Need Help? We are right here!
Search Results:
×






Healthcare is the #1 target of cybercriminals due to the value of patient data.
Average healthcare breach costs $10.9M per incident (IBM, 2023).
83% of medical imaging devices run outdated OS like Windows 7 (Palo Alto Networks).
58% of healthcare breaches come from insiders - higher than any other industry (Verizon).
Hospitals and clinics need PAM to control privileged access across EHRs, IoMT devices, and patient records - while ensuring HIPAA compliance and uninterrupted patient care.
Healthcare organizations store protected health information, making them prime targets for cybercriminals seeking valuable patient data.
Medical devices like infusion pumps and heart monitors often lack proper security controls, creating vulnerable network entry points.
Many medical devices run outdated operating systems, while BYOD policies introduce non-compliant devices into secure healthcare environments.
The healthcare sector faces targeted ransomware attacks that can disrupt life-saving services and compromise critical patient care operations.
Employees, contractors, and vendors with privileged access can intentionally or unintentionally misuse permissions, causing data breaches.
Healthcare organizations must meet strict HIPAA and regulatory requirements to avoid severe financial penalties and reputational damage.

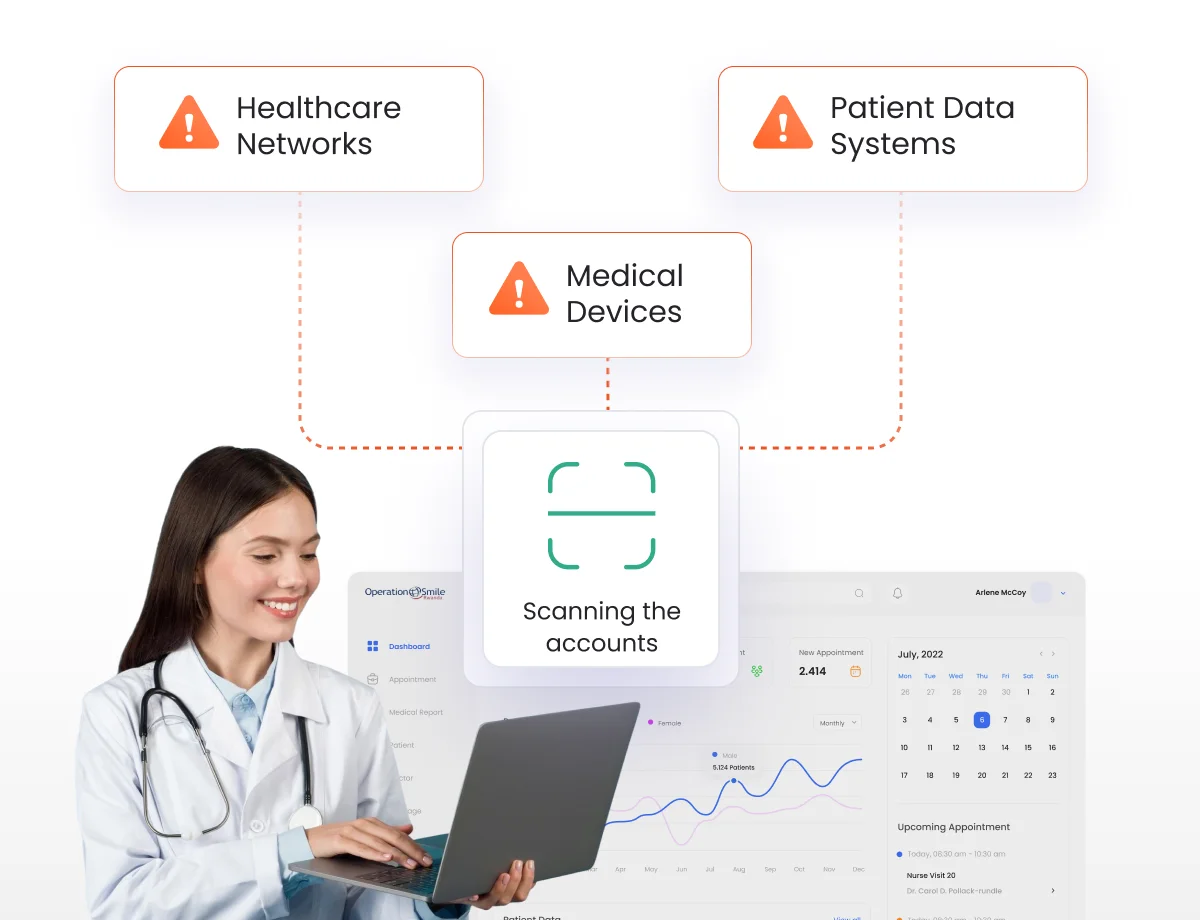
Automatically identify and catalog all privileged accounts across healthcare networks, medical devices, and patient data systems.
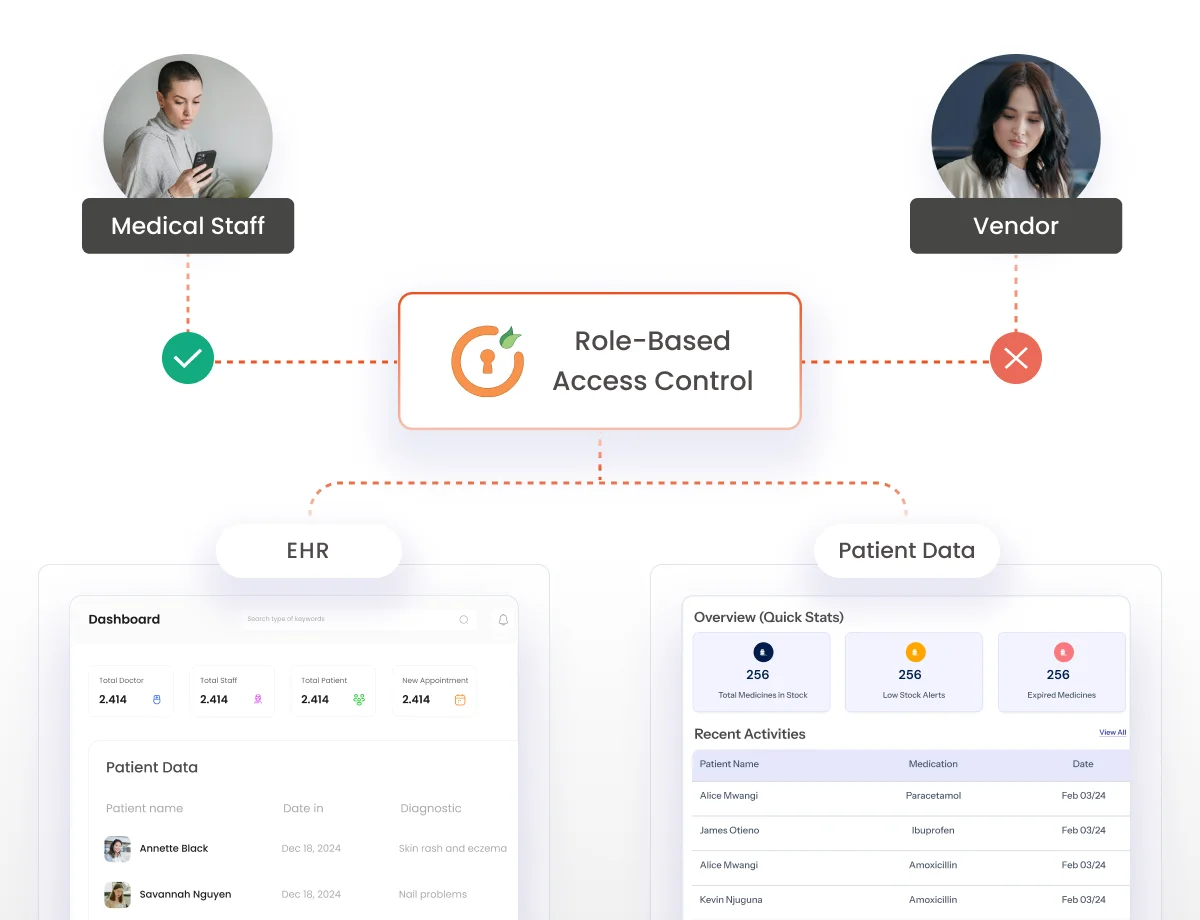
Define precise access permissions for medical staff, administrators, & vendors based on roles and patient care requirements.
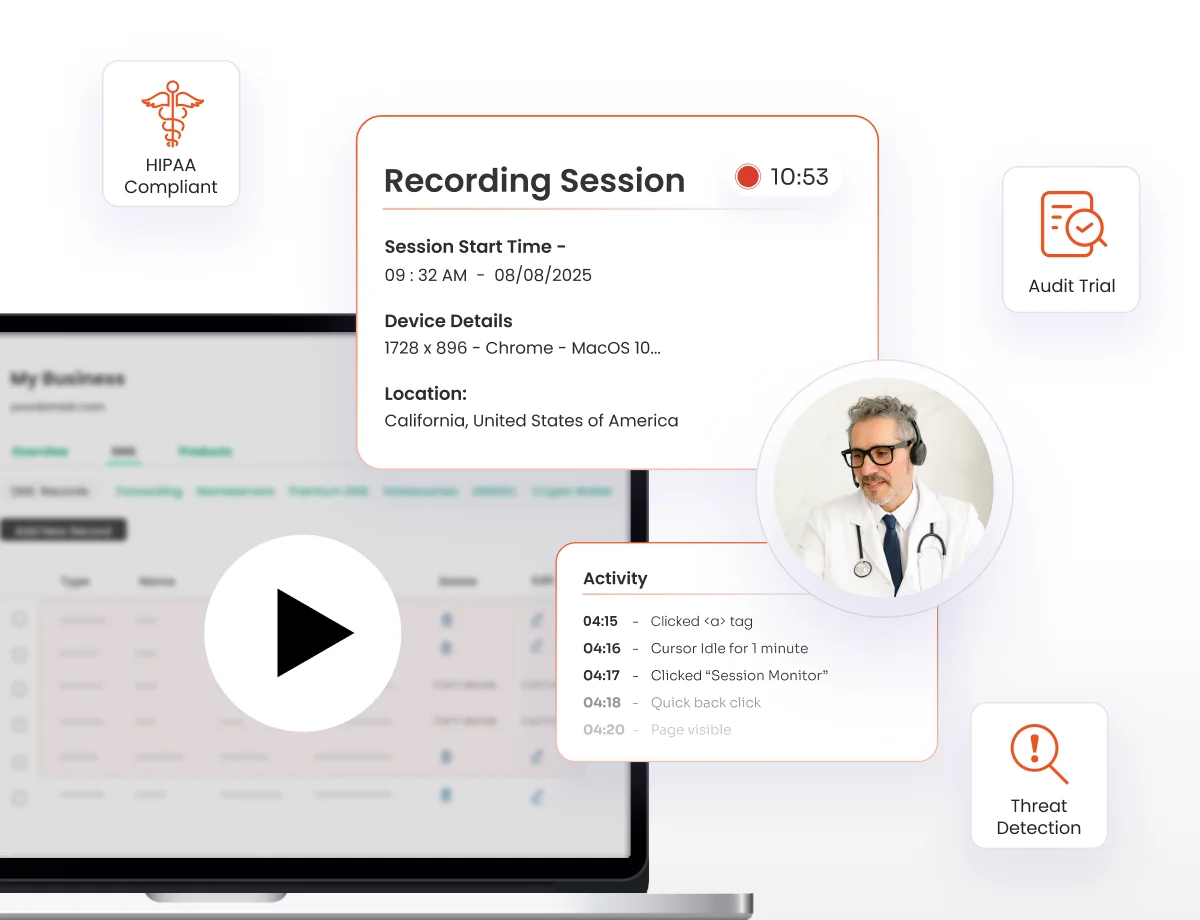
Real-time session monitoring of all privileged sessions for HIPAA compliance, audit trails, and real-time threat detection capabilities.
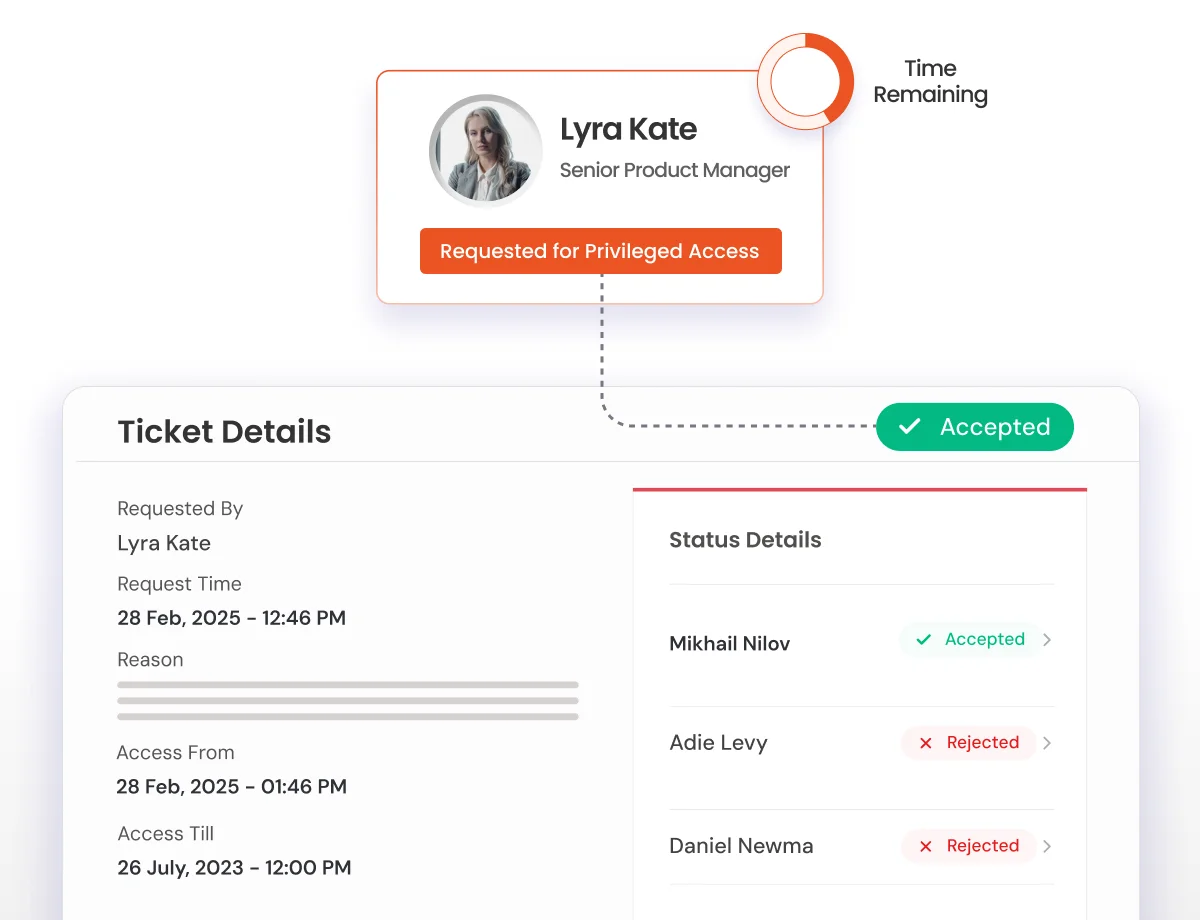
Provide secure, time-bound access for telehealth providers, medical device vendors, and external healthcare service partners.
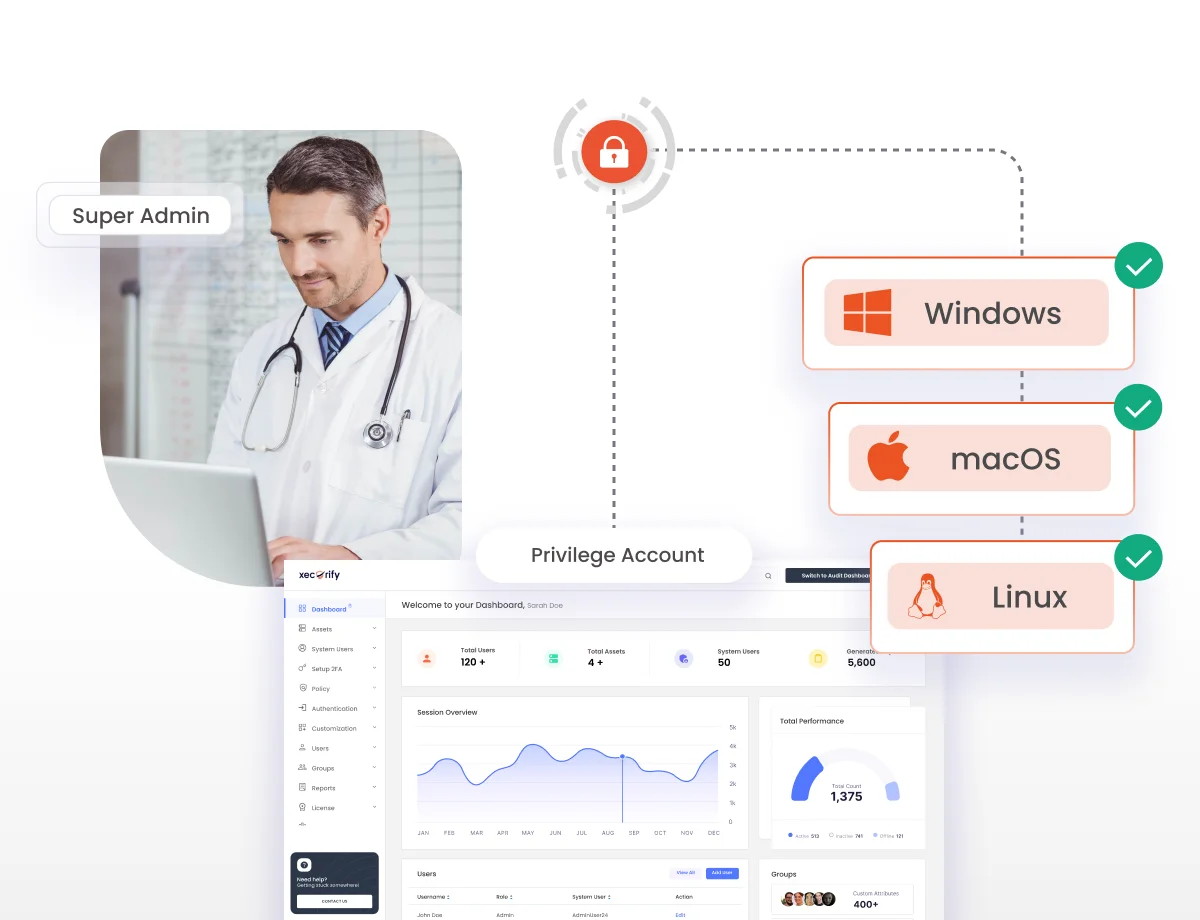
Centrally manage and secure all healthcare endpoints, including workstations, medical devices, and mobile clinical computing systems.
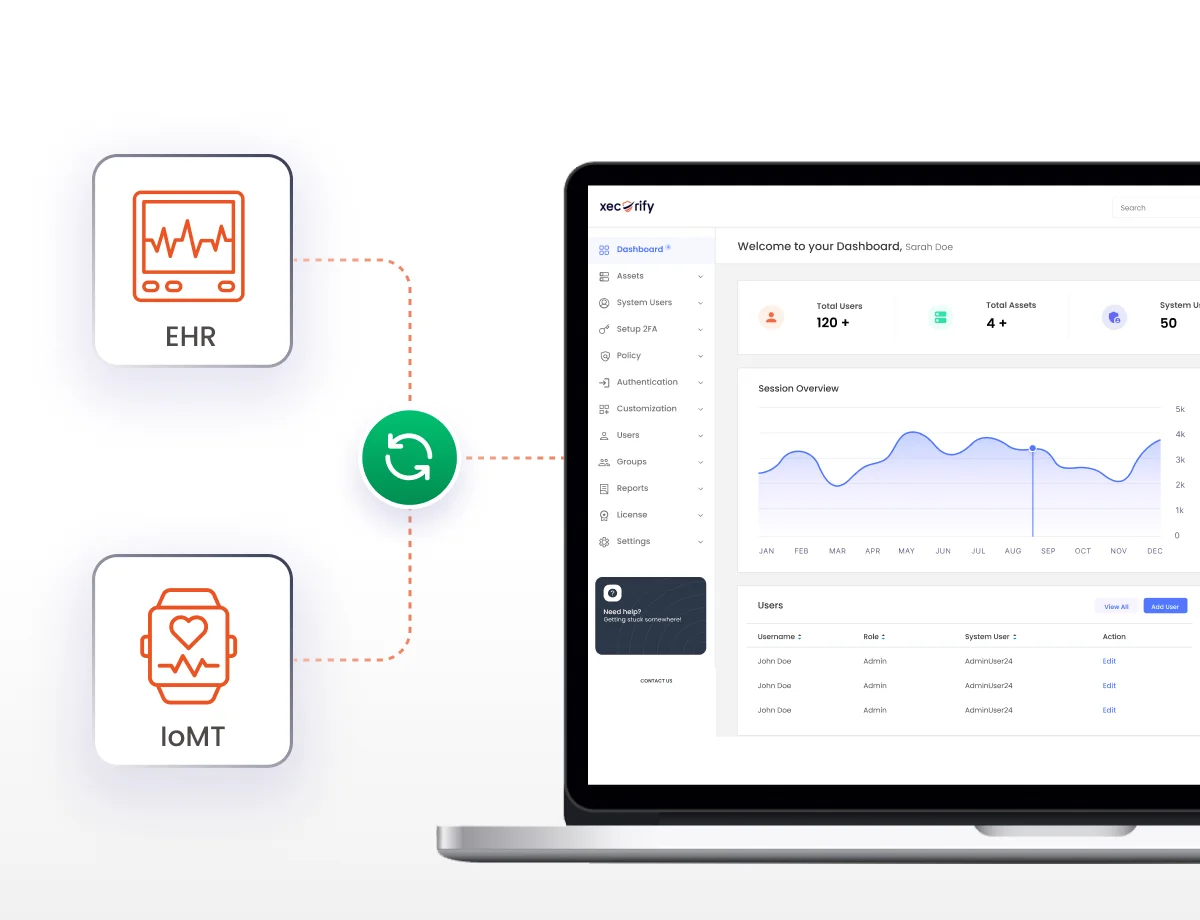
Seamlessly integrate with existing EHR systems, medical IoT devices, and healthcare applications for unified access management.
Deploy without installing agents on endpoints, reducing complexity and maintenance overhead for healthcare IT teams.
Scalable pricing tiers designed for healthcare organizations, from small clinics to enterprise hospital networks.
Adapt PAM solutions to unique healthcare workflows, regulatory needs, and organizational security policies.
Continuous support to ensure uninterrupted access, faster issue resolution, and continuous protection of sensitive healthcare data.
Protect sensitive PHI with granular access controls, encryption, and audit trails, ensuring patient privacy and data integrity.
Meet HIPAA, HITECH, and regulatory requirements with comprehensive audit trails, access controls, and automated compliance reporting features.
Streamline privileged access workflows, automate password rotations, and reduce administrative overhead for healthcare IT staff members.

Deploy PAM within your local infrastructure or on-premise systems, ensuring secure EHRs & medical devices inside hospital networks.
Implement PAM in cloud environments for scalable, secure access management across remote healthcare facilities and cloud-based applications.

Unify PAM across both cloud and on-premise infrastructures, delivering consistent security and access controls for all healthcare operations.
