Need Help? We are right here!
Search Results:
×Hardware Security Module (HSM) is a physical device that performs cryptographic functions such as encryption, decryption, key management, authentication, key exchange, and more. Integration of an HSM in Privileged Access Management, offers an additional layer of security for protecting the master keys that underpin the privileged access, thereby helping organizations meet compliance requirements and protect themselves against external or internal attacks.
Make the best out of PAM HSM Integration with miniOrange as we assure smooth HSM integration, and focus on Zero Trust principles and future-proof architecture for every type of threat. Plus, we’re always there to solve any queries around-the-clock.







Integration of HSM with miniOrange PAM maximizes the security of cryptographic keys by using tamper-resistant hardware key generation, management, and storage. Plus, integration of PAM with an HSM can handle every encryption and decryption method.
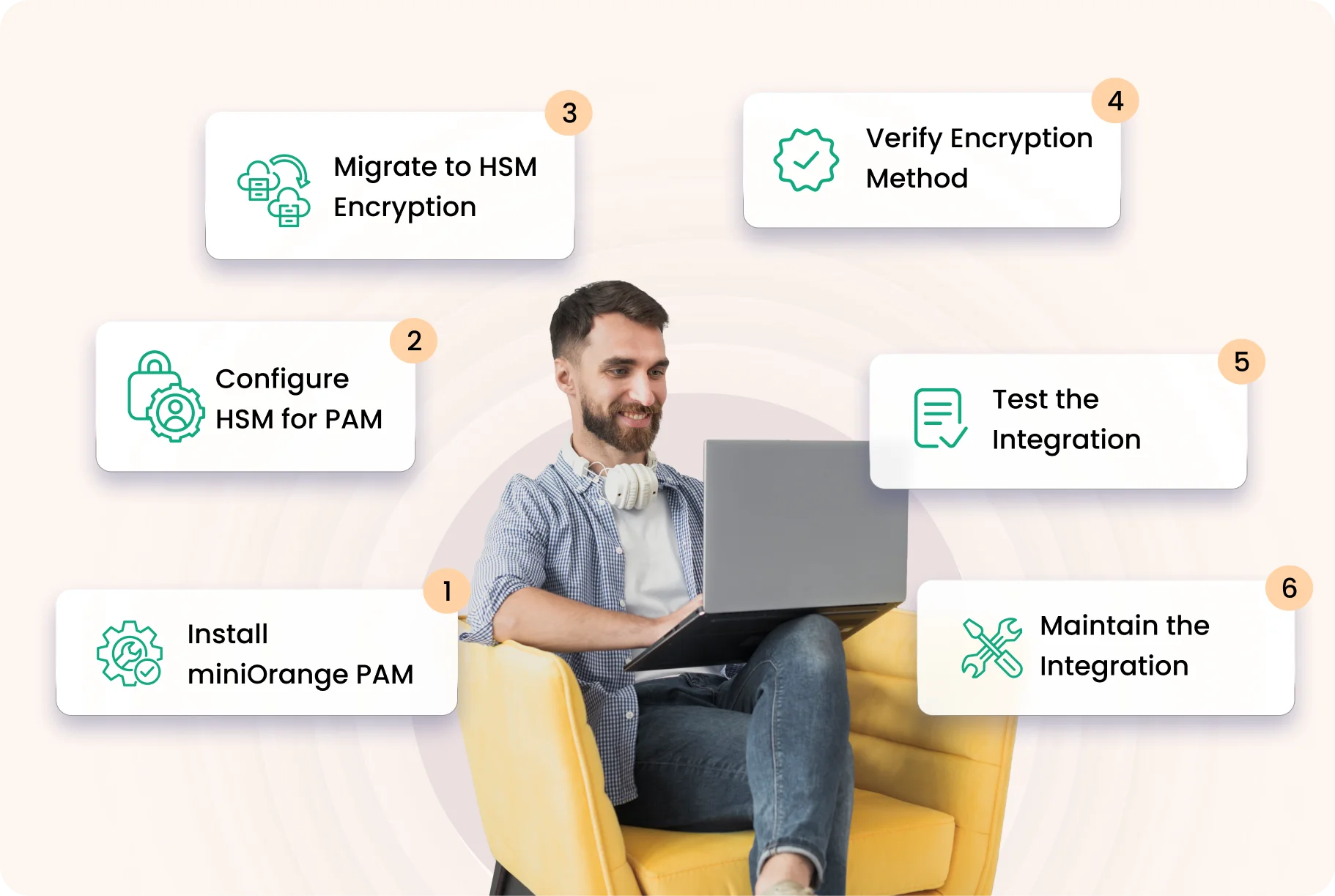
For efficient integration, download and install the miniOrange PAM on the server, followed by configuration of HSM for PAM. Refer to the miniOrange handbook or support team for advanced configurations. After configuration, migrate to the HSM encryption method and verify which encryption method is applied. Test and validate the integration, and maintain the integration to its utmost state.
When HSM is integrated with PAM, they store, generate, and manage keys, assuring that even if a hacker accesses or manipulates the keys, the hardware blocks the attacks, making them tamper-resistant.
A Hardware Security Module (HSM) is usually validated against stringent security standards such as FIPS 140-2 Level 3. This certificate meets the federal rules for cryptographic modules.
HSMs are developed to automatically generate strong encryption keys, and manage their lifecycle, including rotation, archival, and destruction. This reduces manual intervention, minimizing the risk of human error.
Every usage of the key, whether it is encryption, decryption, or authentication, is recorded, thereby supporting full audit trails.
Current PAM software integrates with both cloud and on-premise based HSMs, providing flexibility for organizations operating in multi-cloud and hybrid environments.

Hardware-backed approach minimizes the risk of internal and external breaches, which is essential for the Zero Trust philosophy.
PAM HSM Integration is compliant for standards like FIPS 140-2, HIPAA, GDPR, and other global benchmarks.
Eliminate the risks associated with keys being scattered across multiple locations or systems, as HSM with PAM centralizes the storage of these keys.
