Business Challenge
The customer faces security risks due to insufficient access controls on their REST API. Without group-based and IP-based restrictions, as well as mandatory authentication for public endpoints, the APIs lack additional layers of protection.
Additionally, the enforced layer of authentication for third-party APIs complicates integrations.
These security gaps could lead to operational inefficiencies, increased risk exposure, and potential non-compliance with regulatory requirements for data protection.
Solution Overview
Our product addresses these security challenges by offering robust access control mechanisms, such as group-based and IP-based restrictions, and enforcing authentication on public endpoints while bypassing authentication for third-party APIs.
Key features include group-based access controls, IP whitelist management, and the ability to enforce authentication or bypass it for specific use cases.
The solution is currently available for Data Center.
How It Works
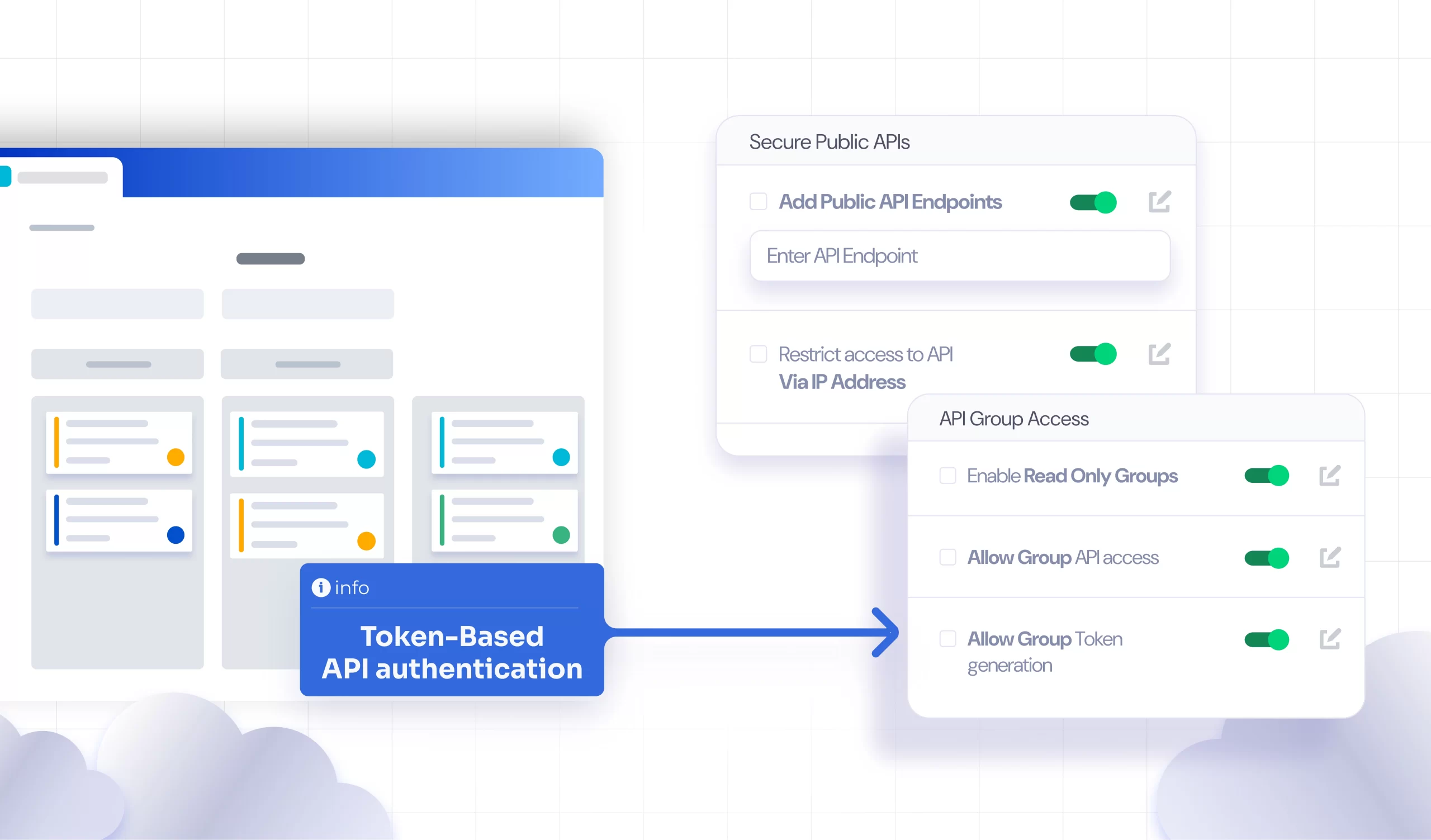
Group-Based Restriction: Administrators configure access control by assigning users to specific groups. Members of these groups are granted access to the API, while others are denied via the Authorization parameter. Certain groups may be assigned read-only access to prevent modifications.
IP-Based Restriction: Only requests from trusted IP addresses or ranges are allowed, ensuring that access is limited to authorized internal networks. The plugin has a feature to validate real client IPs, even when requests come through the proxy.
Enforcing Authentication on Public Endpoints: Public API endpoints are secured by requiring authentication for every request, ensuring that users are properly validated before accessing exposed resources.
Bypassing Authentication for Third-Party APIs: Specific third-party API endpoints are configured to bypass plugin authentication, facilitating seamless communication with external services without disruption.
Key Benefits
Secure access with seamless integrations
Granular Access Control
Group-based restrictions ensure users access only authorized data and operations, preventing unauthorized modifications and data breaches.
Mandatory Authentication for Public Endpoints
Securing public endpoints with authentication prevents unauthorized access, protecting exposed API resources.
Seamless Third-Party Integration
Authentication bypass for third-party APIs enables smooth, conflict-free integrations with external services.
Compliance with Security Standards
The implemented access controls align with best security practices, protecting against internal and external threats while ensuring easy third-party service integration.
Reduced Attack Surface
The combination of group-based restrictions, IP-based controls, and authentication for public endpoints minimizes vulnerabilities, providing robust security without disrupting user experience or external integrations.