Contents
OpenID/OIDC Single Sign On (SSO) into JSM
Our SAML/OAuth SSO for JSM Customers app offers the functionality to seamlessly integrate OpenID/OIDC Single Sign-On into the JSM customer portal, ensuring compatibility with all OpenID/OIDC providers. This guide will outline the steps for configuring SSO between the JSM customer portal and your custom OpenID/OIDC provider. By following these instructions, customers will undergo authentication via your OpenID/OIDC provider prior to accessing the JSM customer portal. This integration facilitates a smooth customer experience while also mitigating spam ticket.
Download and Installation
- Log into your Jira instance as an admin.
- Navigate to the settings and click on Apps.
- Locate SAML/OAuth SSO for JSM Customers.
- Click on free trial to begin a new trial SAML/OAuth SSO for JSM Customers.
- On menu bar click on Apps. Locate SAML/OAuth SSO for JSM Customers .
Step 1: Setup your OIDC/OpenID provider
- Register an OpenID/OIDC application on your provider by configuring the Callback URL provided in the plugin. The callback URL would be {oauth_client_base_url}/jsm/oauth2/callback
- Collect the endpoints given below from your provider to configure them in the plugin.
| Endpoints | Use |
|---|---|
| Client ID | Identify the application. |
| Client Secret | Authenticate the Authorization Server. |
| Scope | Limit an application's access to a user's account. |
| Authorization Endpoint | Identify a user or obtain an authorization code. |
| Access Token Endpoint | Allows an application to access an API. |
| Logout Endpoint (optional) | Enter the Logout endpoint of your OpenID/OIDC provider. Leave it blank if Logout endpoint is not supported by provider. |
Step 2: Setup JSM as OpenID/OIDC Client
- Go to the Manage Apps -> click Getting started under SSO Integration with Helpdesk then click on the Add New Identity Provider.
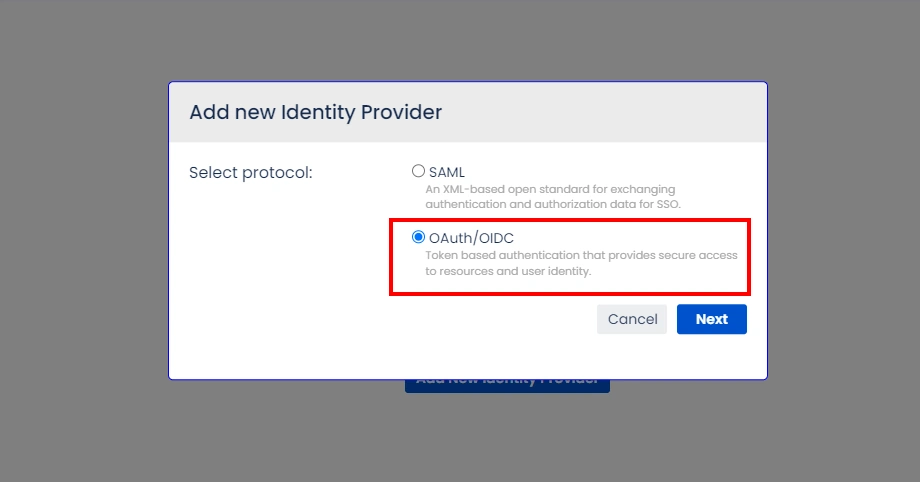
- Select OAuth/OIDC and click on the Next button.
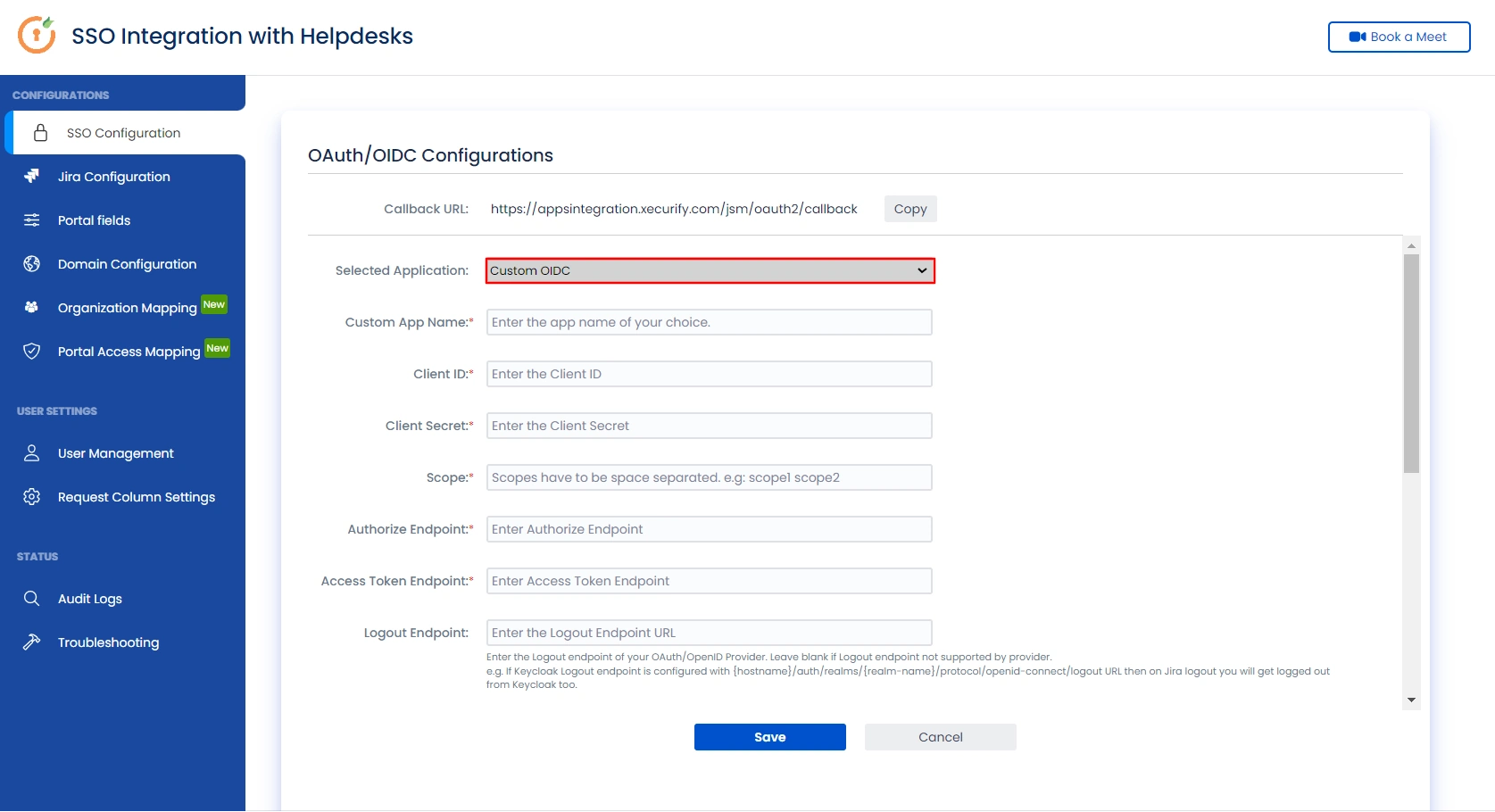
- Select Custom OIDC from the Selected Application dropdown menu.
- Enter Client ID, Client Secret, Endpoints, and Scope as openid.
- Click on Save button and then Test Connection for verifying the entered details.
Step 3: User Attribute Mapping
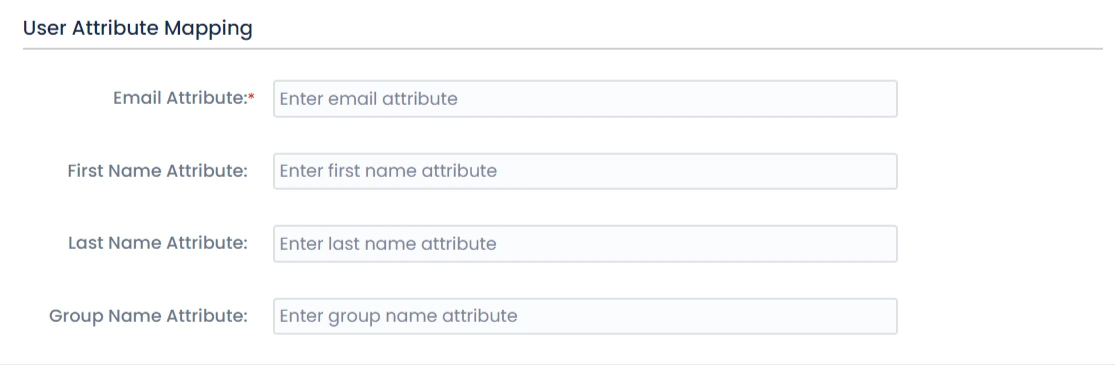
- Once you see all the values in Test Connection, go to User Attribute Mapping. Map attributes like Email, first name, last name, etc. Click on Save.
Step 4: Integrate Atlassian HelpDesk with JSM SSO
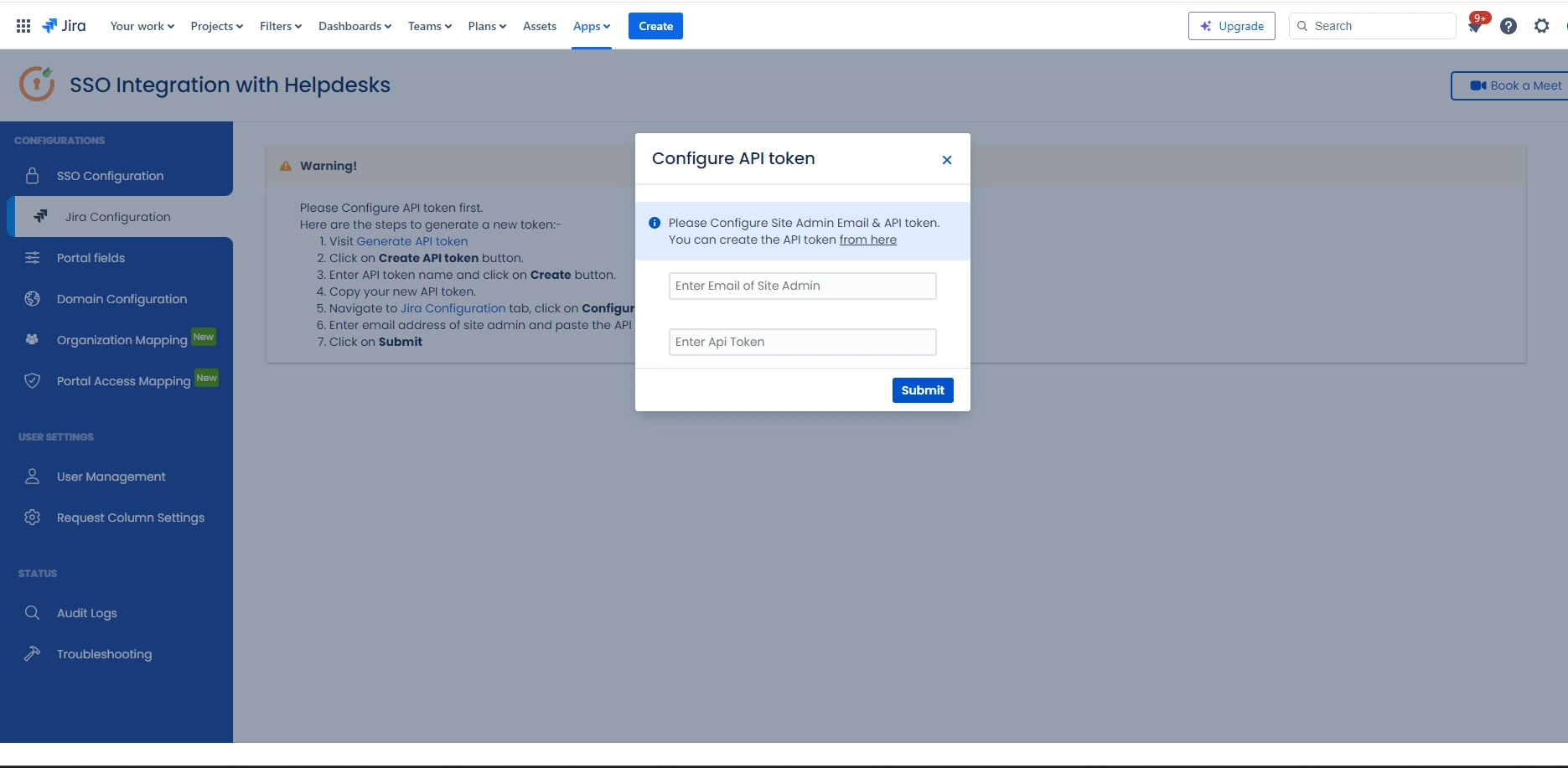
- Navigate to the Jira Configuration tab. Click on the Configure API Token and configure the Service Account API token with the email.
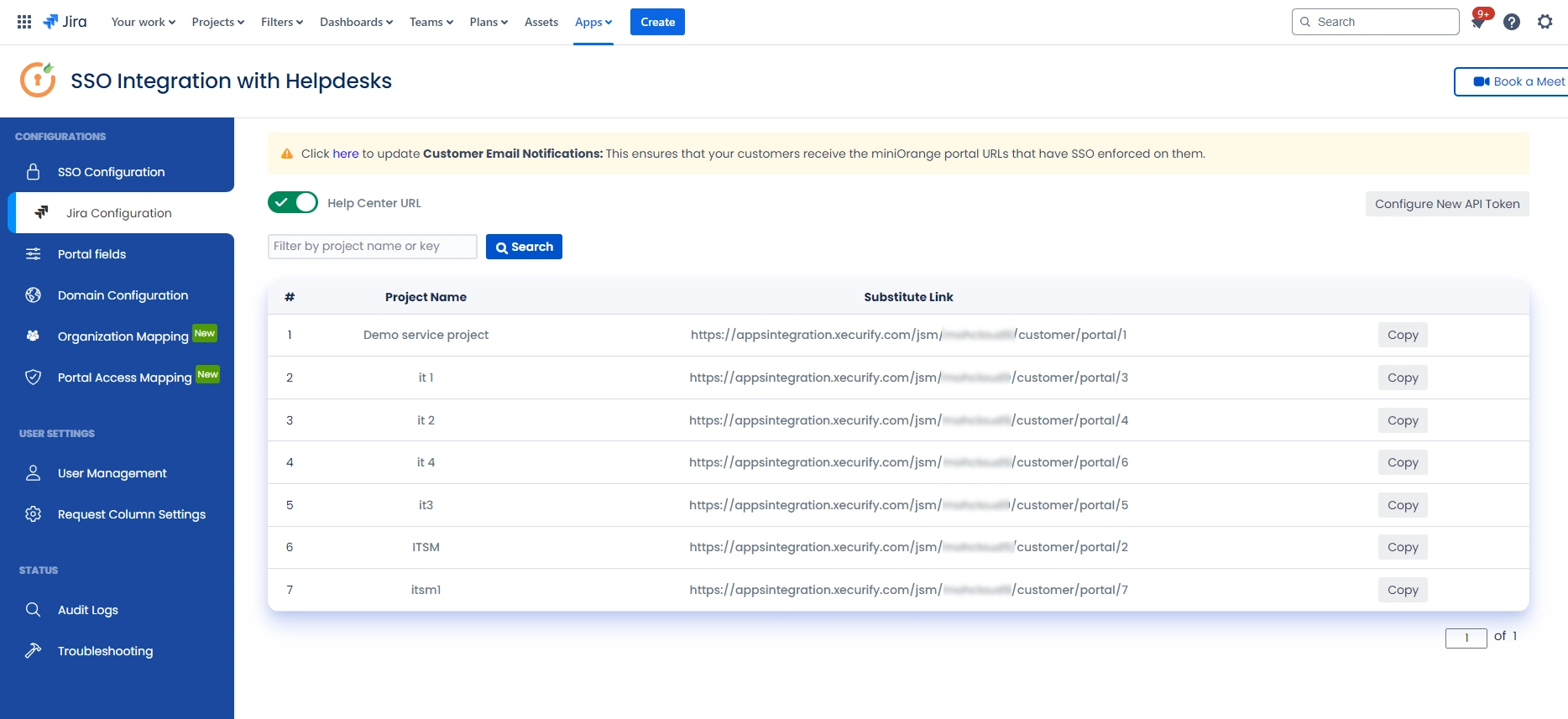
- After successful configuration of API token all the service desk projects with respective links will be displayed. These substitute links will be used by customers for accessing particular projects with SSO.
- Copy any of the substitute links you see for your portals and try accessing it in a private browser window. You would be automatically redirected to your Identity Provider for authentication and would be allowed access to the portal only after successful authentication.
Recommended Add-Ons

Two Factor Authentication
Enable 2FA/MFA for users & groups and let users configure 2FA during their first login.
Know More
User Sync SCIM Provisioning
Synchronize users, groups & directory with SCIM & REST APIs for Server/DC.
Know More
API Token Authentication
Secure your JIRA Data Center/Server REST API using API Tokens.
Know MoreAdditional Resources
Bitbucket Git Authentication App | Kerberos/NTLM Apps | Word/PDF Exporter | WebAuthn | SonarQube SSO | Jenkins SSO
If you don't find what you are looking for, please contact us at support-atlassian@miniorange.atlassian.net or raise a support ticket here.
