Contents
SSO Integration in Helpdesk with Okta and Azure
You can now allow External Customers to login into Jira Service Management (previously Jira Service Desk or JSD) via SSO! SSO Integration with Helpdesks allows you to use your existing IDP to sign into Jira Service Management (Jira Service Desk or JSD) and it also supports multiple IDP's.
Download And Installation
- Log into your Jira instance as an admin.
- Navigate to the settings and Click on Apps.
- Locate SSO integration with Helpdesks.
- Click on free trial to begin a new trial SSO integration with Helpdesks.
- On menu bar click on Apps. Locate SSO integration with Helpdesks to start configuring SSO for customers.
Step 1: Get metadata from miniOrange
- Login to miniOrange Admin Dashboard
- Go to Identity Providers and click on Add Identity Provider button from top right corner.
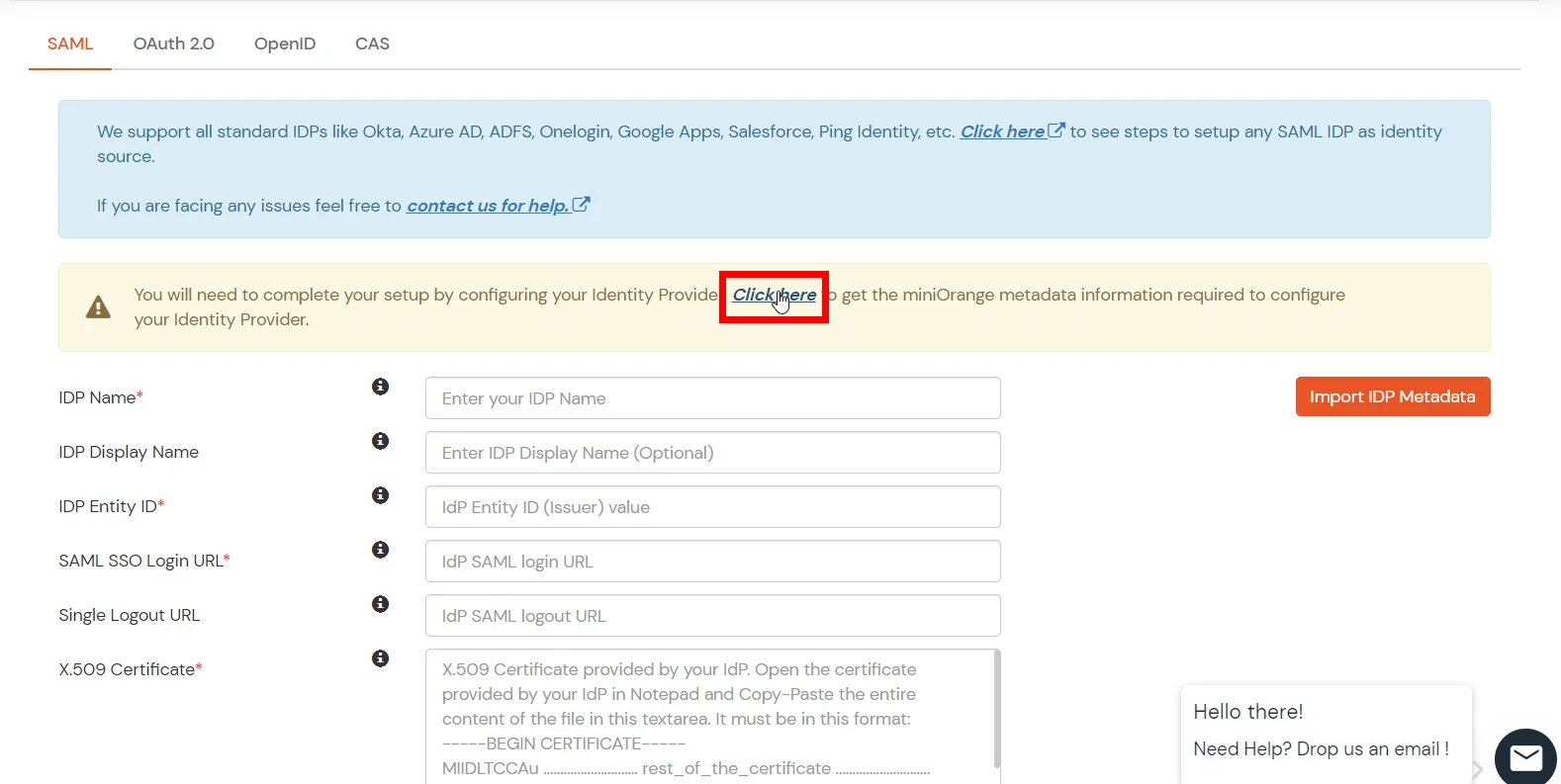
- Click on Click here link from the alert box.
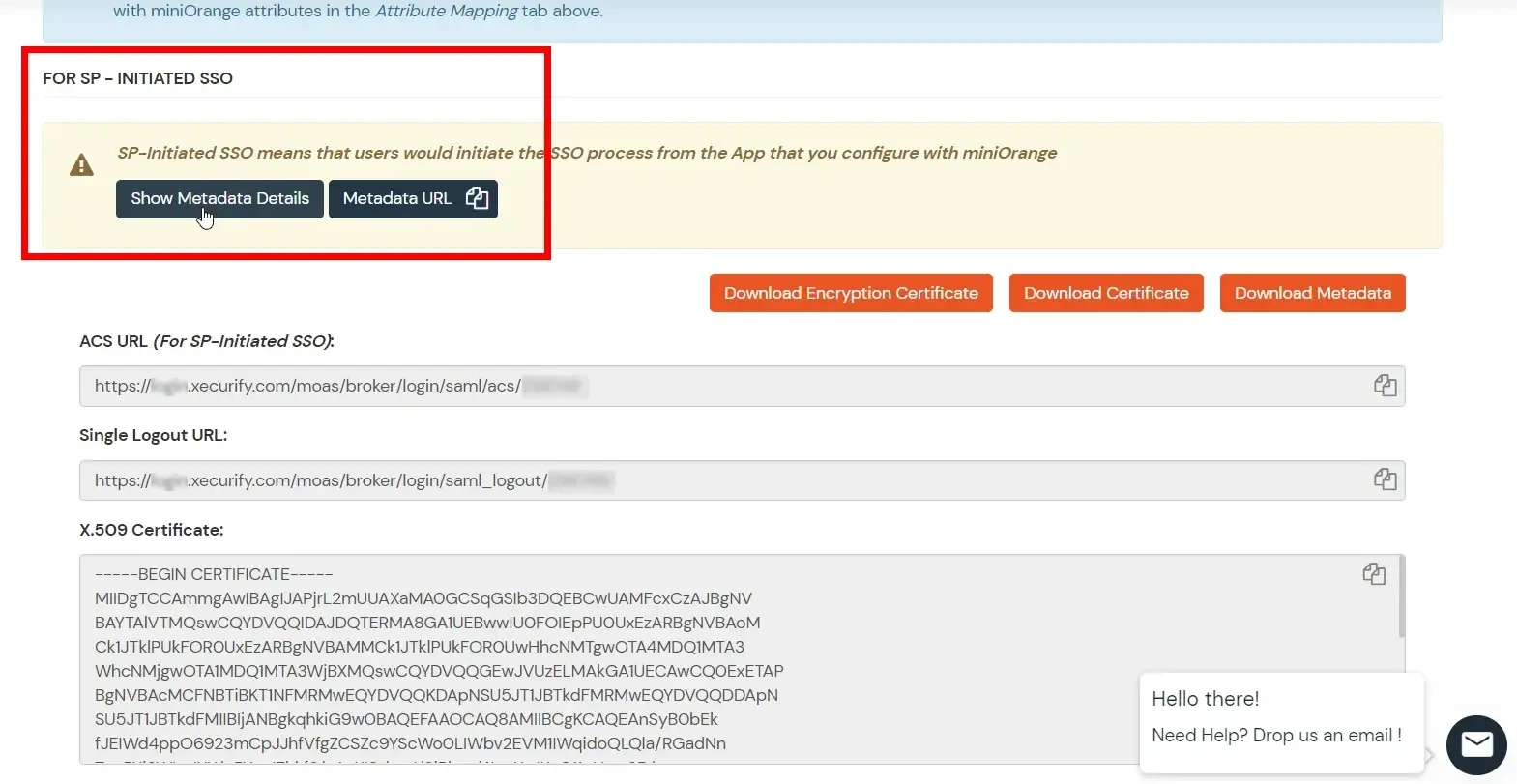
- Now, click on Show Metadata Details under FOR SP - INITIATED SSO heading. You can use the following metadata details to add an app inside your IDP.
Step 2: Connect Okta with miniOrange
Follow the steps below to configure Okta as an Identity Provider
a. Create an app inside Okta
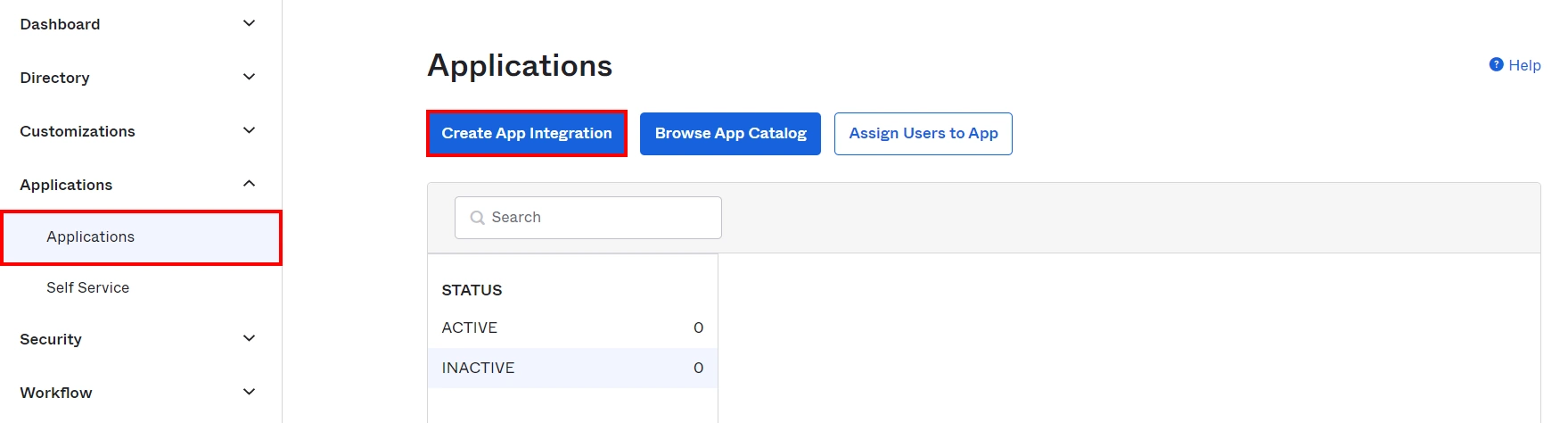
- Log into Okta Admin Console. For developer account, switch to Classic UI to configure app.
- Go to the Application from the left menu and then click on Create App Integration.
- Select SAML 2.0 as Sign on method.
- Click on Create.
- In General Settings, enter App Name and click on Next.
- In SAML Settings, enter the following:
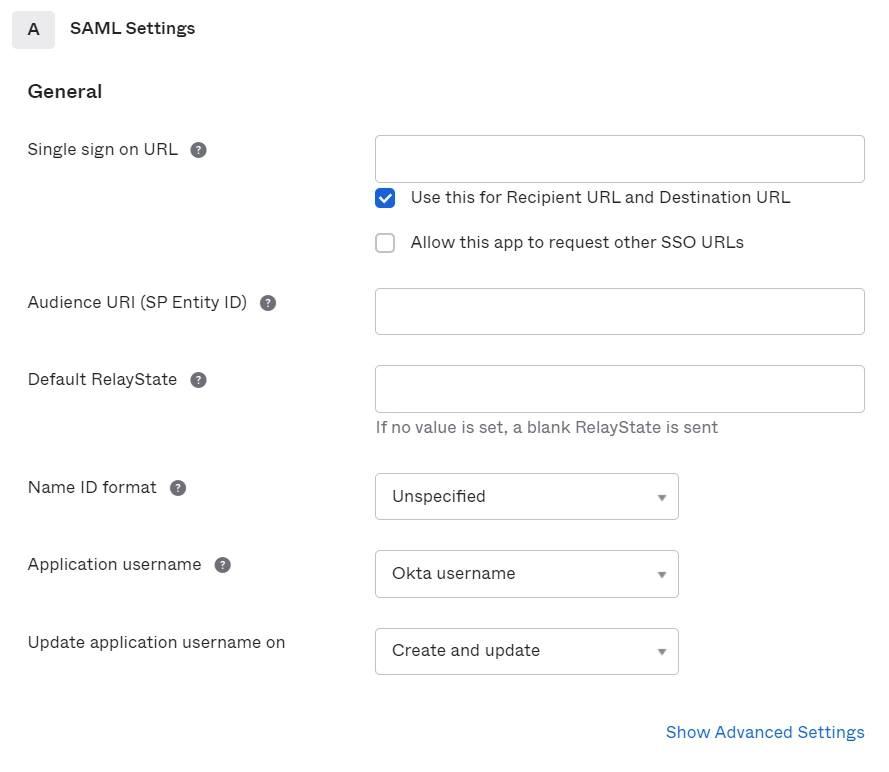
- Configure Attribute Statements and Group Attribute Statement (Optional).
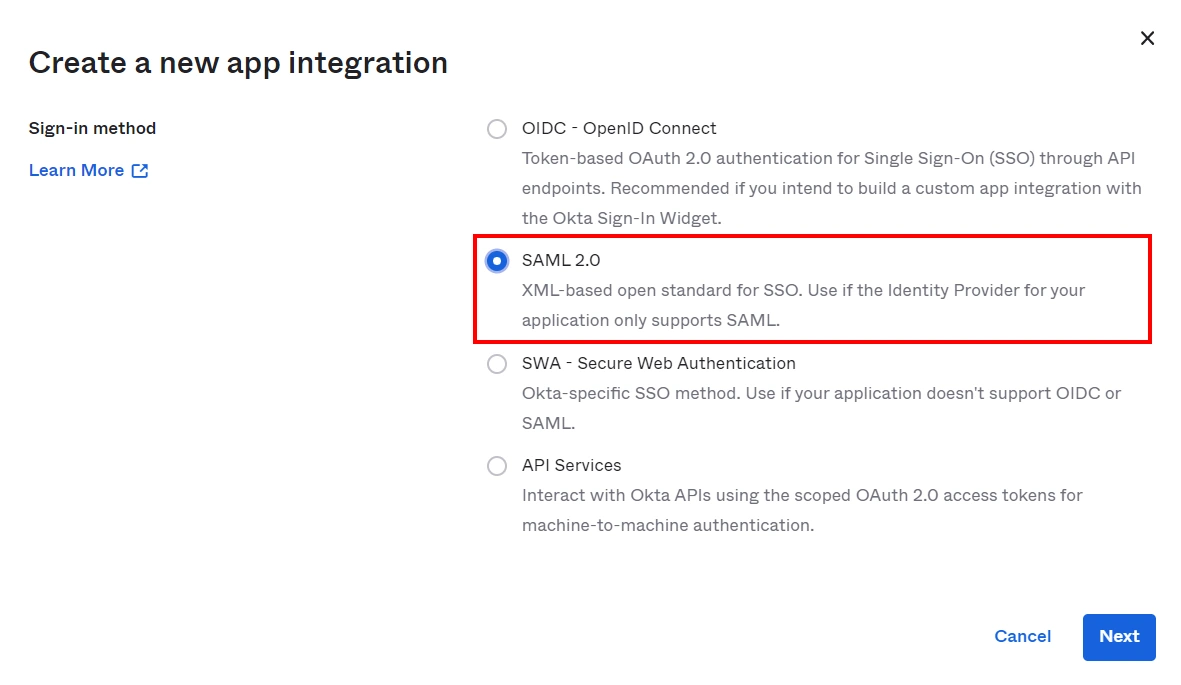
| Single Sign On URL | Enter ACS (AssertionConsumerService) URL from the Service Provider info tab of the module. |
| Audience URI (SP Entity ID) | Enter SP Entity ID / Issuer from the Service Provider info (or SP Information) tab of the module. |
| Default Relay State | Enter Relay State from the Service Provider info tab of the module. |
| Name ID Format | Select E-Mail Address as a Name Id from dropdown list. |
| Application Username | Okta username. |
- For Name, enter "firstName" and select user.firstName from the value dropdown.
- For Name, enter "lastName" and select user.lastName from the value dropdown.
- For Name, enter "Email" and select user.email from the value dropdown.
- For Name, enter "groups" and select Matches regex from the Filter dropdown and enter ".*"
 Assigning
Groups/People
Assigning
Groups/People
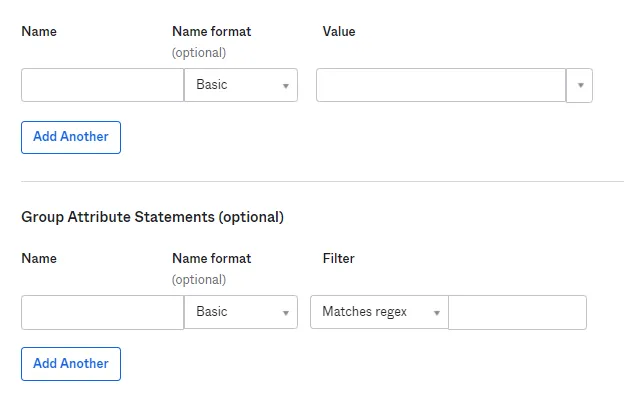
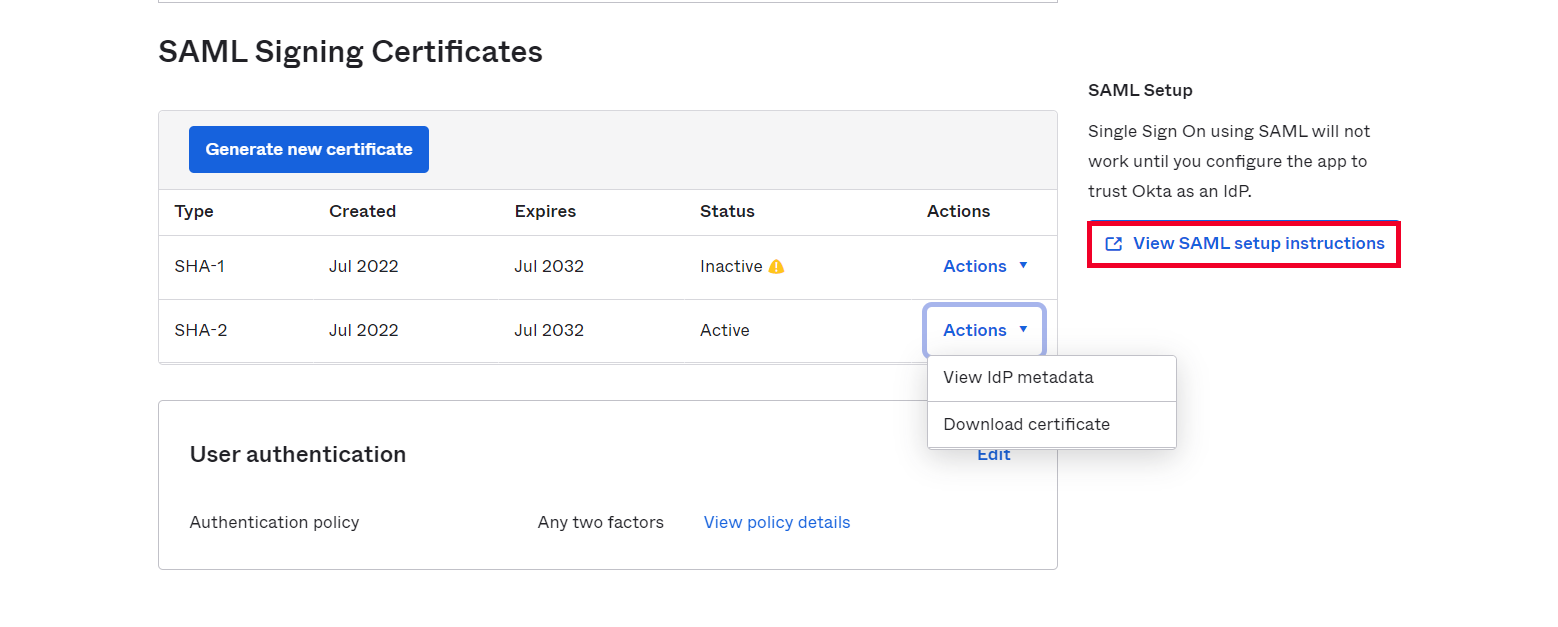
- After creating and configuring the app go to the Assignment Tab in Okta.
- Here we select the peoples and groups you want to give access to log in through this app. Assign this to the people/group you would to give access to.
- After assigning the people/groups to your app, go to Sign On tab.
- Click on View Setup Instructions to get the SAML Login URL (Single Sign on URL), Single Logout URL, IDP Entity ID and X.509 Certificate. You will need this to configure the Service Provider.
b. Add Okta as IDP in miniOrange
Step 3: Connect Azure AD with miniOrange
a. Create an app inside Azure AD
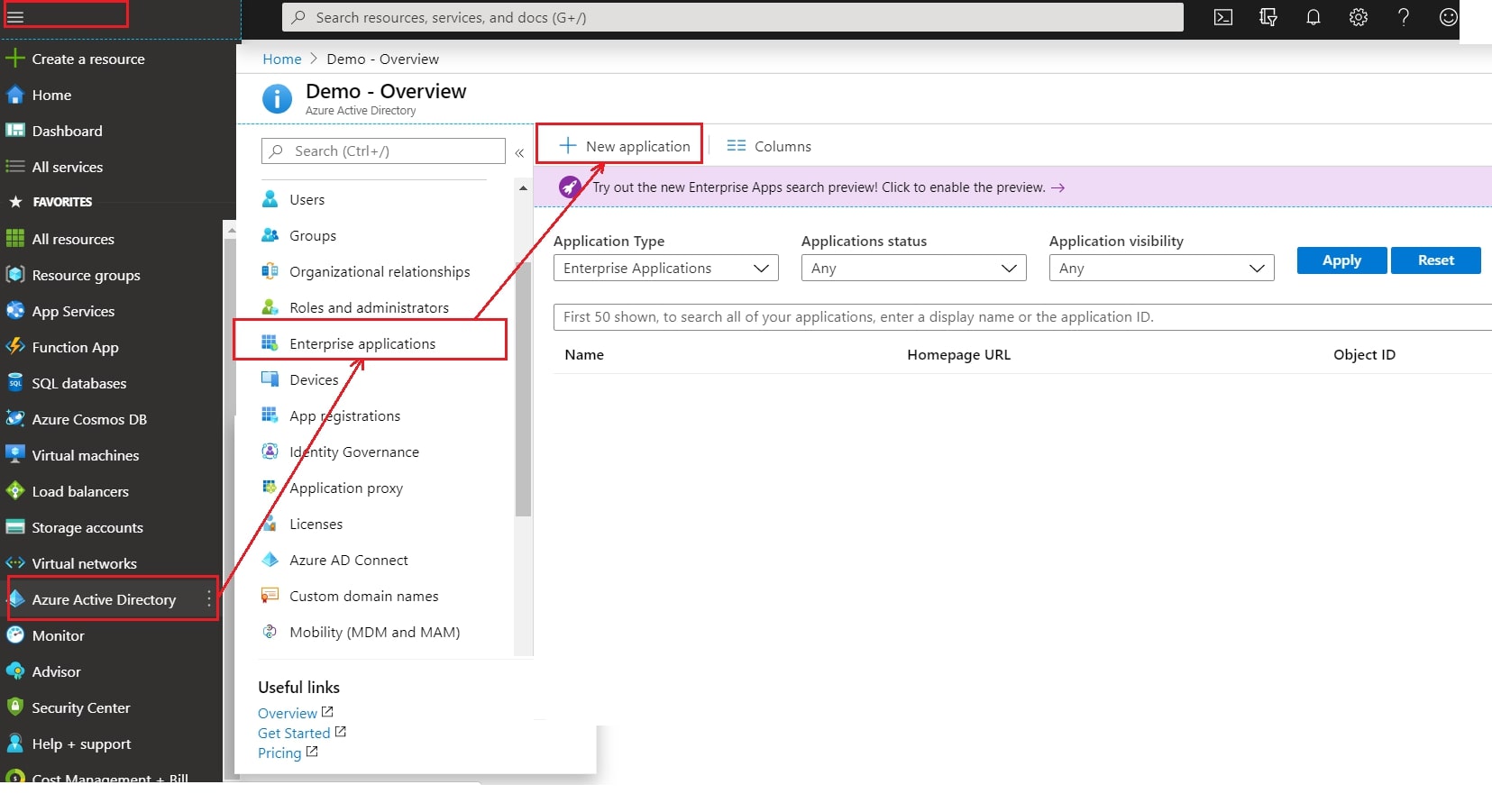
- Log in to Azure AD Portal
- Select ⇒ and Azure Active Directory ⇒ Enterprise Applications.
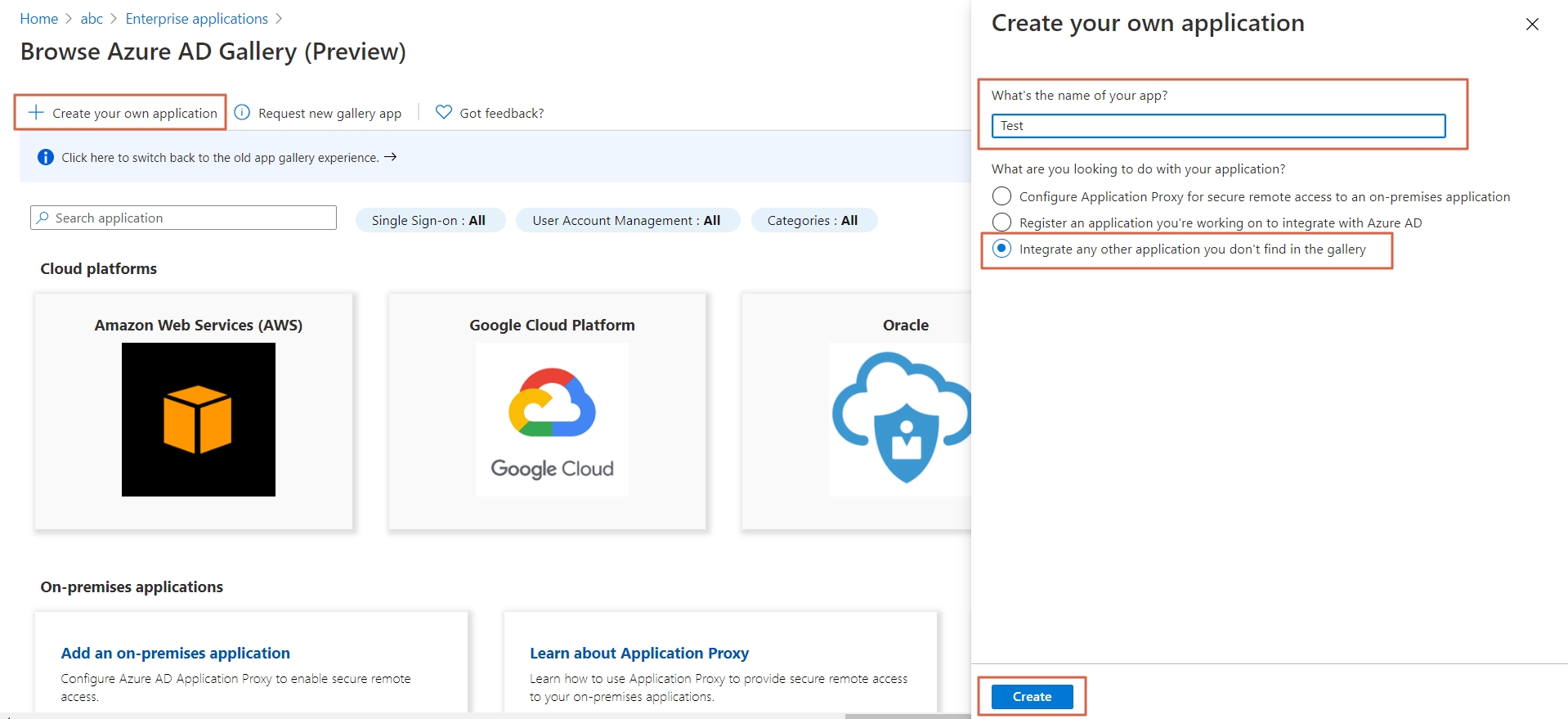
- Click on Create your own application. Then enter the name for your app, select the Integrate any other application you don't find in the gallery checkbox and click on Create button
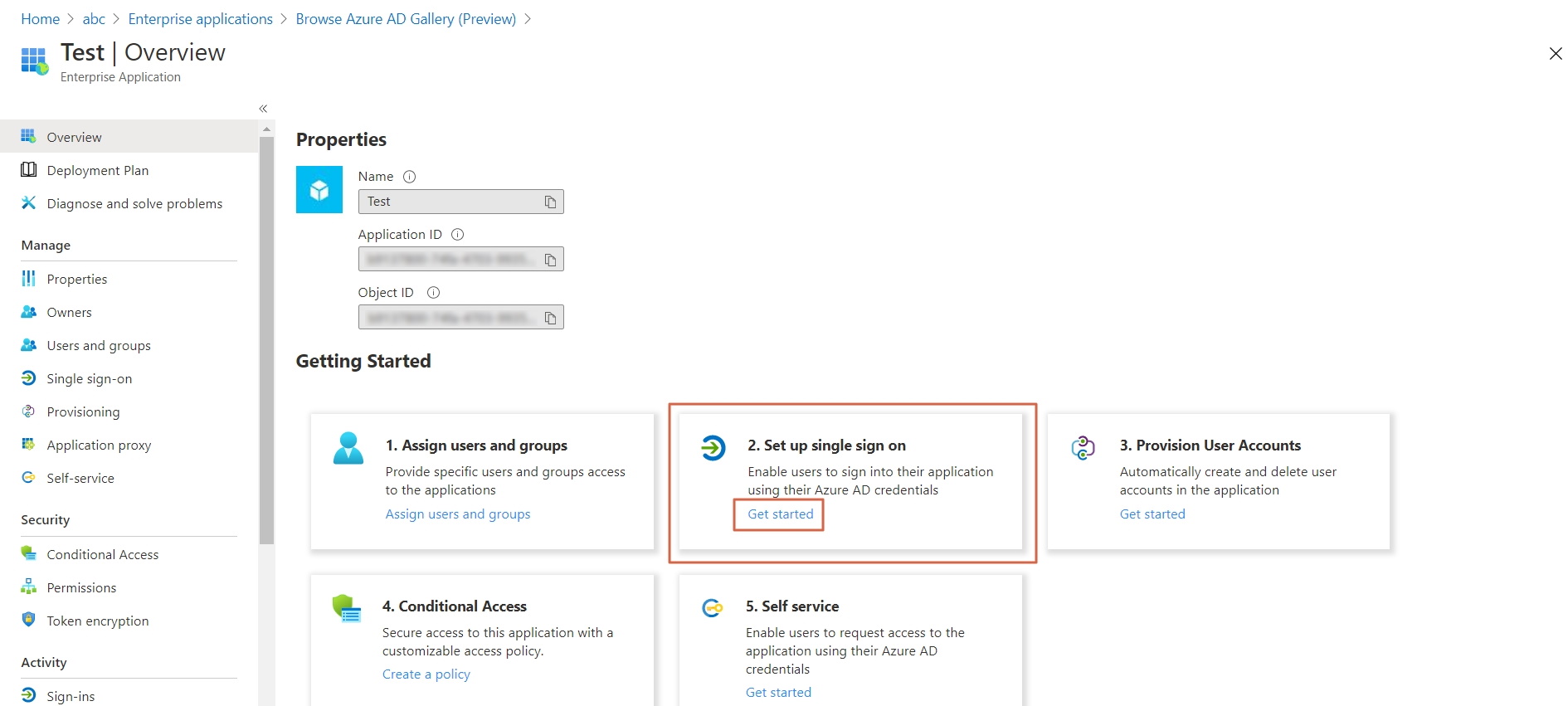
- Click on Set up Single sign-on.
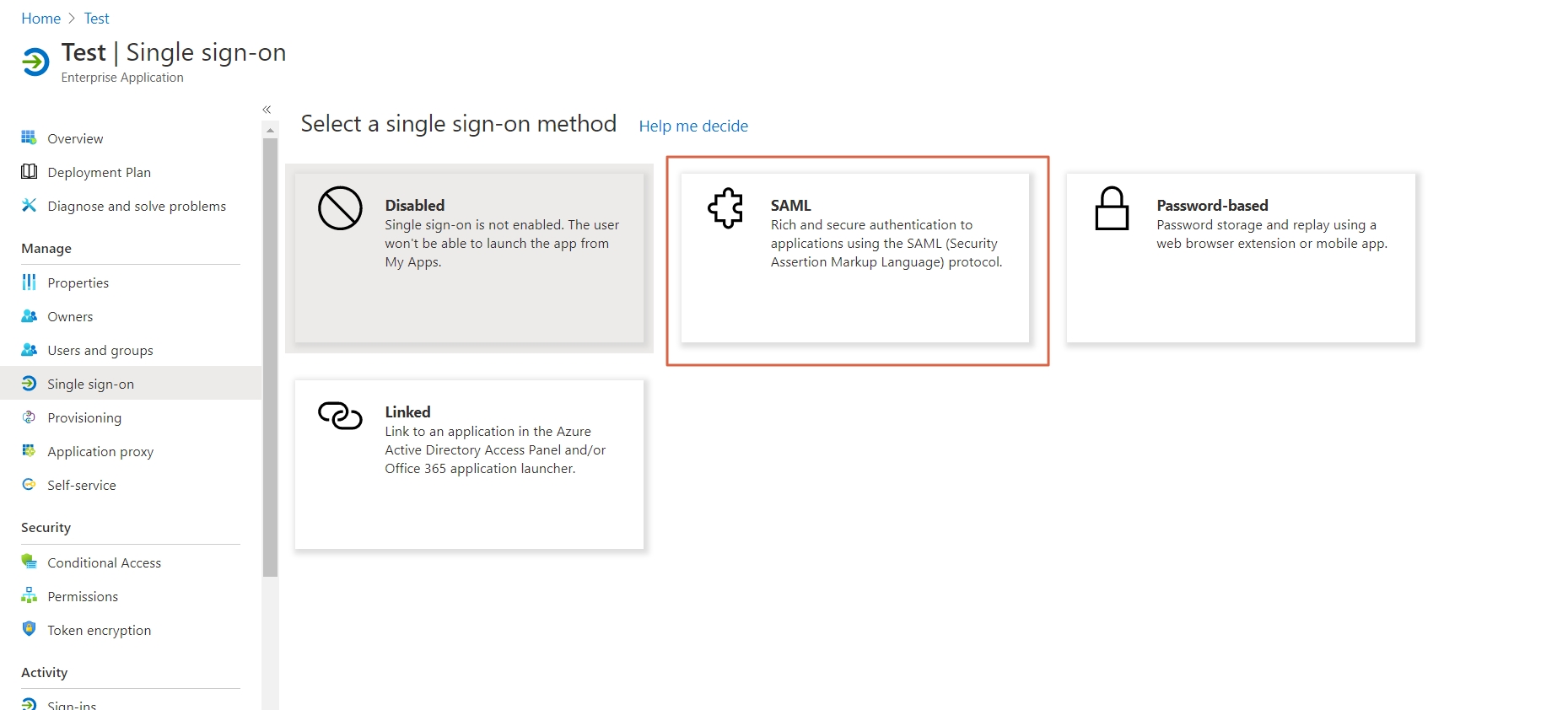
- The next screen presents the options for configuring single sign-on. Click on SAML.
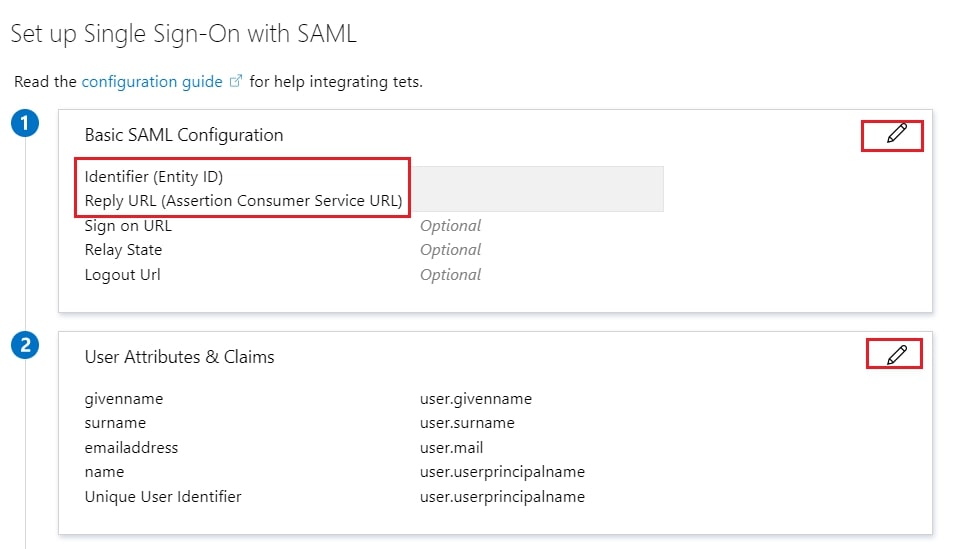
- Edit the option 1 :Basic SAML Configuration to configure plugin endpoints.
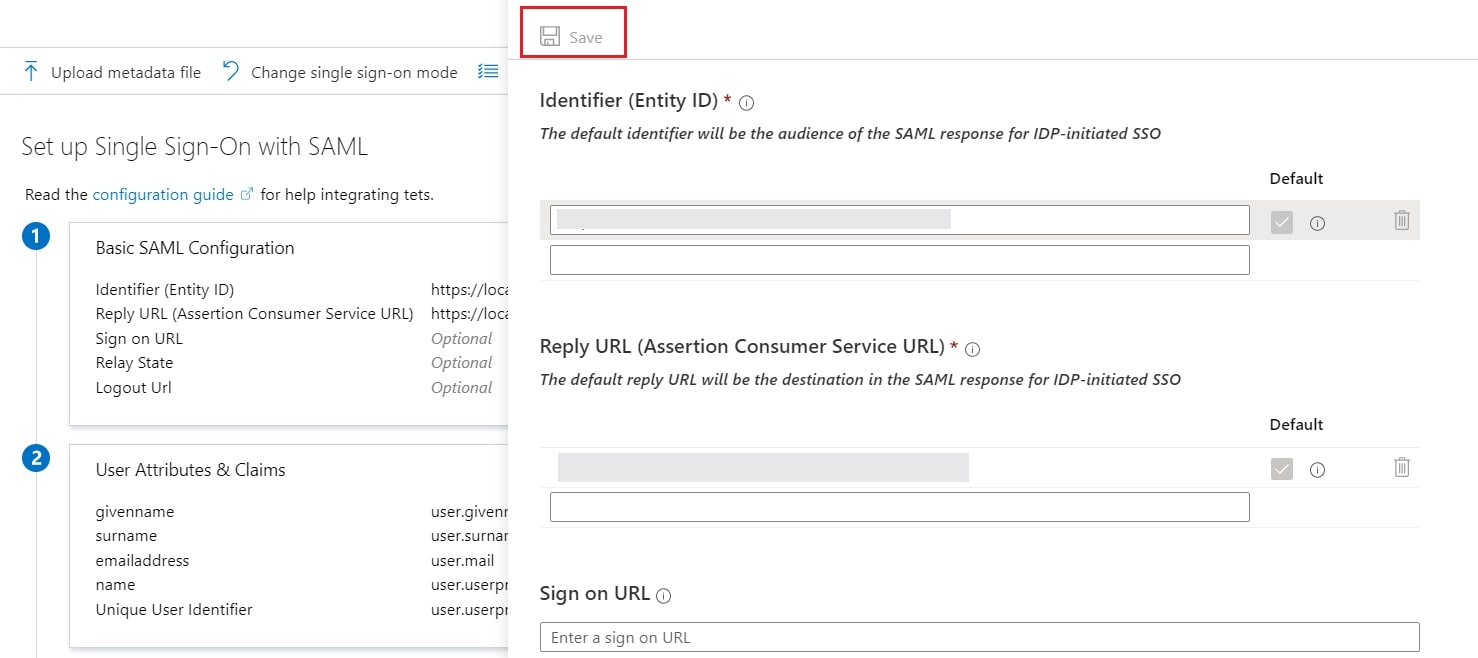
- Enter the SP Entity ID for Identifier and the ACS URL for Reply URL from Service Provider Info tab of the plugin.
- Click on Save icon.
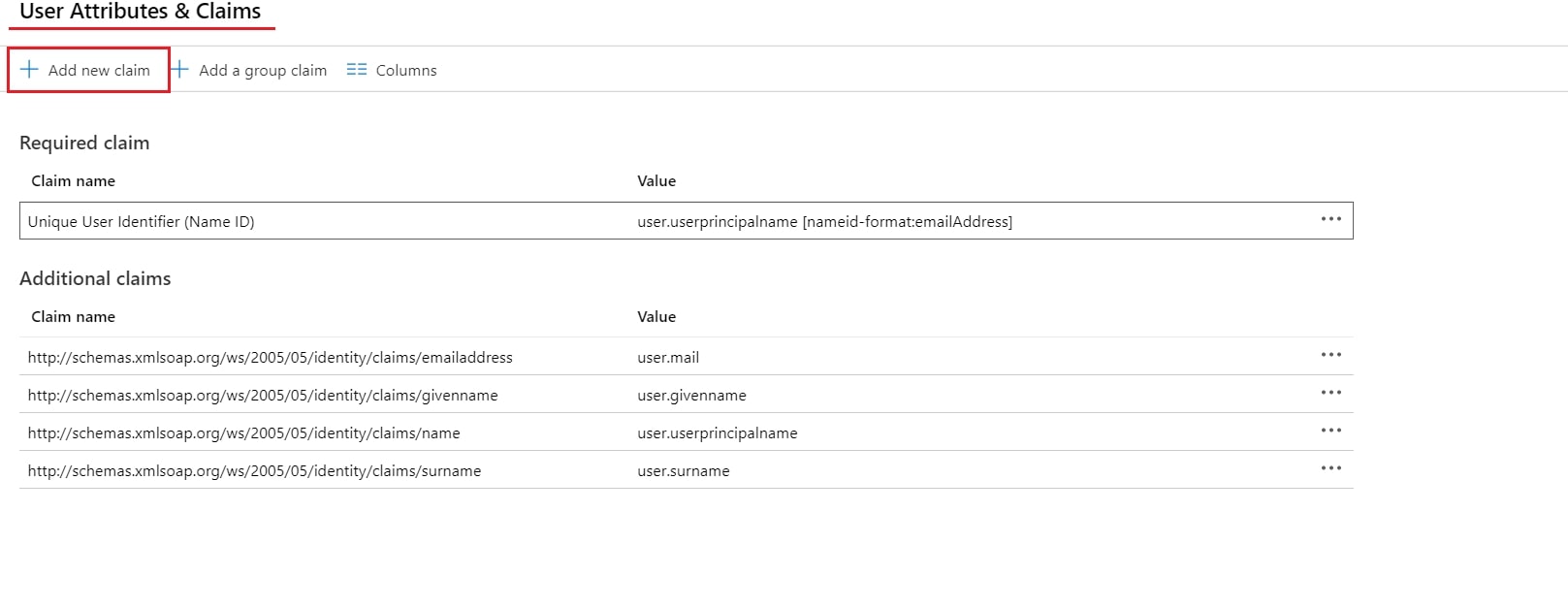
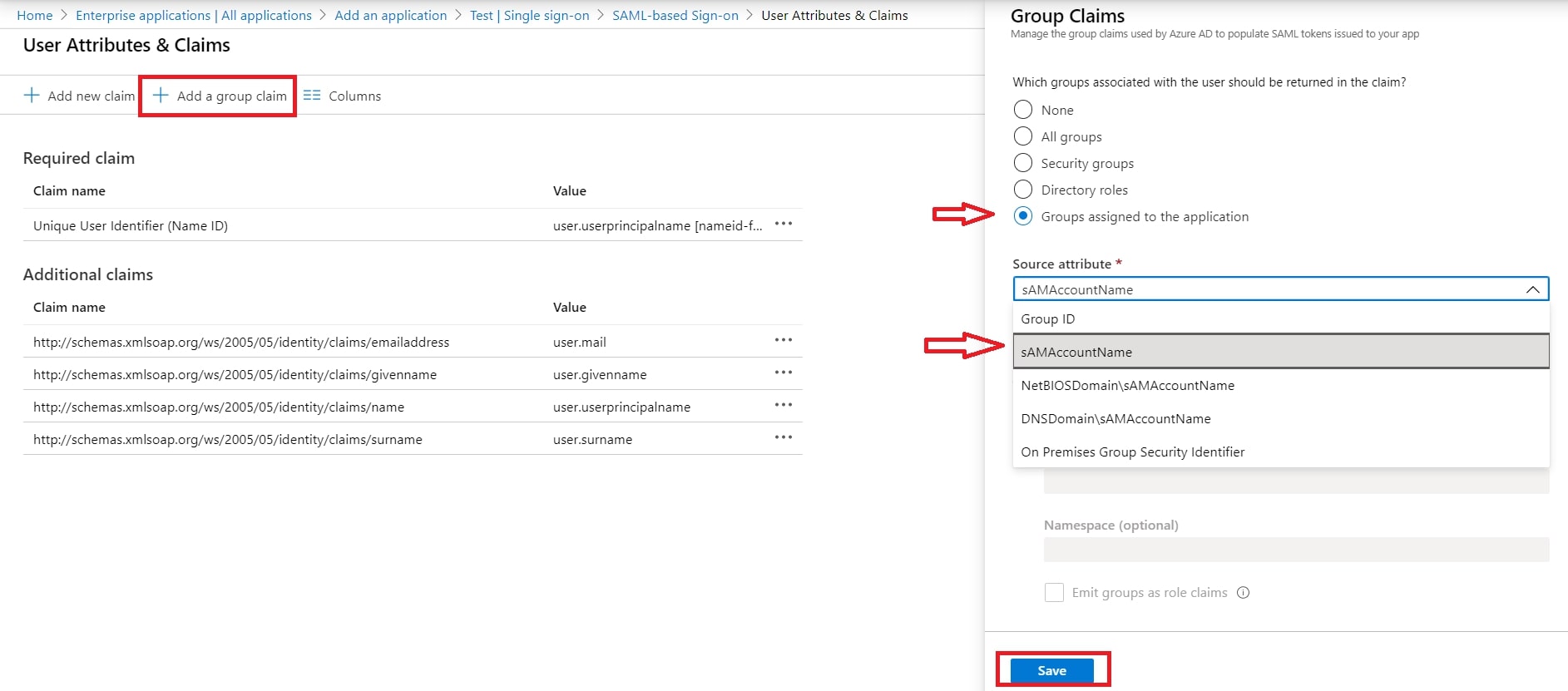
- By default, the following Attributes will be sent in the SAML token. You can view or edit the claims sent in the SAML token to the application under the User Attributes & Claims tab.
- You can add attribute using Add new claim
- You can add group attribute claim using Add a group claim
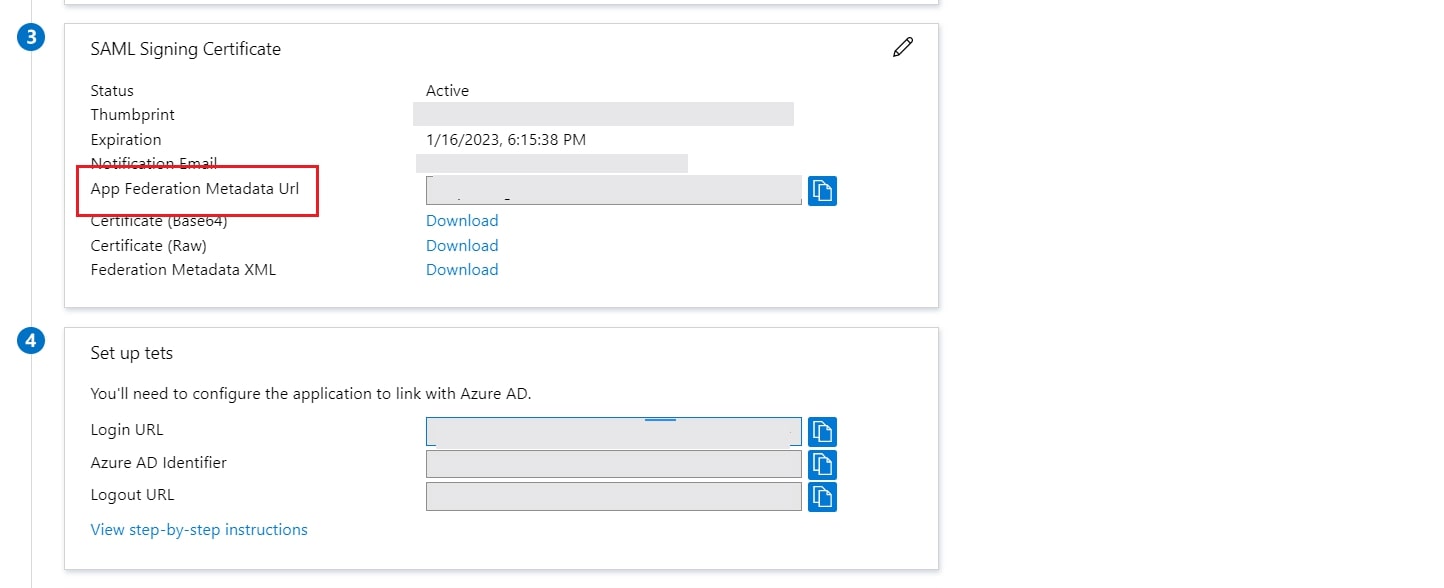
- Copy App Federation Metadata Url from setup tab.
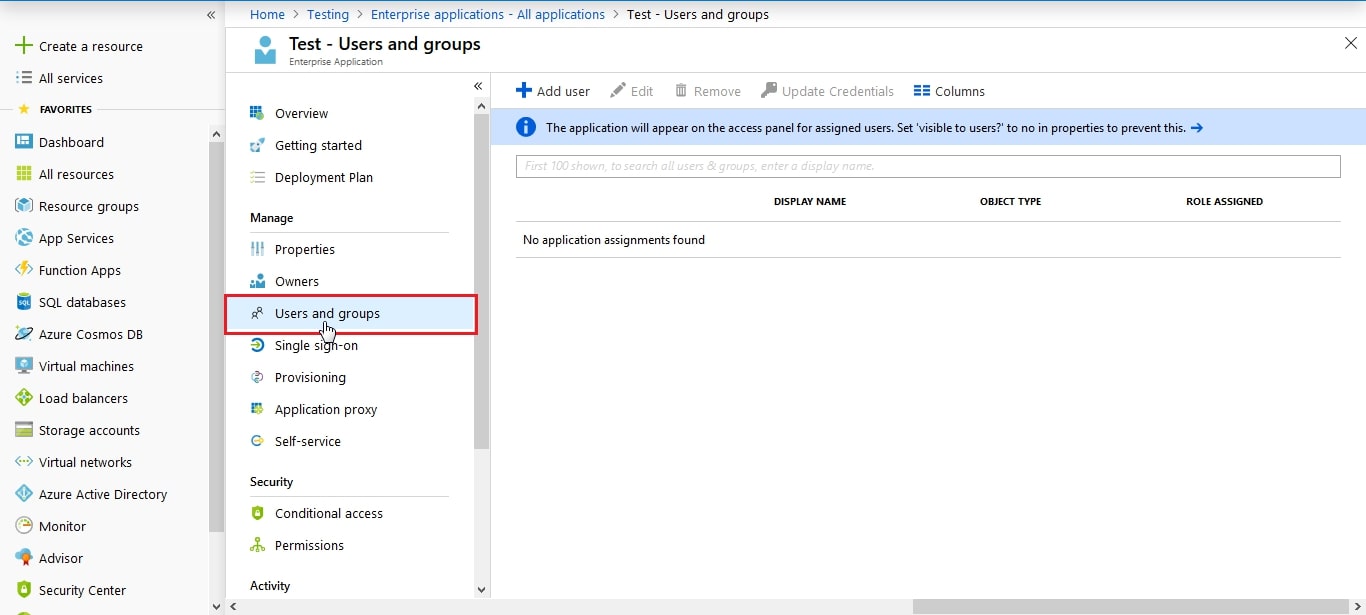
- Click on User and groups from the applications left-hand navigation menu. The next screen presents the options for assigning the users/groups to the application.
b. Add Azure AD as IDP in miniOrange
Step 4: Configure IDP inside miniOrange
- Login to miniOrange Admin Dashboard
- Go to Identity Providers and click on Add Identity Provider button from top right corner.
- Enter the following details and click on Save button.
- Click on Save button.

| IDP Name | Enter IDP name here. |
| IDP Entity ID | Enter IDP Entity ID / Issuer ID from the Identity Provider info. |
| SAML SSO Login URL | Enter Single Sign On url provided by Identity Provider. |
| X.509 Certificate | Enter the cetificate provided by Identity Provider. |
Step 5: Configure Helpdesk SSO with miniOrange
a. Get metadata from Helpdesk SSO
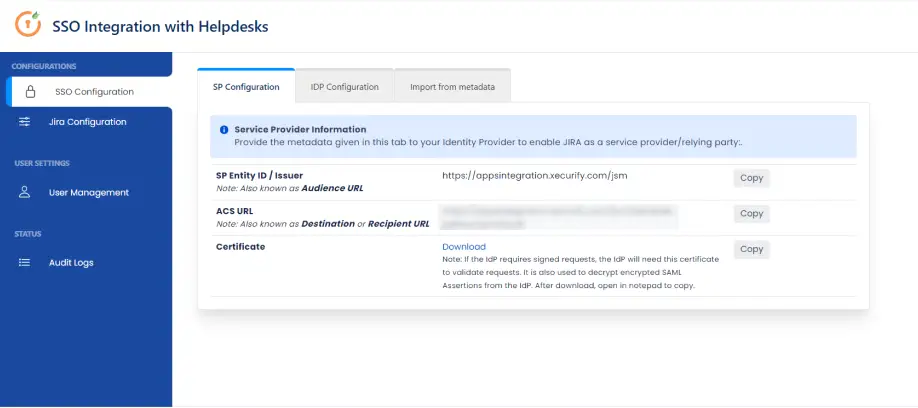
- In your Jira Cloud instance, click on the Apps drop-down menu and select SSO Integration with Helpdesk.
- Go to SP Configuration tab. Here you can access the metadata information to configure IDP.
b. Create an app inside miniOrange
- Login into miniOrange Admin Console.
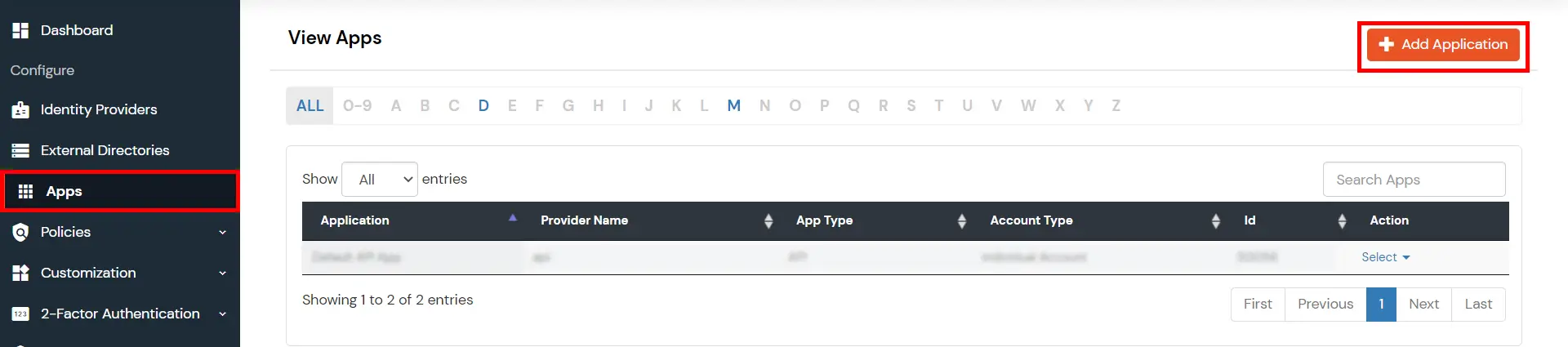
- Go to Apps and click on the Add Application button.
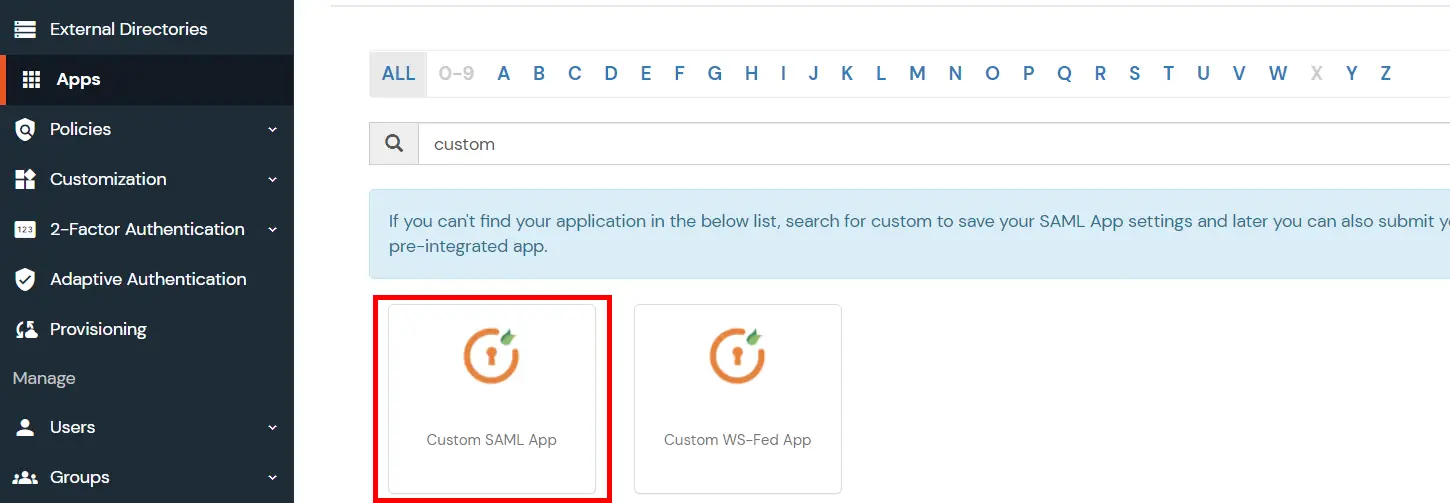
- Then click on SAML/WS-FED app.
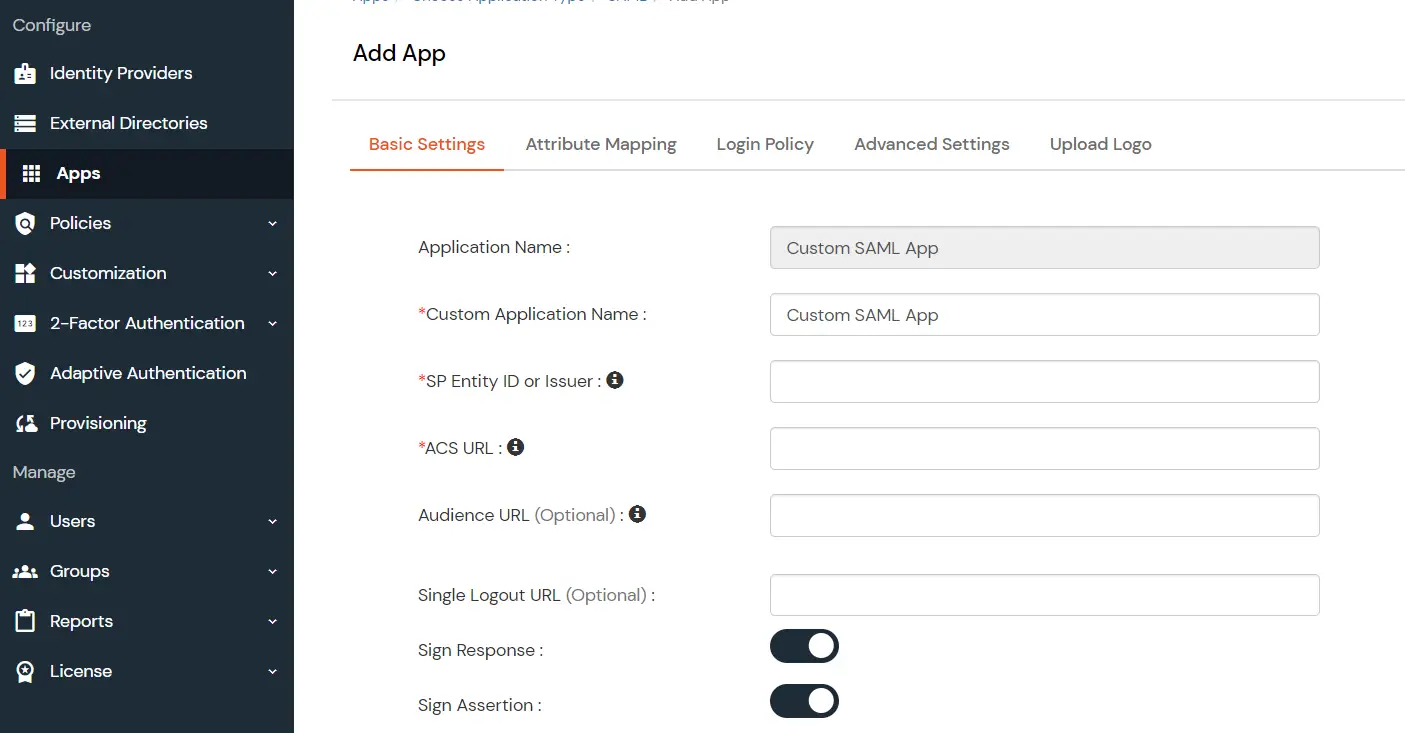
- Enter details copied from Helpdesk SSO add-on and click on Save.
c. Add miniOrange as IDP in Helpdesk SSO
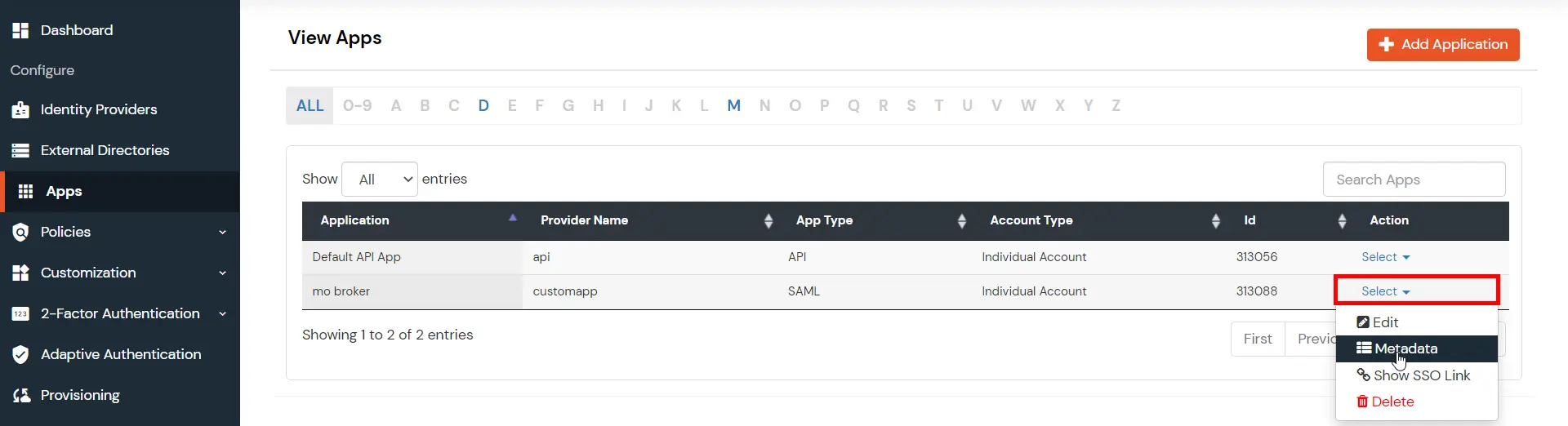
- In miniOrange Admin Dashboard, go to Apps from the left sidebar. Click on the Select dropdown next to your created app.
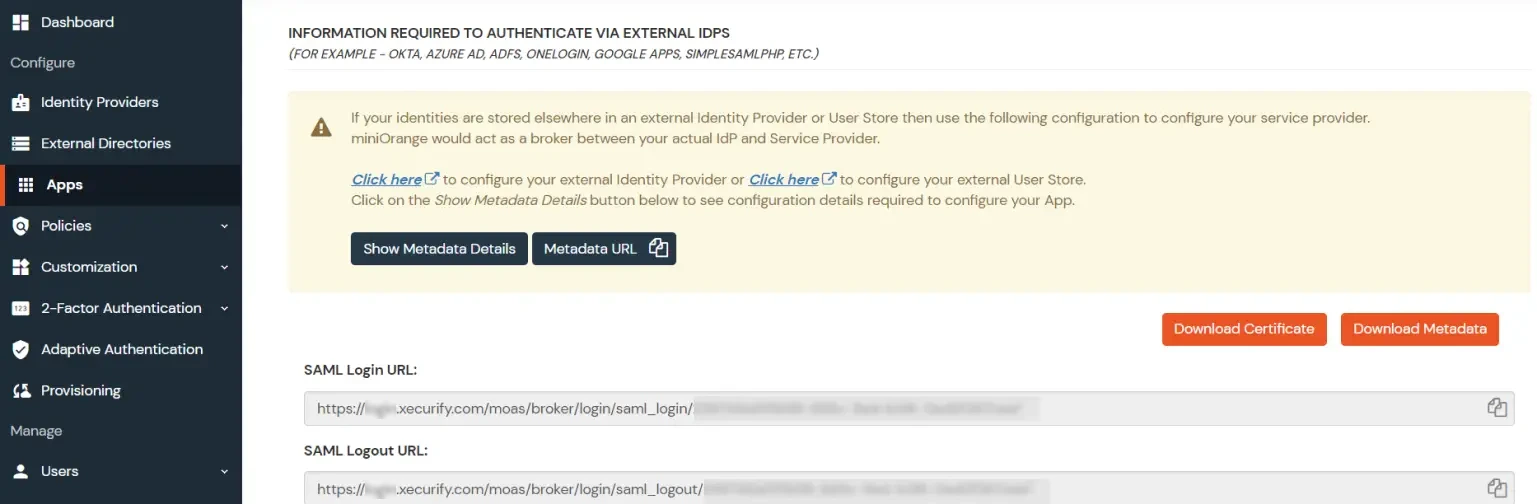
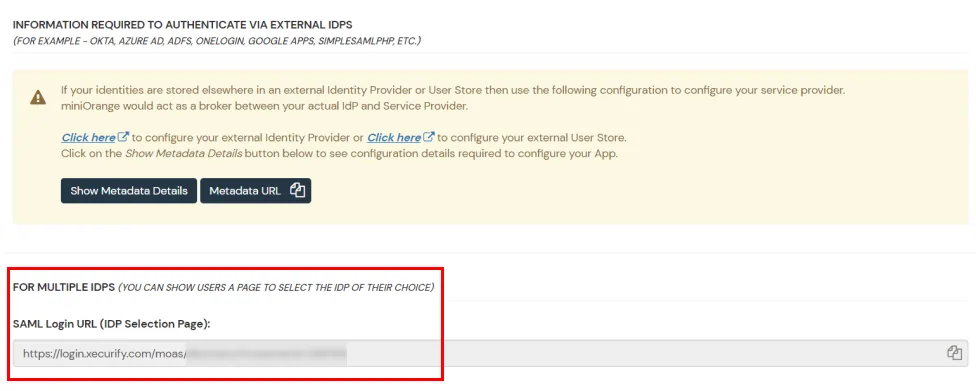
- Click on Show Metadata Details under the section INFORMATION REQUIRED TO AUTHENTICATE VIA EXTERNAL IDPS. You will need these metadata details in order to configure Helpdesk SSO add-on.
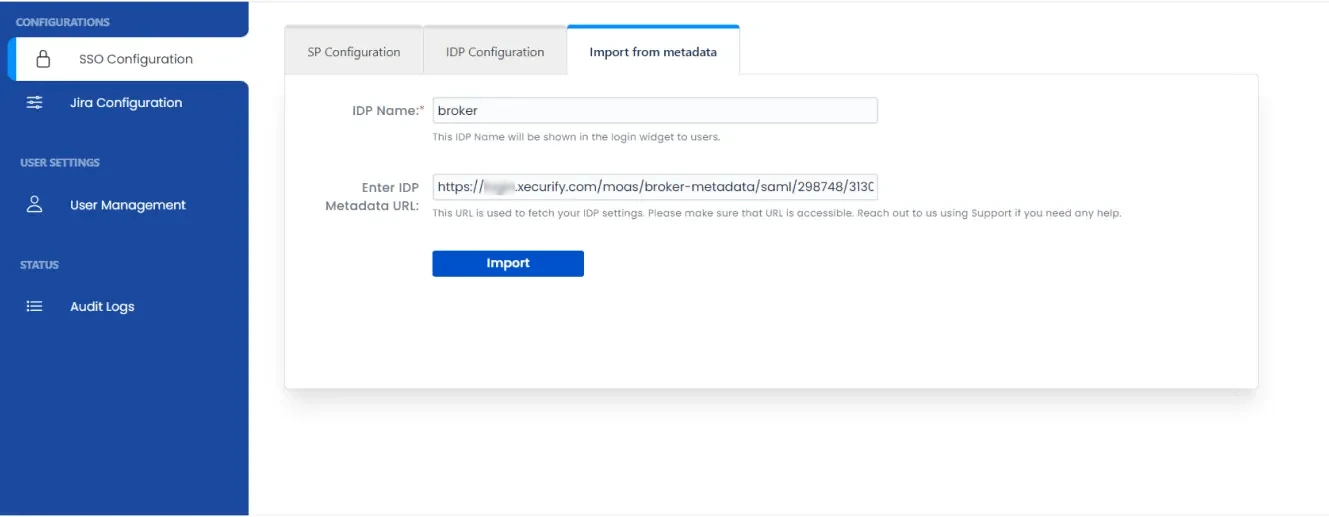
- Import metadata details or manually enter inside the helpdesk add-on.
- Access the App Metadata in miniOrange and copy the SAML Login URL.
- In the helpdesk add-on, click on the IDP Configuration tab, and then replace the Single Sign On URL with the SAML Login URL copied previously.
- click on Save button. You will be able to see below page while performing sso.

 Hi! Do you need help with this guide?
Hi! Do you need help with this guide?
Thank you for your response. We will get back to you soon.
Something went wrong. Please submit your query again

Recommended Add-Ons

Two Factor Authentication
Enable 2FA/MFA for users & groups and let users configure 2FA during their first login.
Know More
User Sync SCIM Provisioning
Synchronize users, groups & directory with SCIM & REST APIs for Server/DC.
Know More
API Token Authentication
Secure your JIRA Data Center/Server REST API using API Tokens.
Know MoreBitbucket Git Authentication App | Kerberos/NTLM Apps | Word/PDF Exporter | WebAuthn | SonarQube SSO | Jenkins SSO
If you don't find what you are looking for, please contact us at support-atlassian@miniorange.atlassian.net or raise a support ticket here.
