Granular Portal Access Control in Jira Service Management SSO
Secure your customer portals by restricting access based on IDP groups and Jira organizations. Dynamically map users after SSO to ensure only authorized users gain access. Enhance security and streamline user management without manual intervention.
Business Challenge
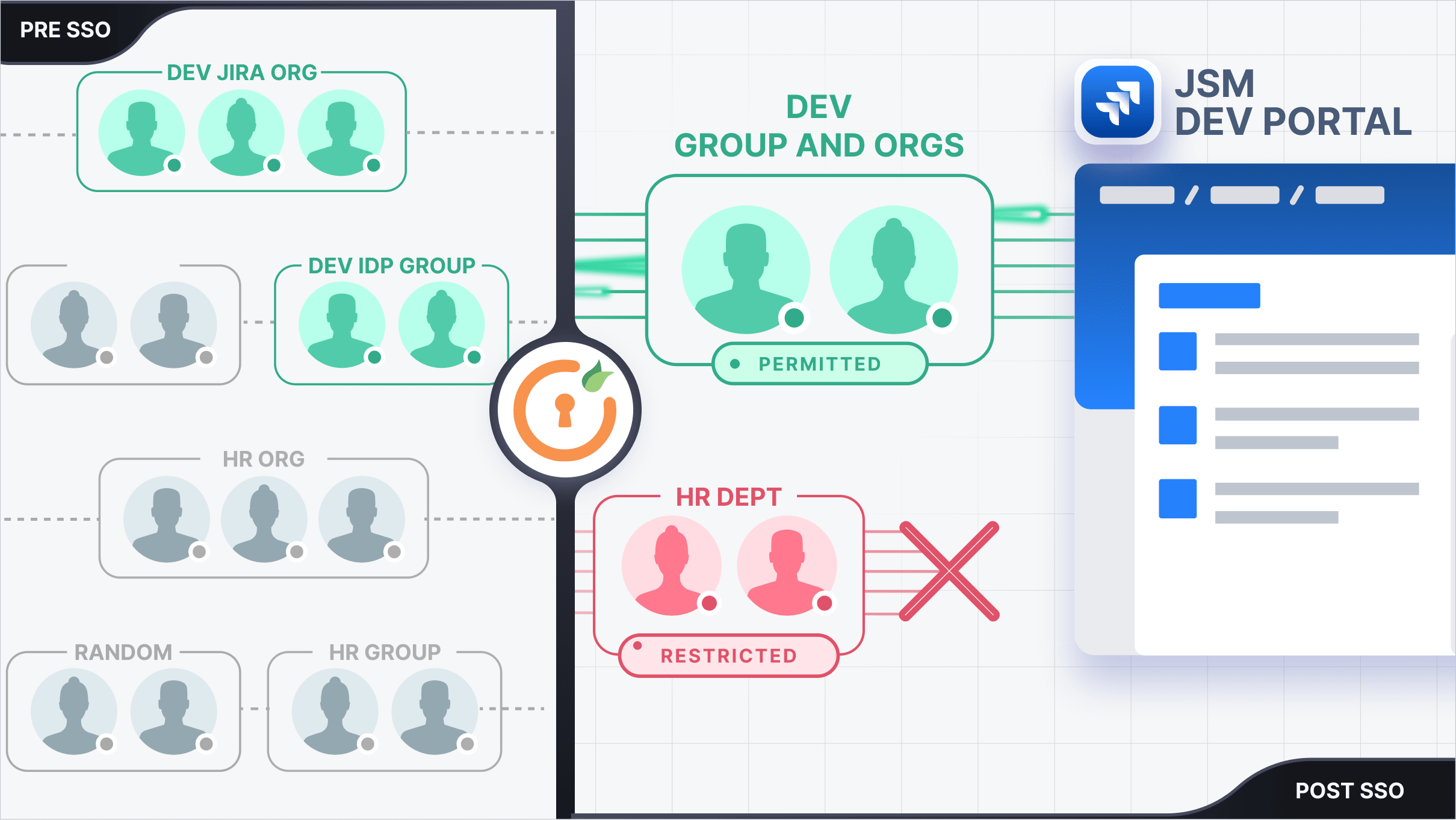
Atlassian’s Jira Service Management (JSM) enables SSO for customer portals, allowing external users to log in seamlessly. However, it lacks granular access control, making it challenging to restrict portal access based on IDP groups or Jira organizations after SSO.
The miniOrange SAML/OAuth SSO app for external customers enhances security and flexibility with its Portal Access Mapping feature. This allows admins to easily control portal access by restricting it based on IDP groups and Jira organizations, ensuring the right users have access to the right portals.
With dynamic access enforcement after SSO, only authorized users can enter specific portals, strengthening security without compromising user experience.
How It Works
The Portal Access Mapping feature overrides Jira's default Customer Access Permissions when mappings are set by the project admin, ensuring access control follows the custom rules defined in our add-on.
Admins can configure portal access in three different ways:
Default (Jira-Based Access Control)
- This setting respects the default Jira “Customer Access Permissions” and does not override any existing permissions. All projects have this setting enabled by default.
- Allows all users to access the portal without any restrictions.
- Only users mapped via IDP Groups or Jira Organizations will have portal access.
Public (Unrestricted Access)
Private (Restricted Access Based on Mapping)
Key Benefits
Effortless setup with multi-IDP support, user choice, and domain-based redirection.
Jira Organization-Based Mapping
Grant portal access only to users belonging to specific Jira organizations configured by the admin.
IDP Group-Based Mapping
Restrict access to users from designated Identity Provider (IDP) groups after successful SSO.
Combined Mapping (Organizations + IDP Groups)
Allow access if a user belongs to either the mapped Jira organization or IDP group, ensuring strict control.
Domain-Based Organization Mapping
Automatically assign users to Jira organizations based on their email domains and restrict access accordingly.

