collect real-time telemetry on every access attempt, analyze for anomalies, plug gaps, update policies—and repeat the cycle.
To safeguard your company's assets, implement zero trust by confirming each access request, imposing least-privilege restrictions, and conducting ongoing monitoring.
Why Choose miniOrange for Zero Trust?
miniOrange is the leader in providing a complete Zero Trust solution that protects digital assets in changing contexts. It has strong multi-factor authentication capabilities, like its flagship miniOrange MFA product, that makes sure only verified users can access important resources, no matter where they are on the network. Its solution works perfectly with both on-premises and cloud ecosystems, which lowers the risks of lateral movement and possible breaches.
miniOrange goes beyond robust authentication and its types by letting businesses set up fine-grained access controls and micro-segmentation that fit nicely with Zero Trust principles. The software centrally manages security settings for various networks and endpoints, continuously monitoring risk factors using real-time threat information. This all-encompassing method not only makes things safer, but it also makes them easier for users. This approach makes miniOrange the best choice as your modern, flexible security software partner.
Getting Started with Zero Trust using miniOrange
The first step in putting zero trust into action is continuous validation, where every access request goes through dynamic, context-based authentication. miniOrange helps businesses keep their data safe by separating identity verification from access control and reacting to new threats.
- Authentication Based on Context
miniOrange uses real-time situational data, including device posture, location, and behavior, to figure out how risky something is. This dynamic mechanism makes sure that access is only provided when the present conditions fulfill strict security standards.
- Authentication vs. Authorization
The platform separates checking a user's identity with authentication from authorization, which is deciding what actions are allowed. This clear difference makes sure that verified identities can only access the resources that policy allows.
- 2FA or MFA
Two-factor authentication (2FA) adds a basic level of protection, but multi-factor authentication (MFA), like miniOrange's MFA offering, enables layered, adaptive verification. MFA uses more than just two steps to improve security. It also uses contextual and behavioral clues to do this.
When you use miniOrange to implement zero trust, you get continuous, smart access verification and fine-grained policy management. This method not only makes security stronger in distributed contexts, but it also makes the user experience better without lowering protection. Check out the miniOrange ecosystem for identity and access management with a 30-day trial or schedule a call with our engineer.
FAQs
What is an example of a zero trust policy?
A zero trust policy can say that every person and device must utilize multi-factor authentication to get to any company resource. They can only access the applications and data they require for their job. We keep an eye on all activity for any signs of suspicious conduct, and any strange access is quickly reported or denied.
How can organizations address potential user resistance to zero trust?
Organizations can deal with resistance by making zero trust processes as easy and frictionless as feasible, like by implementing single sign-on and background checks. People are more likely to grasp and accept something if they are told clearly what the benefits are and given training and support. Automation may make things even smoother, ensuring safety without getting in the way of regular tasks.
What is zero trust in simple terms?
Zero trust is a security model that doesn't automatically trust any person or device, even if they are on the network. Strict authentication and authorization checks are used to make sure that every access request is real. Only the least amount of permissions are given, and all actions are watched for threats all the time.
Is zero trust a product or a strategy?
Zero trust is a full security plan, not just one product. It is a set of rules and guidelines that use different tools and technologies to check every user, device, and action before giving access. Organizations use a mix of rules, processes, and security technologies to put Zero Trust into action.
What are the five pillars of zero trust?
Identity (checking users), device (making sure endpoints are safe), network (dividing and watching traffic), application and workload (managing app access), and data (protecting and limiting access to critical information) are the five pillars of zero trust. As a group, the pillars make up a layered, defense-in-depth security posture. These pillars ensure constant access checks and limits, thereby reducing the likelihood of breaches.


Leave a Comment