Adaptive security is gaining traction in today’s market due to a steady rise in intelligence-driven security solutions such as AI and ML. The adaptive security market is expected to grow from $14.38 billion in 2025 to $32.27 billion in 2030, at a CAGR of 17.54% during the 2019 to 2030 timeframe.
The rapid shift in the adoption of the adaptive security market is due to self-learning frameworks that scrutinize threats and user behavior in real-time. Plus, regulatory mandates such as GDPR, NIS2, DORA, CCPA, etc., are driving the market growth in today’s modern organizations.
So, avail your adaptive security architecture from the best, and connect with miniOrange as your security software solution partner.
We also provide best-in-class authentication solutions such as MFA Software, Two-Factor Authentication (2FA), Single Sign-On (SSO), and more.
Explore Adaptive Authentication Now!
What is Adaptive Security?
Adaptive security is a modern cybersecurity method that continuously monitors threats. It learns from new dangers and adjusts itself automatically in real-time to keep the systems safe.
David Cearley, research vice president and Gartner Fellow, said, “Digital business is built upon an intelligent mesh of devices, software, processes, and people. This means an ever more complex world for security, demanding a continuous, contextual and coordinated approach.”
So, instead of leaning on fixed rules or waiting for a cyberattack, an adaptive network constantly monitors sessions, detects unusual activities, and reacts to them immediately.
Why Static Security isn’t Enough for Today’s Threats?
Static or traditional security tactics are made around fixed rules, predefined policies, and timely policy reviews. So, in the early days of enterprise IT and the internet, this was enough, but now the times are changing.
Traditional security falls short in today’s world because cybersecurity attacks have increased at an alarming rate.
Key reasons why static security is being replaced with a modern approach are:
- Dynamic Infrastructure: APIs, cloud computing, IoT devices, remote access, and more change security perimeters daily, making static policies outdated.
- Emerging Threats: Cybercriminals are continuously developing novel techniques, and static security systems cannot keep up with the pace.
- Integration Challenges: Businesses are continuously integrating new technologies into their systems, such as APIs, third-party apps, and more. Static security is likely to struggle to adapt to these new technologies, leaving security loopholes.
- Delayed Responses: Static security reacts only after an incident, resulting in greater damage and a longer breach window.
What are the Core Objectives of Adaptive Network Security?
The three core objectives of adaptive network security are as follows:
Continuous Monitoring and Threat Prediction
Adaptive cybersecurity constantly scans the network, gathering and analyzing data on devices, users, apps, and traffic patterns. This approach helps to identify suspicious activities early.
With pattern recognition and advanced analytical techniques (using AI tools), adaptive security can predict where the next breach might occur and who will be the likely vectors. This helps the organizations to take preventive measures beforehand.
Real-Time Policy Adjustment
This is one of the powerful facets of adaptive security operations. As soon as a new threat is detected, policies can be altered without any manual intervention.
Network systems can automatically relax or tighten the access control, enable additional authentication methods, block traffic, or completely isolate vulnerable systems.
These abilities reduce human errors and close the gaps that hackers may exploit during policy reviews or after changing an IT infrastructure.
Adaptive Trust Enforcement
Here, trust is dynamically enforced, based on risk analysis and real-time context, rather than on preset, static conditions. For instance, if a user tries to access any sensitive information outside business hours or from an unusual source, adaptive technology can send a prompt to block the access or ask for additional authentication.
Due to these scenarios, trust is no longer a fixed aspect, but it's constantly re-evaluated and measured based on the context, behavior, and risk profiles of every entity.
Experience Passwordless Authentication in Action
Adaptive Security Architecture Explained
Here’s what you need to know about architecture.
The 4-Stage Model: Prevent, Detect, Respond, and Predict
The four-stage model comes from a 2017 Gartner insight, which is as follows:
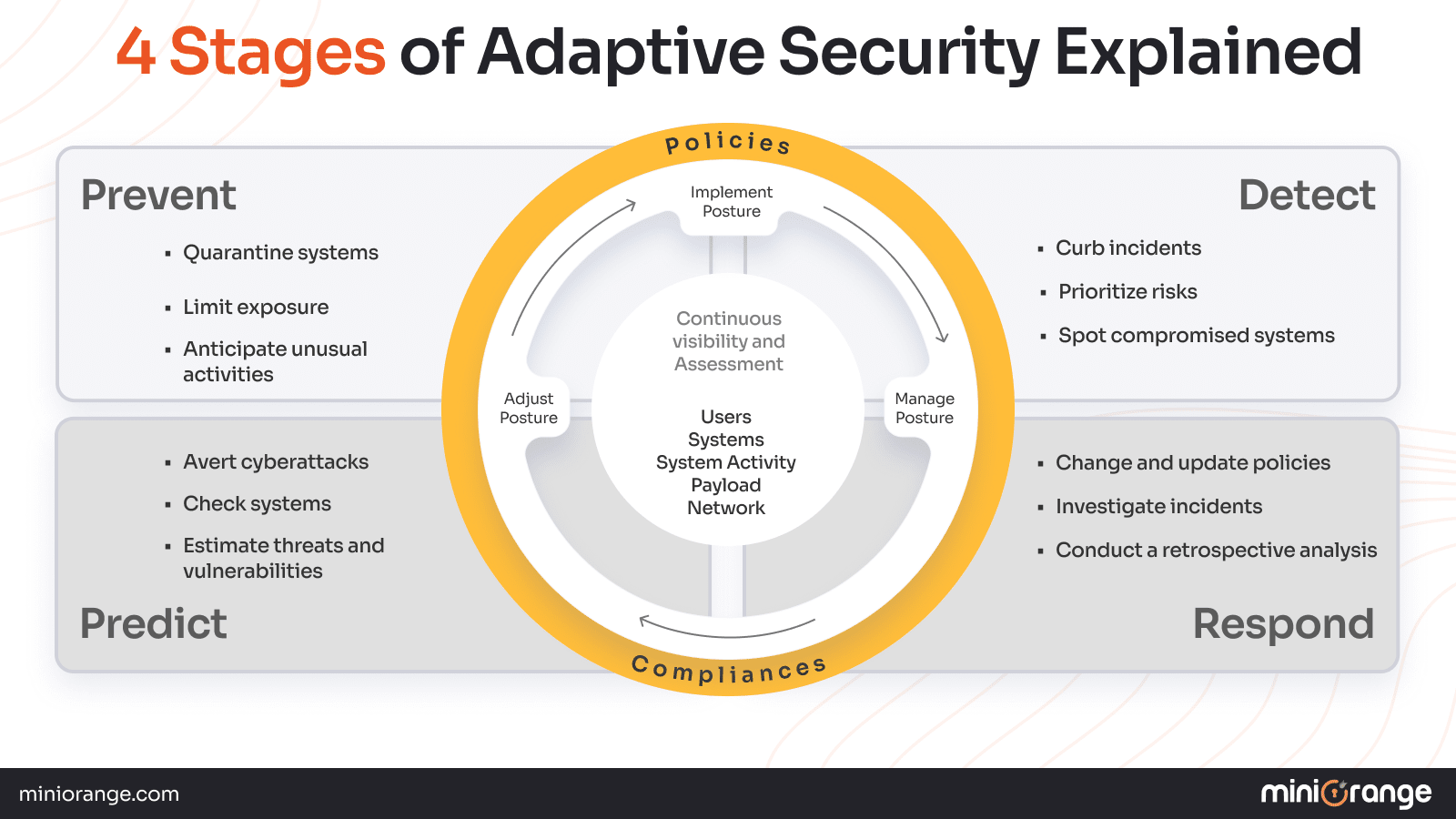
Prevent
This is the first step for organizations to create processes, products, and policies to avoid cyberattacks. Measures are undertaken to avoid incidents and decrease vulnerabilities beforehand. For instance, using zero trust network access control to avoid data breaches. Also, making use of MFA authentication methods such as OTP or push notification to curb unauthorized access.
Detect
Here, threats are detected and reported, which are later managed by the cybersecurity professionals.
This encompasses anomaly detection in cybersecurity networks, behavioral dynamic code analyzers, and analytic systems. This is to decrease the time taken to prevent suspicious attacks from escalating.
Respond
The most logical step in the entire adaptive security architecture. Things such as what actions need to be taken and how to respond to certain threats are defined.
Specific responses include designing policy changes, investigating cybercriminal scenes, and retrospective analysis.
Predict
In this step, probable risks are identified through risk analysis and estimating attack vectors. For instance, evaluating dark web traffic to anticipate the sale or distribution of stolen usernames and passwords. Or, using artificial intelligence to spot unusual behavior.
The above four-stage approach ascertains that adaptive cybersecurity doesn’t just wait for data breaches to happen; it strives to stay several steps ahead.
Role of AI and Automation in Adaptive Security
Artificial Intelligence and automation play a crucial role in adaptive security operations. Machine learning, a branch of AI, analyzes network and endpoint telemetry data, learning what is normal and what’s not. It also flags or automatically takes action on cyber incidents.
Furthermore, automation technology speeds up everything from anomaly detection to response. For example, a network system can auto-quarantine a compromised endpoint and revoke privileges if needed. Plus, multi-factor authentication (MFA) can be implemented in case access seems suspicious and also before a threat amplifies.
The synergy of automation and artificial intelligence maintains accuracy, around-the-clock protection, and speed, which goes beyond the capacity of the best human IT staff.
Learn How to Select the Best Multi-Factor Authentication Types
How to Implement Adaptive Security Architecture?
Businesses can use adaptive cybersecurity irrespective of their nature, size, and vertical, or the type of cybersecurity threats they face. Adaptive security architecture can grow and evolve as per the business’s policies and processes.
These are the steps to follow while using adaptive security:
- Detects threats and their patterns that should be mitigated or averted completely.
- Define components, behaviors, or actions that must not be mistaken for threats.
- Establish triggers to monitor threats, and set up a response mechanism.
- Can enforce the redundancy rule for critical operations.
- Make sure that crucial and trusted elements do not compromise the entire system.
- Threat responses should not hamper the system’s integrity.
- Set up a solid recovery process.
- Lastly, conduct a feedback phase that verifies the response.
It’s essential to establish clear guidelines, train the security teams, and assure that the tools can upscale with the changing cybersecurity landscape.
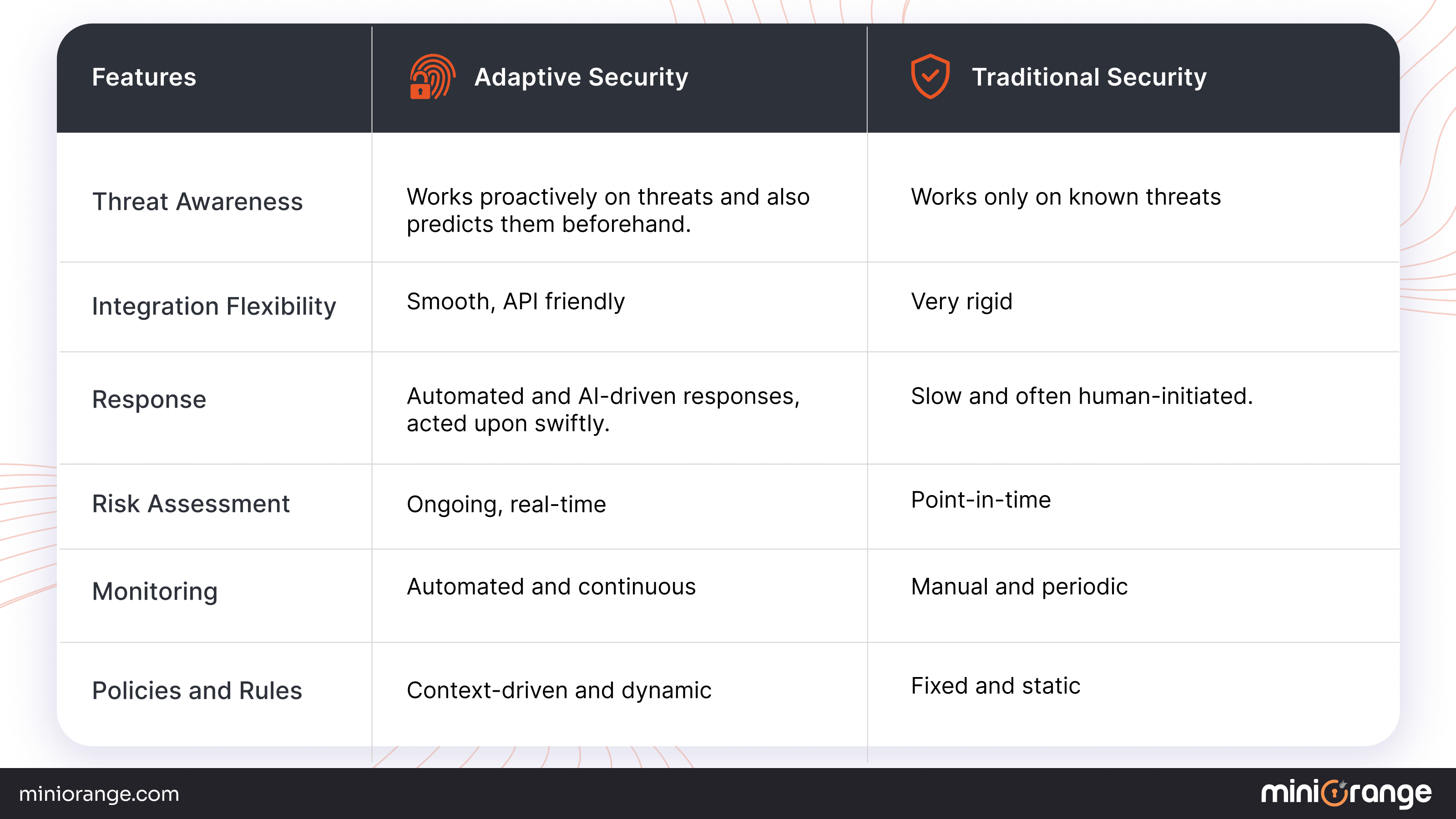
Adaptive Security vs. Traditional Security
Key differences between adaptive security and traditional security can be summarized as follows:
Key Layers of Adaptive Security
Adaptive security architecture consists of layers that play a crucial role in multi-layered protection. These are as follows:
Network Behavior Analysis
Adaptive cybersecurity constantly monitors security at the network level. It evaluates traffic flow, device communication, and access patterns, searching for abnormal activities such as port scans, data transfers, or unusual device connections.
So, by relating different data sources, it can flag insider threats, DDoS attacks, or lateral movements.
Identity and Access Control
Identity is the core of zero trust architecture. The adaptive security framework is used to verify users and enforce risk-based access control.
For example, access privileges can change based on location, user behavior, threat intelligence, and device health. Adaptive MFA helps to raise security needs when the risks escalate.
Encryption and Data Protection
Data is constantly encrypted, both in transit and at rest, but adaptive security goes a notch higher: it imposes encryption keys and rotates credentials automatically in case any vulnerability is spotted. It also restricts data based on sensitivity or context.
Endpoint Security
Endpoints such as mobile phones, laptops, IoT, access points, and more are protected from harmful entities in real-time.
If an endpoint deviates from normal behavior, such as connecting to malicious domains or running unauthorized access, then adaptive controls can quarantine the devices and revoke access.
SIEM and Analytics
Security Information and Event Management (SIEM) and analytics combine all the layers.
They aggregate alerts, logs, behavioral data, and threat intelligence, and then predict, detect, and respond to threats with accuracy and speed.
Features of Adaptive Security Systems
Adaptive security platform delivers five essential features, which are as follows:
Dynamic Risk Assessment
Risk scores are calculated for devices, users, and processes based on threats, behavioral analytics, and contextual data.
These scores trigger adaptive measures such as limiting privileges and permissions and amplifying authentication requirements (mandatory MFA authentication).
Automated Threat Response
In today’s time, relying on humans alone for managing threat responses isn’t enough.
Automation has become a huge part of today’s security system, including adaptive systems. This technology detects, investigates, and mitigates threats with accuracy, minimizing damage.
Compliance and Policy Management
Adaptive systems automate regulatory compliance policies by constantly monitoring compliance violations.
Furthermore, policies are enforced in real-time, and reports and audit logs are created. These logs are quite helpful in scanning for missed threats or future possibilities of vulnerabilities.
Easy Integration
Adaptive security systems are developed on APIs and open standards, which support cloud-based applications and Identity and Access Management (IAM) tools.
IAM solutions include Single Sign-On (SSO), Two-Factor Authentication (2FA), MFA, Privileged Access Management (PAM), and more. This consolidated integration strategy helps to strengthen the defenses.
Scalability and Agility
With businesses skyrocketing, they need security solutions that scale and are flexible.
Adaptive security scales extensively, making it an ideal solution for expanding workforces, dynamic IT systems, and hybrid cloud workloads.
Design Your Access Security Blueprint: In-Depth 2FA vs. MFA Comparison
What are the Benefits of Adaptive Security?
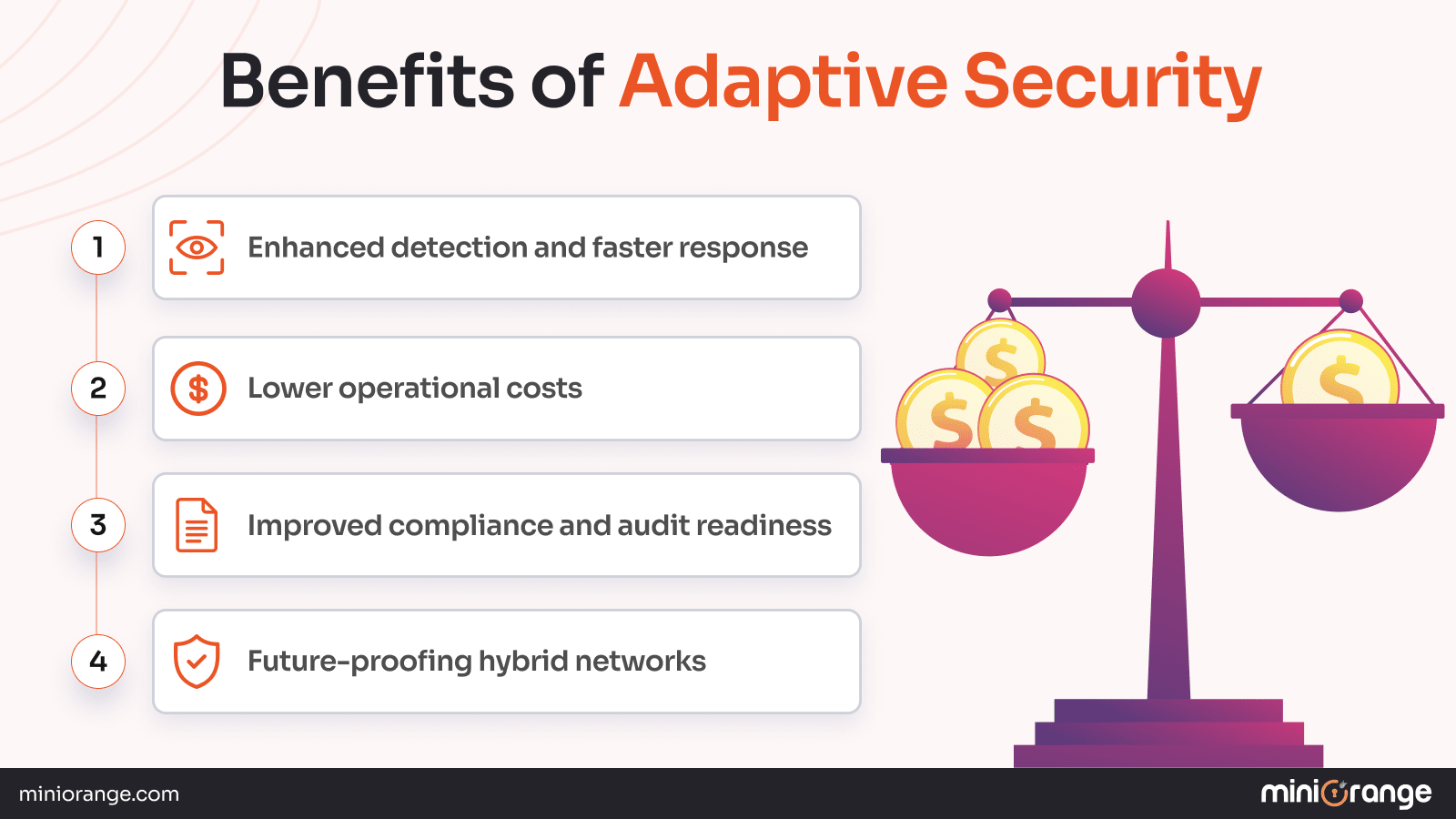
Accurate Threat Detection and Fast Response
Monitor networks and systems continuously so threats are detected very early, before any major damage occurs. This minimizes the time hackers can attack unseen.
For example, adaptive security analyzes all the login attempts, and in case of unusual activity, the system automatically flags and blocks these activities. The response is much faster than a human security team.
Lower Operational Costs
Little to no time is spent on manual alert triage and repetitive, low-level tasks.
With reduced human workload, the security teams can spend time on other complex tasks, such as improvements in the existing security system and overseeing the maintenance activities.
Improved Compliance and Audit Readiness
Aspects such as automated policy enforcement, real-time monitoring, and user logs help to meet regulatory compliance requirements such as HIPAA, GDPR, etc.
Logging every user action aids in creating audit-ready reports, which supports the user’s privacy and compliance mandates. Further, stringent authentication helps in out-of-hours user access.
Future-Proofing Hybrid Networks
Protect hybrid networks without the need for manual configuration when new users or systems are added.
For example, as businesses migrate to cloud and hybrid networks, adaptive security automates safety protocols for new apps and services as soon as they are deployed.
So, when a developer introduces a third-party SaaS application, the adaptive system scans for vulnerabilities and immediately updates policies.
Adaptive Security in Action
Adaptive MFA Explained
Adaptive MFA alters authentication requirements based on the context of every login attempt.
For example, if a user logs in from an unknown device and from an unfamiliar location, showing suspicious behavior, then adaptive MFA is triggered.
The user is required to verify themselves with additional authentication steps or block the login attempt entirely, without affecting the legitimate users.
Adaptive Network and Mobile Security
Adaptive network security is applied to VPN, Wi-Fi, and cloud solutions to establish secure remote access. These are tracked for any weird activities or behavior patterns, and real-time protections are implemented.
For adaptive mobile security, AI-based solutions check apps, device integrity, and user behavior. In case any anomaly is spotted, then the entire device is either wiped clean or locked down.
What are the Real-World Examples and Use Cases?
A few of the real-world examples are:
- Cloud Protection: If a third-party device or service is integrated, then the system scans for vulnerabilities, tracks for unauthorized access, and updates policies in real-time.
- API Security in E-Commerce: Detects unfamiliar API activities, such as data scraping or credential theft, automatically blocking or limiting access before infiltration.
- Financial Institutions: Constant analysis helps to mitigate insider threats, fraud, and scams.
Implementing Adaptive Security in Your Organization
A successful adaptive security rollout involves careful planning, execution, and continuous refinement. Key steps include:
Assess Your Existing Posture
- Detect weaknesses in response abilities.
- List out user roles, digital assets, and current security controls.
Choose the Right Adaptive Tools
- Select tools that are compatible with the organization’s infrastructure.
- Make sure that the tool supports ML, open-source APIs, and automation.
Develop Team Protocols and Training
- Train the security staff on automation, adaptive tools, and threat responses.
- Establish processes for amplifying threats spotted by the automation tools.
Establish Continuous Improvement Loops
- Feedback helps to refine detection models, risk assessments, and response playbooks.
- Update and review policies, and check for malicious activities periodically, so the adaptive tools evolve with the growing cybercrimes.
How miniOrange Implements Adaptive Security?
miniOrange specializes in Identity and Access Management (IAM) solutions, and it offers a comprehensive suite of adaptive security solutions, including MFA, developed to deliver context-driven safety for enterprises.
miniOrange offers AI- and ML-based risk assessments to change MFA methods in real-time to deter potential attackers. Furthermore, our compliance policies are customized to suit users’ needs and risks.
Know about 15+ MFA methods offered by miniOrange, and set up a free MFA trial today!
Conclusion
Adaptive security is not simply a technical upgrade but a fundamental shift in how organizations approach cybersecurity.
By integrating context based authentication, adaptive security continuously evaluates user behavior, device posture, and access patterns to ensure only legitimate users gain entry, significantly reducing the risk of unauthorized access. Through continuous monitoring, AI driven analytics, and automated response, adaptive security transcends the limitations of static reactive defense models, offering protection that is as dynamic as the threats themselves.
As attack surfaces expand and cybercriminals evolve their tactics, adaptive security empowers organizations to protect websites from hackers, ensuring agility, resilience, and proactive defense against ever changing cyber threats.
Get in touch with us to upgrade your security standards now
FAQs
How is adaptive security different from traditional security?
Adaptive security offers automated, AI-driven, and continuous protection by monitoring, tracking, and responding to new attacks in real-time. Whereas traditional security depends on fixed rules and periodic updates, leaving loopholes for hackers to breach the system.
What are the benefits of adaptive MFA?
Benefits include context-based authentication and scalability, accelerating security during risky situations.
Can adaptive security protect mobile and cloud applications?
Yes, adaptive tools are developed to safeguard against mobile and cloud attacks through real-time tracking.
How does adaptive security support compliance?
It automates the policies and compliance status constantly and maintains reports and logs.



Leave a Comment