How to Set Up Access Governance Automation App for Jira with Entra ID (Azure AD)
Welcome to the setup guide for the Access Governance Automation app for Jira — your go-to solution for streamlining and automating access requests using Jira Service Management (JSM) and Microsoft Entra ID (formerly Azure AD).
This step-by-step guide will help you:
- Integrate Entra ID with the app
- Automate access approvals and provisioning
- Improve visibility, compliance, and control over access management
By the end of this guide, you’ll have a secure, rule-based workflow in place for handling access requests across your organization — directly from your Jira portal.
App Overview
The Access Governance Automation app for Jira is an advanced solution built on Jira Service Management (JSM) to simplify and automate access request workflows across your organization.
It supports integration with major enterprise platforms, including:
- Okta
- Entra ID (Azure AD)
- AWS
- Google Workspace
- Jira, Confluence, Bitbucket, and GitHub
Instead of relying on manual request and approval steps, the app enables:
- End users to submit access requests through the JSM portal.
- Automated routing of approval workflows based on predefined rules.
- Instant provisioning actions once approvals are complete.
By automating these processes, the Access Governance Automation app for Jira ensures secure, policy-driven, and audit-ready access management across your tech ecosystem.
Pre-requisites
Before you begin, make sure you have the following:
- Admin access to Jira Service Management (JSM): Required to configure workflows, custom fields, and automation rules.
- Admin access to Entra ID (Azure AD) portal: Needed to authorize integrations and manage access provisioning.
- Access Governance Automation app for Jira: Ensure the app is installed from the Atlassian Marketplace and properly licensed via miniOrange.
1: Register an App in Entra ID(Azure AD)
To begin the integration, register a new app in Microsoft Entra ID (formerly Azure AD):
- Log in to your Azure Portal.
- Navigate to Azure Active Directory → App registrations.
-
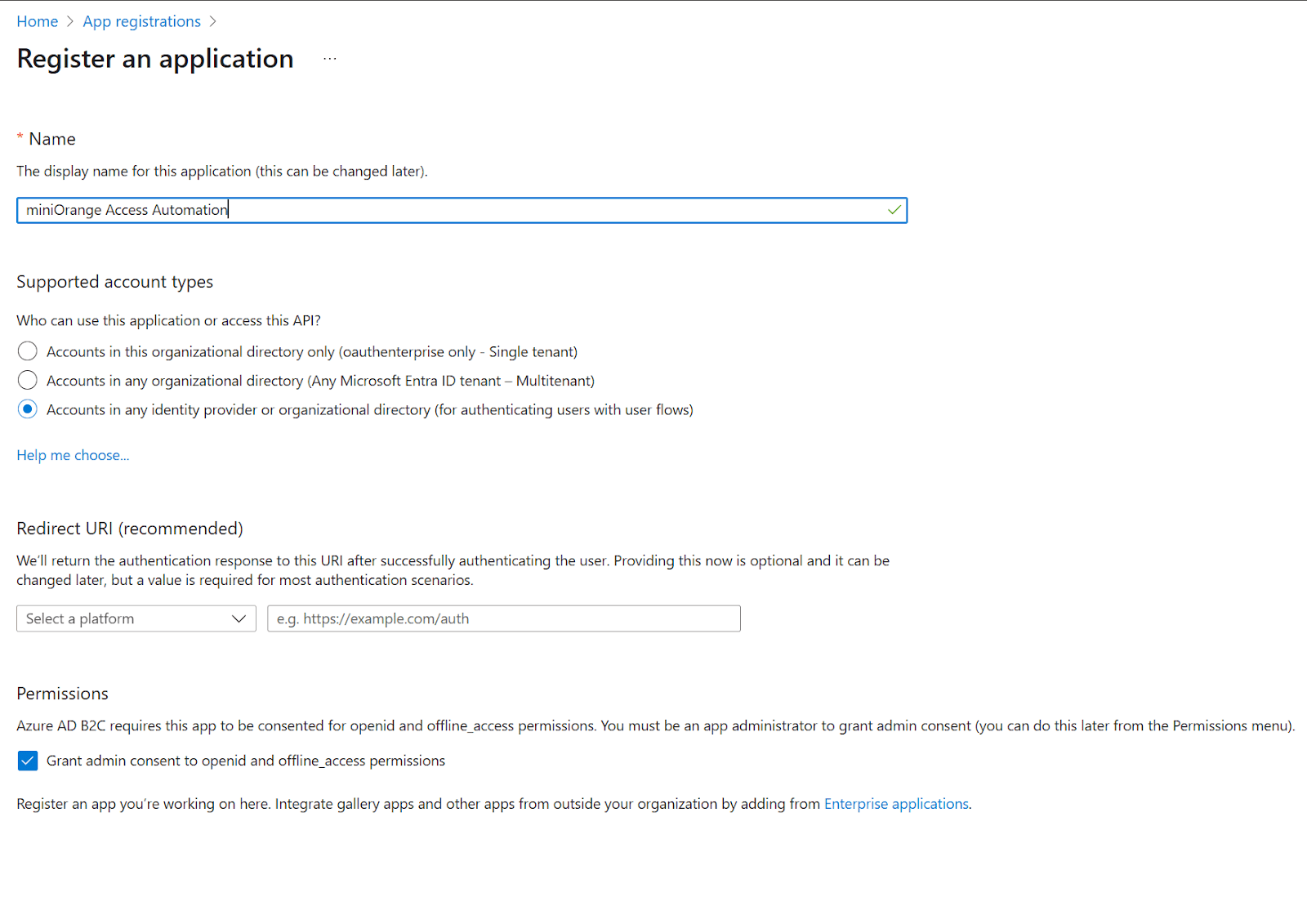
Click New Registration and fill the following details:
- Name: Provide Name for new application, for eg, miniOrange Access Automation App
- Redirect URL: Leave blank or enter dummy if required
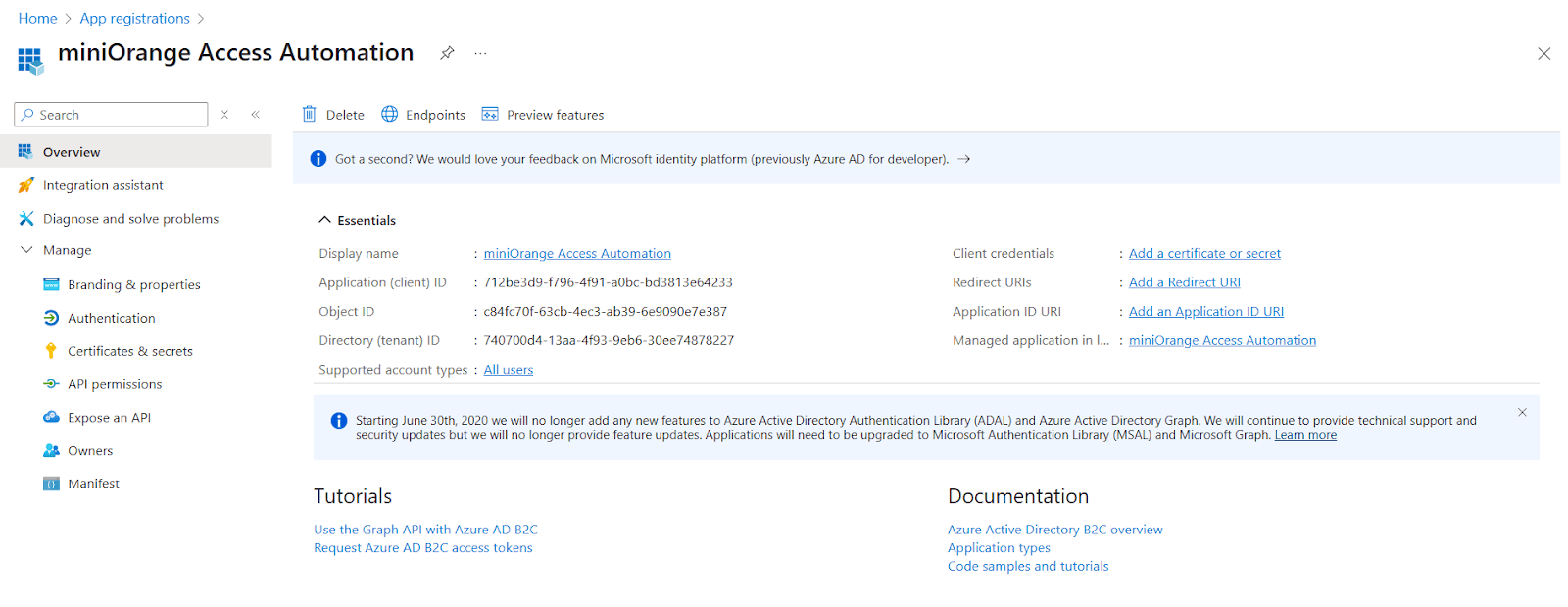
- After registration, go to the App Overview page and copy the Client ID and Tenant ID.
-
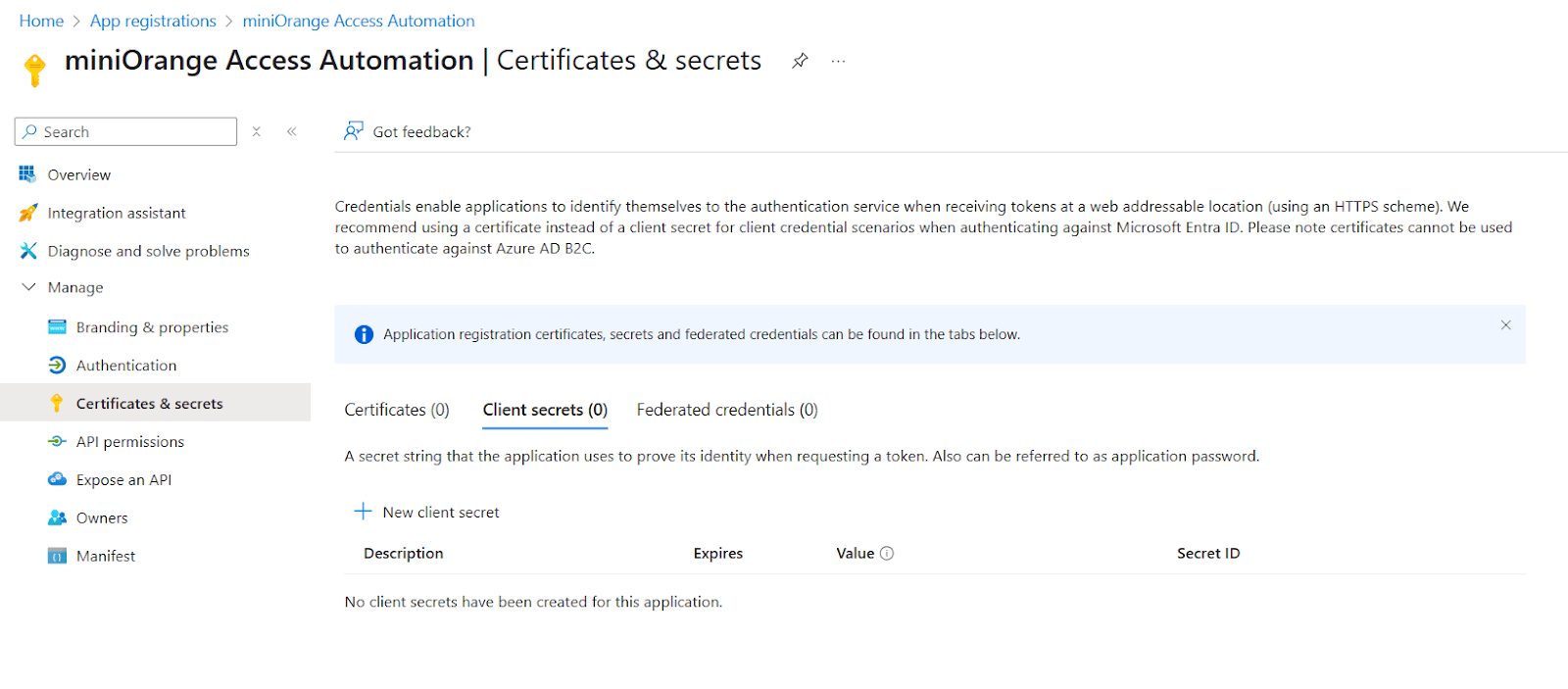
Under Certificates & Secrets → Client secrets, click
New client secret.
- Add a description and expiration period.
- Copy the secret value and keep it on your person (you won’t be able to view it again later).
-
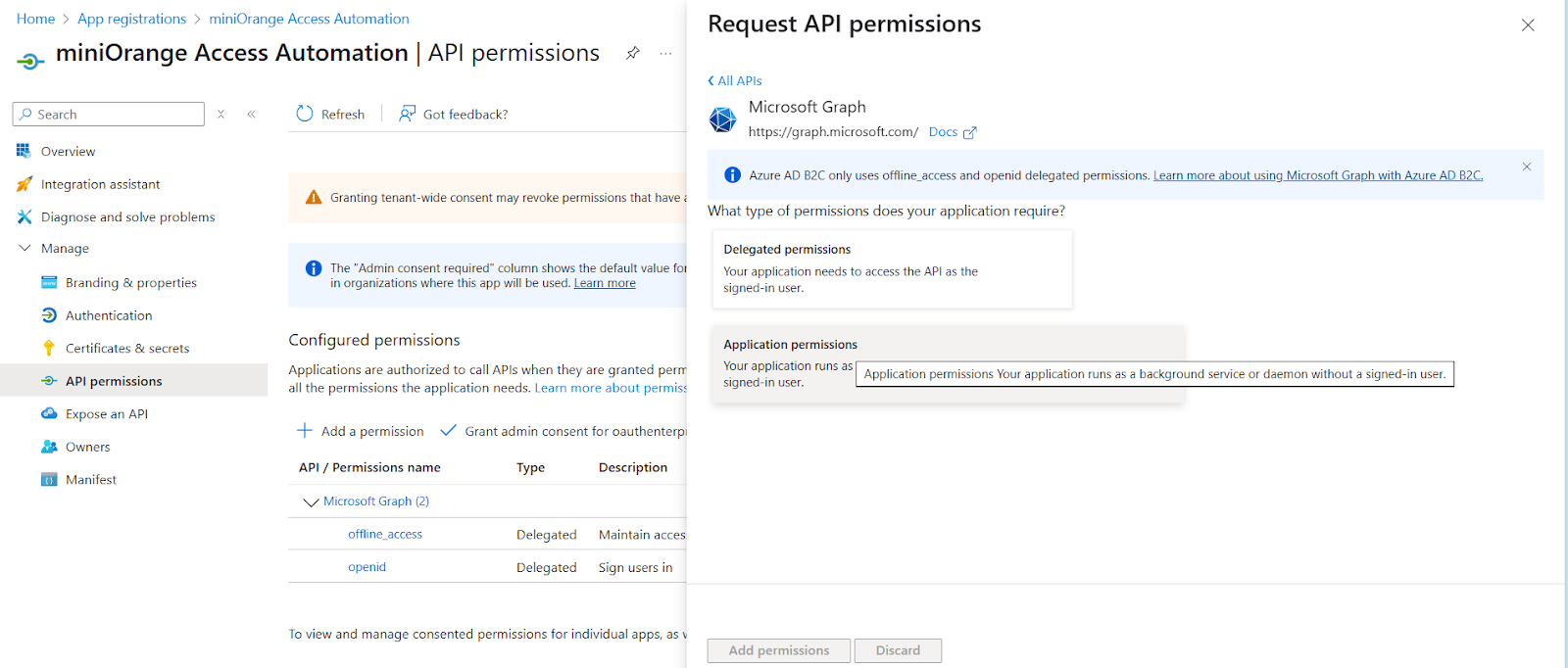
Navigate to API Permissions and click Add a permission
- Select Microsoft Graph → Application permissions.
-
Add:
User.ReadWrite.All
Group.ReadWrite.All
- Click Grant admin consent to apply these permissions.
2: Integrate Entra ID with the Access Governance Automation App
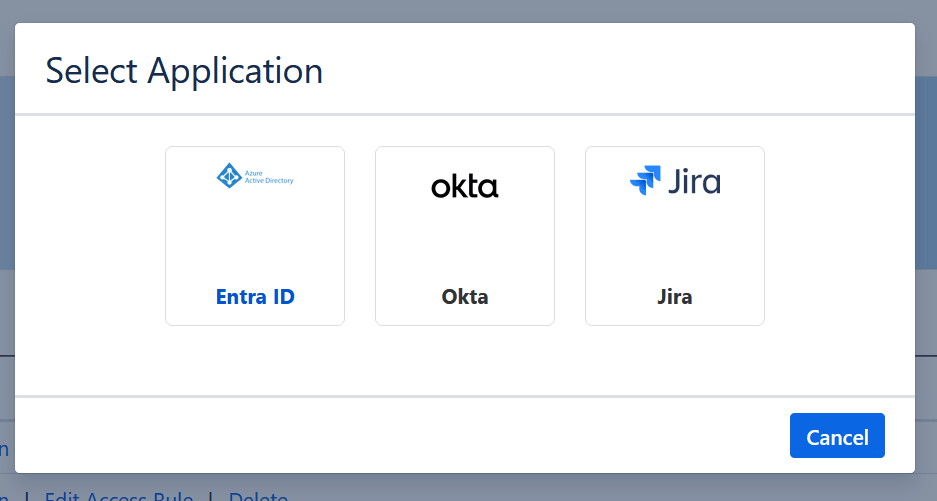
- Navigate to the miniOrange App → Application Integration section in Jira.
- Click New Application, then select Entra ID.
-
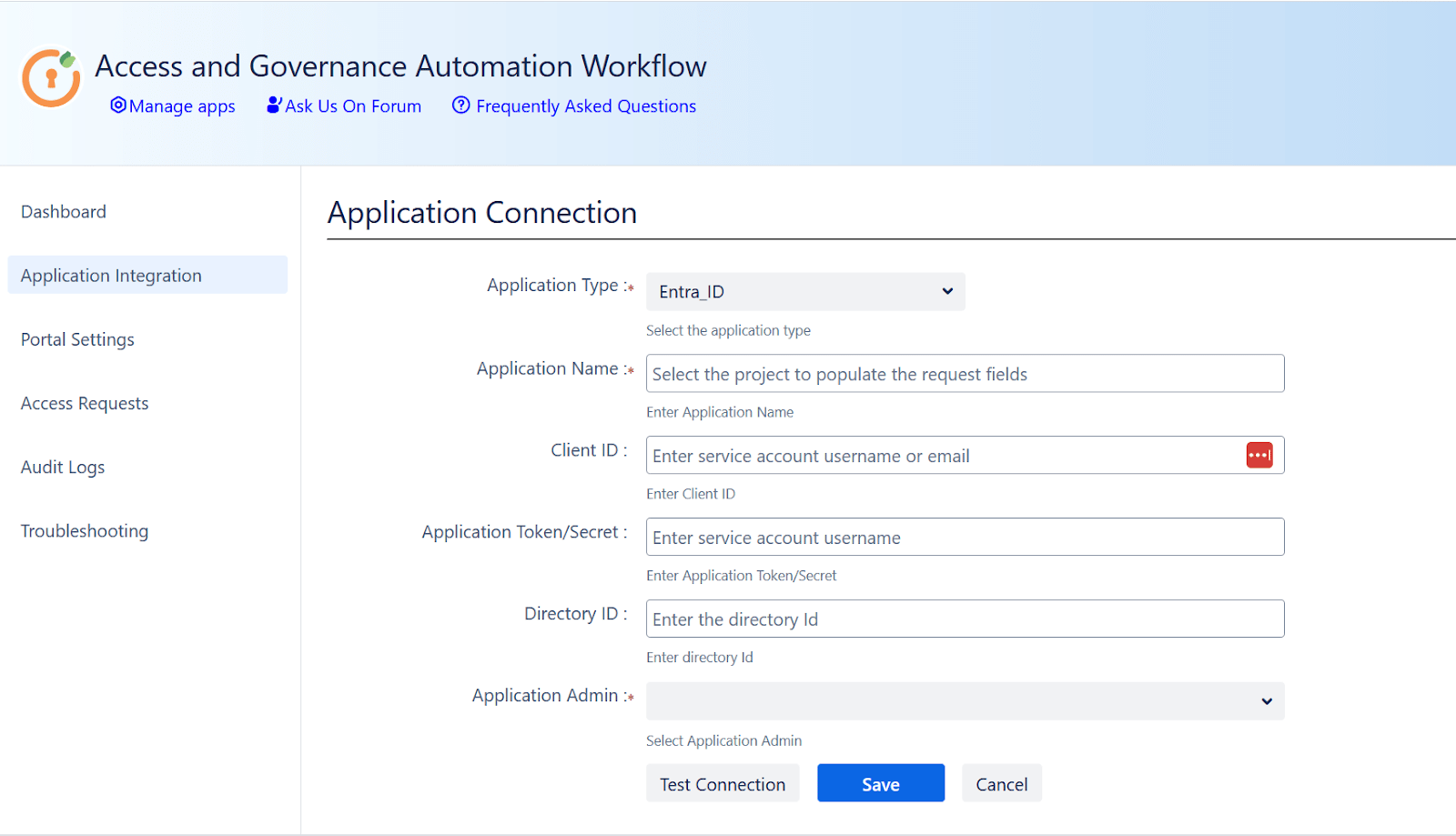
Enter the following details from Step 1:
- Client ID: The Client ID generated during app registration
- Application Token: The Client Secret you created
- Directory ID: The Tenant ID from Entra ID
- Fill in Application Name and Application Owner fields as needed.
- Click Save, then Test Connection to verify that the integration is successful.
3: Define Access Rules
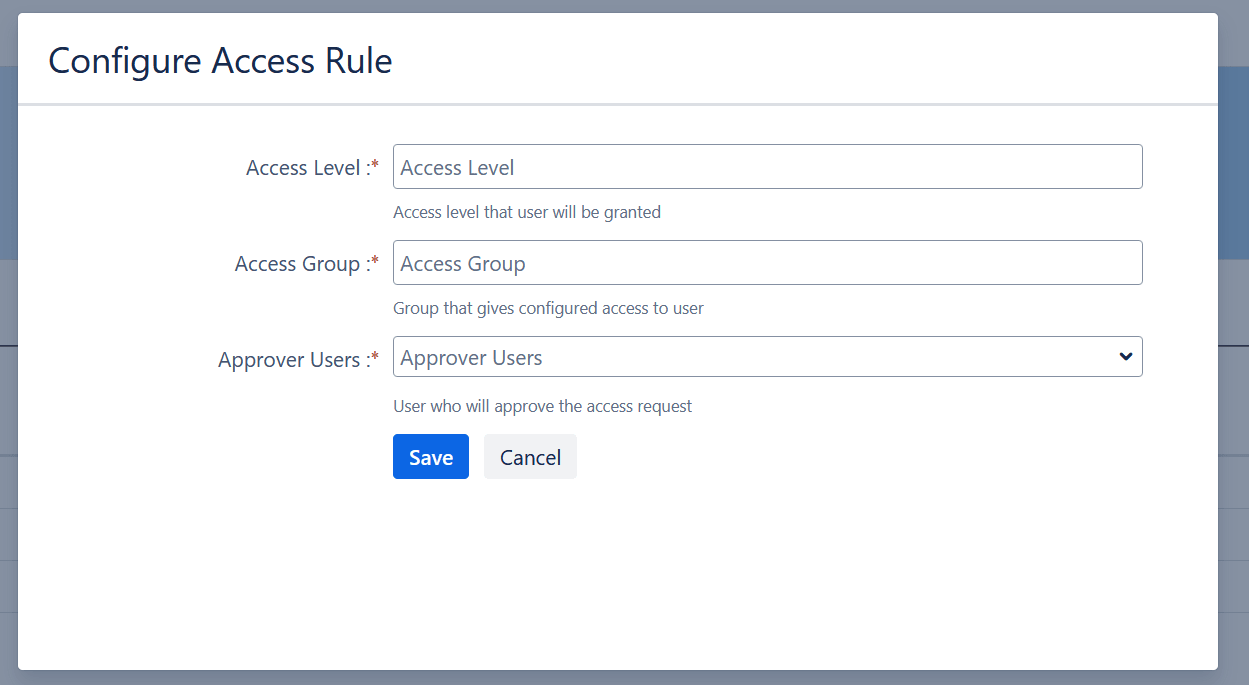
- Navigate to miniOrange App → Application Integration → Access Rules.
- Create a new access rule for each application you want to manage.
-
Configure the following for each rule:
- Access Level: Specify roles like User, Admin, etc.
- Access Groups: Define groups such as jira-software-users.
- Approvers: Assign the users or groups responsible for approving requests of this type.
- Save each rule to enable automated access management upon approval.
4: Set Up a Dedicated Access Request Portal in Jira Service Management
To keep access governance requests organized and separate from general IT support, it’s recommended to create a dedicated Jira Service Management (JSM) project for access requests.
How to Create the Access Request Portal:
- In Jira, go to Projects → Create Project.
- Choose the IT Service Management template.
- Name your project (e.g., Access Requests Portal).
Once the project is created, go to Project Settings → Request Types and create the following request types:
- Request Application Access
- Request Access Removal
- Request Access Change (optional based on your use case)
After creating request types, you need to add Custom Fields (List – Single Select):
-
Application: Lists all integrated applications
(e.g., Jira, Okta, AWS, Google Workspace) -
Access Type: Lists access levels
(e.g., User, Admin, Read-only)
These fields will power the automation rules and help route requests to the right approvers based on the selected app and access level.
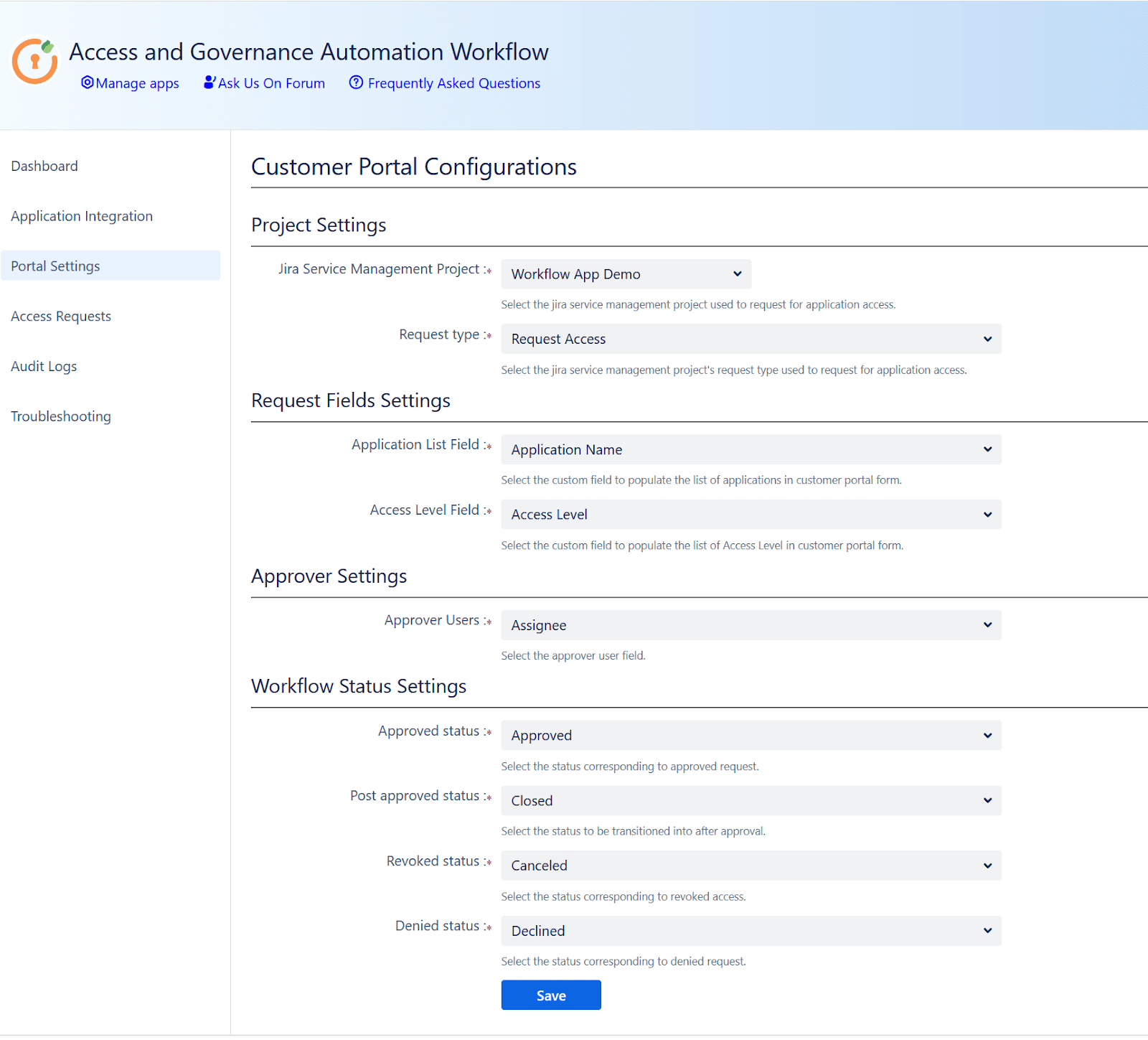
5: Map JSM Fields and Statuses in the Access Governance Automation App
To fully automate access provisioning workflows, you'll need to map your Jira Service Management (JSM) fields and statuses with the Access Governance Automation app for Jira.
Follow these steps:
- In Jira, go to the miniOrange Access Governance app → Portal Settings.
- Select and map your dedicated JSM project and its relevant request types.
Link Custom Fields:
Map the following JSM fields to their corresponding fields in the app:
- Application → Maps to the integrated application name (e.g., Okta, AWS)
- Access Type → Maps to predefined access levels (e.g., User, Admin)
- Approver User Field → Typically maps to a JSM field like Assignee
Map Jira Ticket Statuses to App Statuses:
To automate the request lifecycle, link your Jira ticket statuses to the app’s internal workflow:
| App Status | Jira Ticket Status (example) | Purpose |
|---|---|---|
| Approved | e.g., "Approved by Manager" | Triggers access provisioning |
| Denied | e.g., "Rejected" | Marks the request as denied |
| Revoked | e.g., "Access Revoked" | Triggers deprovisioning |
| Declined | e.g., "Declined by User" | Marks the request as declined |
Troubleshooting Common Issues
Having trouble setting up the Access Governance Automation app for Jira with Okta? Here are a few steps to help you quickly identify and resolve common setup issues.
Check the following:
- API Credentials: Make sure your Okta token and domain URL are correct and haven’t expired. Confirm that the account used has sufficient permissions.
-
Workflow & Approver Configuration: Ensure that:
- Access rules are properly defined
- Approvers are mapped correctly
- The right request types and custom fields are linked
- Jira Logs: Check Jira’s system logs for detailed error messages or permission-related failures.
- App Status Mapping: Verify that ticket statuses in Jira are correctly mapped to app statuses (e.g., Approved, Denied, Revoked).
Need More Help?
- Refer to the official support documentation
- Or reach out to our support team for personalized assistance
Best Practices
Maximize the efficiency, security, and compliance of your access management workflows by following these recommended best practices:
- Define Clear Access Policies: Ensure that your approval workflows are aligned with your organization's security and compliance policies. Define who can approve which types of requests and under what conditions.
- Regularly Review Audit Logs: Enable and monitor audit logs to track every access request, approval, denial, or revocation. This supports compliance audits and helps identify potential misconfigurations or misuse.
- Implement Role-Based Access Control (RBAC): Configure role-based provisioning so users are granted access based on their job roles or departments. This reduces manual effort, ensures consistency, and prevents over-provisioning.
Did this page help you?


 Try it for free
Try it for free