Need Help? We are right here!
Search Results:
×






Industrial Control Systems (ICS) and SCADA environments managing critical manufacturing processes face escalating cyber threats due to legacy operating systems, default credentials, inadequate authentication mechanisms, and unencrypted proprietary protocols.
With Manufacturing being the most attacked industry in recent years, these vulnerabilities expose industrial operations to exploitation and unauthorized system manipulation. miniOrange PAM addresses these security gaps with robust manufacturing access management solutions specifically engineered for industrial environments.
Manufacturing faces a 71% surge in threat actor activity, with ransomware attacks on industrial control systems doubling since 2022, causing catastrophic production halts and millions in revenue losses.
Trusted personnel and third-party contractors with privileged access pose significant risks through credential misuse, data theft, or sabotage of critical manufacturing operations and intellectual property.
Complex global supply chains with weaker cybersecurity links enable threat actors to infiltrate manufacturing systems through trusted vendor relationships and third-party software vulnerabilities.
Industry 4.0 technologies introduce new attack surfaces through connected sensors, edge devices, and machine learning algorithms that lack robust security controls and monitoring capabilities.
Legacy industrial control systems with limited visibility, partial support, and inadequate access management create critical security gaps that cannot adapt to contemporary cybersecurity standards.
Manufacturing environments struggle with unified visibility across IT and OT systems, making it difficult to monitor privileged access activities and detect unauthorized system modifications.
Manufacturing companies face increasing compliance requirements and potential penalties while balancing operational uptime demands with stringent security controls and audit requirements.


miniOrange PAM's Just-In-Time and Just Enough Access features provide instant, temporary privileged access for critical maintenance tasks and production emergencies with automatic expiration.
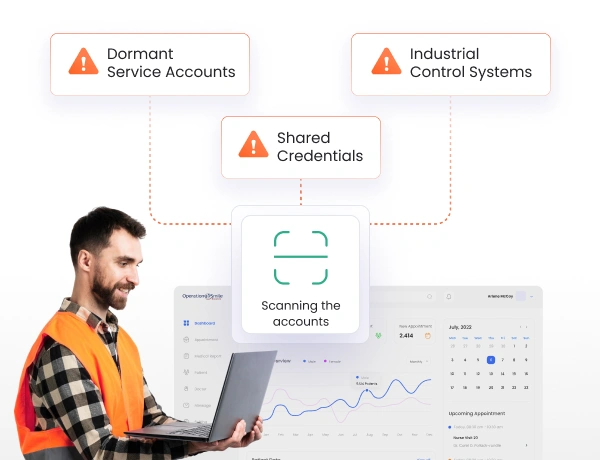
Automatic Discovery of Privileged Accounts functionality scans factory networks to identify dormant service accounts, shared credentials, and forgotten administrative access across industrial control systems.
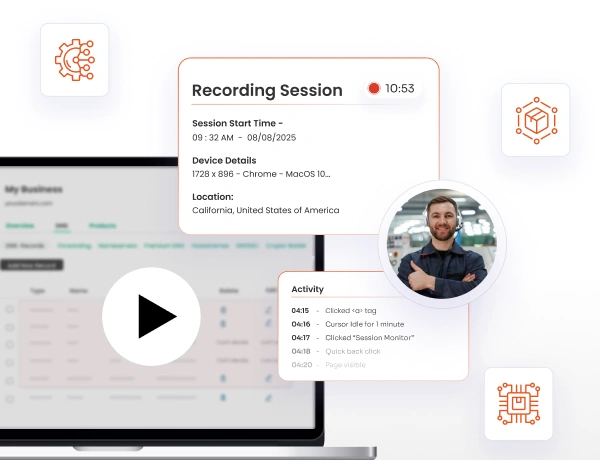
Session Monitor & Control capabilities record and stream privileged sessions on manufacturing equipment with instant termination capabilities for immediate threat response and compliance auditing.
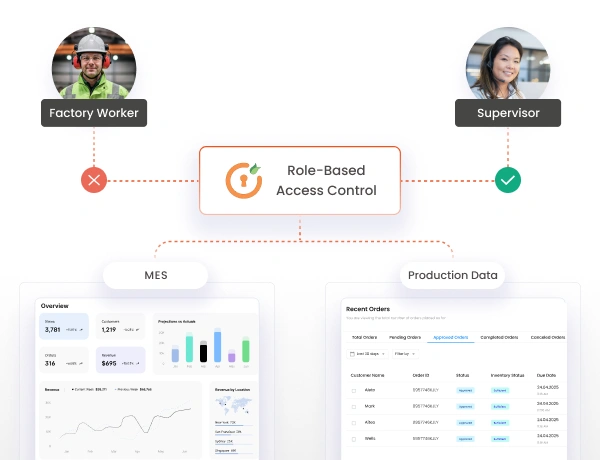
Granular Access Control implements role-based permissions for production lines, quality systems, and inventory management, ensuring operators have access only to necessary manufacturing resources with detailed restrictions.
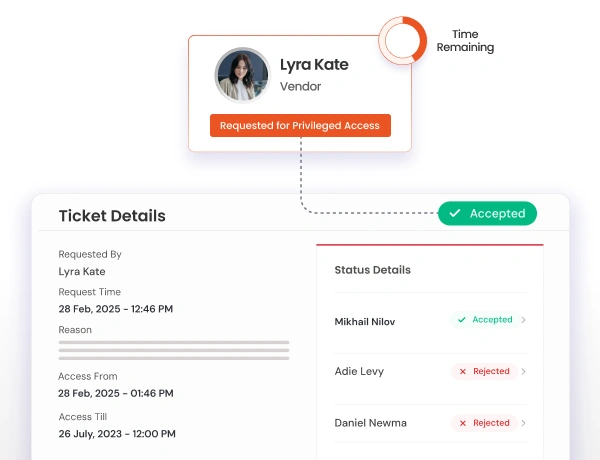
Remote Device Security protects remote connections to industrial equipment through encrypted gateways, multi-factor authentication, and controlled access for maintenance personnel and vendors.

Segregation of Duties (SOD) enforces separation between production control, quality assurance, and maintenance roles, preventing conflicts of interest and ensuring manufacturing process integrity.
miniOrange's agentless PAM architecture provides complete privileged access protection across legacy and modern industrial systems, eliminating endpoint maintenance overhead.
We offer deep customizations for industrial protocols, OT/IT convergence scenarios, and specialized manufacturing workflows ensuring seamless integration with existing production systems.
Our architecture scales effortlessly from single production lines to global manufacturing networks, maintaining consistent security policies and performance.
miniOrange PAM delivers comprehensive privileged access management at competitive pricing, making advanced security accessible for both SMB manufacturers and large industrial enterprises.
Protect intellectual property, production data, and critical systems from unauthorized access while maintaining operational integrity across manufacturing environments.
Streamline privileged access workflows, reduce downtime from security incidents, and enable secure remote operations for maintenance personnel and vendors.
Meet regulatory requirements with comprehensive audit trails, automated compliance reporting , and granular access controls that satisfy industry security standards.

Secure privileged access with complete control over data, compliance standards, and infrastructure, ideal for manufacturing facilities with strict regulatory requirements and network isolation needs.
Deploy our PAM solution through leading cloud marketplaces, including AWS, Azure, and GCP, to leverage scalable infrastructure that grows with your manufacturing operations while maintaining enterprise-grade security.

Bridge on-premise industrial control systems with cloud applications through agentless architecture, enabling seamless manufacturing privileged access management across diverse environments and remote facilities.
