Jira Service Management SSO with Integrated Broker Flow
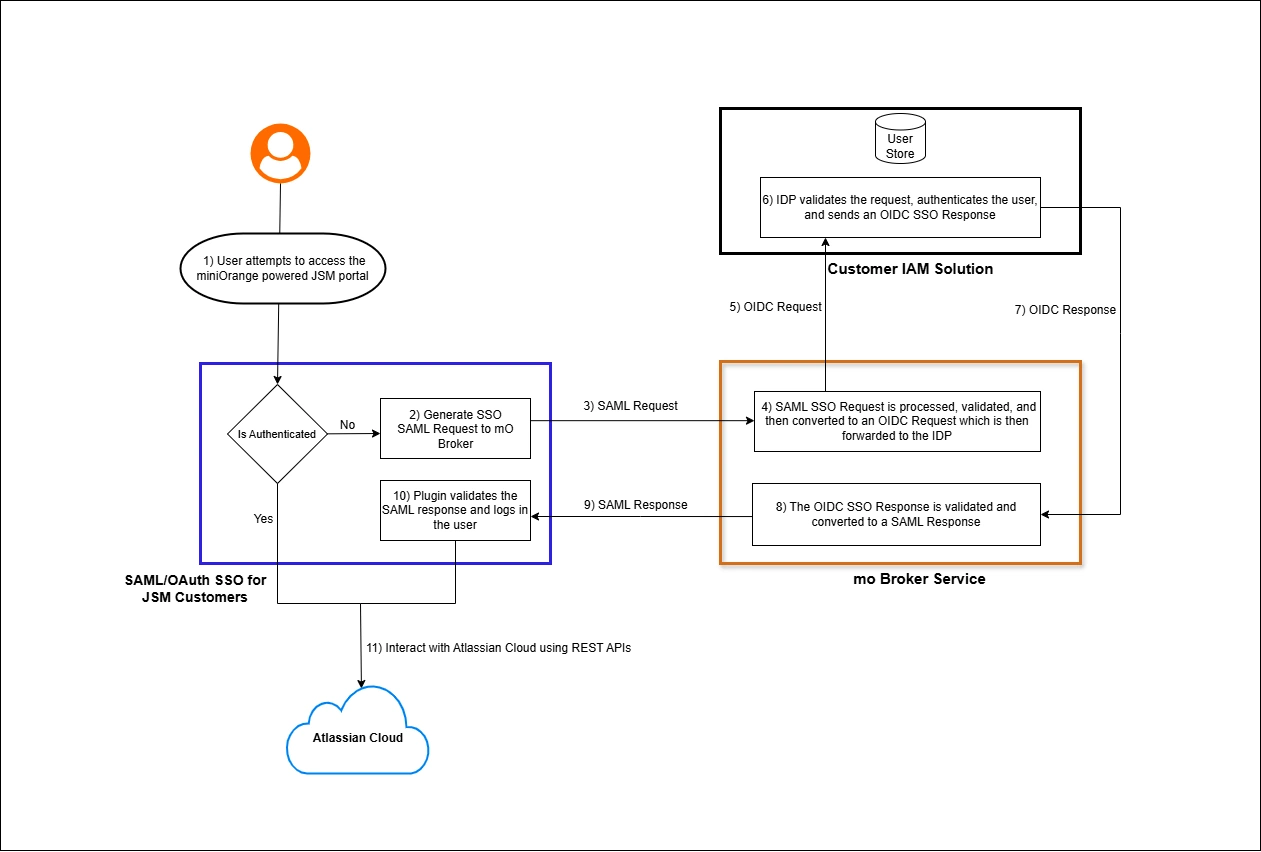
User Flow Diagram
Applications involved:
- SAML/OAuth SSO for JSM customers (mO powered JSM portal)
- miniOrange Broker Service
- Customer IAM Solution
- Atlassian Cloud
User Authentication and Data flow:
- When a user accesses the customer portal URL powered by miniOrange, they are redirected to the miniOrange broker with a SAML request.
- The broker validates the SAML request and initiates an OAuth request to the Identity Provider (IdP) for user verification.
- The user is then redirected to the IdP's login page.
- After successful authentication, the IdP redirects the user back to the miniOrange broker with an OAuth response.
- The broker converts the OAuth response into a SAML response and forwards it to the plugin.
- The SAML/OAuth SSO for JSM Customers plugin verifies the SAML response and redirects the user to the customer portal powered by miniOrange.
How Data is stored and processed by Each Application
1. SAML/OAuth SSO for JSM Customers (mO powered JSM portal)
This is the customer portal that end users access after successful authentication. It replicates the native Jira Service Management (JSM) portal experience, as for cloud environments, Atlassian does not allow third-party control over its authentication mechanism.
- Data Stored:
- Email address and API token of a service account with admin privileges (used for Atlassian REST API calls).
- Account ID of authenticated users for audit logging.
- IP address and last login time of users for session tracking and user activity visibility.
- Data & Security Measures:
- We do not store end-user email addresses or any personally identifiable information (PII), apart from the account ID required for audit purposes.
- We use authenticated Atlassian REST API endpoints to securely and dynamically retrieve and update data to and from the Atlassian Cloud.
2. miniOrange Broker Service
This in-house service manages identity federation between the SAML/OAuth SSO for JSM Customers and the customer’s Identity and Access Management (IAM) system, using SAML 2.0, OAuth 2.0, or OpenID Connect (OIDC) protocols.
- Data Stored:
- No user data is stored. All authentication and token data is processed in-memory and discarded post-session.
- Data & Security Measures:
- All inter-service communication is conducted over HTTPS (TLS 1.2 or higher).
- Tokens and assertions are signed and validated using secure cryptographic standards.
- No persistent storage of user identities or credentials.
Additional Resources:

