80% of breaches exploit privileged credentials, a statistic that should make every organization rethink its security strategy. In 2025, as cloud sprawl, AI-driven cyber threats, and hybrid workforces redefine the attack surface, relying on traditional PAM solutions with standing privileges is a ticking time bomb.
Here comes Zero Trust PAM (ZTPAM) , an advanced security model that verifies every user, enforces Just-in-Time (JIT) access, and continuously monitors privileged sessions. No one is inherently trusted, access is granted only when absolutely necessary, and every action is tracked to prevent privilege abuse before it happens.
This blog breaks down why Zero Trust PAM is essential, how it stops modern threats, and the step-by-step process to implement it. Because when it comes to securing privileged access, hesitation is no longer an option.
What Is Zero Trust? A Simple Guide
Zero Trust is a security model that enforces continuous verification of users and devices before granting access to enterprise resources. Unlike traditional perimeter-based security, where users inside the network are inherently trusted, Zero Trust Security follows the principle of "never trust, always verify", ensuring that every access request is authenticated and monitored.
In traditional security, once inside the network, an attacker can move laterally and access critical data. Zero Trust Architecture mitigates this risk by enforcing strict authentication, access controls, and real-time monitoring, regardless of the user’s location.
When comparing Zero Trust vs PAM, PAM (Privileged Access Management) controls privileged accounts, while Zero Trust enforces continuous authentication and monitoring for all users, including privileged ones. A Zero Trust PAM solution strengthens privileged access by minimizing standing privileges and enforcing just-in-time access, multi-factor authentication (MFA), and continuous monitoring to prevent unauthorized access and security breaches.
One of the key principles of Zero Trust PAM is the elimination of standing privileges, which refers to permanent, unrestricted access to privileged accounts. Zero standing privileges (ZSP) ensures that privileged access is granted only when needed and for a limited time. By using JIT access, users request temporary, purpose-based access, reducing the risk of credential misuse, insider threats, and privilege escalation attacks.
With Zero Standing Privileges, organizations can:
- Prevent attackers from exploiting dormant admin accounts.
- Reduce insider threats by ensuring access is granted only when necessary.
- Enforce stronger compliance by maintaining a strict access audit trail.
What is Privileged Access Management (PAM)?
Privileged Access Management (PAM) is a cybersecurity strategy designed to protect sensitive data and critical systems from unauthorized access. It leverages a combination of technology, processes, and people to monitor, control, and restrict privileged account access, ensuring that only authorized users can perform high-risk actions.
A PAM solution enforces strict access controls, session monitoring, and credential security to prevent privilege misuse and data breaches. By continuously verifying user identities and limiting privileged access to only what is necessary, PAM reduces the risk of cyber threats, insider attacks, and system-wide compromises.
The Role of PAM in Zero Trust
Privileged Access Management (PAM) is essential in a Zero Trust strategy, ensuring secure access to critical IT infrastructure. Without a Zero Trust PAM solution, enforcing strict access controls across privileged accounts remains incomplete.
PAM applies Zero Trust principles such as least privilege access, continuous monitoring, risk-based access control, and session management to regulate privileged account usage. By implementing Zero Trust PAM, organizations can enforce strict access policies, track privileged activity in real time, and reduce security risks associated with over-privileged accounts.
In a hybrid workforce, where access requirements constantly evolve, PAM Zero Trust ensures privileged access is granted based on continuous authentication, contextual risk assessment, and strict session controls, strengthening security across the enterprise.
Traditional PAM vs. Zero Trust PAM
| Feature | Traditional PAM | Zero Trust PAM |
|---|---|---|
| Access Control | Grants standing privileges, leading to potential misuse. | Implements Just-in-Time (JIT) access, revoking privileges after use. |
| Authentication | One-time authentication at login. | Enforces continuous authentication with risk-based policies. |
| Privileged Session Monitoring | Limited monitoring, primarily for logging. | Real-time monitoring, with session recording and instant termination. |
| Threat Detection | Reactive approach with manual reviews. | Automated risk analysis, identifying and blocking threats proactively. |
| Adaptive Security | Fixed access policies with minimal flexibility. | Uses adaptive MFA to dynamically enforce security based on user behavior and risk level. |
| User & Device Risk Assessment | Lacks continuous risk assessment for users and devices. | Continuously monitors user activity and device security posture to enforce access control. |
| Automation & Response | Requires manual intervention for access revocation. | Automates access revocation, session termination, and policy enforcement. |
| Third-Party Access Control | Provides basic access control for vendors and contractors. | Applies Zero Trust principles to third-party users, ensuring strict access governance. |
Why Zero Trust PAM Matters in 2025
As cyber threats become more sophisticated, traditional security models are no longer enough to protect privileged accounts. Zero Trust PAM enforces continuous authentication, least privilege access, and real-time monitoring, making it essential for organizations in 2025.
Real-World Risks Driving the Need for Zero Trust PAM
- Privileged Credential Theft: Attackers often target admin and service accounts to gain unauthorized access. Zero Trust PAM removes standing privileges, reducing the risk of exploitation.
- Insider Threats: Employees and contractors with excessive access can pose security risks. Just-in-Time (JIT) access ensures users only get temporary permissions when needed.
- Remote Access Vulnerabilities: In hybrid work environments, Zero Trust Remote PAM secures access from unmanaged devices using adaptive MFA and continuous verification.
- Compliance & Regulations: Organizations must meet security standards like ISO 27001, NIST, and GDPR. Zero Trust PAM automates audit logs and enforces strict access policies to ensure compliance.
- Advanced Persistent Threats (APTs): Cybercriminals use sophisticated tactics to maintain unauthorized access. Privileged session monitoring and risk-based authentication detect and block threats in real-time.
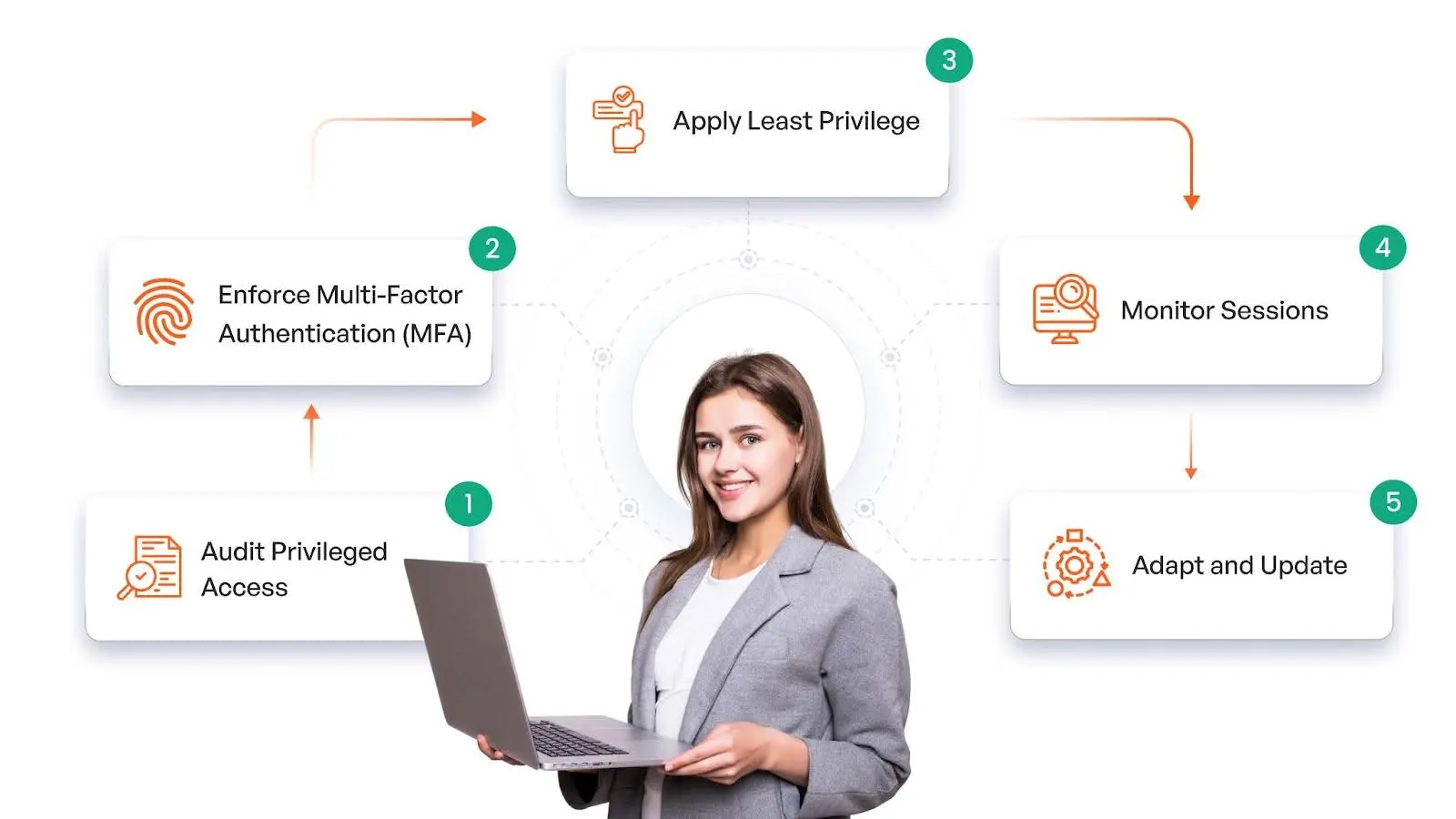
How to Implement Zero Trust PAM: 5 Practical Steps
Implementing Zero Trust PAM requires a structured approach to eliminate standing privileges, enforce strict access controls, and continuously monitor privileged activity. Here’s how organizations can adopt Zero Trust principles in PAM effectively:
- Audit Privileged Access: Identify and assess all privileged accounts, roles, and access levels. Remove excess privileges and ensure each user has only the minimum access required for their role.
- Enforce Multi-Factor Authentication (MFA): Secure privileged accounts by implementing adaptive MFA, requiring multiple verification layers before granting access. Adjust authentication methods based on user behavior and risk factors.
- Apply Least Privilege Access: Implement Just-in-Time (JIT) access to grant temporary, need-based privileged access instead of standing permissions. Define strict policies to prevent over privileged accounts.
- Monitor Privileged Sessions: Track all privileged activities in real time with session monitoring, recording, and automated alerts. Detect anomalies and unauthorized actions to prevent security breaches.
- Adapt & Continuously Improve: Regularly update access policies based on threat intelligence, user behavior, and compliance requirements. Ensure security measures evolve with emerging risks and attack patterns.
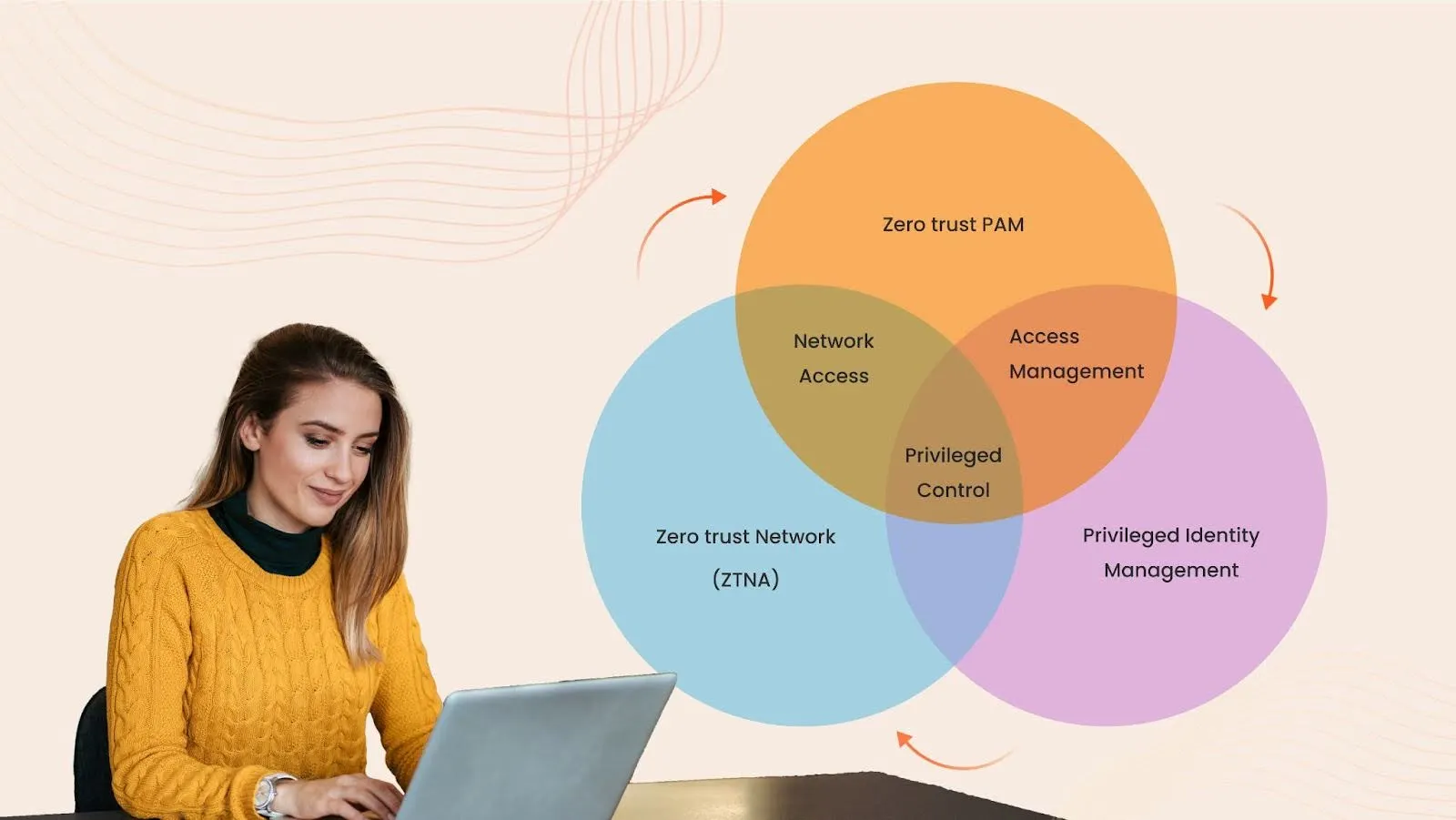
Zero Trust PAM vs. ZTNA vs. PIM: What’s the Difference?
| Category | Zero Trust PAM | ZTNA (Zero Trust Network Access) | PIM (Privileged Identity Management) |
|---|---|---|---|
| Focus | Manages privileged accounts with Zero Trust principles like Just-in-Time (JIT) access, session monitoring, and continuous authentication. | Enforces strict access controls across the entire network, verifying users and devices before granting access to any resource. | Controls individual identities and their access privileges, managing access dynamically based on user roles and risk assessment. |
| Scope | Limited to privileged users such as IT admins, executives, and service accounts. | Applies to all users and devices, requiring continuous identity verification before granting network access. | Manages all identities, including privileged accounts, focusing on context-aware, risk-based access control. |
| Primary Security Measure | Just-in-Time (JIT) access, MFA, and privileged session monitoring to prevent privilege abuse. | Device posture checks, adaptive authentication, and network segmentation to limit lateral movement. | Granular access control and lifecycle management for user identities, reducing excessive privileges. |
| Application | Used for securing privileged credentials, admin access, and critical IT assets. | Ensures secure remote access to applications and data, even for non-privileged users. | Provides centralized identity management with automated access provisioning and revocation. |
Zero Trust PAM in Action: Stopping a 2025 Ransomware Attack
Ransomware attacks are becoming more sophisticated, often exploiting privileged access to spread laterally across enterprise networks. Zero Trust PAM (Privileged Access Management) plays a crucial role in preventing these attacks by enforcing strict access controls, continuous authentication, and real-time monitoring. Here’s how Zero Trust PAM makes a difference in stopping a ransomware attack.
Without Zero Trust PAM
- Standing Privileges: Admin accounts with permanent, unrestricted access allow attackers to move laterally and encrypt critical data once compromised.
- Weak Authentication: A single compromised password provides attackers access to privileged systems without additional verification.
- Limited Visibility: Organizations lack real-time monitoring, making it difficult to detect abnormal privileged activity before damage is done.
- Delayed Response: Manual security responses allow ransomware to spread rapidly, increasing downtime and data loss.
With Zero Trust PAM
- Zero Standing Privileges (ZSP): Just-in-Time (JIT) access ensures privileged accounts are only active when needed, reducing the attack surface.
- Adaptive MFA: Multi-Factor Authentication (MFA) dynamically adjusts authentication requirements based on user behavior, location, and device security posture. Session Monitoring & Threat Detection: Continuous tracking of privileged sessions allows immediate detection of suspicious behavior, triggering automated alerts and response actions.
- Automated Access Revocation: If a privileged session shows signs of compromise, Zero Trust PAM can automatically terminate access, preventing lateral movement.
Zero Trust PAM Tools: What to Look For
When selecting a Zero Trust PAM solution, organizations must ensure it includes key security and access control features to protect against modern threats.
1. MFA Integration
A robust Zero Trust PAM solution should enforce Multi-Factor Authentication (MFA) for all privileged access requests. This ensures that even if credentials are compromised, unauthorized access is blocked through additional verification layers like biometrics, OTPs, or hardware tokens.
2. Session Recording
Privileged access should be monitored and recorded in real-time to detect unauthorized activities and maintain an audit trail for compliance. Session recordings allow security teams to replay actions, investigate incidents, and prevent privilege abuse.
3. Behavior Analytics
Advanced behavioral analytics detect anomalies by continuously analyzing user activity, access patterns, and device posture. If unusual behavior is identified—such as an administrator logging in from an unrecognized location—the system can trigger risk-based authentication, restrict access, or terminate the session automatically.
4. Scalability
A Zero Trust PAM solution should seamlessly scale with growing IT environments, supporting hybrid cloud, multi-cloud, and on-premises infrastructures. It must integrate with existing identity providers (IdPs), ITSM platforms, and security tools to ensure a flexible and future-proof security posture.
Take Control of Privileged Access in 2025
As cyber threats evolve, privileged access remains a key target. Zero Trust PAM is essential for enforcing least privilege, eliminating standing privileges, and securing critical assets. With MFA, continuous monitoring, behavior analytics, and automated threat response, businesses can proactively block ransomware, insider threats, and credential misuse.
miniOrange Zero Trust PAM ensures secure, just-in-time privileged access, adaptive security, and real-time risk mitigation. With seamless integration and advanced automation, miniOrange helps organizations stay ahead of evolving threats while maintaining compliance and operational efficiency.




Leave a Comment