Hackers rely heavily on phishing; however, YubiKey changes the game by blocking over 99% of phishing attempts, making it one of the strongest hardware-based MFA solutions available in 2025. This small, physical security key requires your presence to authenticate, preventing attackers from stealing credentials remotely.
Built for both individuals and enterprises, YubiKey delivers phishing-resistant, enterprise-grade protection without complexity, stopping account takeovers before they happen. Easy to deploy and scale, it’s the security upgrade your digital environment needs to stay one step ahead in a world full of highly damaging cyber threats.
In this article, we’ll explore what YubiKey is and how it works, covering its reliability, usage across different MFA methods, comparison with other authentication approaches, available key types, best practices, implementation steps, and real-world use cases with miniOrange as an identity provider.
What is a YubiKey?

The YubiKey is a small device that allows users to log in securely without the need for passwords or mobile code-based systems. It supports both newer and older authentication methods, such as OTP, FIDO U2F, FIDO2/WebAuthn, and Smart Card (PIV). With a single key, users can access thousands of services, ensuring simple and secure account authentication.
- Acts as your physical proof of identity
- Can enable passwordless & Multi-Factor Authentication
- Is offline capable; requires neither battery nor connection to internet
- Is compatible with all of the most popular operating systems: Windows, macOS, Linux, and Android
- Prevents phishing, SIM swaps, and intercepting of OTP
- Has been built to offer a user-friendly experience while also offering speed and enterprise-level protection
Why Use a YubiKey?
Passwords and mobile OTPs are no longer enough. Hackers easily phish SMS codes or intercept app-based logins. A YubiKey stops that by demanding physical confirmation; no key, no access. It prevents remote credential theft and locks down your accounts with enterprise-grade security. At an affordable cost, it delivers unbeatable protection and peace of mind from malicious actors.
- Stops phishing attacks dead in their tracks
- Blocks remote credential theft
- Requires physical presence for login
- Delivers enterprise-grade security
- Costs less than a cup of coffee per user/month
- Works with major platforms and services
- Supports FIDO2 and passwordless authentication
YubiKey vs. Other Authentication Methods
YubiKey uses hardware token-based authentication that resists phishing and password theft, unlike traditional methods that rely on stolen credentials. Some of the methods YubiKey is effective against include:
- Passkeys
Single cloud-based biometric/PIN login syncing across devices. Risk: cloud compromise. YubiKey stores credentials offline, safe if the cloud is hacked. - Authenticator App Generates OTP but is vulnerable to phone malware. YubiKey keeps keys offline, stopping the phishing/malware risk.
SMS/Email Verification
Easy to intercept/spoof codes. YubiKey uses physical cryptographic authentication, which is immune to SIM-swap/phishing.
Biometric Authentication
Biometric authentication is quick but specific for devices that have a biometric sensor, which can be problematic if the device is lost or switched. YubiKey offers high security and portable logins anywhere, without an internet connection.
YubiKey works better than other hardware tokens like OnlyKey by Duo and Google Titan Security Key because it keeps your login information stored offline, protects against phishing, malware, and network attacks, and allows for secure logins on the go without sacrificing ease of use.
Types of YubiKeys
Yubico has multiple YubiKey versions that are designed for specific uses or environments; there is:
Yubikey 5 Series:
YubiKeys in the 5 series support a variety of authentication protocols, including FIDO2, U2F, and smart card (PIV); as well as support cross-platform use on both computers and mobile devices. The capability for multiple protocols allows for an effortless transition between operating systems.
Yubikey 5 FIPS Series:
These YubiKeys are created for use in government and regulated industries, where they must be compliant with FIPS 140-2 certification. They provide a high level of hardware authentication combined with security compliant with regulations.
Yubikey Security Key Series:
The security key series of YubiKeys provides for basic FIDO2 and U2F authentication, eliminating password vulnerabilities for Google, Microsoft, and GitHub. This is an ideal option for users requiring easy and phishing-resistant logins.
YubiHSM:
YubiHSM is a hardware security module that secures cryptographic keys for servers and applications, providing enterprise-grade protection for digital signatures, encryption and authentication processes.
Yubikey Nano:
YubiNano is a much smaller version of the YubiKey 5 and was designed for covert/constant use. While it is approximately flush with your laptop/desktop, it still provides the strong authentication of the larger version.
Yubikey Bio Series:
The bio series uses internal fingerprint recognition for passwordless login and provides FIDO2-based security using the biometric method of authentication.
Yubikey For Mobile:
Provides a secure way to authenticate on mobile devices via NFC and/or USB-C. It is an excellent solution for protecting mobile devices, tablets, and hybrid devices that are used for work.
How Does YubiKey Authentication Work?
Strong physical action, using the YubiKey, defends against weak passwords while utilizing basic yet secure forms of authentication.
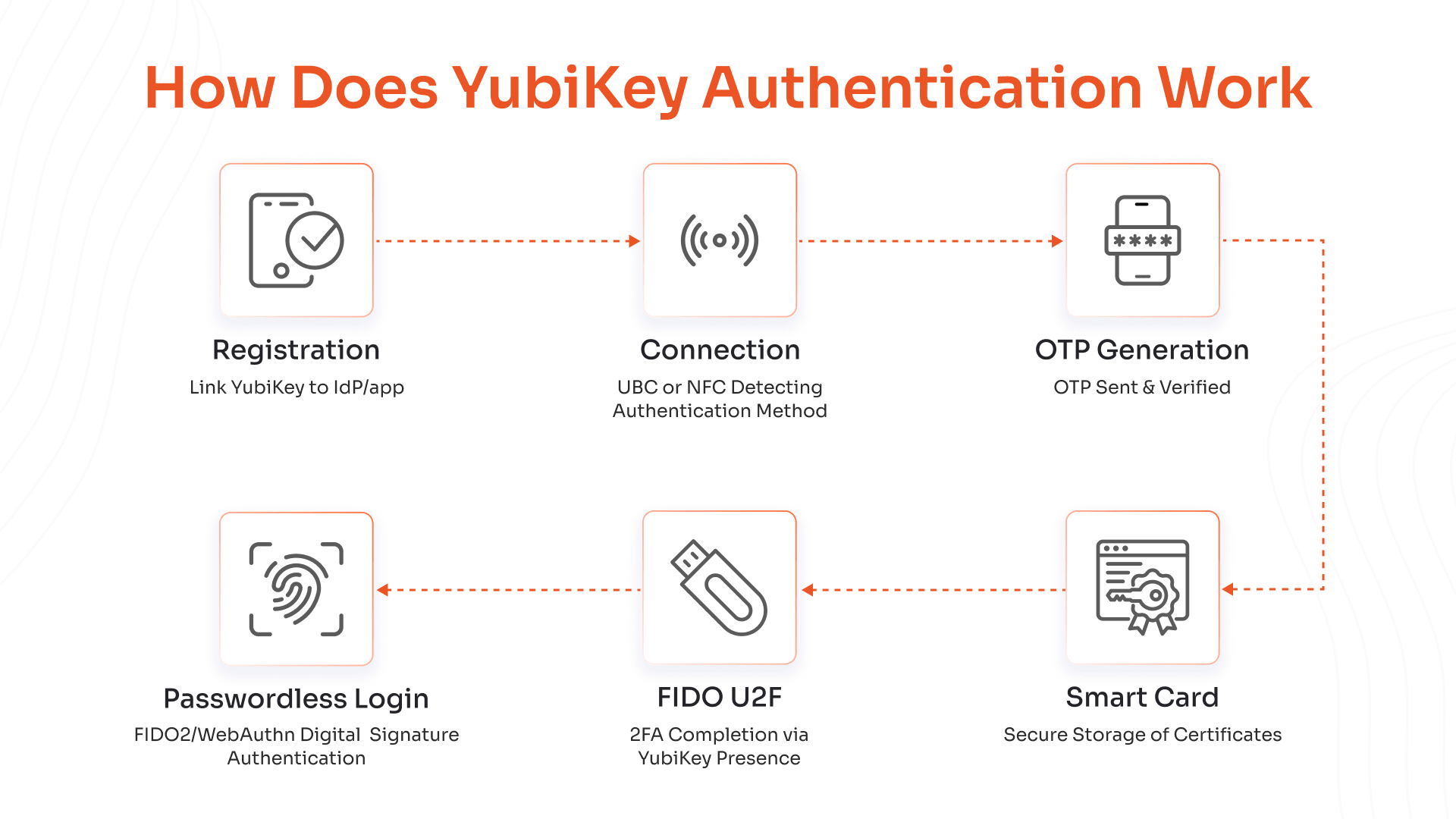
Registration
In this phase you create a link between your YubiKey and your Identity Provider (IdP), or the application services that you want to utilize with your YubiKey. By doing this you ensure that another individual or organization cannot utilize your YubiKey as proof of your identity.
Connection
Once you connect your YubiKey to a computing device via a USB connection or to an NFC-enabled device by tapping it to the device, the computing device checks which method of multi-factor authentication allows you to log into your account as quickly as well as safely as possible.
OTP Generation
While logging in using your Yubikey, it will generate an OTP. The generated OTP will be sent to the app to verify. If the OTP has been successfully authenticated, it is deleted and can never be used again in the future. An OTP prevents hackers from having access to your account via either a hacked password or stolen login credentials.
Smart Card
In secure workplaces, the YubiKey works like a smart card and keeps the important security certificates needed for strong protection.
FIDO U2F
Since only the person who has the actual YubiKey will be able to successfully complete the second part of the two-factor authentication process, hackers are unable to gain access to your account, even if your password is compromised, as they would need to have the YubiKey to successfully complete the second stage of the two-factor authentication.
Passwordless Login
With FIDO2/WebAuthn, when you attempt to sign into an application, your YubiKey produces a digital signature in response to the application's challenge to authenticate you. FIDO2/WebAuthn makes it easy and safe for you to sign into your applications and protects you from phishing scams.
Find out how OTP simplifies strong authentication
Common Use Cases of Yubikey Authentication
YubiKey makes it easy to use advanced phishing-resistant (MFA) while improving security, as opposed to using difficult-to-remember passwords.
Hardware-based MFA for Remote/Hybrid Workforce Teams
Protect employee access to company applications remotely or in a hybrid manner; hardware-based MFA replaces vulnerable user-entered passwords that can allow unauthorized access to protected business data.
Security of Personal Accounts
Adds an additional layer of hardware security protection to personal account access to Google, Facebook, GitHub, and password manager accounts; even when passwords are compromised by a third party, your accounts remain secure.
Government & Compliance-Centric Organizations
Satisfies compliance requirements of highly regulated industries such as finance, healthcare, and defense; provides secure access to confidential systems across large numbers of users.
Supports a Wide Variety of Applications
Supports Google Workspace, Microsoft 365, Dropbox, GitHub, and many other applications; works with most IAM platforms, including Okta, Ping Identity, and Descope.
Security Best Practices in Yubikey Authentication
Secure your YubiKey with secure and reliable practices for configuration. Each of these configuration practices will enhance your authentication process while protecting your access to sensitive data.
- Create a Secure Backup of your YubiKey: Get another YubiKey stored in a safe offline area (in case you lose or damage your primary) and replace it on a regular basis so you always have two up-to-date, working YubiKeys.
- Turn on PIN Protection: Create a long and difficult-to-guess PIN to protect yourself from having someone else use your YubiKey to gain access to your accounts. Use a unique PIN for each YubiKey.
- Store Recovery Codes Safely: Store recovery/backup codes in an encrypted password manager for future reference. This way, you'll be able to gain access back into your accounts without jeopardizing your security.
- Do Not Share Keys or Mix Uses for the Same Key: Have one YubiKey specifically for personal use and one specifically for work use. In doing this, you limit the potential risk of cross-domain exposure, because you treat each YubiKey as confidential hardware for their respective purposes.
- Update Firmware and Configuration Regularly: Look for and install YubiKey firmware updates as they become available to address potential vulnerabilities. Furthermore, review your account bindings regularly to make sure that all accounts are still authorized and linked properly.
- Protect Physical Access to Your YubiKey: Remove your YubiKey from the device when not using it and do not leave it plugged into a device when it is unattended. Don't forget; physical possession means control, so treat your YubiKey with the same respect as you would a passport.
Benefits of YubiKey
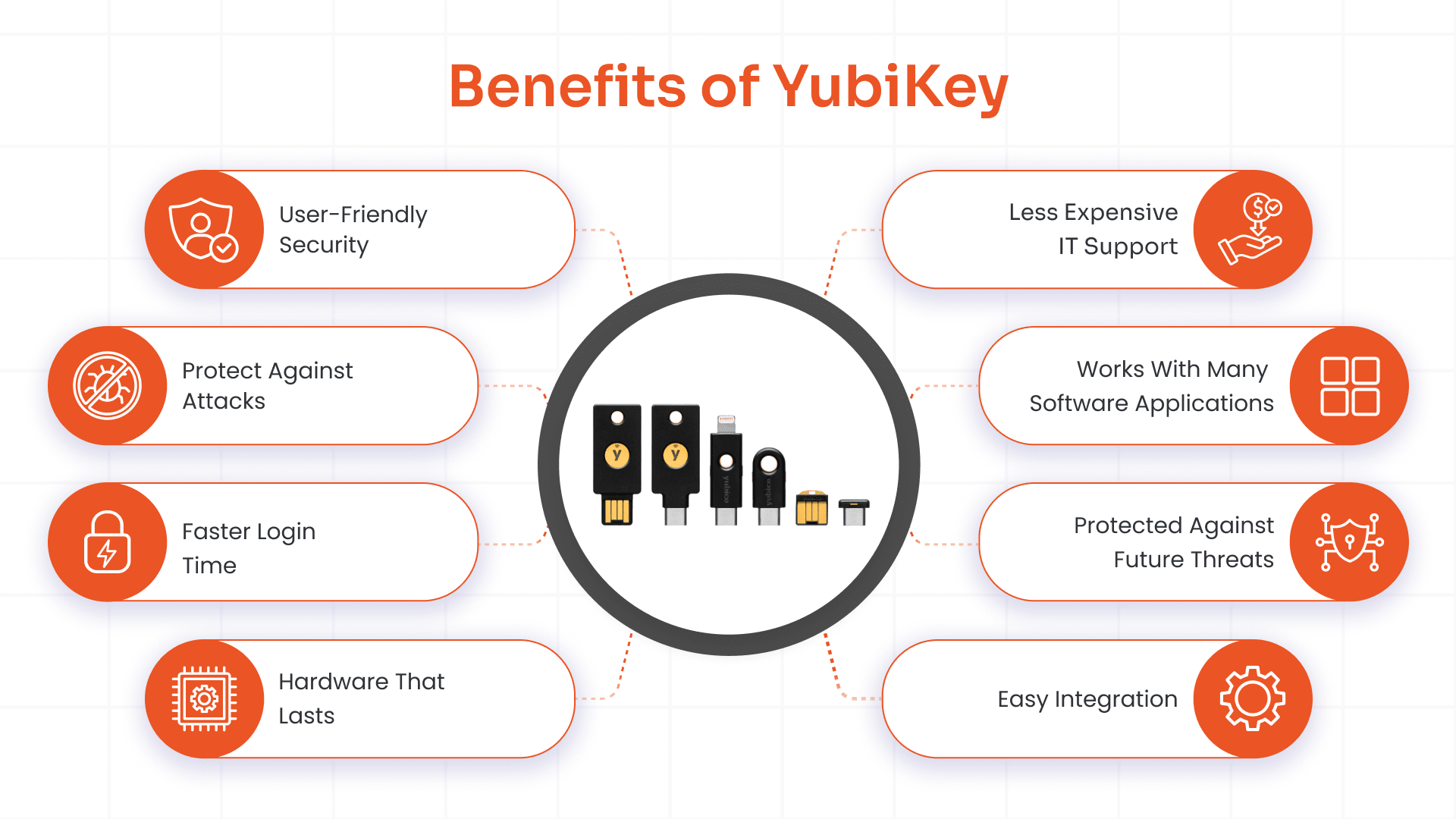
YubiKey as a hardware token provides stable security against online threats. Here are some of the major benefits it offers:
- User-Friendly Security - Easy-to-use hardware tokens are designed to provide a safer, phishing-proof, two-factor and multi-factor protection experience.
- Protect Against Attacks - The YubiKey keeps your information safe from phishing, stolen passwords or PINs, replay attacks, and Man-In-The-Middle (MITM) attacks after you log in securely, so you can access your system safely.
- Faster Login Time - The YubiKey eliminates the need to recall long and complex passwords and multiple authentication codes when logging into a user’s account using the YubiKey, therefore reducing errors created by humans and creating a faster and more efficient way of logging in.
- Hardware That Lasts - Because the YubiKey has no battery and is both water-resistant and crush-proof, it can be used for many years without concern for environmental conditions, as long as it remains connected to your device or computer.
- Less Expensive IT Support - Companies that implement YubiKeys typically report an average reduction of over 90% of their password resets, which is another reason why companies choose to implement and deploy MFA with the YubiKey because it is a simple way to do so while being cost-effective.
- Works with Many More Software Applications - There are over 1,000+ software applications supported by YubiKeys (Google, Microsoft, Cisco, GitHub, etc.) and the YubiKey also supports the majority of operating systems (Windows, macOS, iOS, Android, etc.) as well as many different authentication protocols (FIDO2, U2F, OTP, etc.).
- Protected Against Future Threats - The YubiKey is maintained/updated by Yubico and follows FIDO/WebAuthn standards; therefore, once a user purchases a YubiKey, they won't ever need to update their software again.
- Easy Integration - The YubiKey may be integrated into the organization's current Identity Access Management (IAM) solutions, such as miniOrange, to enable passwordless onboarding and Adaptive Multi-Factor Authentication (MFA), allowing the organization to quickly and easily deploy MFA while increasing the security of access to the organization's systems.
Understand why authenticator apps are key to passwordless logins.
Get Started with Yubikey Authentication with miniOrange
Use the power of YubiKeys to ensure secure, phishing-resistant access across all of your organization's cloud, on-premises, and VPN-based solutions. Use one of many YubiKey devices to provide the best option for your teams' device types and workflows; there are YubiKey models available in USB-A, USB-C, NFC, and biometric. With miniOrange MFA and YubiKey deployed throughout an entire organization, you will never have to worry about users remembering passwords again and you will be able to prevent attackers from using credentials to breach your environment without having to do anything.
miniOrange MFA provides enterprise-level security that can scale as easily as your organization grows. The miniOrange MFA solution is a simple "plug-and-play" solution that integrates YubiKey authentication with your existing zero-trust policies across all of your cloud applications, VPNs, and legacy systems, providing the most seamless way possible to reduce your breaches and increase user confidence. It is not complex security that creates safety; it is the use of a simple, physical method such as the YubiKey that makes a difference. See how quickly you can cut down your login time from minutes or hours to seconds. Schedule a quick demo, and watch your login process shrink.
FAQs
What is the purpose of YubiKey?
YubiKey is a hardware security token providing strong two-factor and multi-factor authentication for secure access to computers, networks and online services. YubiKey allows the user to secure his identity by generating one-time passwords or using cryptographic protocols such as FIDO2, making logins more secure and phishing resistant.
What are the downsides of YubiKey?
YubiKey’s disadvantage is that with loss or damage of the device, access to the respective account may be impossible. The configuration of the device may be somewhat complex and acquisition of the know-how by the user is required. Not all systems are compatible with it. It is recommended to have backup devices to prevent blocking the access to the respective account.
How much does a YubiKey cost?
YubiKeys for individual users cost between USD 25 and 50 for the standard devices, but if used in an enterprise solution or if FIPS-certified versions are acquired, the costs go up to USD 80 and more as of 2025. There are also differences in the price if quantities of devices are acquired, whereby sets of 50 pieces may cost several thousand USD.
Why is Yubikey so expensive?
YubiKey’s price results from brand recognition and quality parameters, protective features of higher categories, use of high-quality hardware, extensive protocol support and intense work on software integrations, which allows easier handling features for the user. Also, certification projects such as FIPS are frequently time-consuming and costly, which is justified with the better price.
Can a YubiKey be hacked?
YubiKeys are extremely resistant against being hacked and extraction of secrets from the device is almost impossible to fulfill if no great amounts of resources are available. Side-channel attacks or physical possession of the device may lead to security problems. There are hardly any 2FA solutions perfectly safe from being hacked; however, YubiKey is very effective against attacks at a distance.
What if I lose my Yubikey?
If you lose your YubiKey, use your backup key or recovery codes to access your accounts, and disable the key that is lost right away. It is best to have at least one spare YubiKey on hand for emergencies and to put it in a secure place. Have this key so that you are not locked out of your accounts and can access them without any obstacles.



Leave a Comment