REST API Authentication In Atlassian using Microsoft Entra ID (Previously known as Azure AD) as OAuth Provider
Enhance API Security for Jira REST APIs with OAuth/API Token plugin will let you authenticate any application (Jira, Confluence, Bitbucket) APIs using any third-party OAuth/OIDC provider or API Tokens. The app supports Azure AD, Keycloak, Okta, AWS Cognito, Google, Github, Slack, Gitlab, Facebook, and any custom provider.
Atlassian provides REST APIs to perform several operations such as Create Page, Delete Page, Add Comment, Create Space, etc. However, it supports only two authentication methods for REST APIs:
1. Basic Authentication
2. Using OAuth 1.0
Video Setup Guide
Download and Installation
- Log into your Atlassian instance as an admin.
- Navigate to the settings menu and click Manage Apps.
- Click Find new apps or Find new add-ons from the left-hand side of the page.
- Locate Enhance API Security for Jira REST APIs with OAuth/API Token app.
- Click Try free to begin a new trial or Buy now to purchase a license.
- Enter your information and click Generate license when redirected to MyAtlassian.
- Click Apply license.
Step 1: Configure Microsoft Entra ID (Previously known as Azure AD) server:
- Sign in to Azure portal. Click on App Services and go to Manage Azure Active Directory.
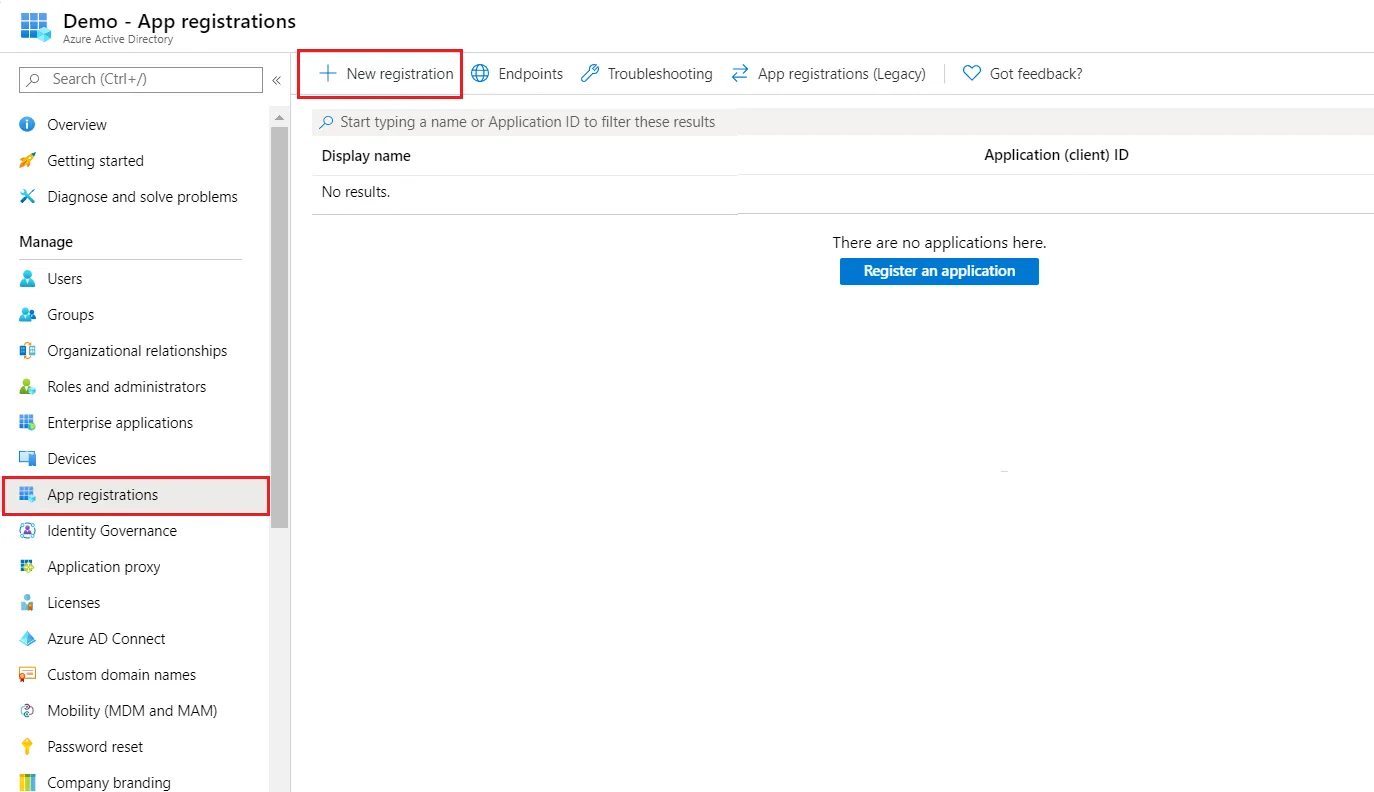
- In the left-hand navigation pane, click the App registrations service, and click New registration.
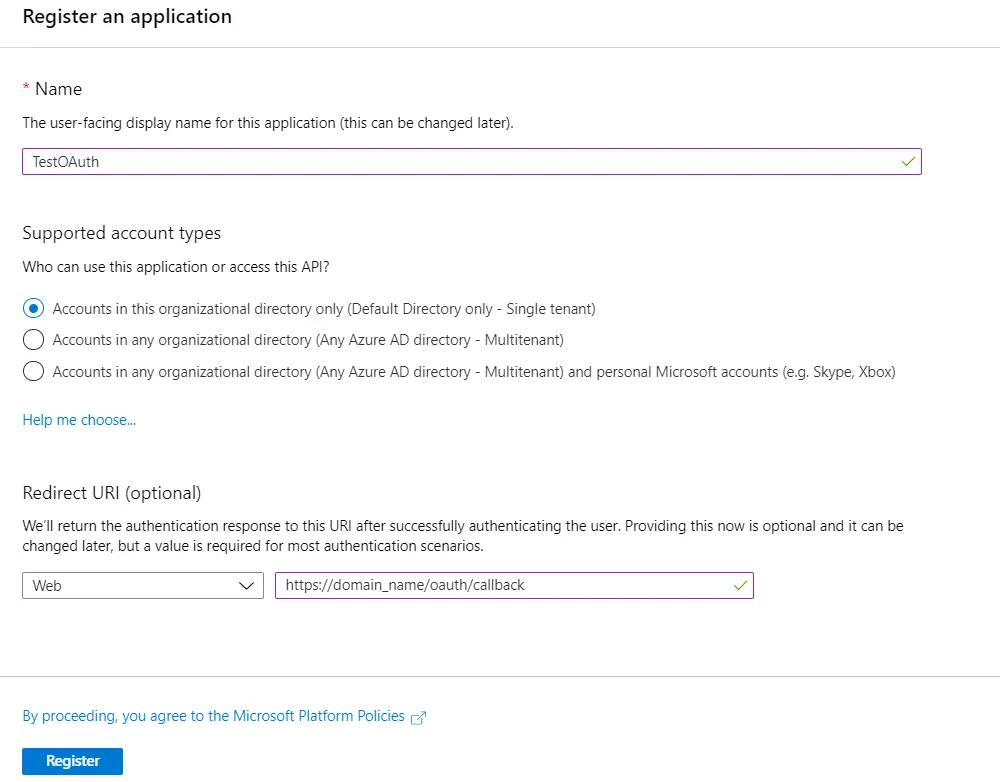
- When the Create page appears, enter your application's registration information. Enter the Your Application's Base URL as callback URL. When finished, click Register.
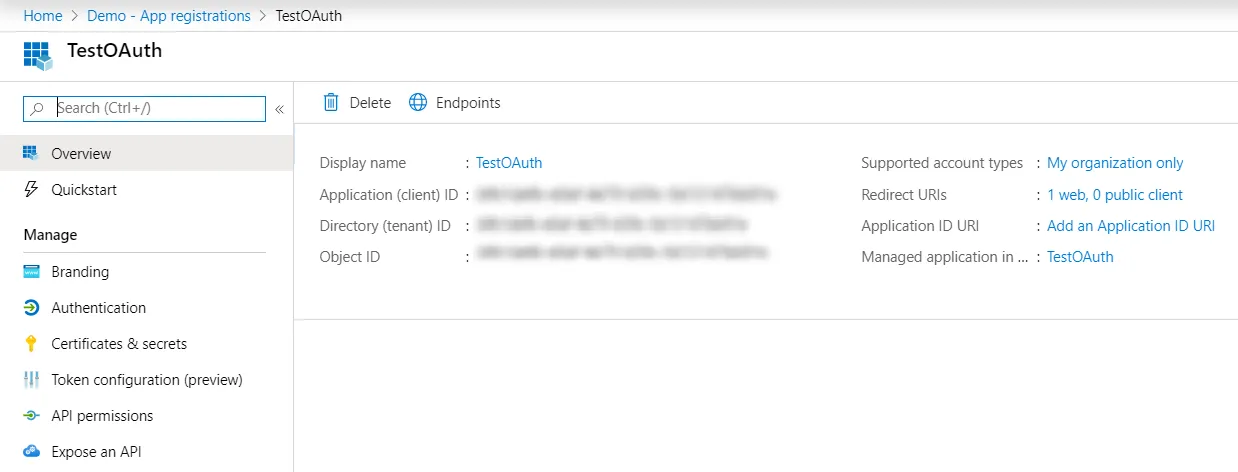
- Microsoft Entra ID (Previously known as Azure AD) assigns a unique Application ID to your application. Copy Application ID and the Directory ID , this will be your Client ID and Tenent ID.
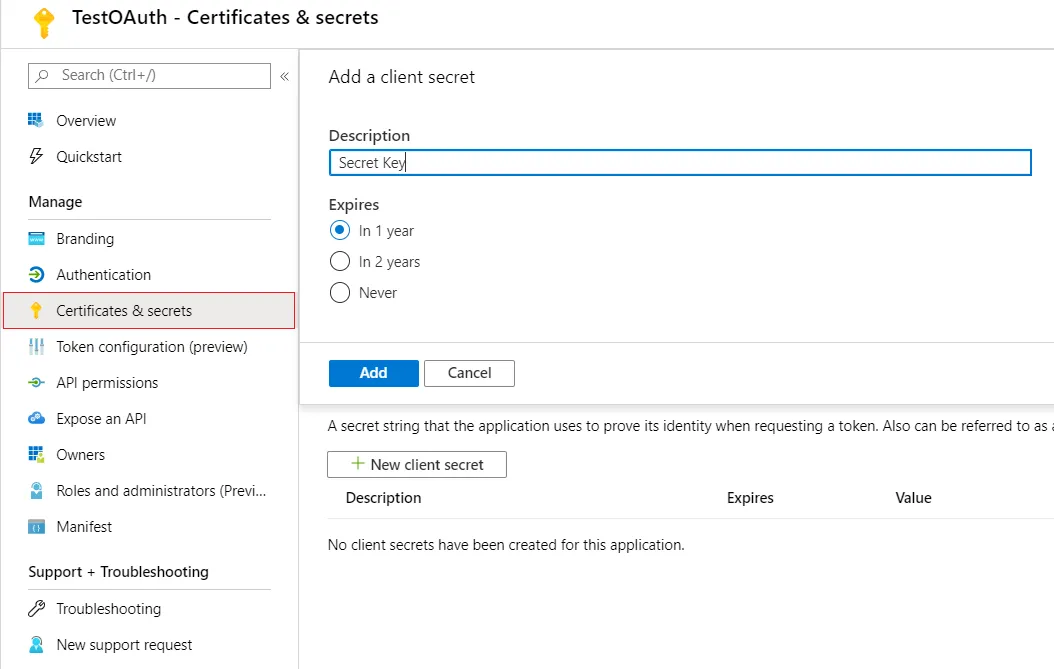
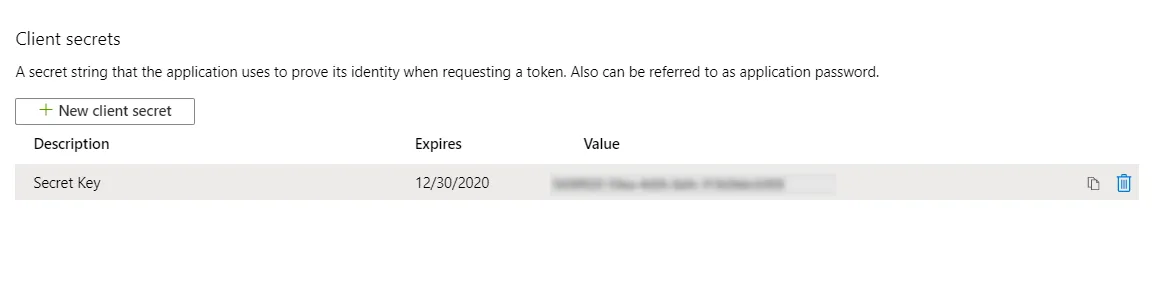
- Go to Certificates and Secrets from the left navigaton pane and click on New Client Secret. Enter description and expiration time and click on ADD option.
- Copy value. This will be your Secret key.
Step 2: Fetch Access token through POSTMAN:
- Open the Postman Application (Here is the link to download Postman Application).
- Go to Authorization tab.
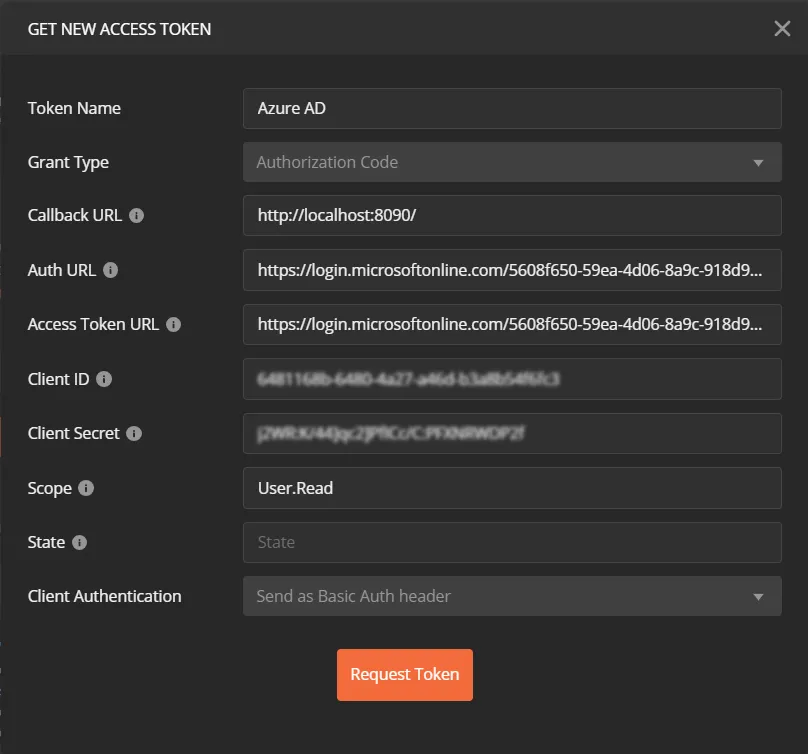
- From the dropdown select type as OAuth 2.0 and click on Get access token.
- Add the following information from the table below.
- Postman starts the authentication flow and prompts you to use the access token.
- Select Add token to the header.
- Copy the Access Token or click on Use Token.
- A sample access token from Microsoft Entra ID (Previously known as Azure AD) Provider looks like this.
| Grant type | Authorization Code or Client Credentials |
| Callback URL | Enter your application's base URL if you dont have a callback URL |
| Auth URL | https://login.microsoftonline.com/{TenantID}/oauth2/v2.0/authorize |
| Access token URL | https://login.microsoftonline.com/{TenantID}/oauth2/token" |
| Client ID | Enter the Microsoft Entra ID (Previously known as Azure AD) Client ID |
| Client secret | Enter the Microsoft Entra ID (Previously known as Azure AD) Client secret |
| Scope | User.Read |
| Client Authentication | Send as Basic Auth Header |
e8ec210628306b1df26ff61e6b9b3195814a2d79d38a2c7c1dc5836f6ddd7143
Step 3: Fetch Username through Microsoft Entra ID (Previously known as Azure AD):
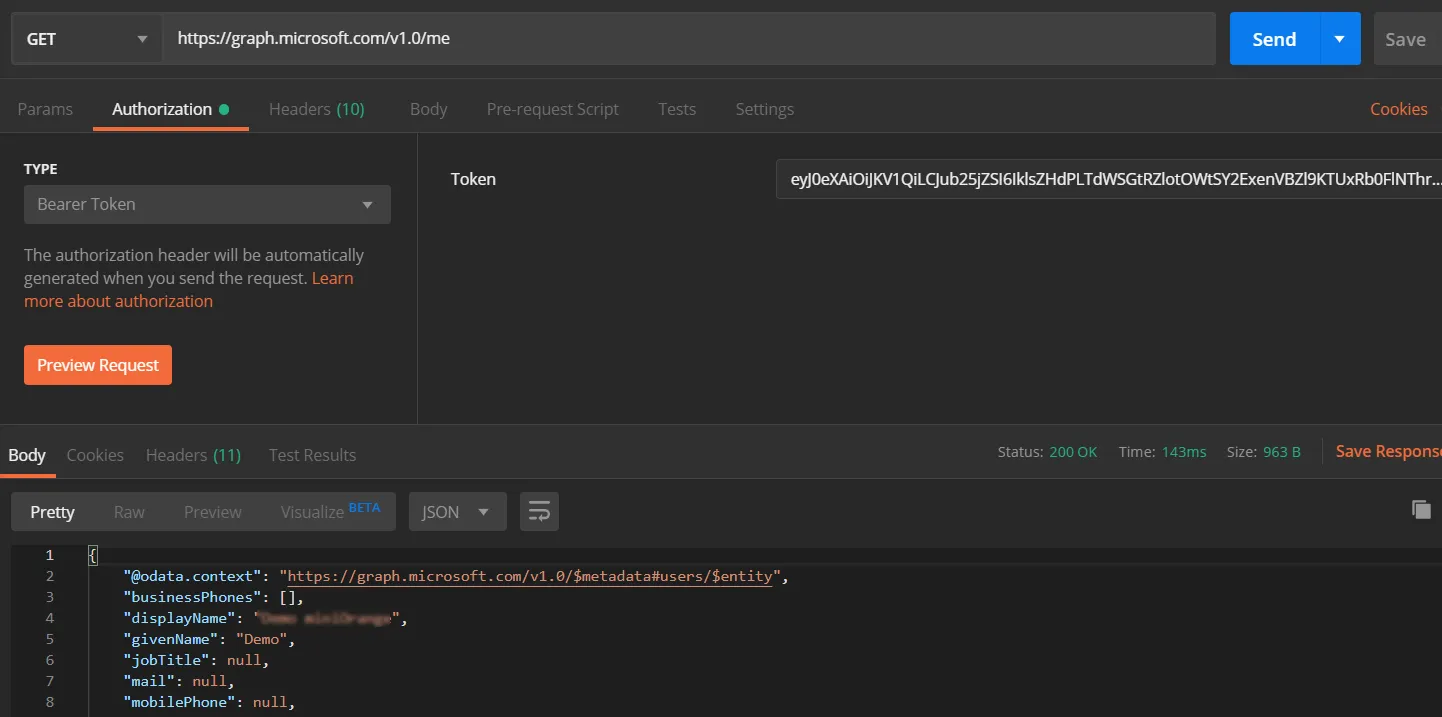
- Choose the method type as "GET".
- Enter the interoception Endpoint from the plugin to fetch the username in the Request URL. For Microsoft Entra ID (Previously known as Azure AD) it is "https://graph.microsoft.com/v1.0/me".
- Go to the Authorization tab select the Bearer Token and enter the access token here.
- Add the header "content-type: application/json" and click on Send.
Request:
curl
-X GET
-H "Authorization: Bearer <Access Token>"
-H "Content-type: application/json"
https://graph.microsoft.com/v1.0/me
Copy the attribute value against the username, you will need to configure it in plugin. In this example, the value is "givenName".
Step 4: Configure the Rest API plugin:
1: Enable Rest API Authentication:
- After installing the app, click on Configure to configure plugin.
- Select the Authentication type and navigate to Oauth/OIDC tab, then click on Configure.
- From the drop down select Microsoft Entra ID (Previously known as Azure AD) as OAuth Provider.
- Enter the Tenant ID, that you will find in the Microsoft Entra ID (Previously known as Azure AD) console.
- Enter the attribute value against which we received the username in the Postman response.
- Save the settings.
- Now navigate to the Global Settings tab.
- Here you will have to Enable the Authentication through Enable REST API Authentication and click on Save.
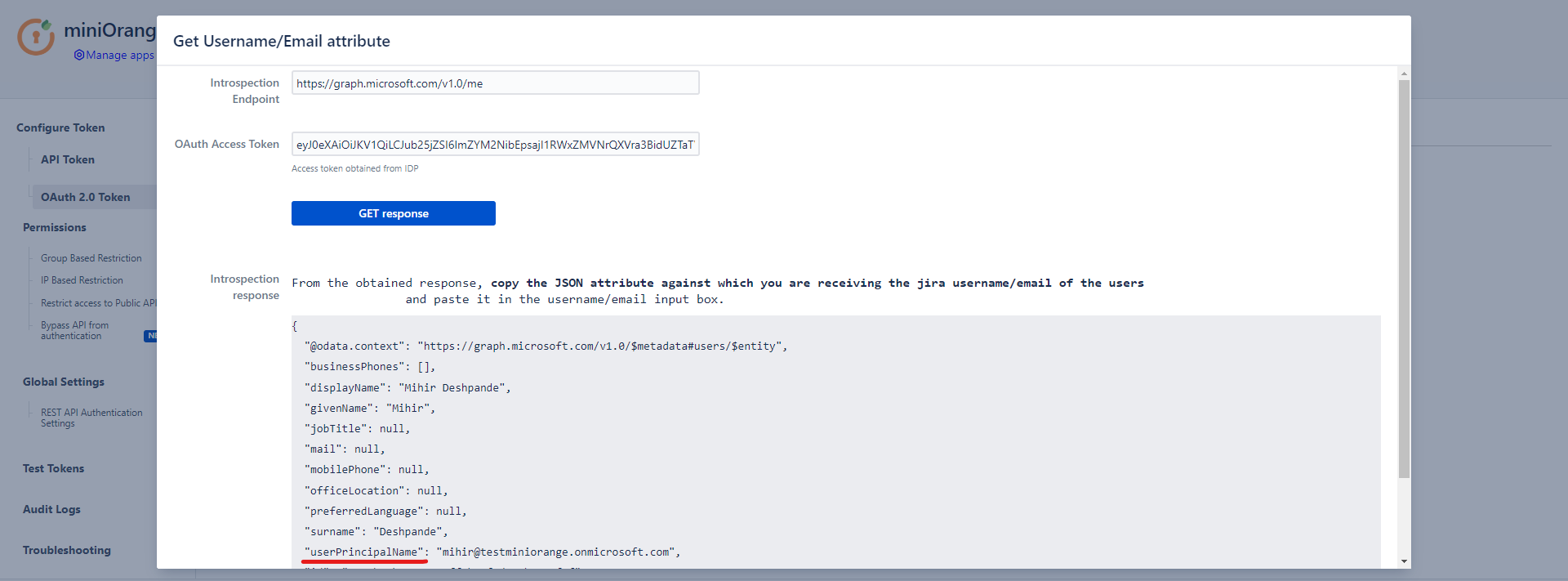
- To configure the username attribute, click on Get username/email Attribute button.
- Paste the OAuth 2.0 Access token obtained from the OAuth provider and click on Get response.
- In the received response, copy the JSON attribute against which you are receiving the username/email of the user in the local directory and paste it into the Username/Email Attribute input field, and click on Save.
Step 5: Test REST API using access token:
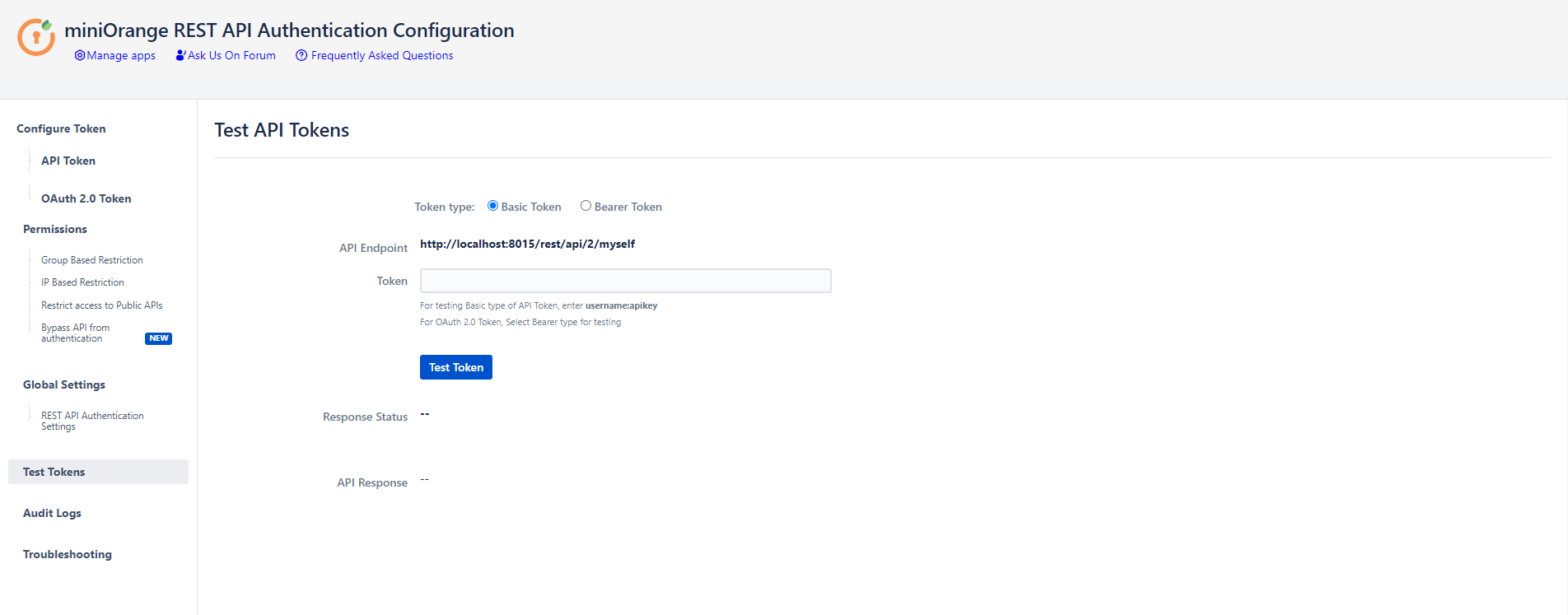
- API keys and Tokens can be tested with the Test tokens feature. Select the type - Basic/Bearer, paste the token and click on Test token button.
Click here to get a FREE TRIAL of Confluence REST API Plugin
- Call Confluence REST API endpoint. Include the access token in the Authorization header. Here’s an example of fetching content from Confluence.
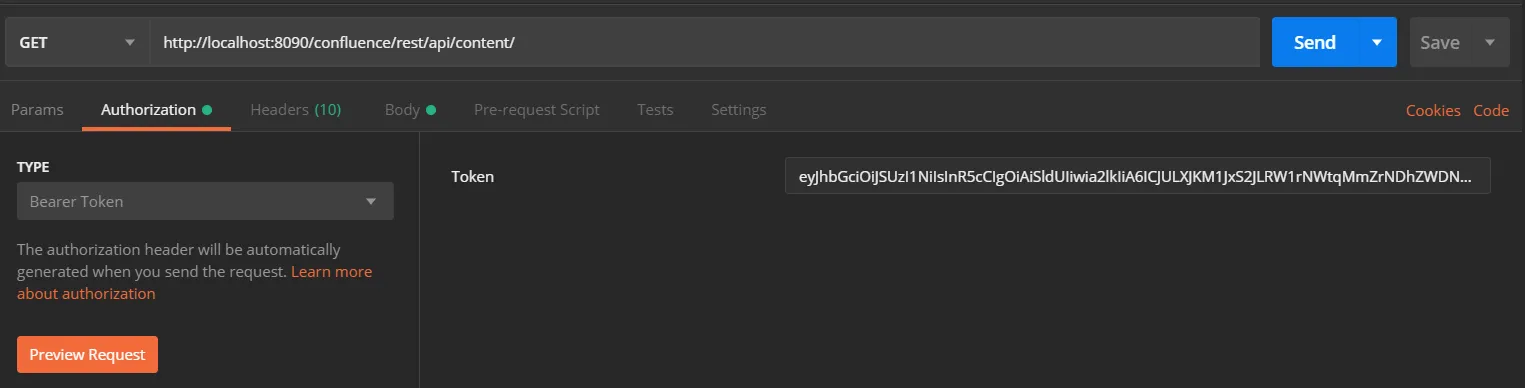
- Go to the Postman application select method type as GET and enter the Request URL. For eg. http://{Confluence_Base_URL}/confluence/rest/api/content/
- In the Authorization tab select type as Bearer Token.
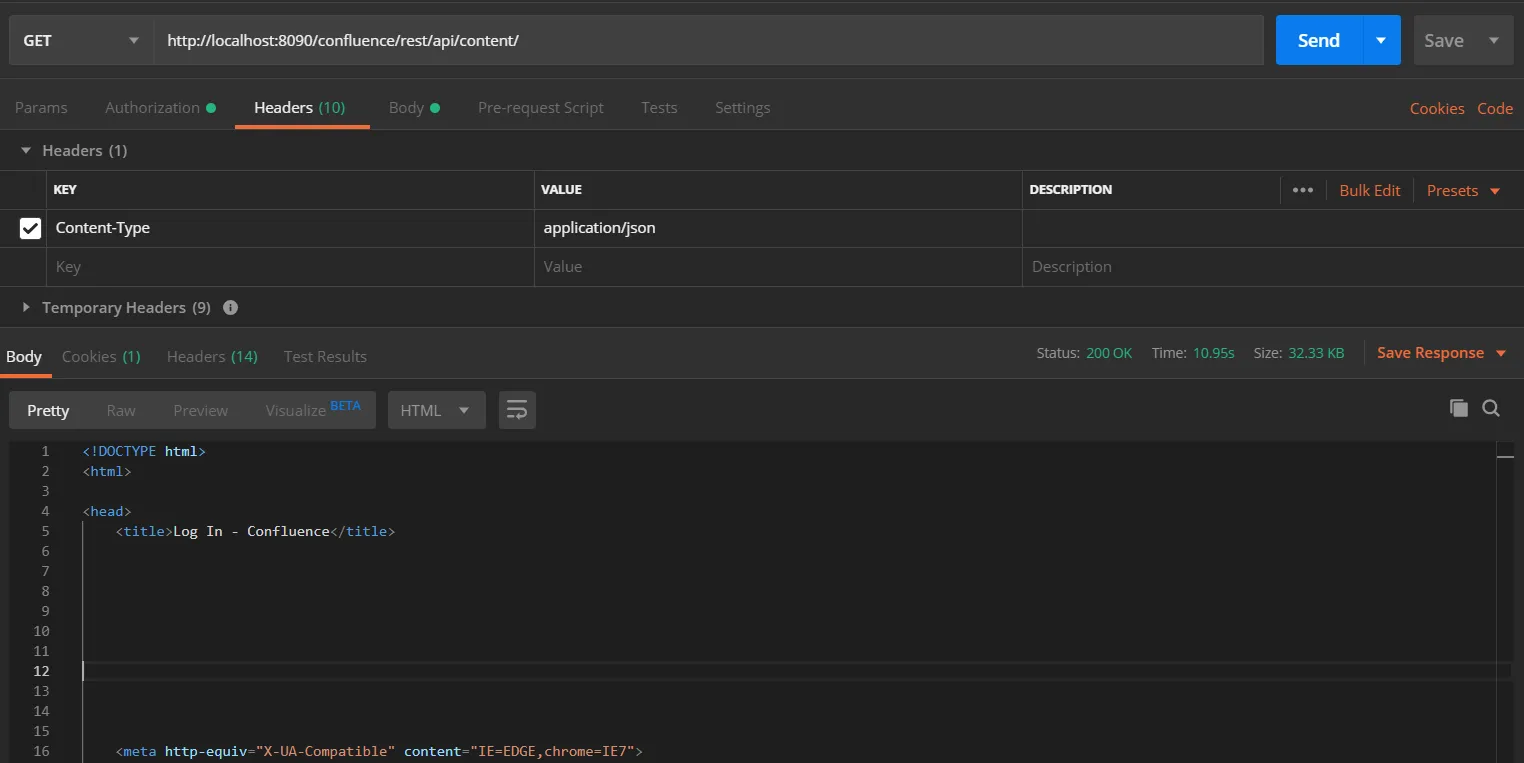
- In the Header tab add the header “content-type: application/json and send the request.
Request:
curl
-X GET
-H "Authorization: Bearer <Access Token>"
-H "Content-type: application/json"
http://{confluence_base_url}/confluence/rest/api/content/
Click here to get a FREE TRIAL of Bitbucket REST API Plugin
- Call Bitbucket REST API endpoint. Include the access token in the Authorization header. Here’s an example of fetching content from Bitbucket.
- Go to the Postman application select method type as GET and enter the Request URL. For eg. http://{Bitbucket_Base_URL}/rest/api/1.0/dashboard/pull-requests
- In the Authorization tab select type as Bearer Token.
- In the Header tab add the header “content-type: application/json and send the request.
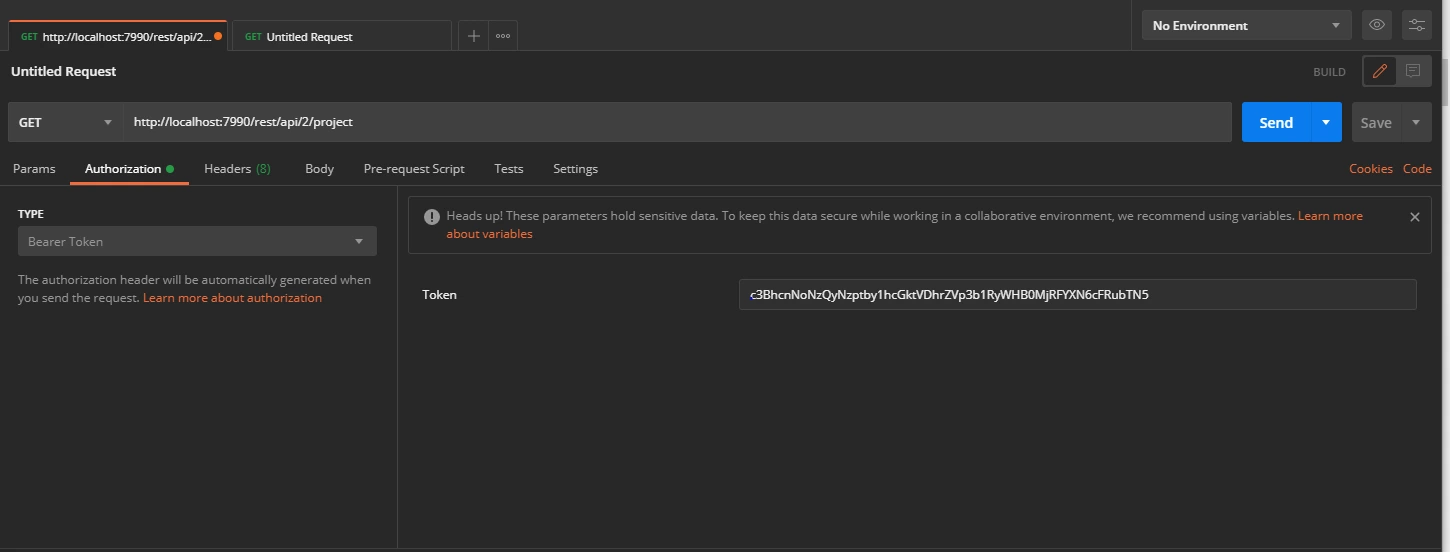
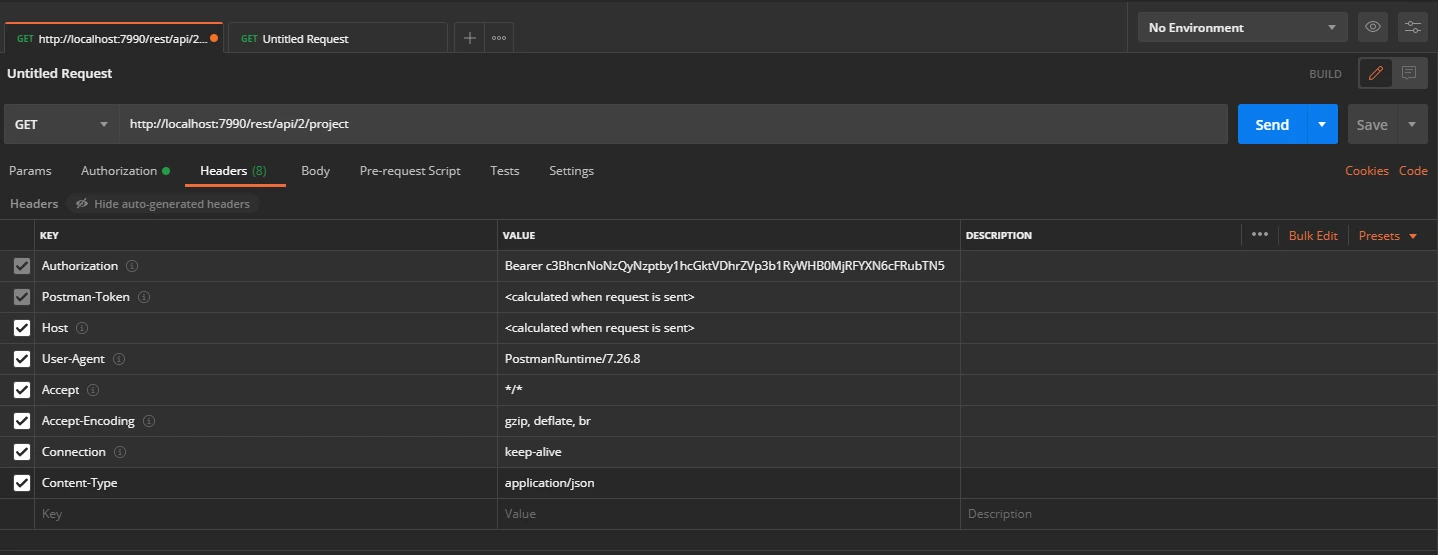
Request:
curl
-X GET
-H "Authorization: Bearer <Access Token>"
-H "Content-type: application/json"
http://{bitbucket_base_url}/rest/api/1.0/dashboard/pull-requests/
Additional Resources
Did this page help you?


 Try it for free
Try it for free