Configure & Manage Database Policies
Database Policies in miniOrange PAM help administrators control and manage access to database resources securely. These policies allow enforcement of session timeouts, MFA, activity recording, and access permissions to enhance security and compliance.
This guide walks you through the steps to configure database policies, set security controls, and define access management rules.
How to Manage Database Policies
Follow these steps to add and manage database policies effectively.
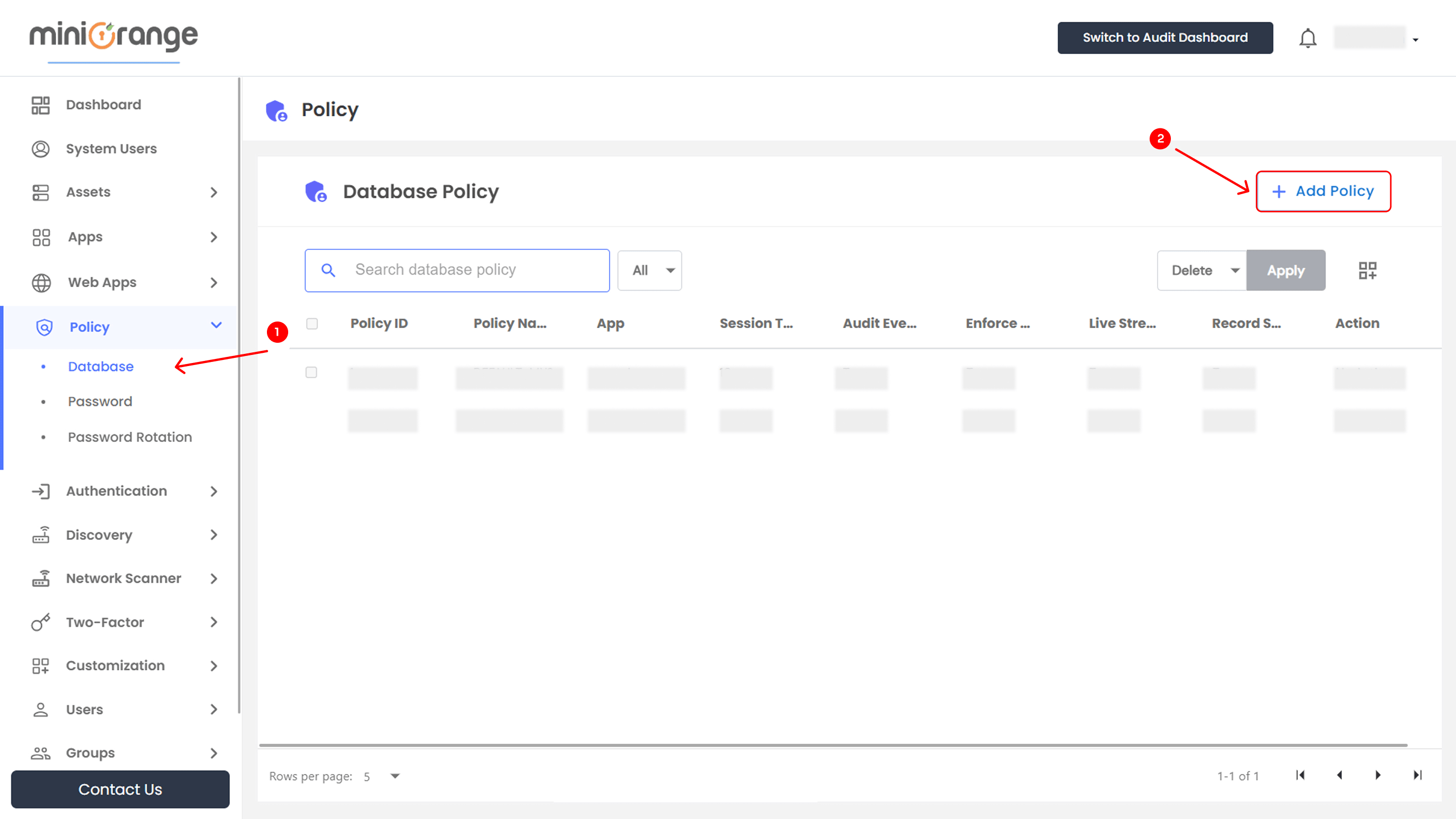
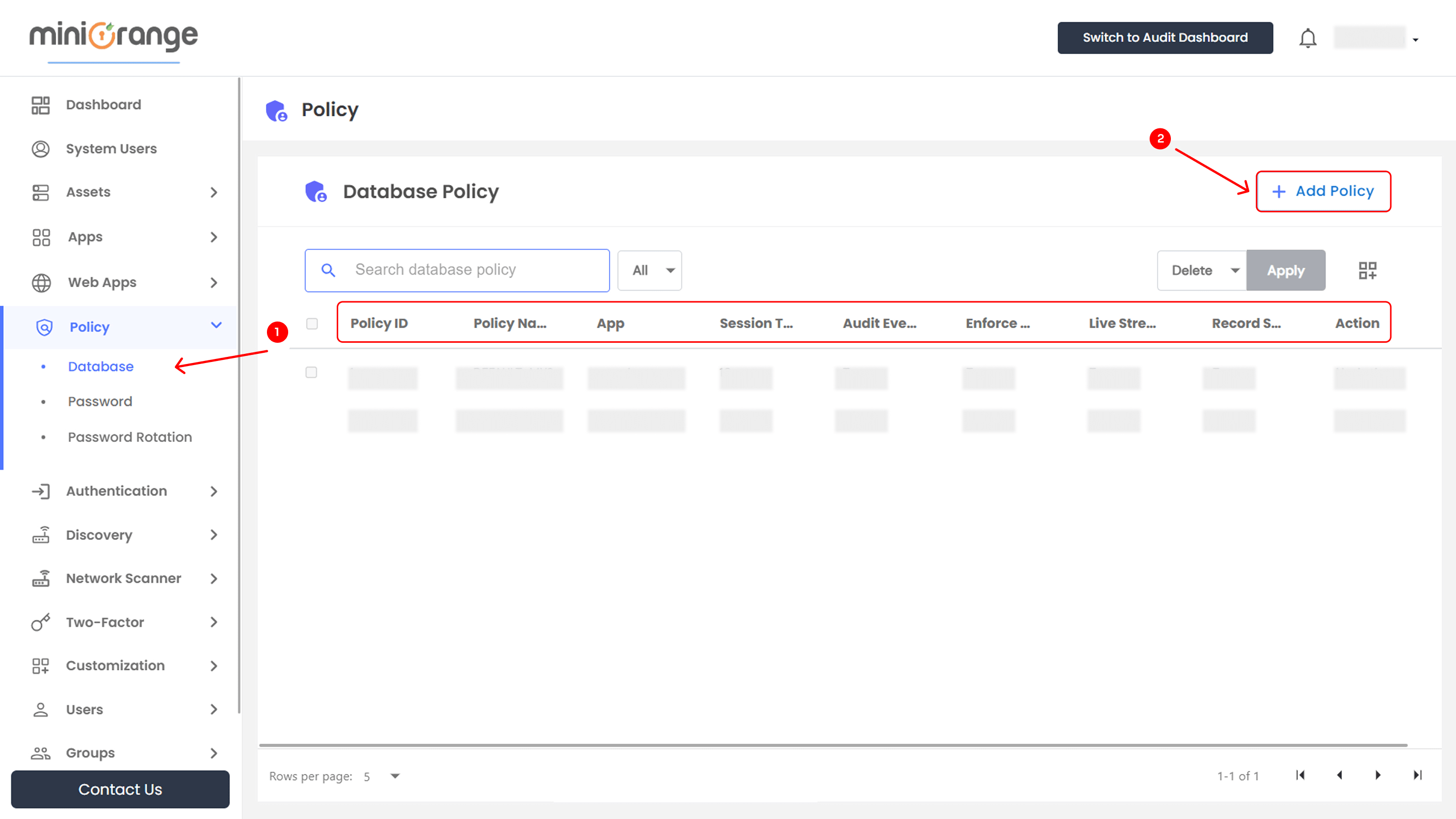
Accessing the Database Policies Section
- Open the miniOrange PAM dashboard.
- Navigate to the Policy section in the left-side menu.
- Click on Database to access the policy dashboard.
Adding a Database Policy
To add a setup new Database Policy
- Click + Add Policy in the database policy dashboard.
- A new window opens with two configuration tabs.
- General
- Advanced
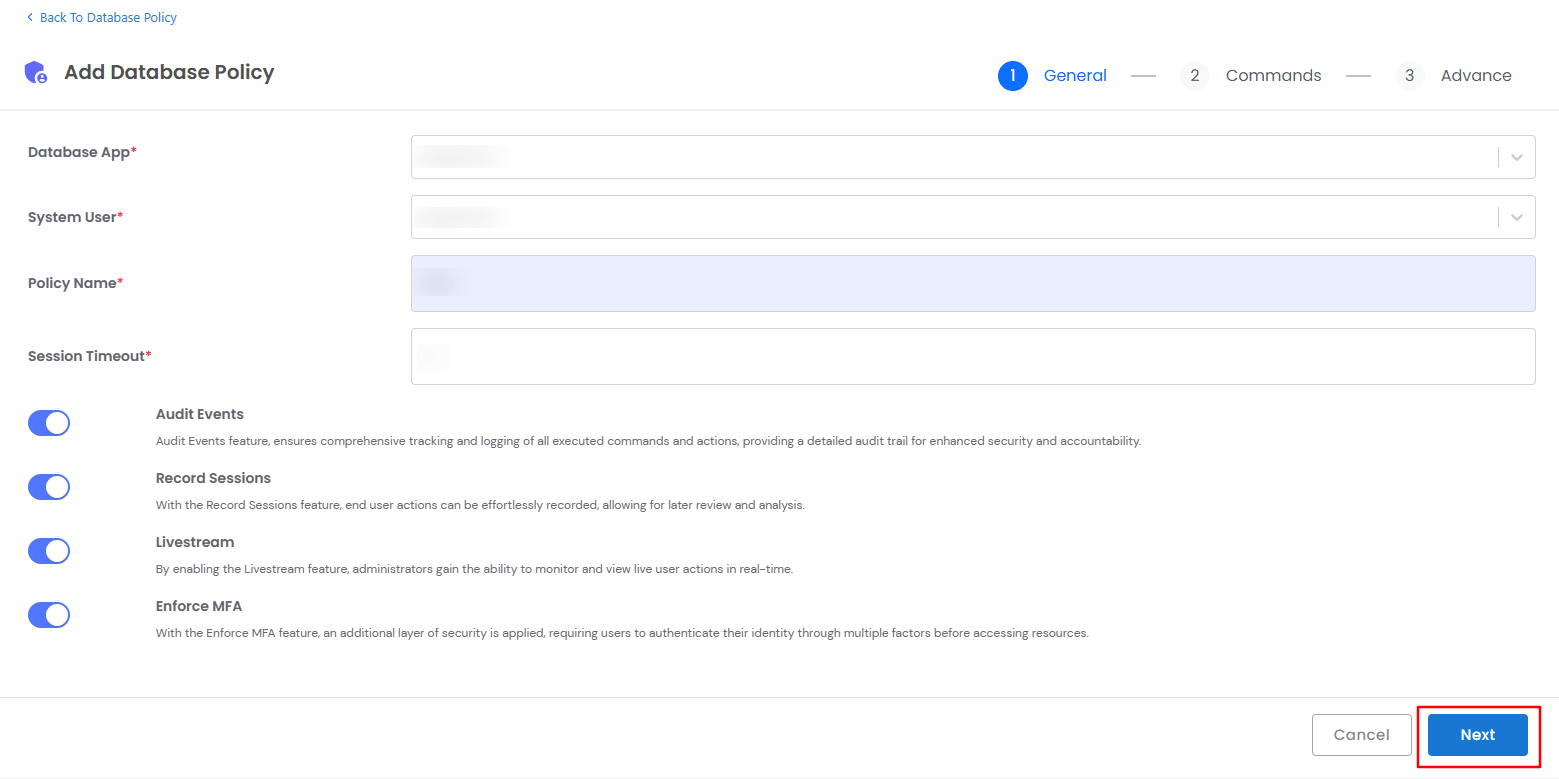
General Settings
- Database App: Select the target database from the dropdown.
- System User: Used to connect and authenticate with the database application.
- Policy Name: Enter a descriptive policy name.
- Session Timeout: Define the idle session timeout in minutes.
- Enable Security Features(Checkbox options):
- Audit Events: Tracks all actions for security and compliance.
- Record Sessions: Records all user activities for later review.
- Live Stream: Allows real-time monitoring of database sessions.
- Enforce MFA: Adds an extra layer of authentication security.
Advanced Settings
- Transaction Control
Determines whether database commands should be executed as part of a transaction.
- Commands: Specify which database commands (DELETE, UPDATE, INSERT) should be controlled.
- Password Field: Enter the password field identifier.
- Auto Commit Conditions: Define when commands should be auto-committed.
- App Access Action
Defines user access levels to database applications. The available options include
- ALLOW: Grants direct access to the database.
- ELEVATED_REQUEST: Allows users to request elevated access.
- REQUEST: Requires admin approval for access.
- BLOCK: Restricts user access completely.
- Default Resource Action
Specifies how commands are handled when no matching policy is found. The available options include:
- ALLOW: Allows the command execution.
- DENY: Blocks the command execution.
- Command Control
Configure allowed (whitelist) or restricted (blacklist) database commands.
- WHITELIST: Only the specified commands are allowed.
- BLACKLIST: The specified commands are blocked.
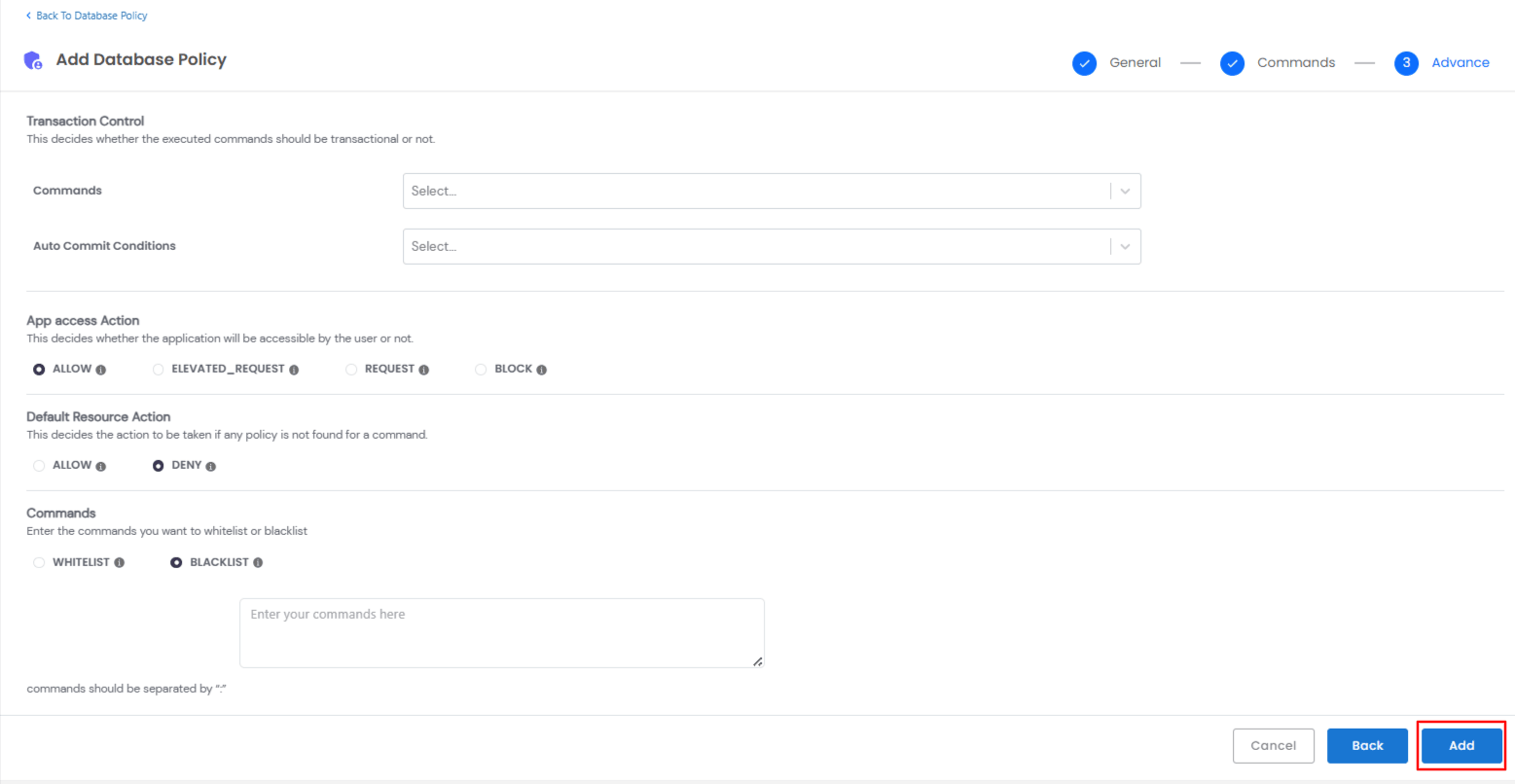
Note: Enter commands in the text box, separated by a colon (:).
- Once all settings are configured, click Add to save the policy.
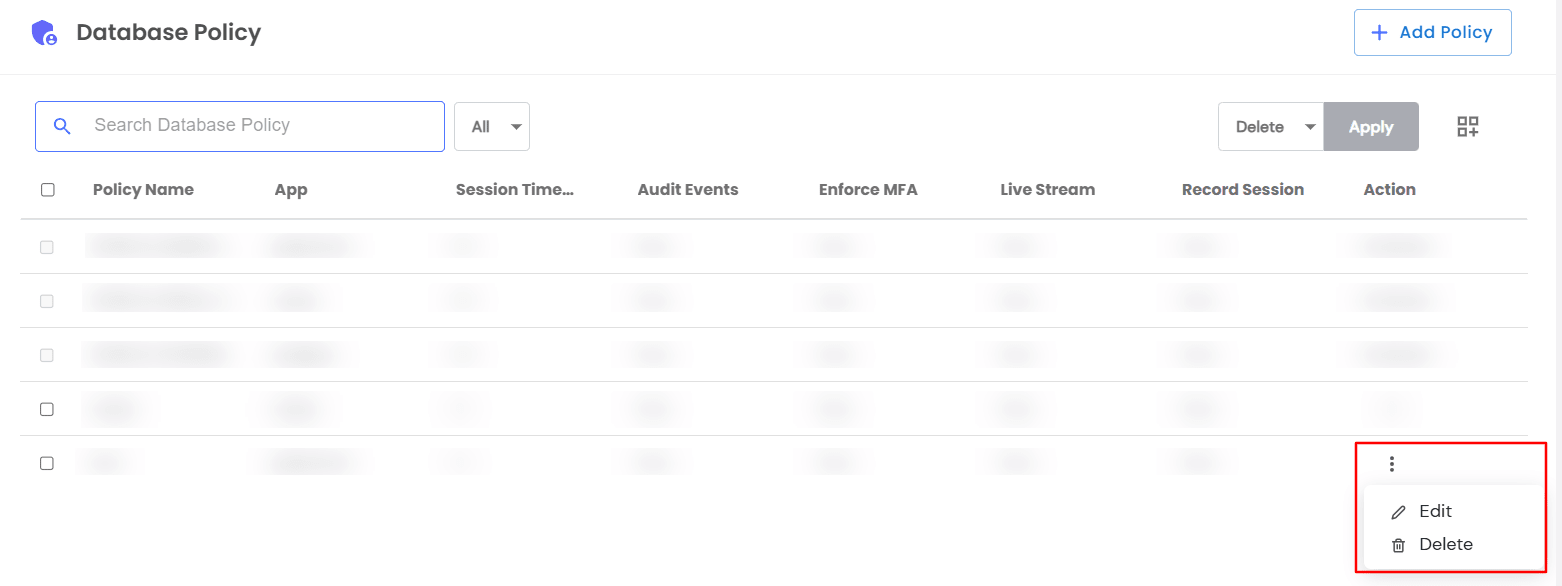
Database Policy Table Overview
Once database policies are added, they appear in the Database Policy table with the following details:
- Search Bar & Actions
- Search Bar: Quickly find specific policies.
- Delete Button: Remove selected policies.
- Apply Button: Apply changes to selected policies.
- Table Overview
- Checkbox: Select policies for bulk actions.
- Policy Name: The assigned name of the policy.
- App: The database application associated with the policy.
- Session Timeout: Duration before an idle session is terminated.
- Audit Events: Indicates if audit logging is enabled (True/False).
- Enforce MFA: Specifies if multi-factor authentication is enforced (True/False).
- Live Stream: Displays whether real-time monitoring is enabled (True/False).
- Recorded Sessions: Shows if user activity recording is active (True/False).
- If you need to manage a database policy, you can do it from the main page.
- Locate Action >> select the required option from the dropdown.
| Action |
Option Overview |
| Edit |
With the edit option, you are able to alter the details you have added in the configuration section. |
| Delete |
Delete the selected database policy from the dashboard |