Need Help? We are right here!
Search Results:
×The modern PAM uses IP filters for IP-based access control to block unauthorized networks at the edge by checking source addresses. Geo-fencing, or geo-access, means to enforce rules based on location and flag VPN or proxy attempts. System for managed device state, operating system health, certificates, and hardware IDs are all checked by device verification before privileged access is granted. These restrictions collaborate to create a model for defense in depth to prevent unauthorized attacks, make sure everyone follows the rules, and let trusted users access without any problems.
The upshot is a lot less risk of breaches, uniform audit records that make inspections faster, and more productivity as legitimate personnel get around superfluous obstacles. This makes PAM a strategic asset for both security and operational flexibility.







IP restrictions validate the source network before deeper location and device checks kick in.
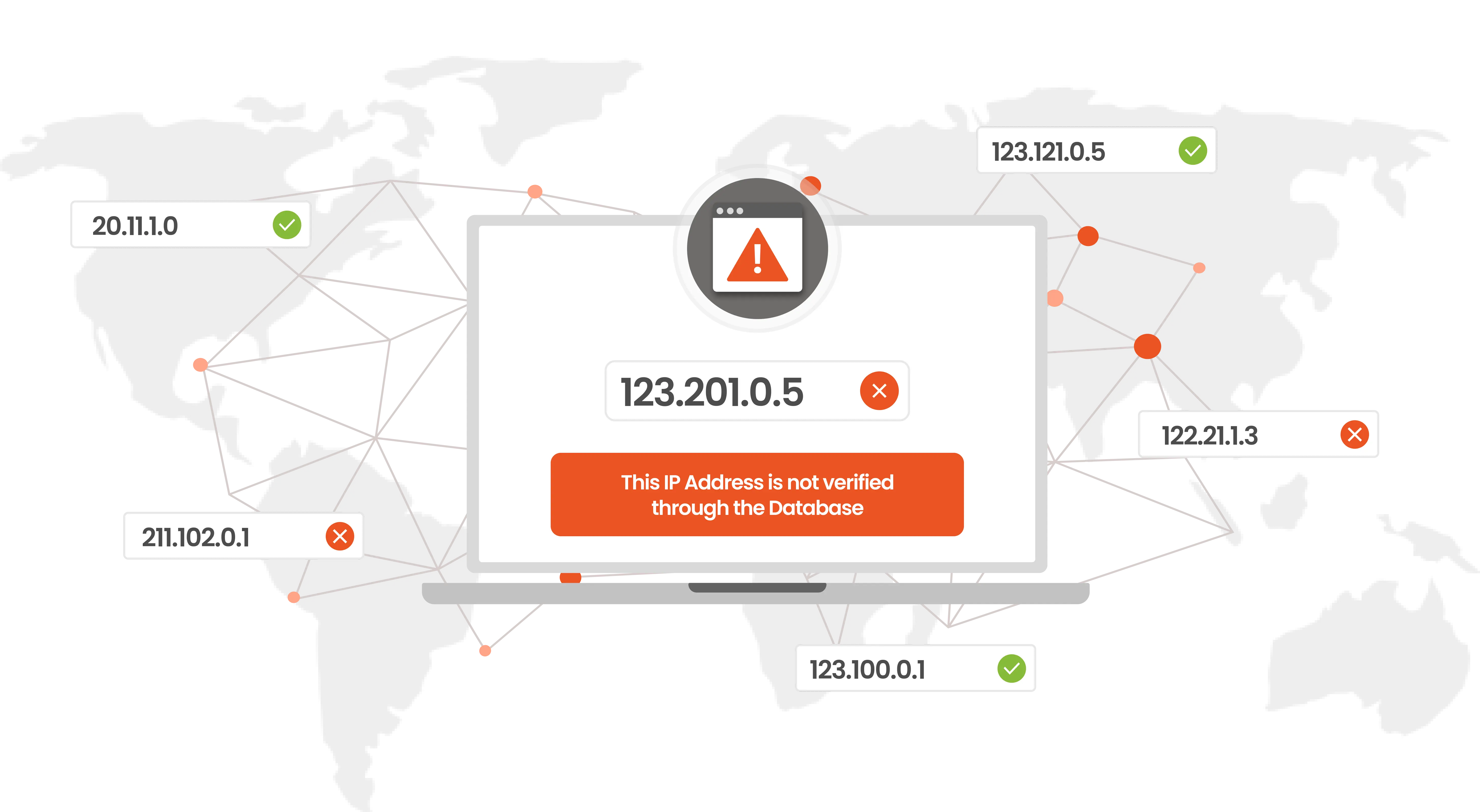
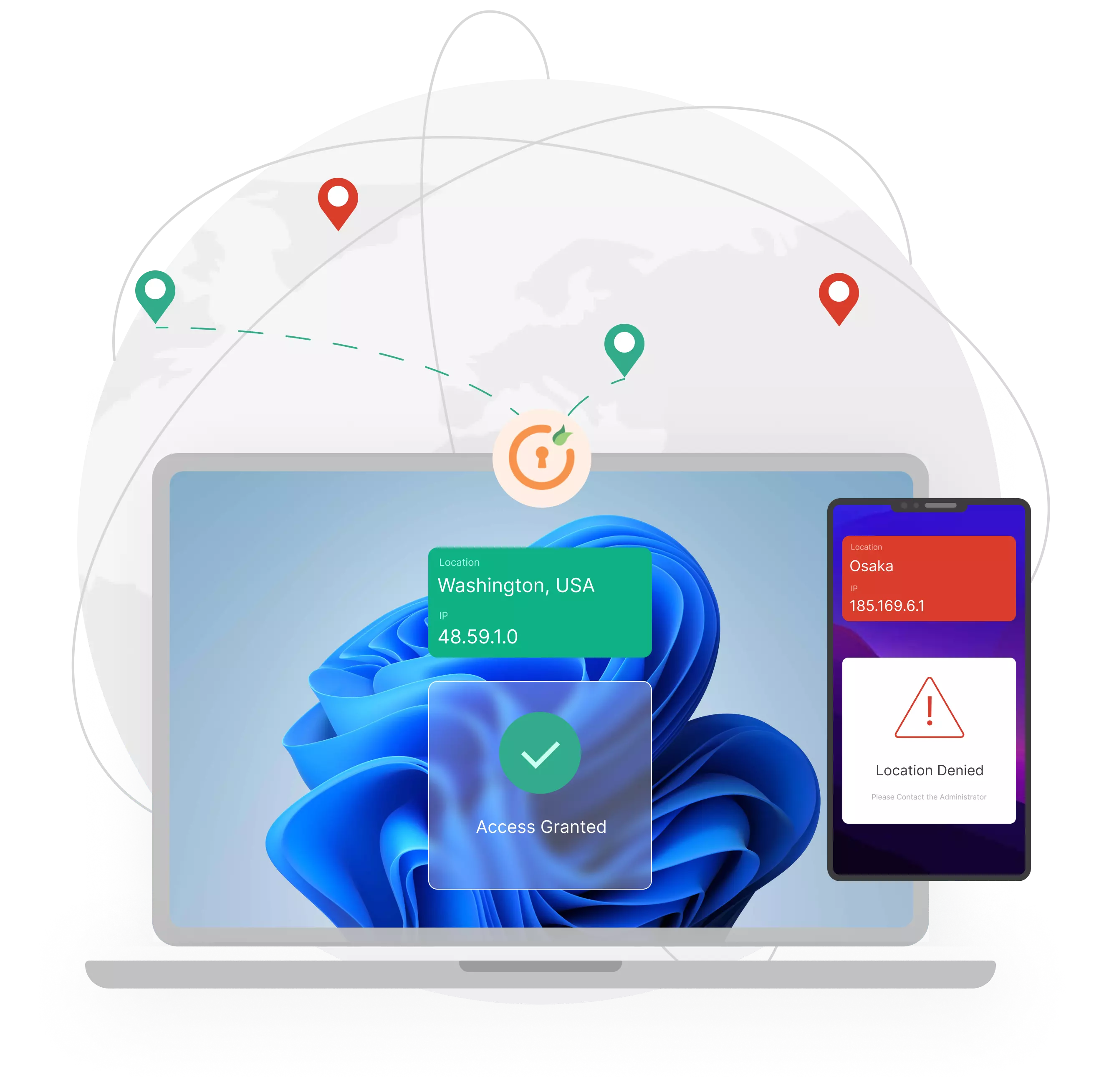
Geo-blocking restrictions enforce location-based policies in tandem with IP and device checks.
Device controls inspect endpoint security before IP and geo layers permit access to the user.
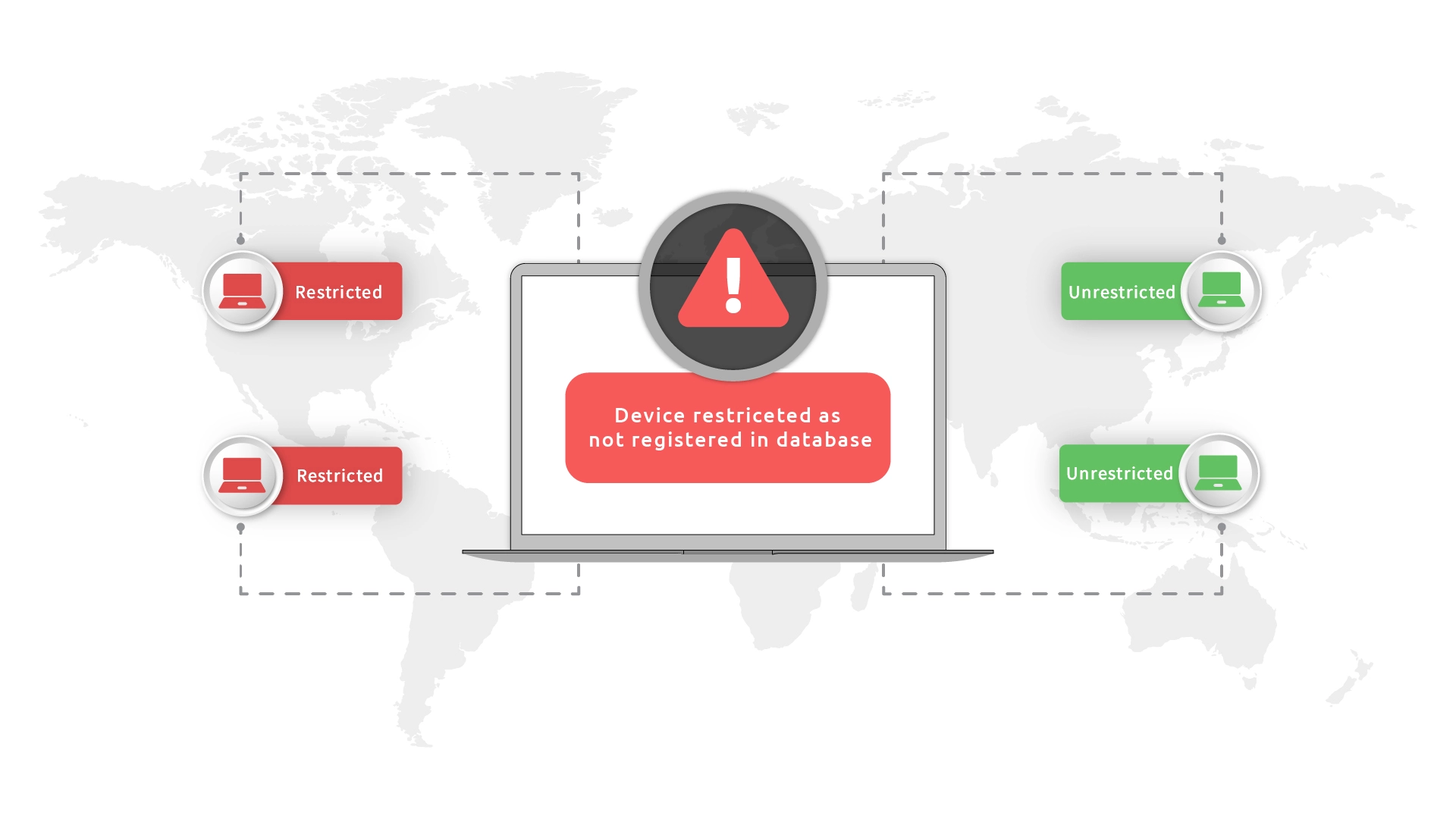
Minimize breach costs by blocking unrecognized IPs and devices before they reach sensitive systems.
Elevate user experience and simplify user journey with user workflows for trusted users to balance security and convenience.
Restrict privileged user access only to approved regions and corporate-issued hardware. Ensure what happens in your organization stays within alongside your trade secrets.
Apply strict security policies for a global workforce with a seamless, policy-driven access control across office and home networks.
Boost confidence by showcasing granular controls that safeguard your customer and partner data.





I can't speak highly enough regarding miniOrange, I am totally satisfied with the process and results in every regard.
5.0

Awesome tech service, Awesome product. Overall Awesome people. This solution is very simple and easy to implement
5.0
