How to Set Up Access Governance Automation App for Jira with Entra ID (Azure AD)
Welcome to the setup guide for the Access Governance Automation app for Jira — your go-to solution for streamlining and automating access requests using Jira Service Management (JSM) and Microsoft Entra ID (formerly Azure AD).
This step-by-step guide will help you:
- Integrate Entra ID with the app
- Automate access approvals and provisioning
- Improve visibility, compliance, and control over access management
By the end of this guide, you’ll have a secure, rule-based workflow in place for handling access requests across your organization — directly from your Jira portal.
App Overview
The Access Governance Automation app for Jira is an advanced solution built on Jira Service Management (JSM) to simplify and automate access request workflows across your organization.
Instead of relying on manual request and approval steps, the app enables:
- End users to submit access requests through the JSM portal.
- Automated routing of approval workflows based on predefined rules.
- Instant provisioning actions once approvals are complete.
By automating these processes, the Access Governance Automation app for Jira ensures secure, policy-driven, and audit-ready access management across your tech ecosystem.
Pre-requisites
Before you begin, make sure you have the following:
- Admin access to Jira Service Management (JSM): Required to configure workflows, custom fields, and automation rules.
- Admin access to Entra ID (Azure AD) portal: Needed to authorize integrations and manage access provisioning.
- Access Governance Automation app for Jira: Ensure the app is installed from the Atlassian Marketplace and properly licensed via miniOrange.
1: Register an App in Entra ID(Azure AD)
To begin the integration, register a new app in Microsoft Entra ID (formerly Azure AD):
- Log in to your Azure Portal.
- Navigate to Azure Active Directory → App registrations.
-
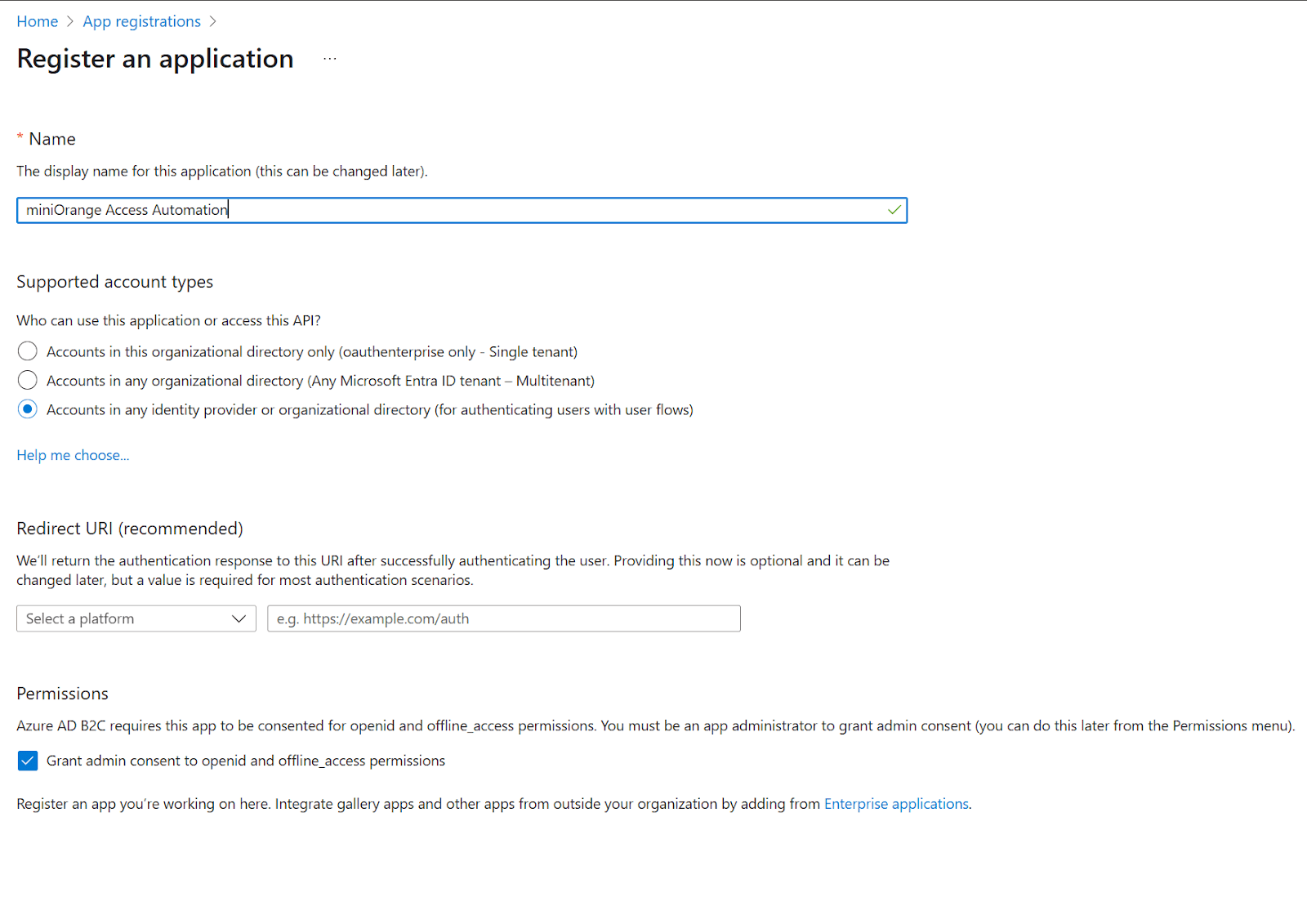
Click New Registration and fill the following details:
- Name: Provide Name for new application, for eg, miniOrange Access Automation App
- Redirect URL: Leave blank or enter dummy if required
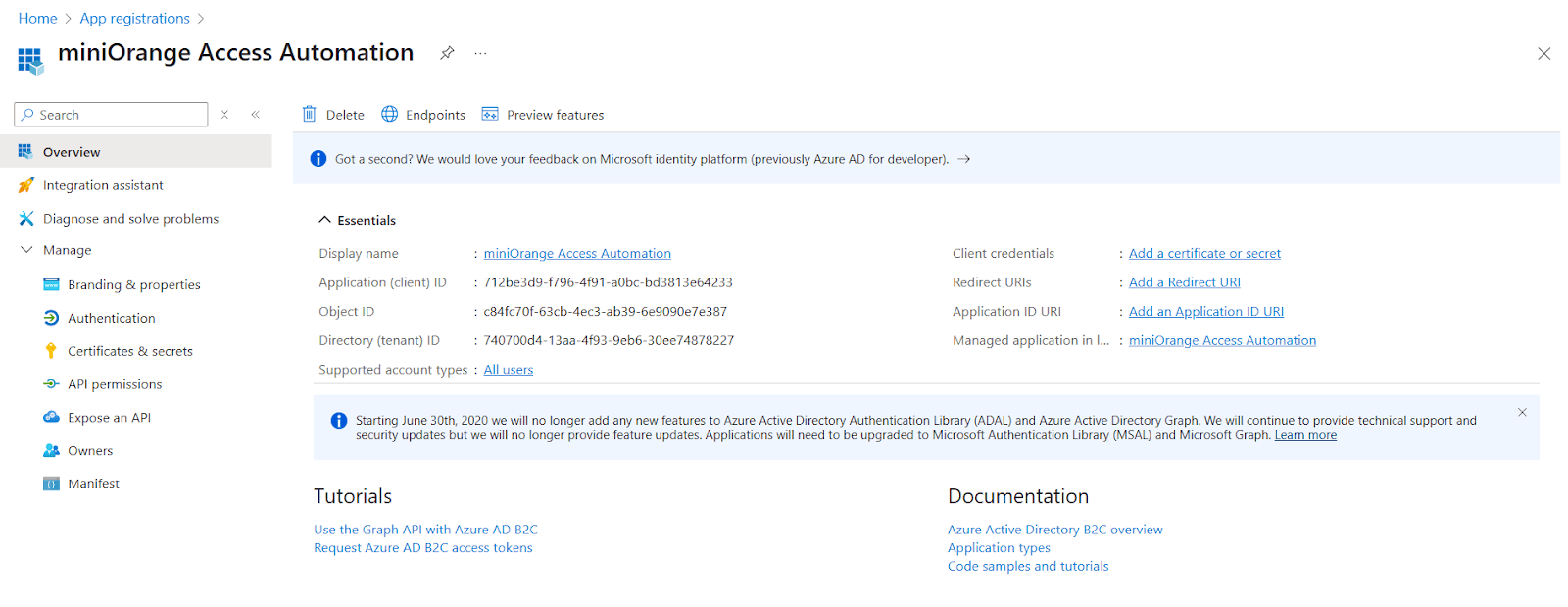
- After registration, go to the App Overview page and copy the Client ID and Tenant ID.
-
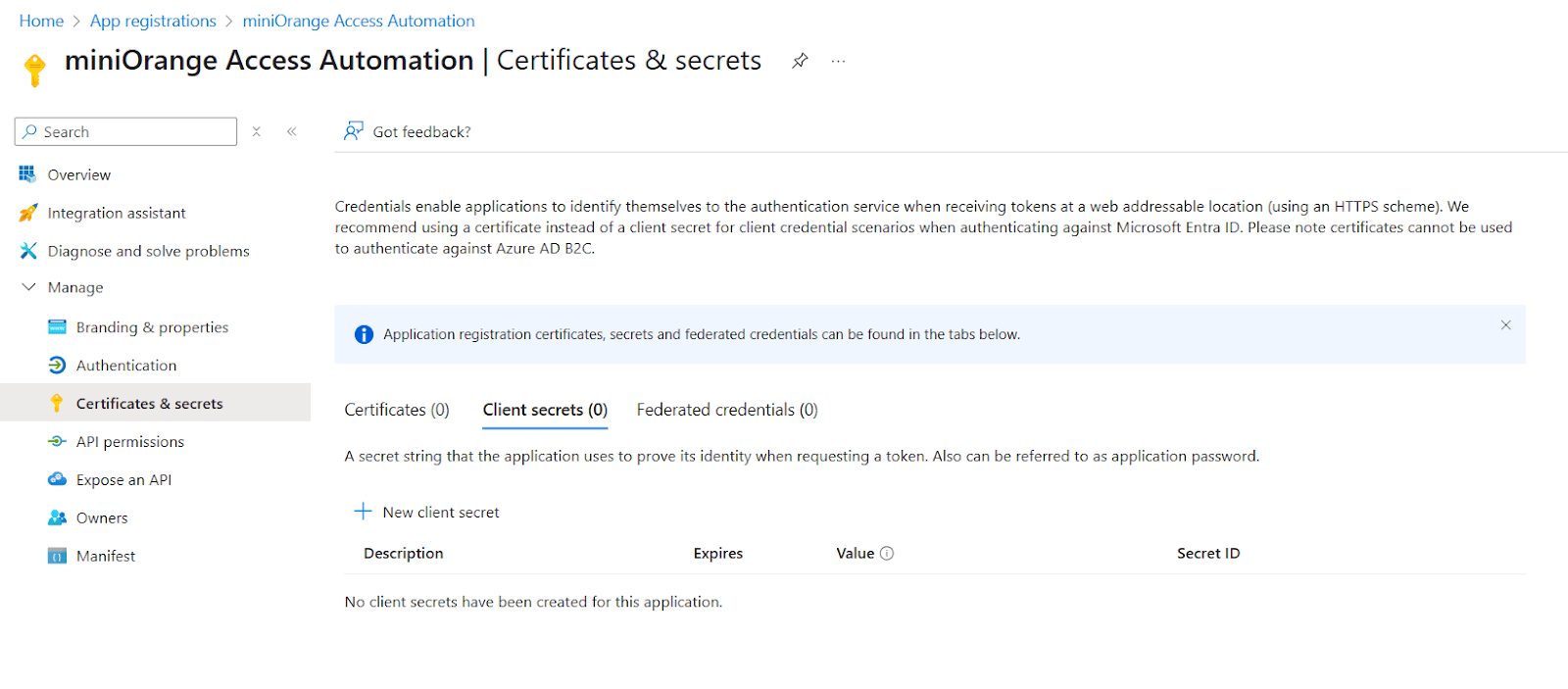
Under Certificates & Secrets → Client secrets, click
New client secret.
- Add a description and expiration period.
- Copy the secret value and keep it on your person (you won’t be able to view it again later).
-
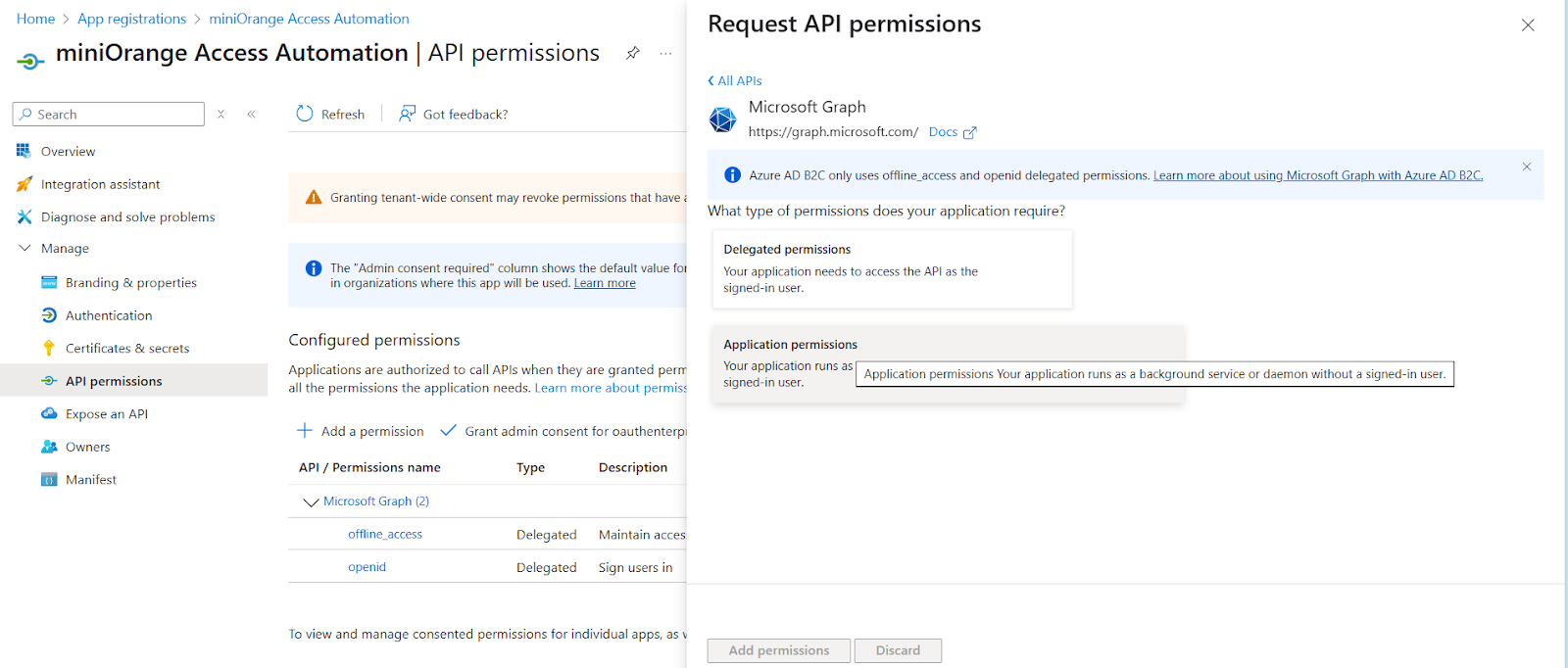
Navigate to API Permissions and click Add a permission
- Select Microsoft Graph → Application permissions.
-
Add:
User.ReadWrite.All
Group.ReadWrite.All
- Click Grant admin consent to apply these permissions.
2: Integrate Entra ID with the Access Governance Automation App
- Open App Connections from the sidebar.
- Click Connect new app and choose Entra ID.
-
Enter the following details from Step 1:
- Client ID: The Client ID generated during app registration
- Application Token: The Client Secret you created
- Directory ID: The Tenant ID from Entra ID
- Fill in Application Name and Application Owner fields as needed.
- Click Save, then Test Connection to verify that the integration is successful.
3: Portal Config — Set Project, Request Type, Fields, Statuses for Access Requests
Configure the Jira project, request type, fields, and status names used by access workflows. Complete this before creating automations.
- Jira Service Management Project: Select the JSM project used for access requests.
- Request Type: Select the request type within the chosen JSM project. This determines which custom fields are available.
- Access Level Field: In the selected JSM project and its request type, create a new custom field of type Select list (single choice). Then select that field here. It will store values like "Application Name - Access level".
- Approver Field: Map the custom field that holds the approver for the request raised.
- Status: Map Approved and Denied status names used by your Jira workflows.
- Click Save Settings.
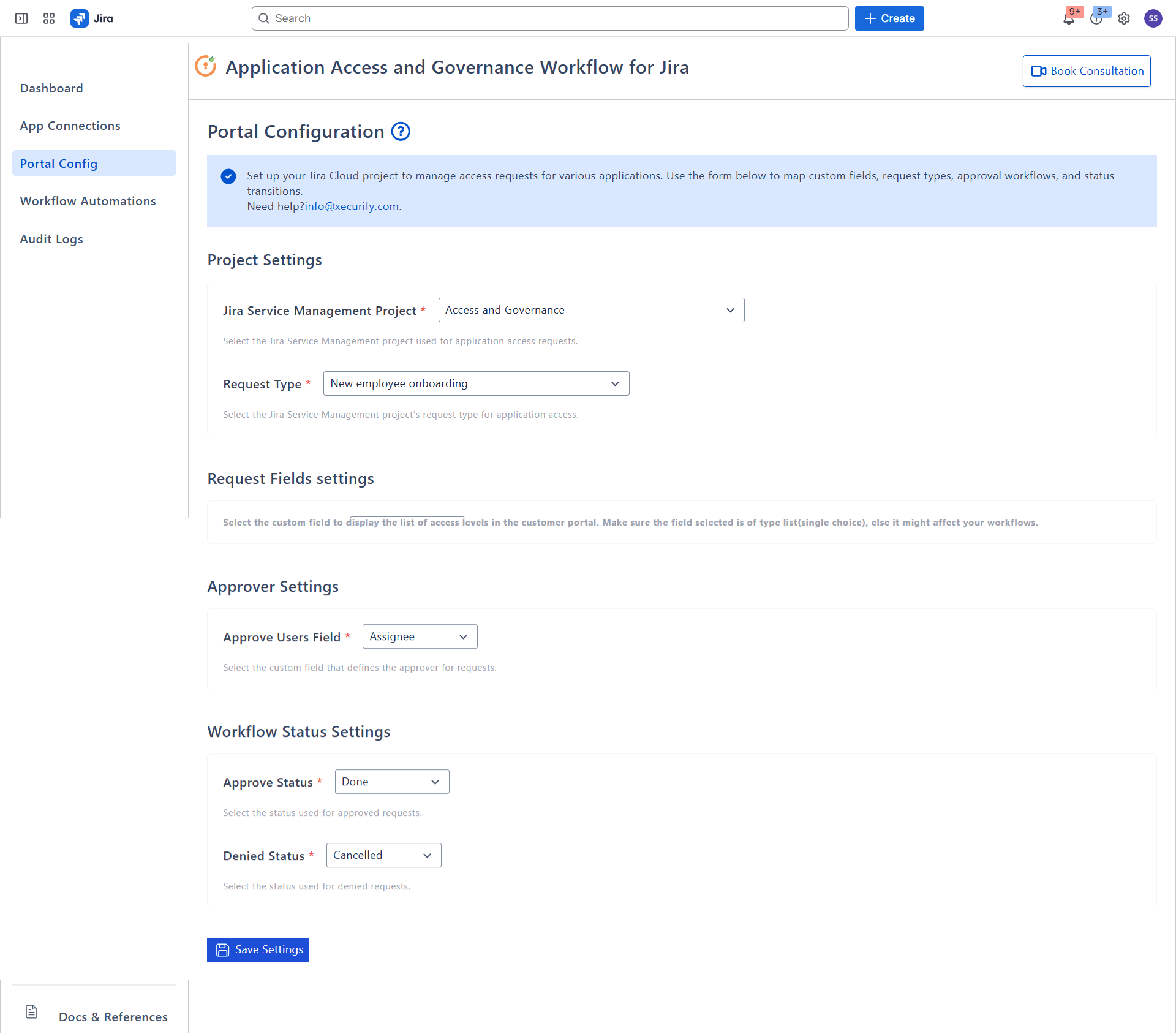
Access Level options are added to your Jira field when you save a workflow. On app rename, related options are removed and recreated automatically to reflect the new app name.
4: Define Access Rules for Entra ID
Once your Entra ID integration is connected, the next step is to define access rules within the Access Governance Automation app for Jira. These rules determine how access requests are routed and approved for your application.
How to Create Access Rules:
- Go to Workflow Automations and click Create New Automation.
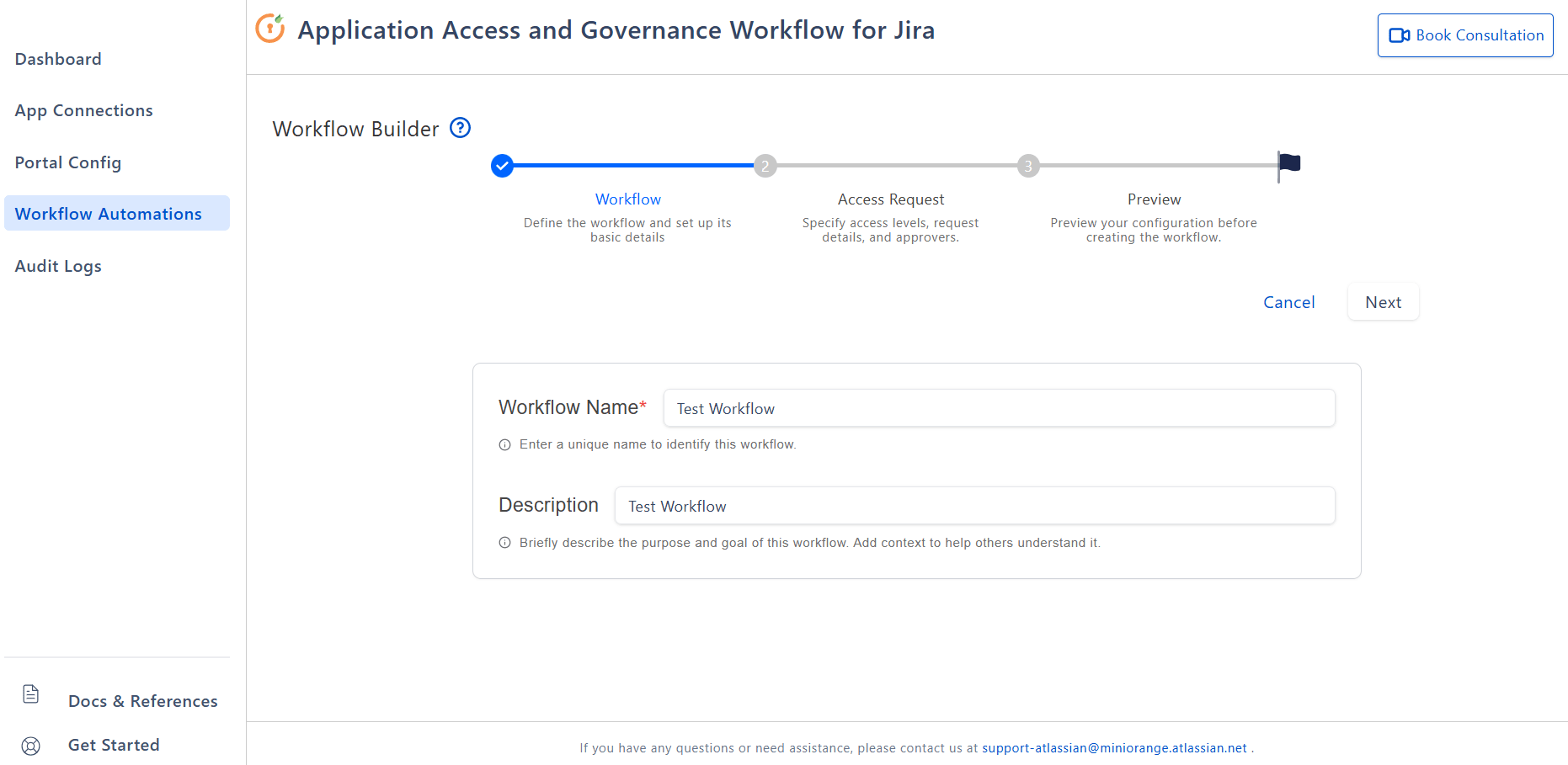
- Workflow: Enter a clear name and a short description.
-
Access Request:
- Select Application.
- Enter an Access Level (e.g., L1, L2). When you save the workflow, the system will create the corresponding option in your configured Access Level Jira field, formatted as "Application Name – Access level".
- Choose an Approver (licensed, active user). The system stores the user’s accountId and sets it on the Jira issue in the Approver field you selected in Portal Config, when the selected workflow runs for the request.
- Enter the Access Group to be granted. This group must already exist in the connected application; otherwise the workflow will not run successfully.
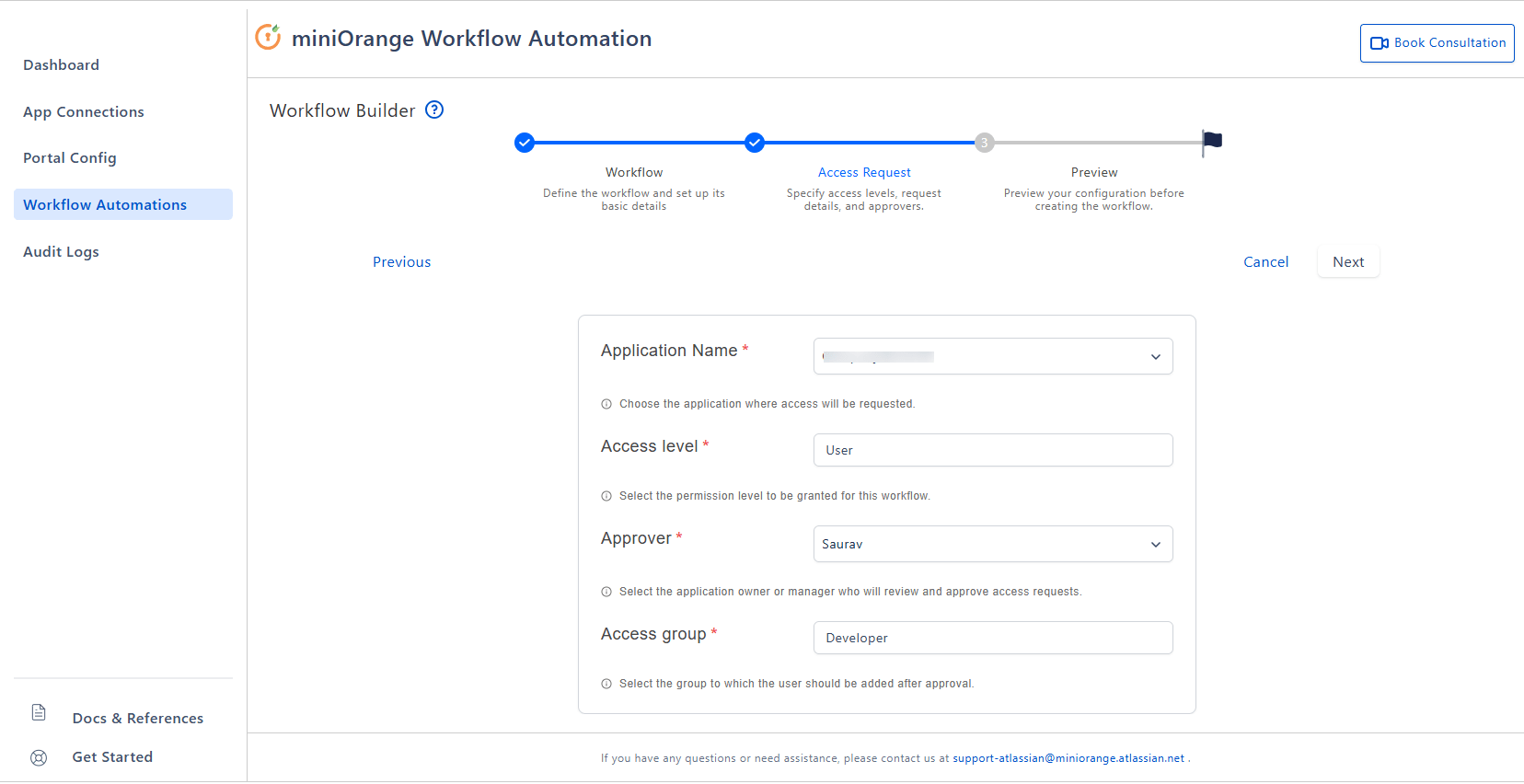
- Review and click Save.
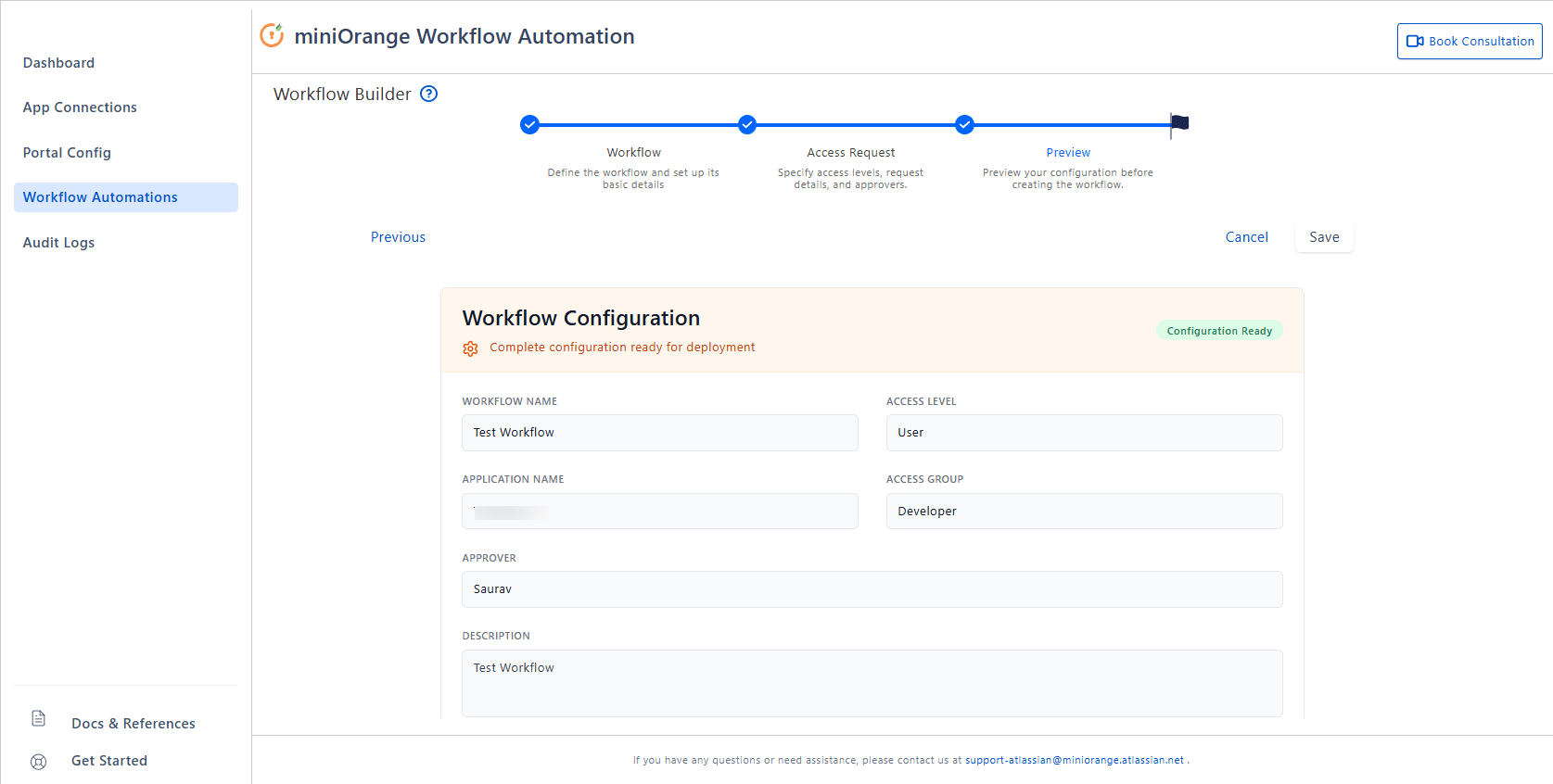
After saving, the Access Level option is created automatically if it doesn’t already exist.
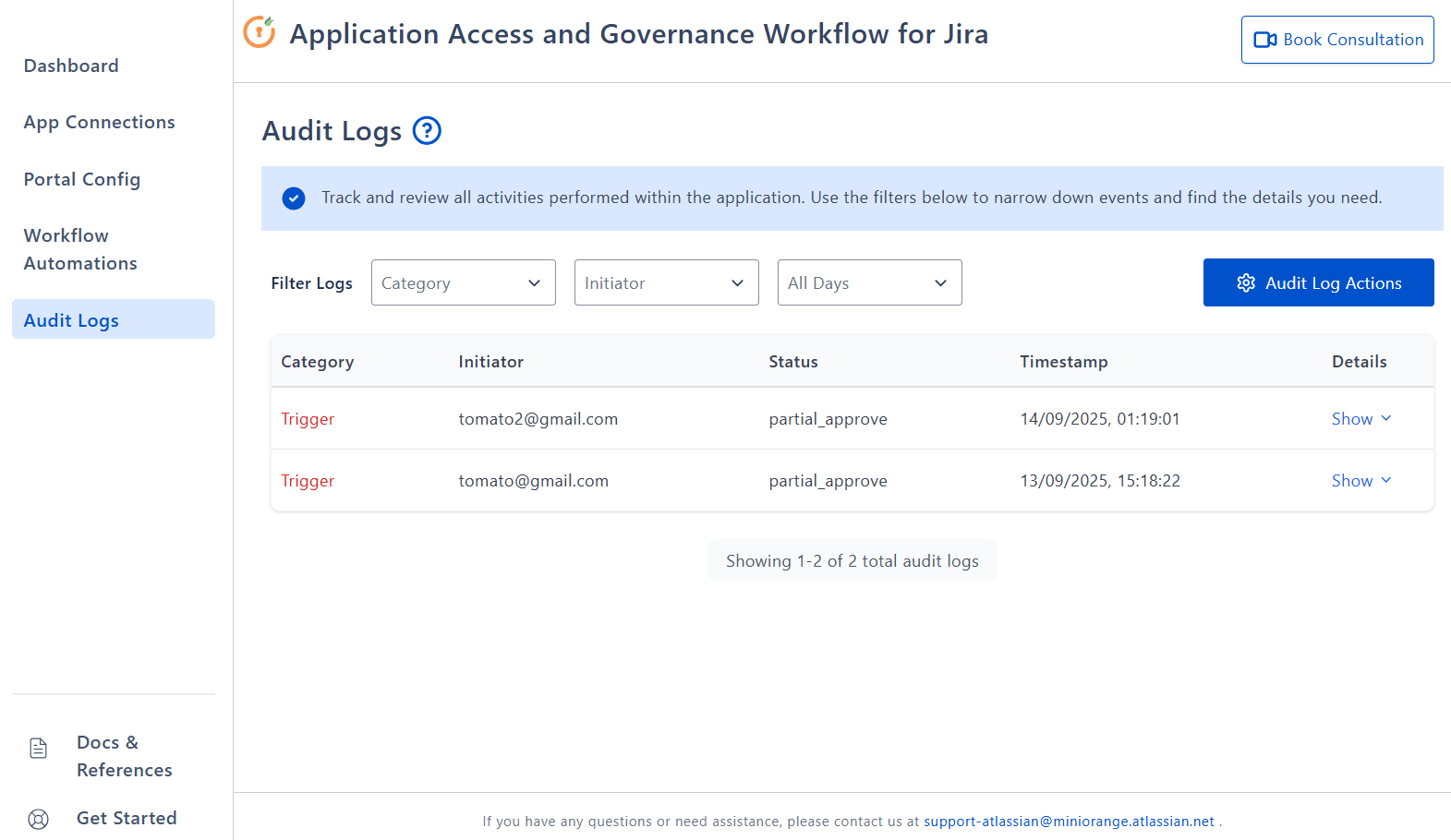
5: Review Audit Logs for Compliance and Troubleshooting
Use Audit Logs to search, review, and export activity for troubleshooting and compliance.
- Open Audit Logs.
- Apply filters (Category, Initiator, Date/Range).
- Click Audit Log Actions to export audit logs as CSV/JSON/PDF.
Best Practices for Admins
Maximize the efficiency, security, and compliance of your access management workflows by following these recommended best practices:
- Use service accounts for provider tokens; rotate them regularly.
- Keep Portal Config consistent (fields and status names) across projects.
- Always test connections after credential changes.
- Name workflows clearly (e.g., "Entra ID – HR L1").
- Review Audit Logs periodically and export for audits.


 Try it for free
Try it for free