Need Help? We are right here!
Search Results:
×Privileged Session Management (PSM) is a security practice that controls, monitors, and records access to privileged accounts during user sessions, ensuring only authorized individuals can access sensitive systems and data.
It utilizes advanced vaulting technology within PAM sessions, PSM provides a robust framework for managing privileged accounts and offers comprehensive audits through detailed session recordings and video logs of all activities conducted by IT administrators on remote systems. By facilitating a secure log-in to target systems or applications through a proxy machine, PSM ensures that privileged credentials remain protected.
A privileged session manager maintains system security, particularly in sessions where users with administrative rights access critical IT infrastructure, locally or remotely. Example: a database administrator engaging in a PAM session to access sensitive corporate data or a third-party vendor using remote access tools within a management session. This layer adds essential oversight and accountability, preventing misuse and ensuring compliance with established privileged access management (PAM) policies. Ultimately, the privileged session manager acts as a control point, enhancing security and ensuring that administrative activities are conducted safely and with best practices.
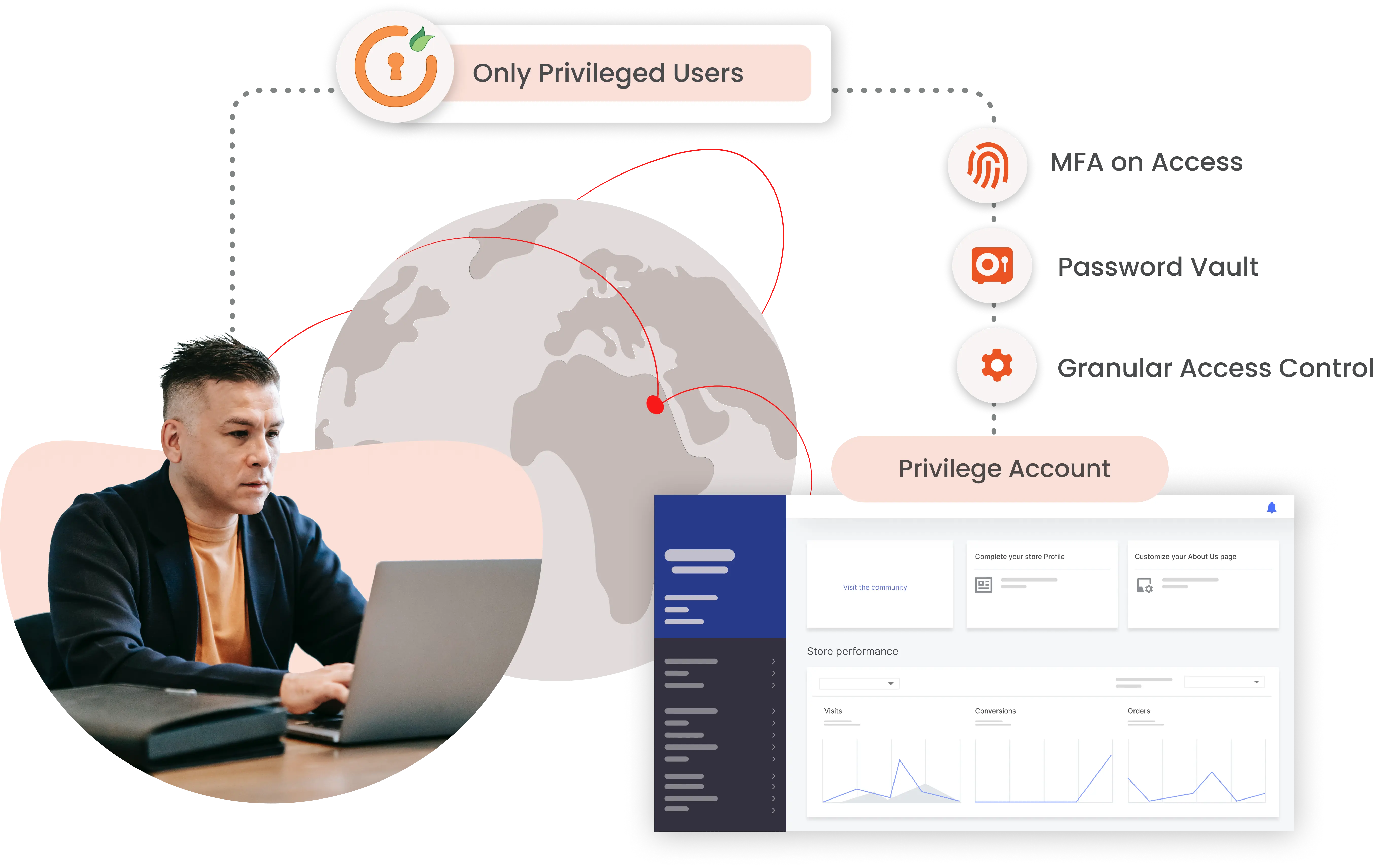
Remote session management plays an important role in Privileged Access Management (PAM), facilitating secure user or system authentication during sessions with elevated privileges. It ensures the safe transmission of complex credentials over encrypted network communications, safeguarding information from unauthorized access.
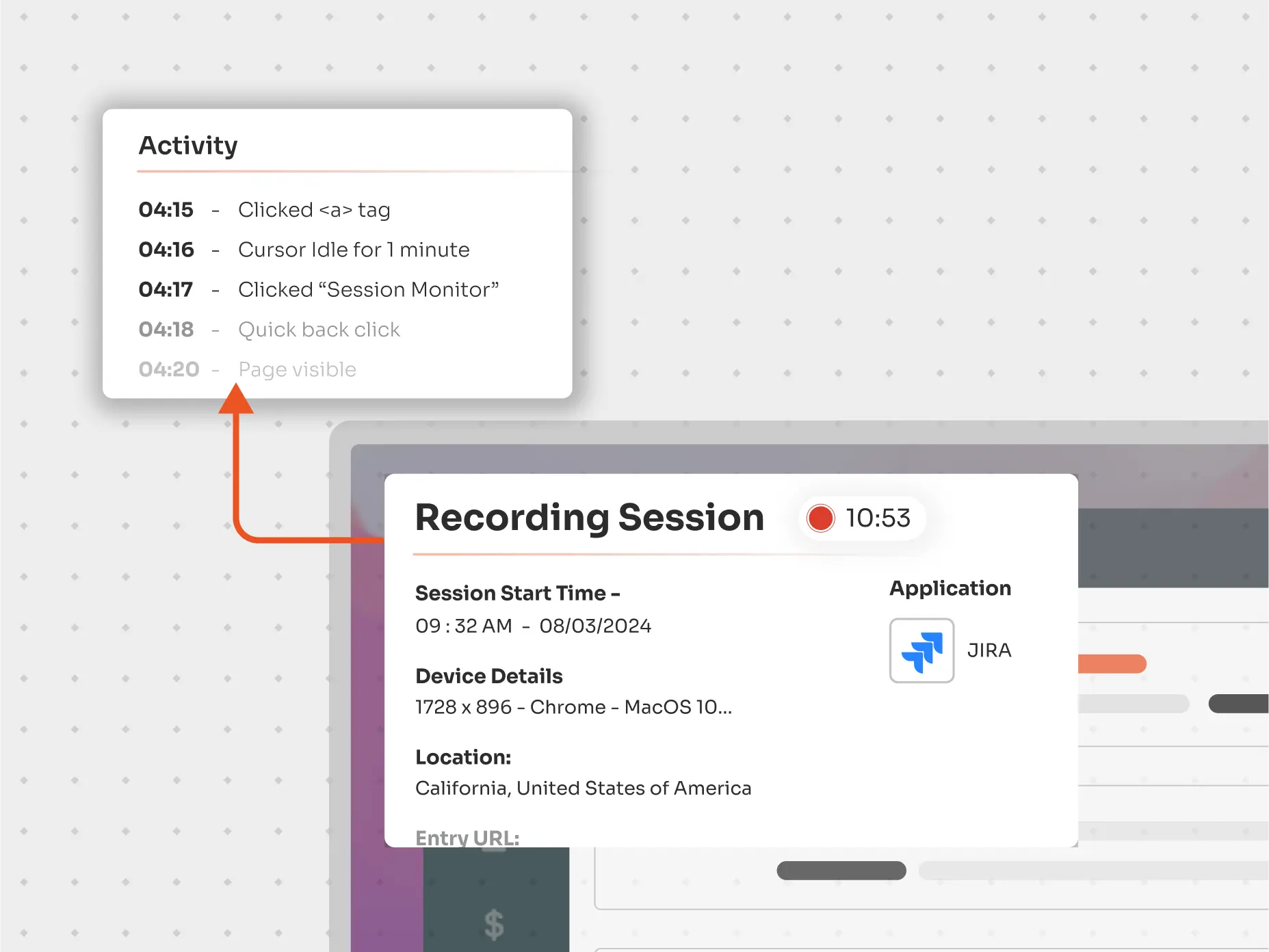
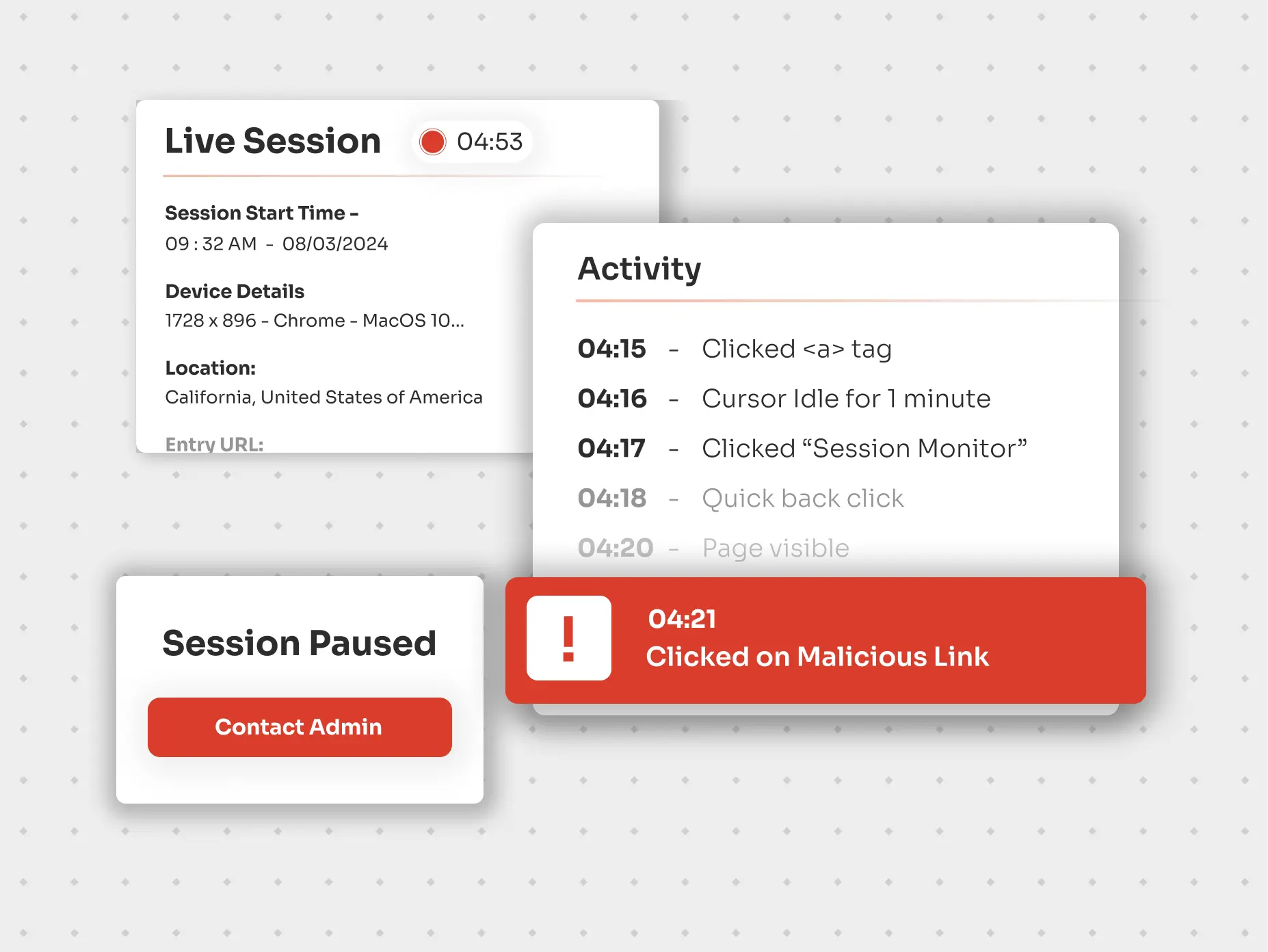
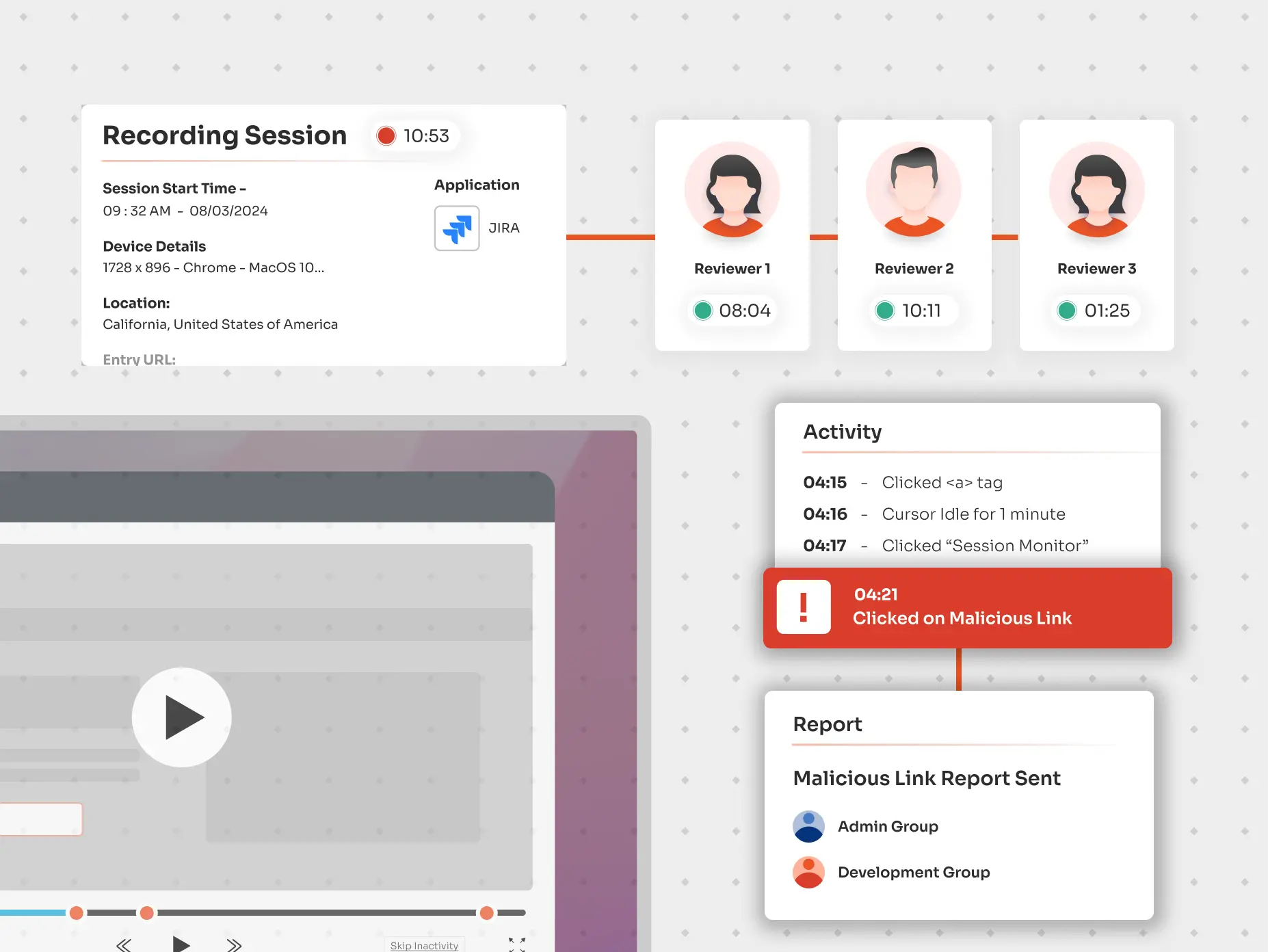
Through live-session monitoring It oversees privileged sessions in real-time, allowing administrators to detect suspicious or unauthorized activities, particularly in scenarios involving critical systems, remote desktops, or external vendors.
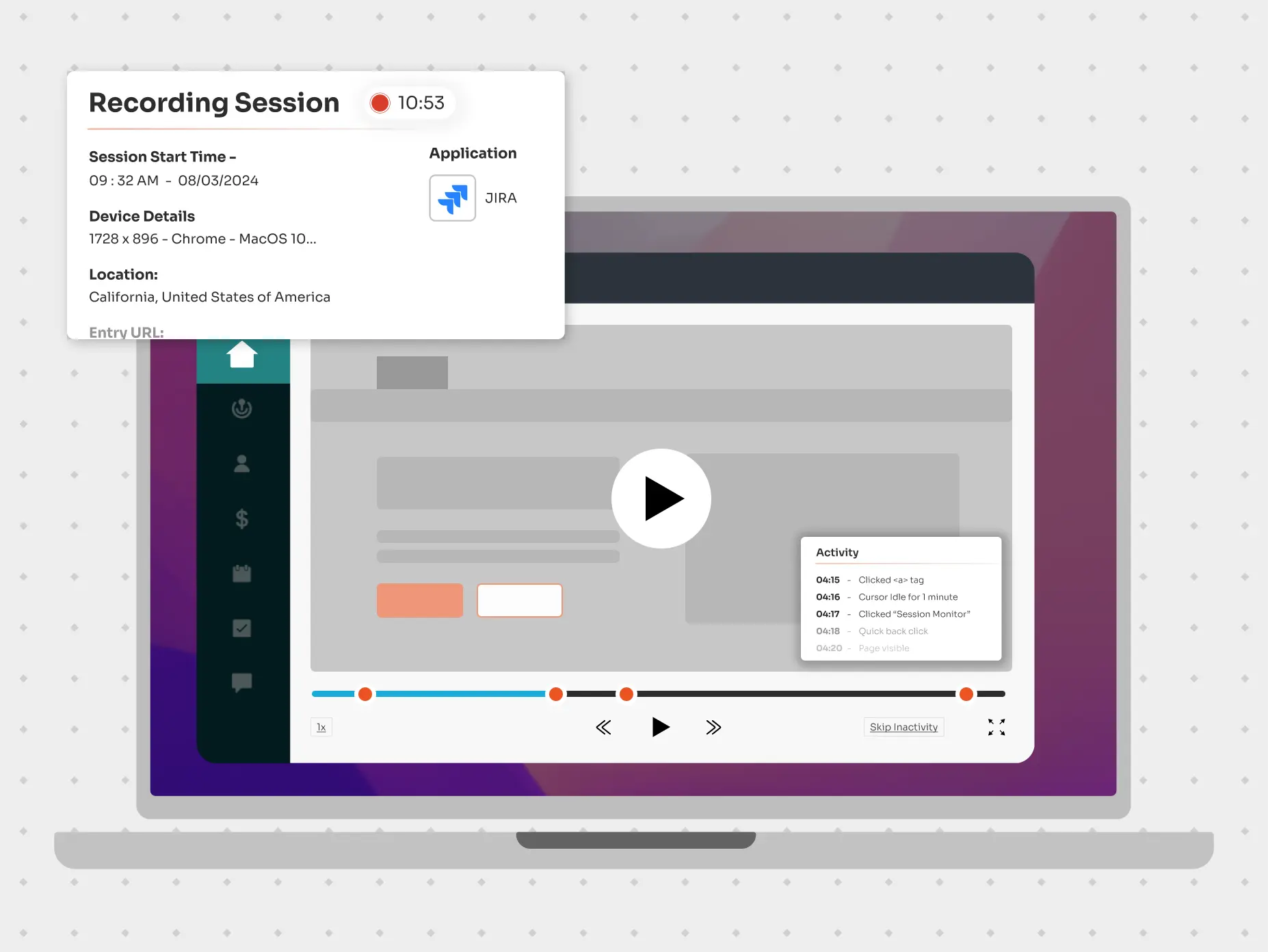
It is a valuable security tool that captures every keystroke and action taken during a session for future review and analysis. In the event of a privileged attack, session recording allows organizations to sift through past recordings to identify the source of the breach and adjust security policies to prevent incidents.
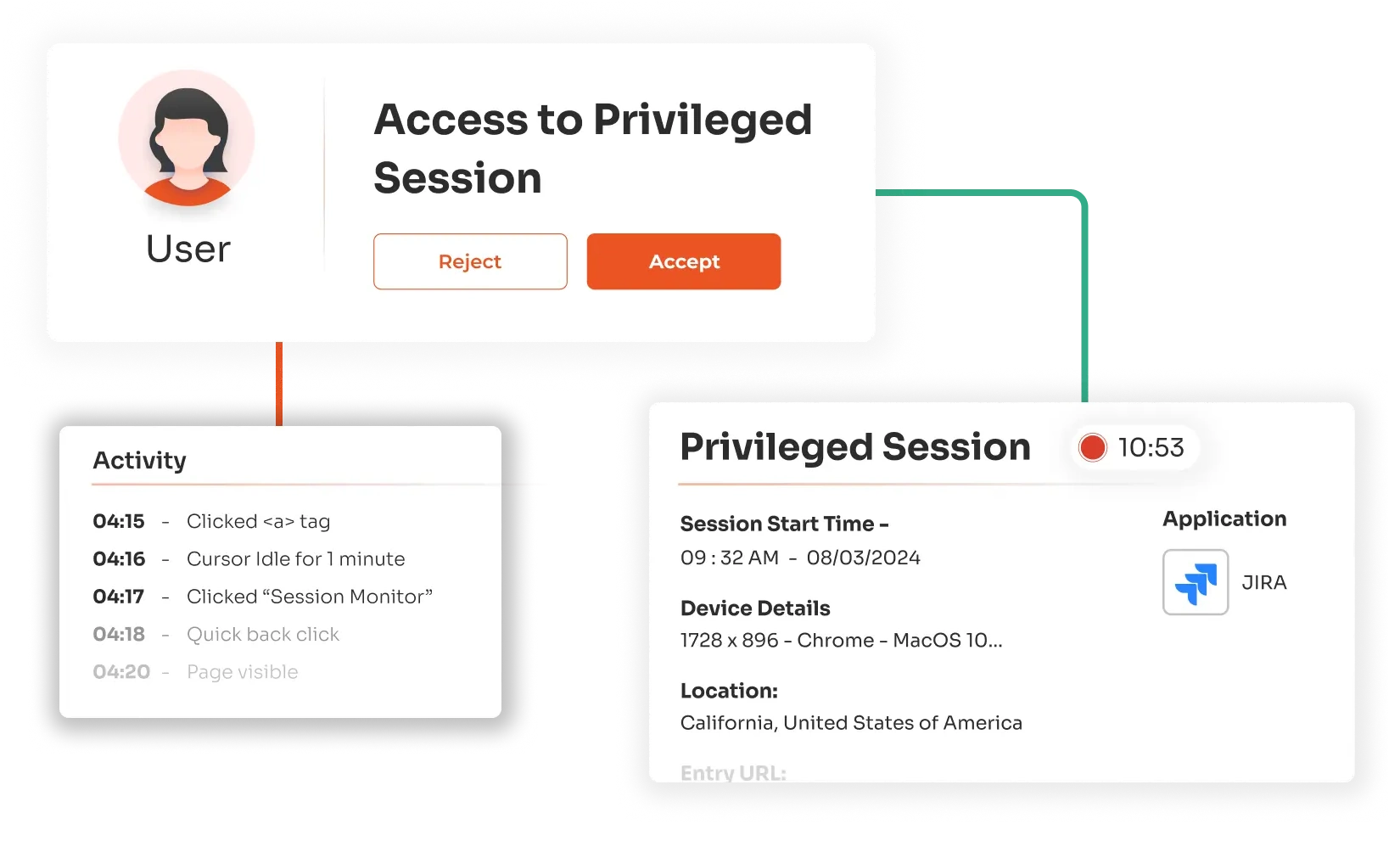
Workflow management in privileged account security can be enhanced by incorporating approval requirements for accessing privileged sessions. This setup reinforces security and ensures transparency regarding who is accessing sensitive information and why.
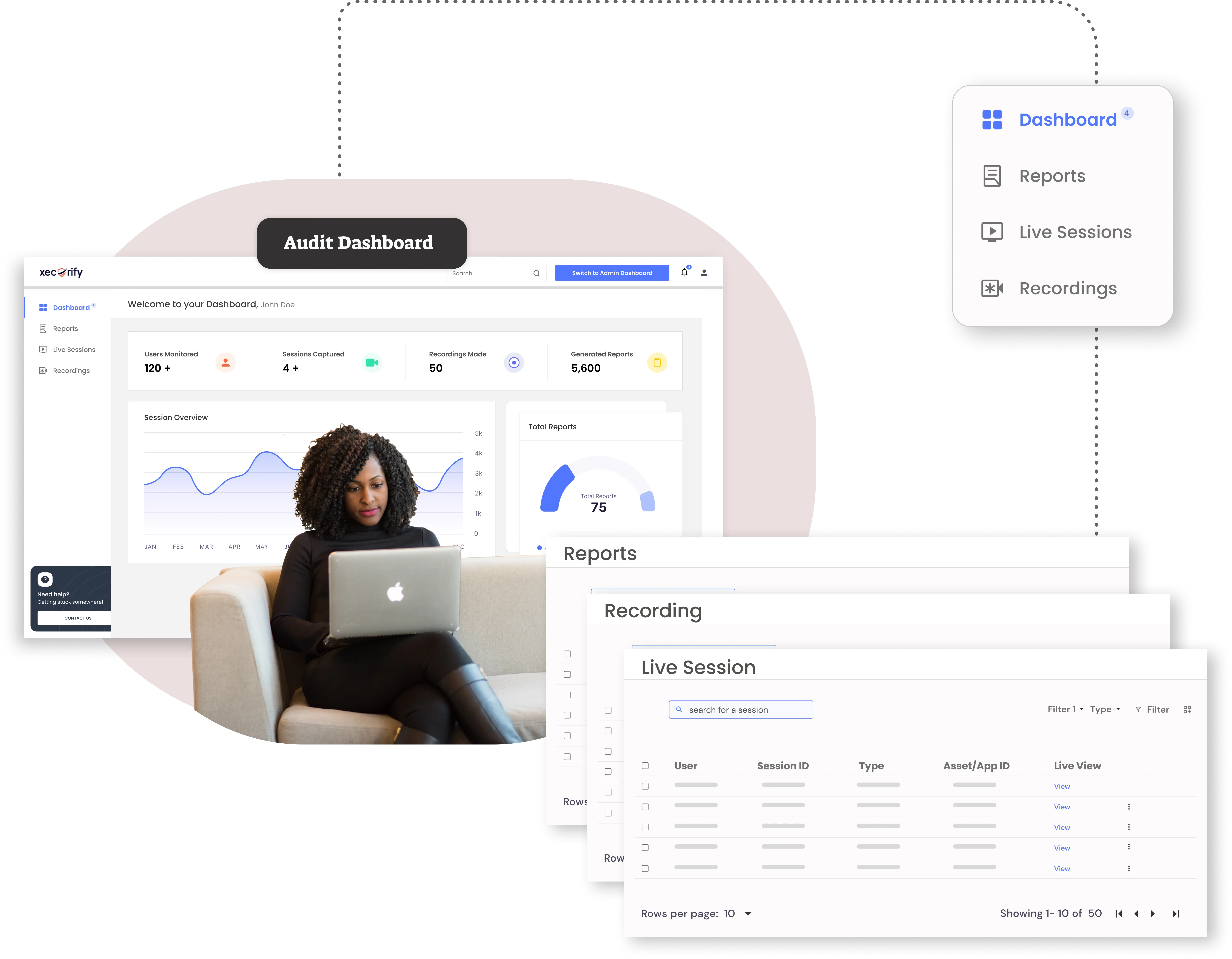
Auditing and reporting of privileged sessions are crucial for maintaining compliance with rigorous regulations such as HIPAA, SOX, and PCI, which require monitoring of actions performed by privileged accounts. Here’s how advanced session management systems facilitate this:







PSM creates a safe link between users and systems, blocking unauthorized access and removing the need to share passwords.
Quickly grant and remove temporary access for third parties, ensuring they only get what they need without permanent passwords.
Customize login and registration pages with multi-language support for a smooth experience for employees, customers, and partners.
Supports all SSO protocols (SAML, OAuth, LDAP, etc.) for easy integration with any app.
Admins can manage groups, roles, and permissions, while tracking user logins with downloadable reports.
Meet data regulations like GDPR, NIST, PCI DSS, and SOC by integrating SSO effortlessly.
Privileged Access Management seamlessly integrates into your existing infrastructure, ensuring secure and
managed access to critical systems





I can't speak highly enough regarding miniOrange, I am totally satisfied with the process and results in every regard.
5.0

Awesome tech service, Awesome product. Overall Awesome people. This solution is very simple and easy to implement
5.0
Privileged Session Management focuses on controlling, monitoring, and recording sessions of privileged users. whereas Privileged Access Management (PAM) is an identity security solution that focuses on ensuring that only authorized individuals can perform critical tasks within an organization's IT environment. PSM is considered as a subset of PAM, as most pam solutions including miniOrange provides PSM features.
Privileged sessions in PAM (Privileged Access Management) are secure, monitored sessions that grant users temporary access to critical systems and resources with elevated permissions.
These sessions are controlled through privileged session management techniques to ensure that all activities are recorded and that access is only granted for the duration necessary to complete specific tasks.
To create a privileged session, a privileged session manager in a PAM environment is used. The process typically involves the following steps: a user requests access to a resource, the request is evaluated against established policies, and upon approval, the session is initiated through a secure, controlled environment.
This privileged session allows for detailed auditing and monitoring as per compliance and security requirements.
PSM is required by every organization that has users with elevated access to sensitive systems and high-value data, where it is necessary to monitor, record and control the privileged activities to prevent insider threats and detect suspicious activity. It is also essential for Organizations in regulated industries to comply with regulations like HIPAA, PCI DSS, SOX, GDPR, and NIS2.
In cybersecurity, PSM (Privileged Session Management) is a component of PAM that focuses on securing, managing, and monitoring privileged sessions. This management session strategy is vital for preventing unauthorized access and potential security breaches by providing a secure, monitored gateway for accessing critical systems and data.
A privileged session manager is crucial for cloud environments as it provides secure access to cloud-based resources and services. It ensures that all privileged sessions are conducted within a secure, isolated management session framework, reducing the risk of data breaches and unauthorized access.
The manager also facilitates compliance with various regulations by ensuring that all actions taken during a session are logged and auditable.
miniOrange PAM comes with a privileged session management that regulate and monitor all remote privileged access in your organization. It provides real-time monitoring and session recording enabling organizations to monitor privileged sessions and capture privileged user activity in real-time also gives the functionality to escalate the suspicious activities.
