Need Help? We are right here!
Search Results:
×SAP systems like S/4HANA manage an organization's most sensitive data, including financial records, customer information, employee details, and intellectual property. With ransomware attacks targeting SAP systems surging by 400% in recent years, securing administrative and high-level access to these systems has become mission-critical.
Privileged Access Management (PAM) protects cloud, on-premise, and hybrid SAP environments by enforcing the Principle of Least Privilege. Credentials are granted only when needed and for fixed durations, without disclosing the actual password to end users, thereby reducing the risk of security breaches.
PAM for SAP systems also provides detailed logging, recording, and tracking of privileged activities, which is essential for audits and regulatory compliance.







miniOrange PAM automatically identifies all privileged, service, and technical accounts across your SAP landscape, providing complete visibility into who has elevated access. This comprehensive discovery eliminates security blind spots and establishes a foundation for privileged access governance.
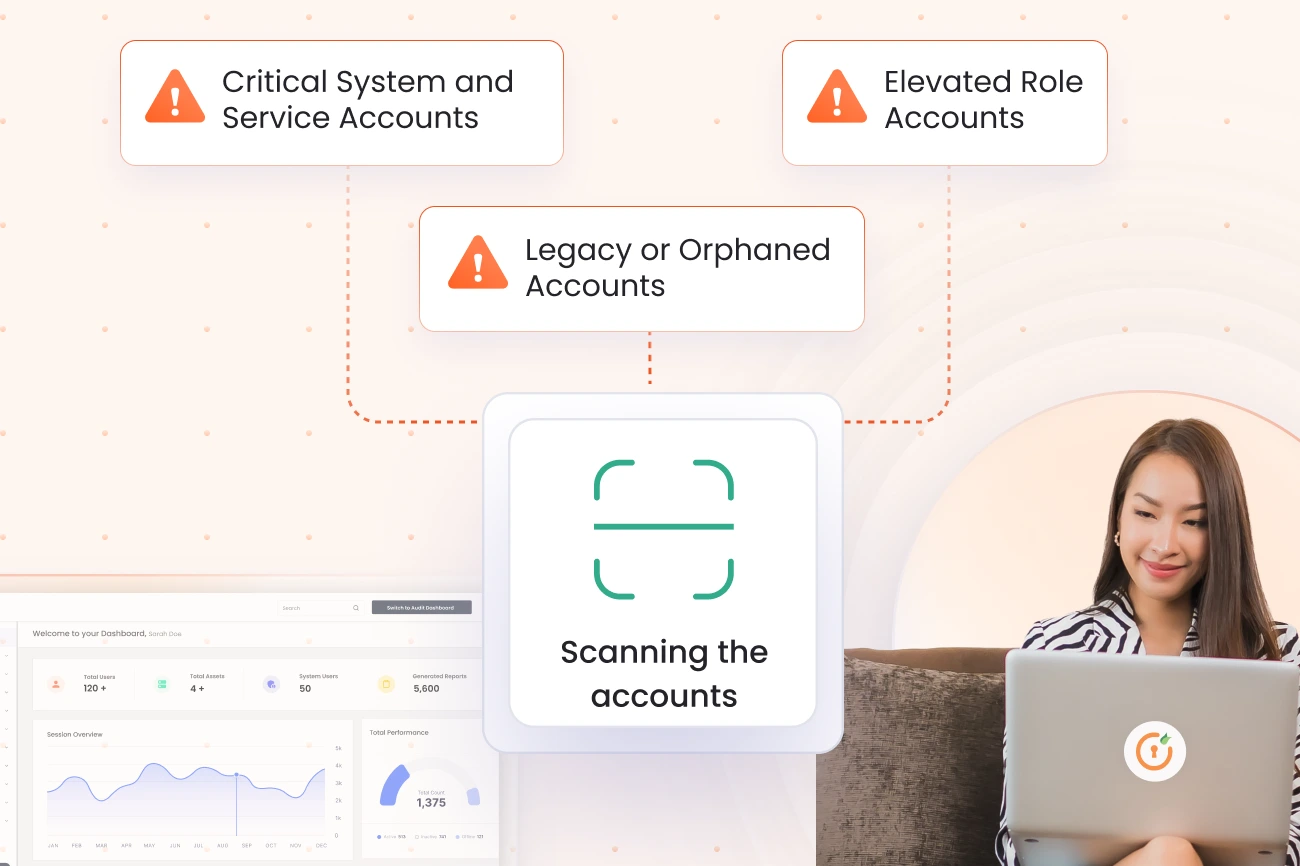
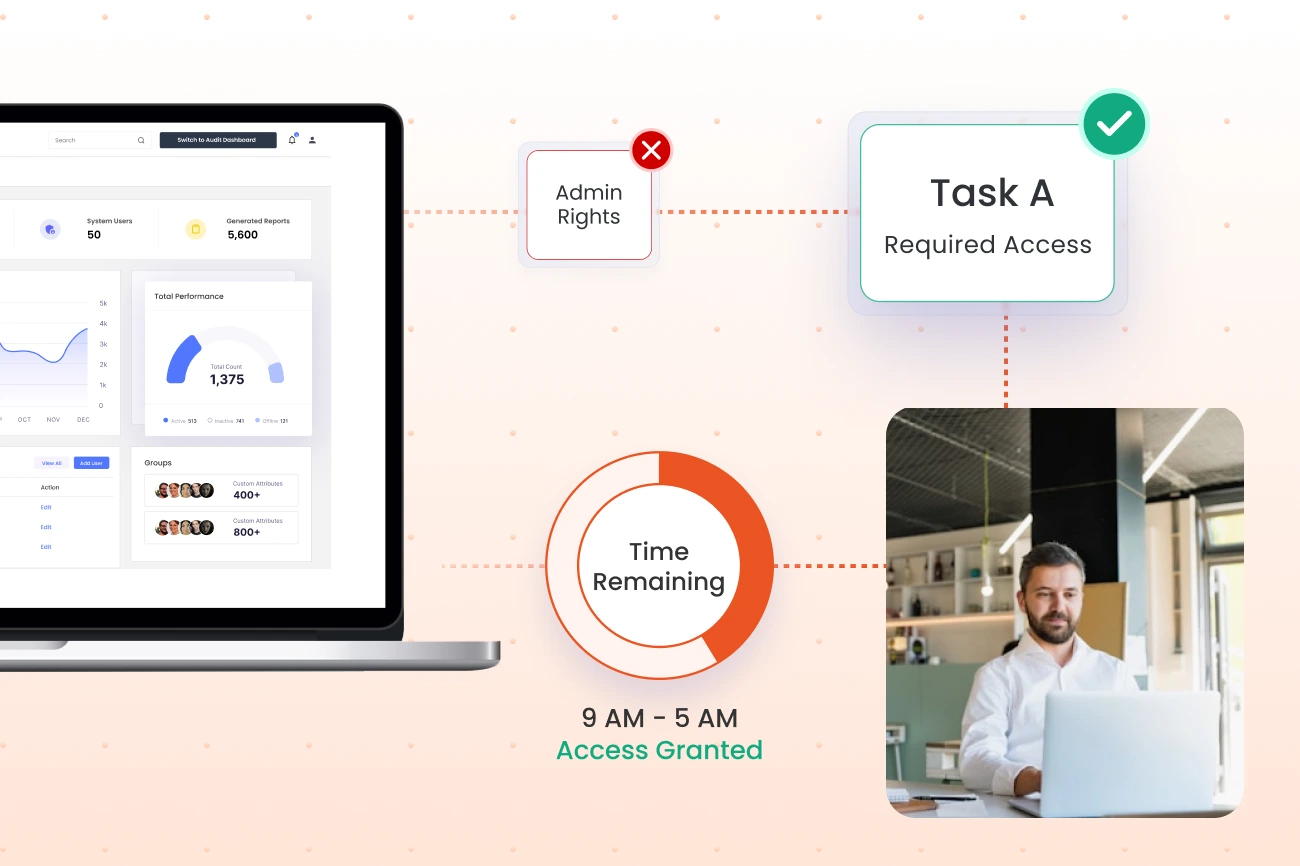
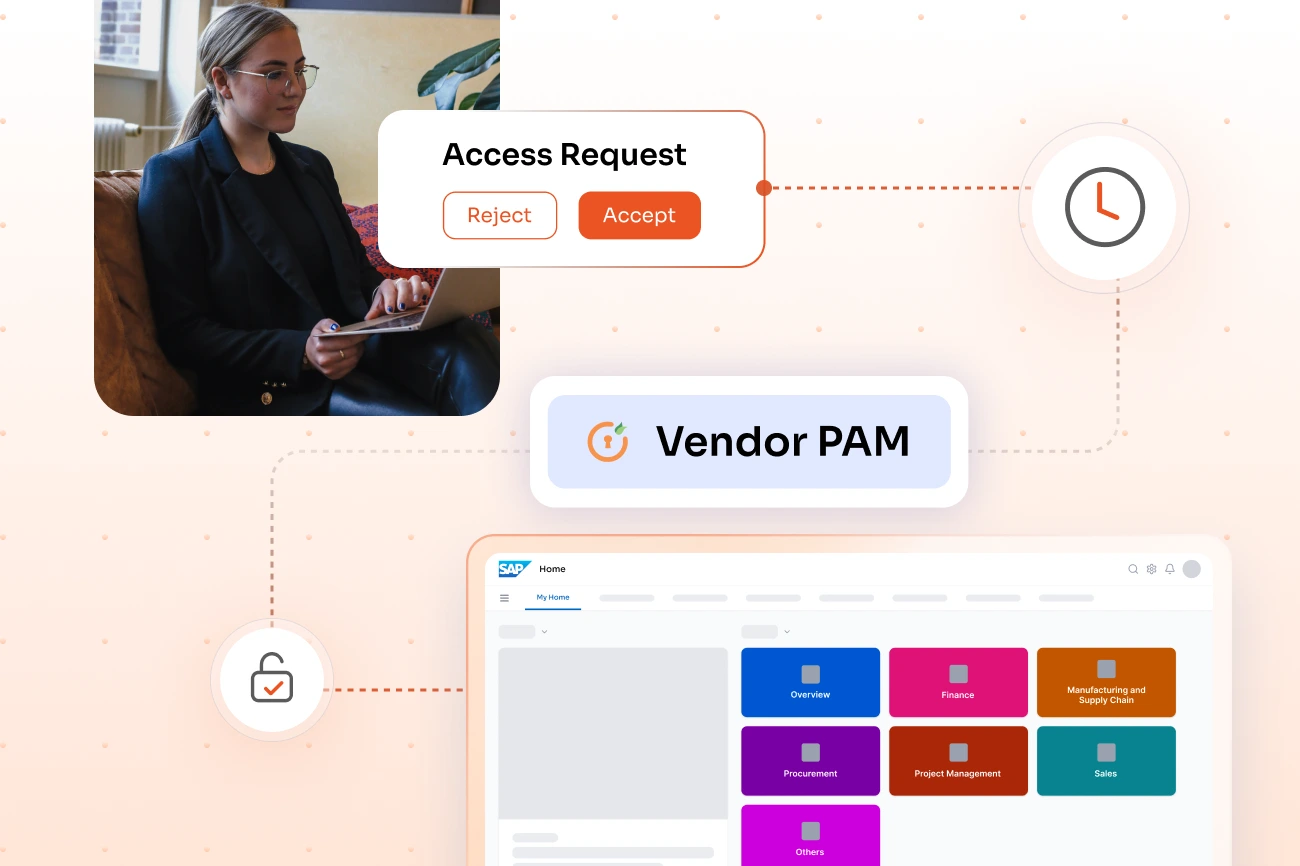
Users receive only the minimum privileges required to complete their specific tasks in SAP systems, granted on demand for limited durations. Approval workflows ensure every privileged access request is authorized and time-bound, preventing standing privileges.
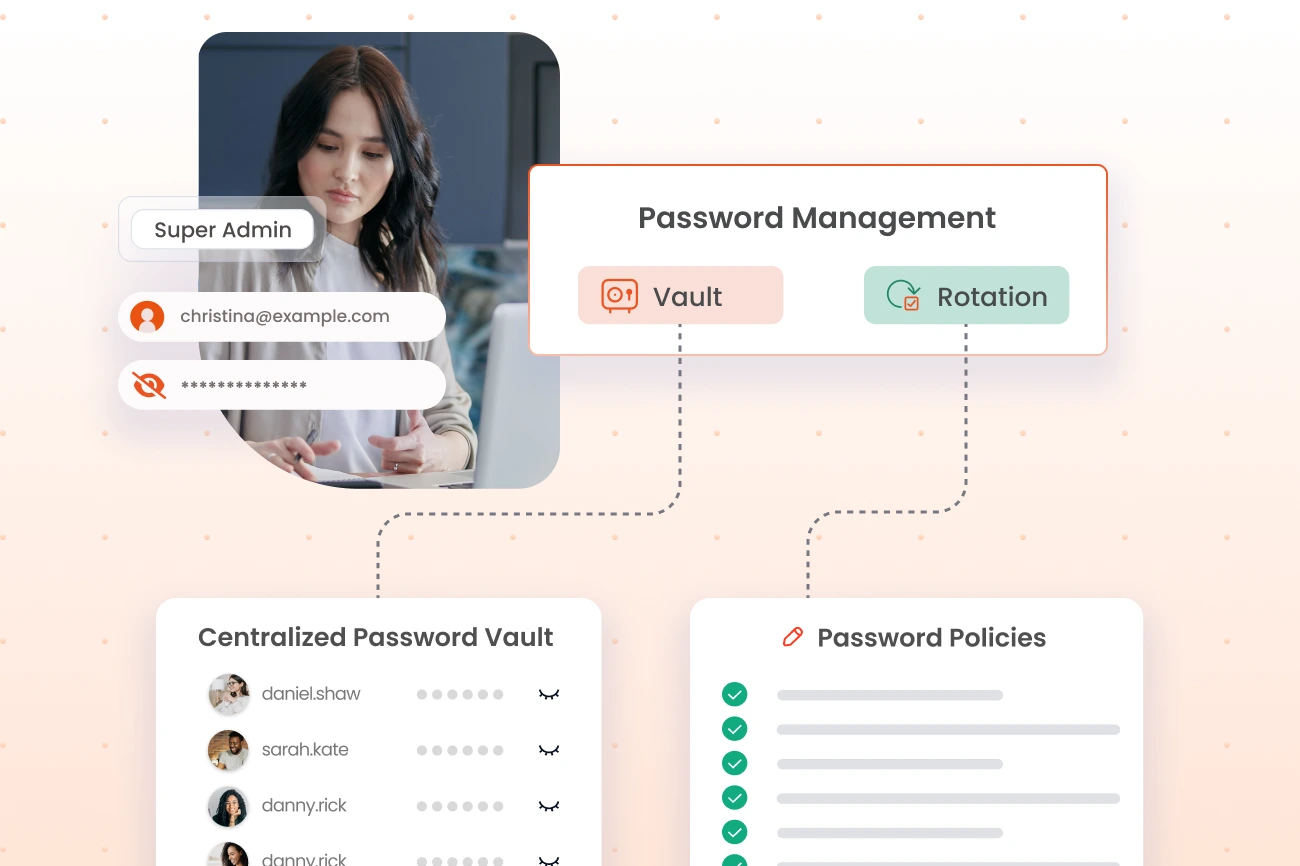
All critical SAP passwords are stored in an encrypted, tamper-proof vault with automatic rotation after every use or on scheduled intervals. Users can access SAP systems without ever knowing or entering passwords, while credentials remain protected from unauthorized exposure.
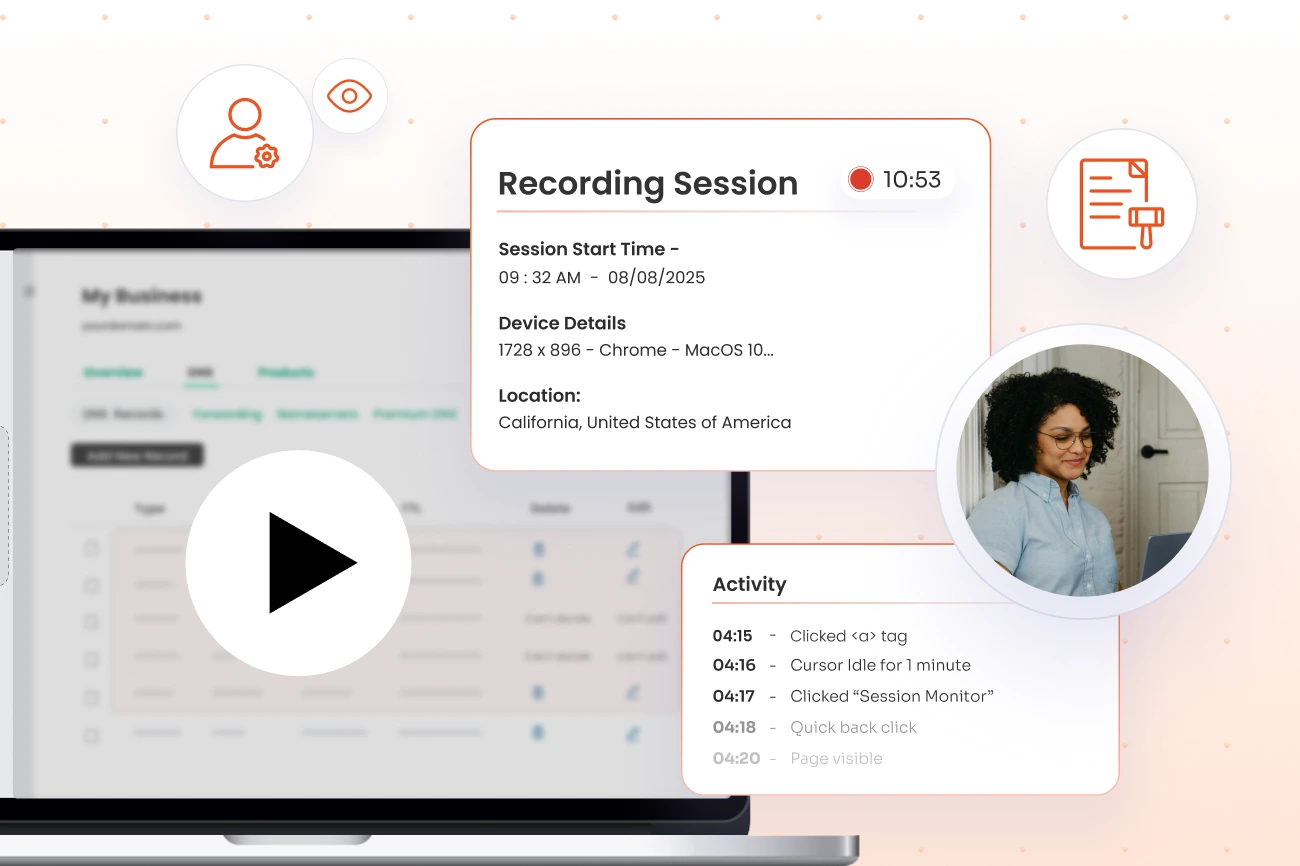
miniOrange PAM acts as a secure gateway, isolating critical SAP infrastructure from end-user workstations and monitoring all privileged activities. Security teams can watch sessions in real-time, intervene to terminate suspicious activities, and set policies to prevent vulnerabilities.
Third-party vendors, contractors, and consultants receive controlled, temporary access to SAP systems only when business requirements demand it. Role-based, time-bound access policies ensure vendor activities are closely monitored and fully logged for audit compliance.
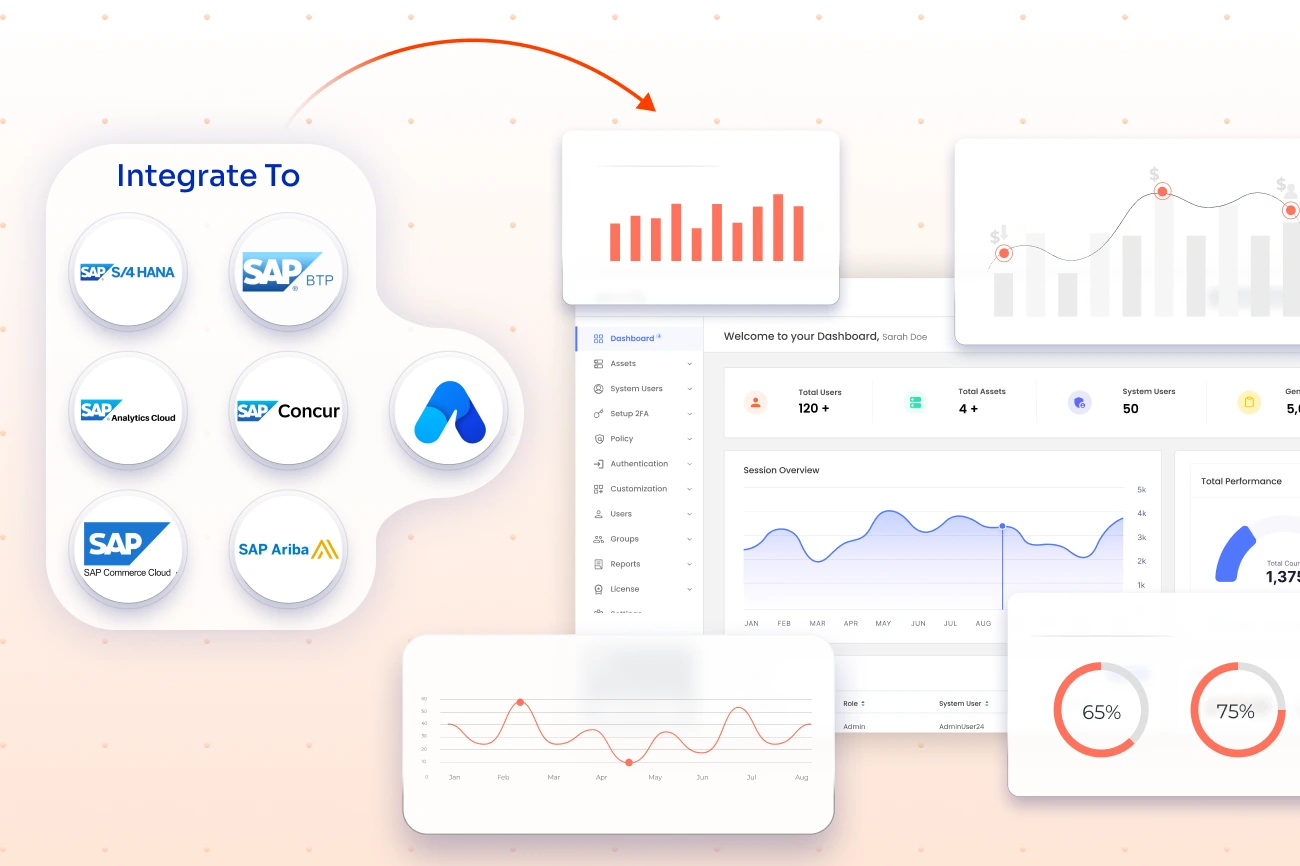
miniOrange PAM integrates seamlessly with SAP S/4HANA, SAP BTP, SAP Commerce Cloud, SAP Ariba, SAP Concur, and analytics platforms like SAP Build and SAP Analytics Cloud. It works across SMB to enterprise-level environments and enhances traditional firefighter or super-user access management in SAP.
Three-Step Formula to Secure Your SAP System with miniOrange PAM

Integrate SAP S/4HANA, Ariba, SuccessFactors, BTP, Commerce Cloud, or Concur. Create resources and add credentials for seamless agentless deployment.
Add users and assign SAP resources by role. Grant time-bound access with automatic expiration. Configure approval workflows and access policies.
Monitor real-time user activities and record privileged sessions. Generate comprehensive access reports. Track all actions with detailed audit trails.
PAM minimizes the risk of unauthorized access and data breaches by enforcing the Principle of Least Privilege. It reduces your attack surface by controlling privileged accounts and preventing credential theft, insider threats, privilege escalation and lateral movement attacks.
PAM automates access controls and provides detailed audit trails for SOX, GDPR, and PCI DSS compliance. It centralizes privileged access and maintains comprehensive logs, reducing governance effort and audit prep time.
PAM quickly identifies and responds to security threats through real-time monitoring and automated detection. By blocking unauthorized changes, it keeps SAP systems stable, secure, and performant for operations.
