Contents
Generic SAML Integration
Step 1: Setup Identity Provider to enable SAML for your module
Pre-requisite: You will need SAML information from your IDP to configure this app. Please get SAML metadata from your Identity Provider. If your IDP does not have a metadata URL or XML, please ask for the following information:
- Issuer/ Entity ID.
- SAML Login URL.
- SAML Logout URL (only if you want users to logout from IDP when they logout from atlassian application. eg.Jira).
- X.509 Certificate.
- NameID format (optional).
- SAML Login binding type (optional).
- SAML Logout binding type (optional).
- Provide setup information to your Identity Provider so that they can configure atlassian application as a SAML Service Provider for your account. You can provide them the SAML metadata URL or SAML related information. We have given more information on how you can get each one of them below.
- Go to Service Provider Info and give the link shown below to your Identity Provider. When you click on the link, you will be able to view the metadata for the SAML Single Sign On app.
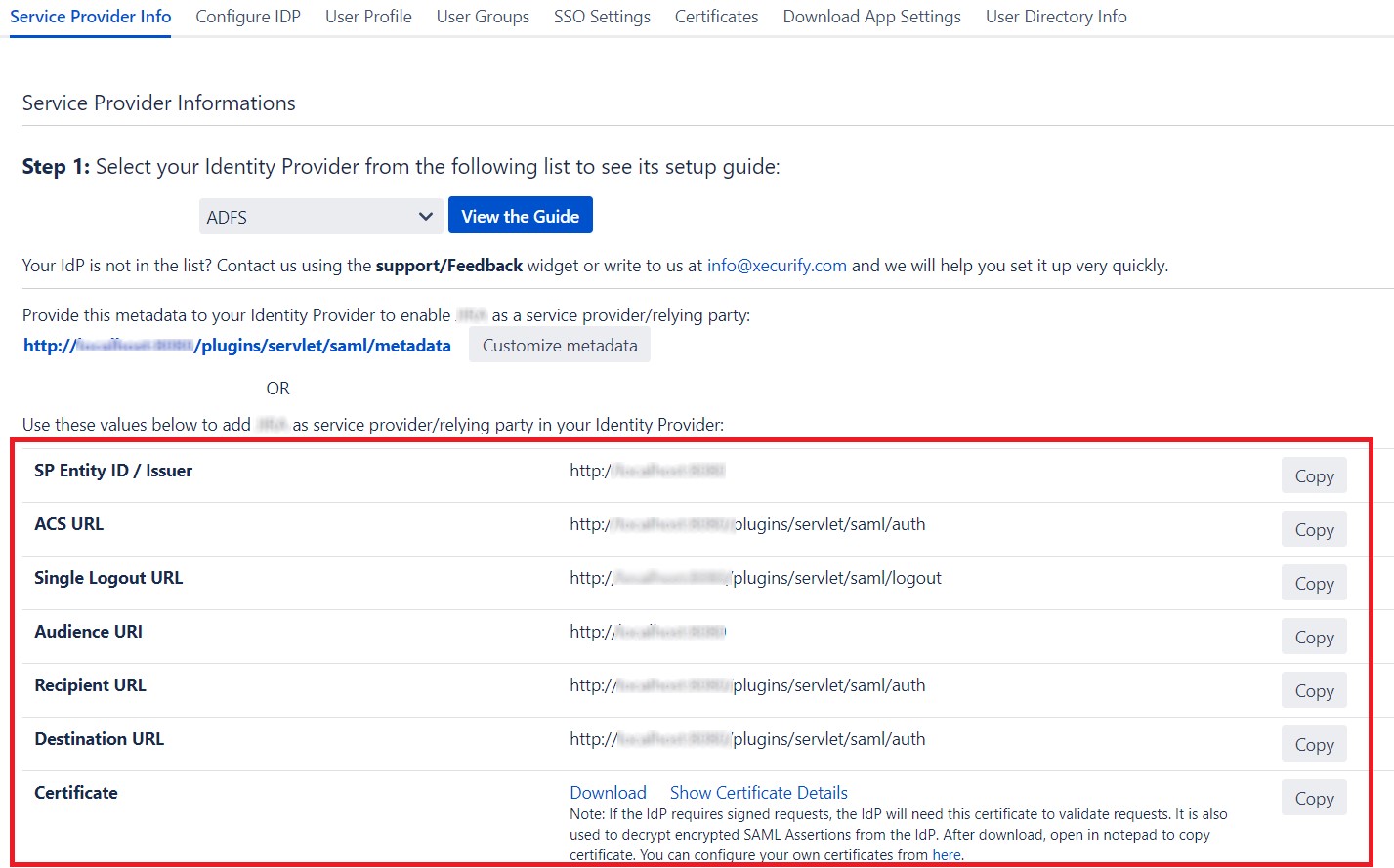
- If the Identity Provider does not accept metadata, you can give them SAML information manually. Go to Service Provider Info tab and get the following information.
| SP Entity ID / Issuer | This value contains unique identifier for your Atlassian application. |
| ACS URL | This is the URL the IdP will return SAML authentication requests to. |
| Single Logout URL | This will terminate all server sessions established via SAML SSO. |
| Audience URI | IdP will prepare SAML authentication requests for. |
| Recipient URL | IdP will return SAML authentication requests to. |
| Destination URL | IdP will return SAML authentication requests to. |
| Certificate | This Certificate is used validate SAML request and used to decrypt encrypted SAML assertions from the IDP. |
×
![ADFS_sso]()
