Need Help? We are right here!
Search Results:
×Cryptographic key management in PAM involves techniques and processes to create, store, distribute, rotate, and retire cryptographic keys, to protect privileged credentials from being accessed within an organization. miniOrange makes use of both AES 256 and AES 128, global encryption standards to secure the user data.
In simpler terms, it’s like having a digital vault that protects the secret codes used to lock and unlock your sensitive data.







Cryptographic key management in PAM is a structured process, where only authorized users can access and use confidential data.
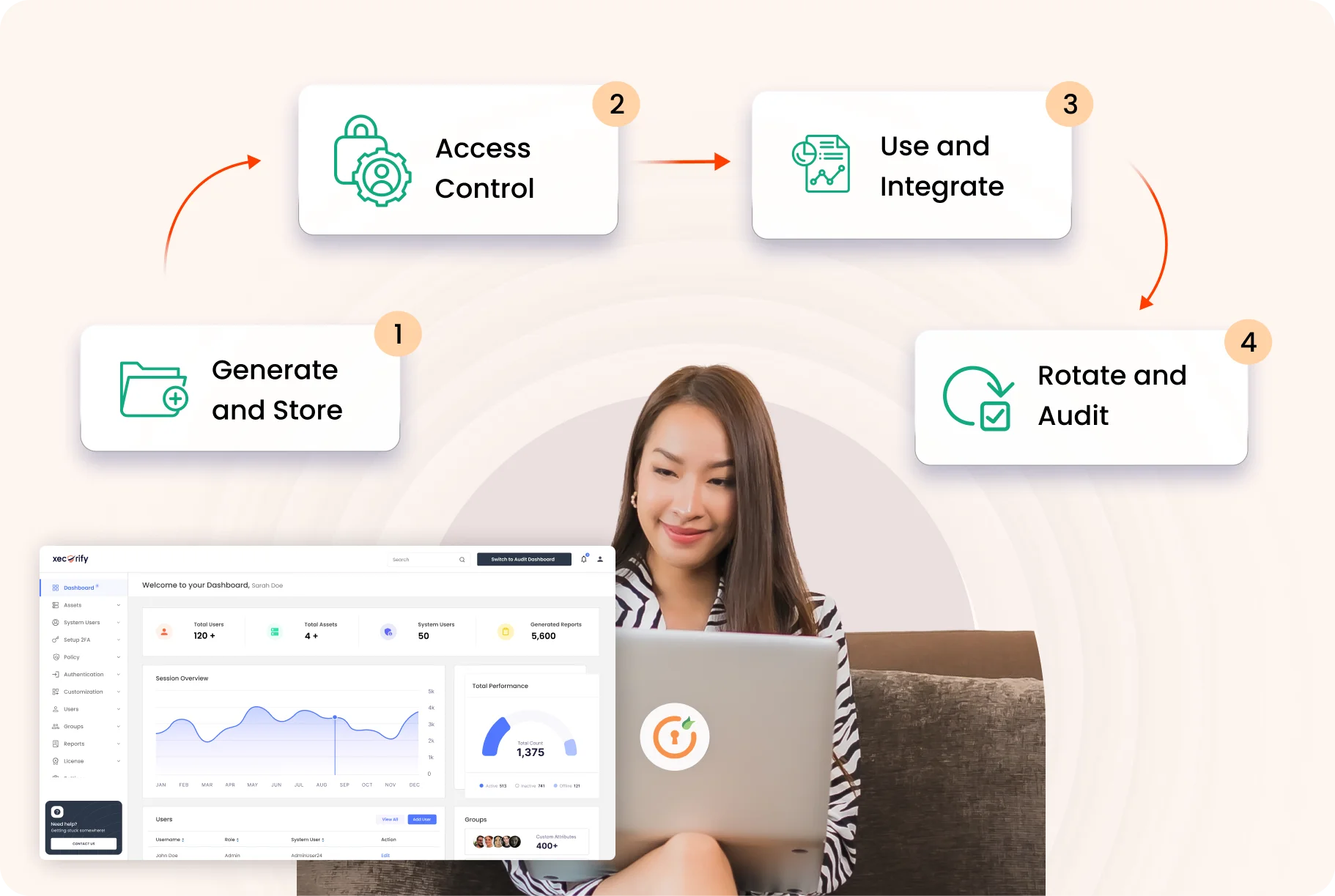
Here’s a comprehensive explanation on its working:
This is a centralized vault to securely store encryption keys with hardware security modules (HSMs) or encrypted databases, secrets, and certificates. HSM doesn't allow the keys to leave the system unencrypted, thereby preventing theft or tampering.
Permission to use the keys depends on roles, with granular access control, so only authorized users can access or manage specific keys, thus preventing unprivileged access to applications and databases.
The cryptographic keys are auto-replaced on a stringent schedule or triggered by strict policies. Short life span of keys prevents compromises and maintains a solid encryption hygiene. Automation password rotation also eliminates human errors and takes care of compliance protocols.
Events for every key usage and access are logged in detail, including who used each key, when, and for what purpose. These logs offer an in-depth audit trail, which can be later used to spot any kind of compromising situations.
Instantly revoke or expire keys if compromised or no longer needed. Revocation blocks further usage of the keys, averting unwanted access.
Cryptographic keys are consolidated within PAM workflows such as session management, password vaults, and apps. This keeps the keys hidden from users while accessing PAM workflows.
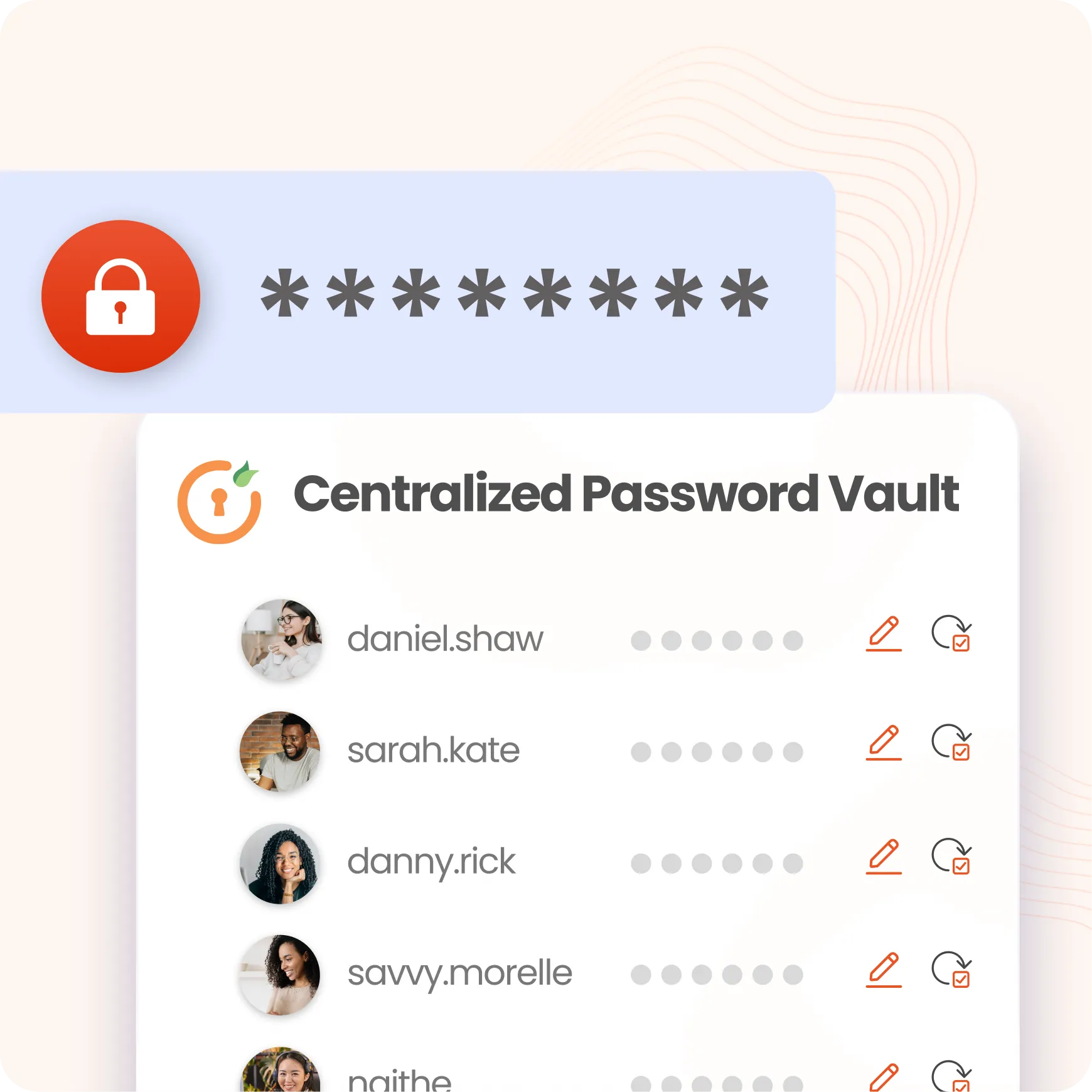
Cryptographic key management in PAM encrypts sensitive information like credentials, logs, and session data, making the data unreadable to suspicious users.
PAM with key management easily meets requirements for GDPR, HIPAA, PCI-DSS, and more, by simply enforcing access policies, automating key rotation, and maintaining audit logs.
Modern PAM solutions are developed to integrate keys with the existing IT infrastructure, apps, and automation tools. This enables safe workflows on cloud, on-premise, and hybrid architectures.
