Need Help? We are right here!
Need Help? We are right here!
Thanks for your Enquiry. Our team will soon reach out to you.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
Search Results:
×
A step-by-step guide to setting up Oracle JD Edwards via miniOrange Access Gateway for secure authentication and seamless access.

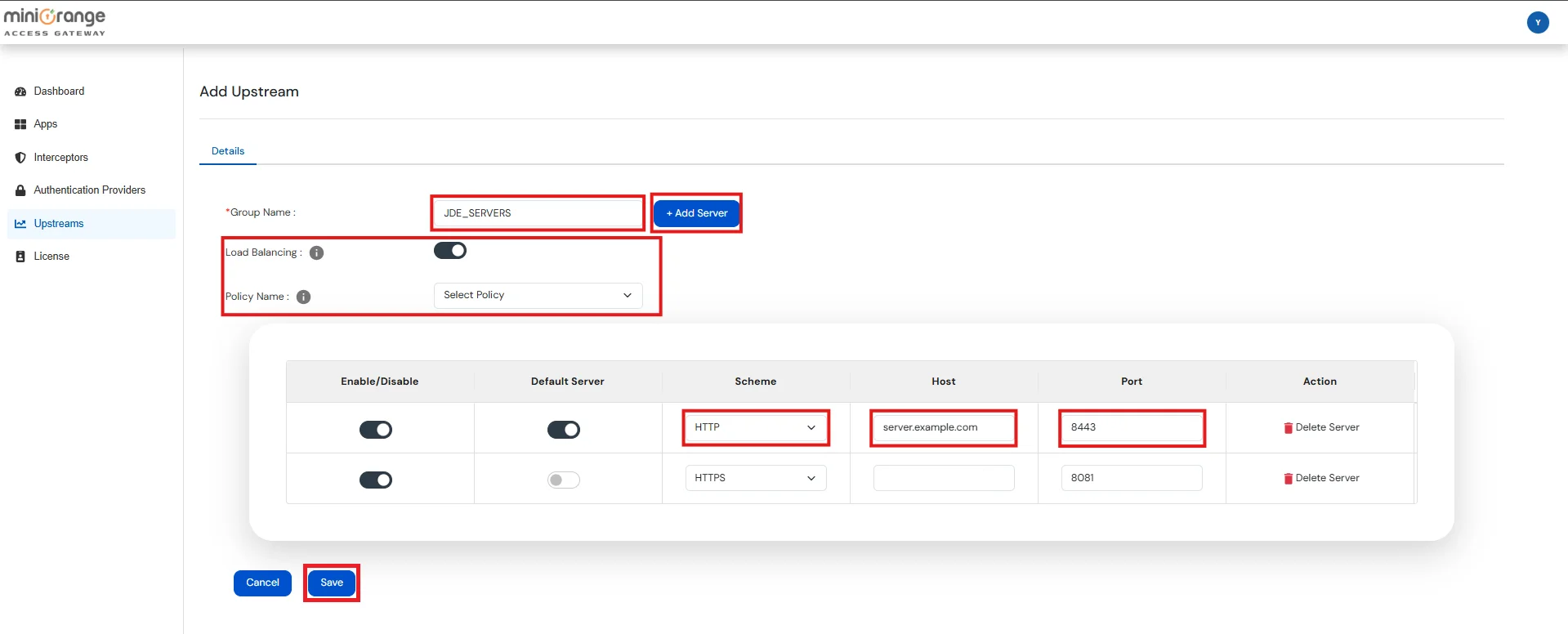
Note: Upstream Group contains the details of servers on which your application is deployed.
Upstream Group Details:
| Group Name | Enter a unique name for the Group of Upstream Servers |
| Load Balancing |
|
Server Details:
| Scheme | Select the scheme/protocol used to access the JD Edwards Server. This field can only have one value either HTTP or HTTPS |
| Host | The FQDN or IP Address of JD Edwards Server |
| Port | The Port on which the JD Edwards Server is listening |
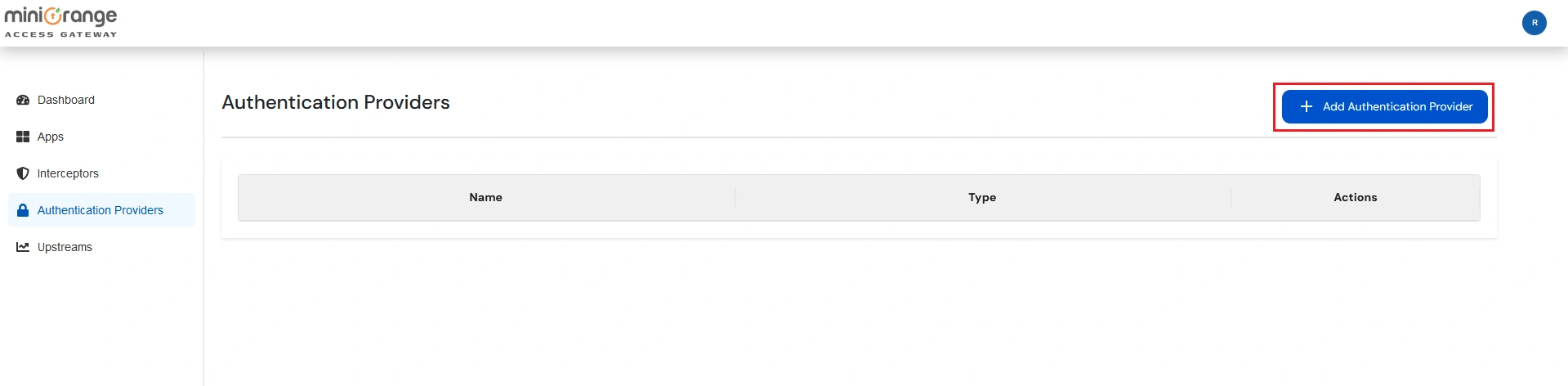
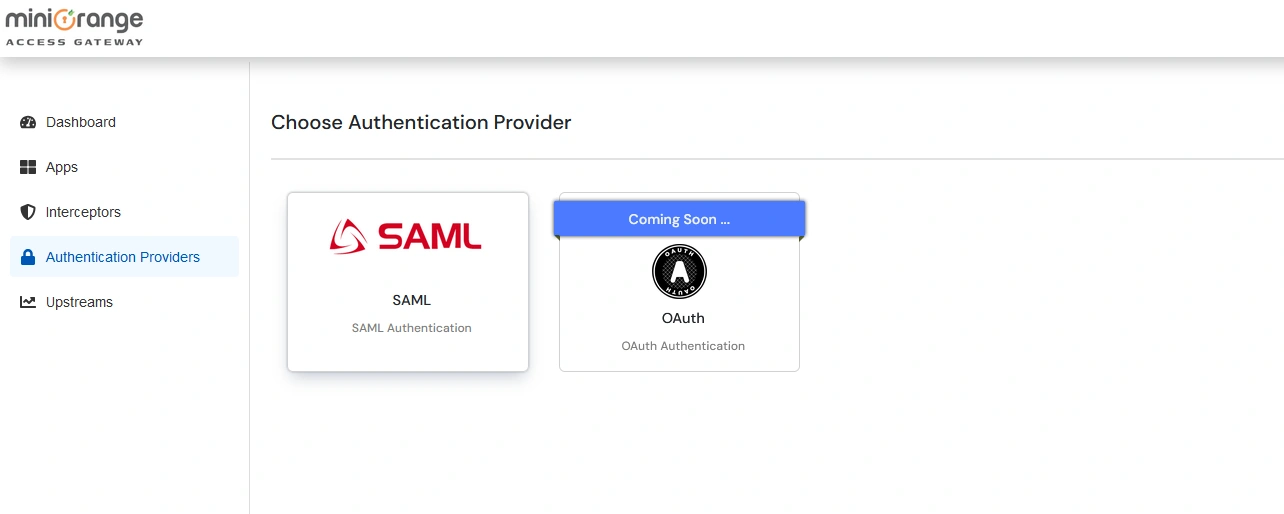
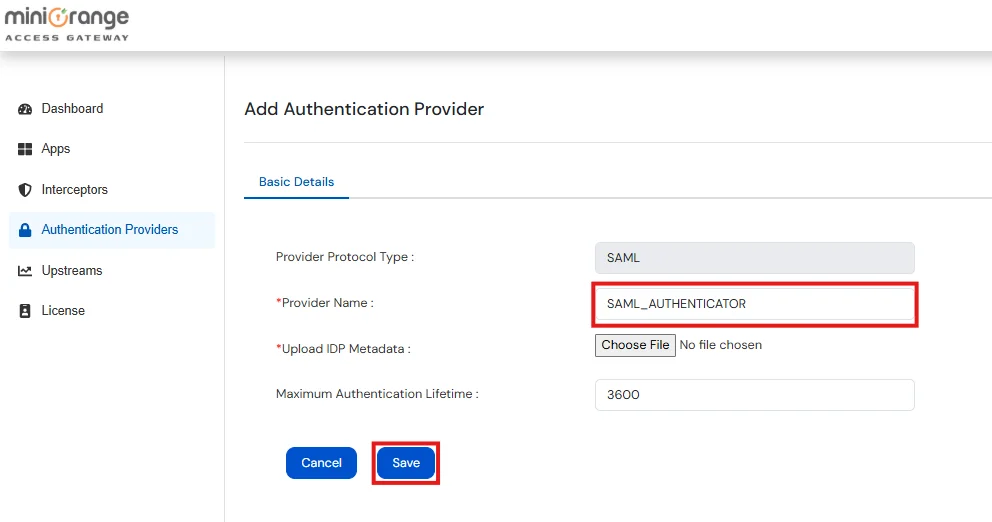
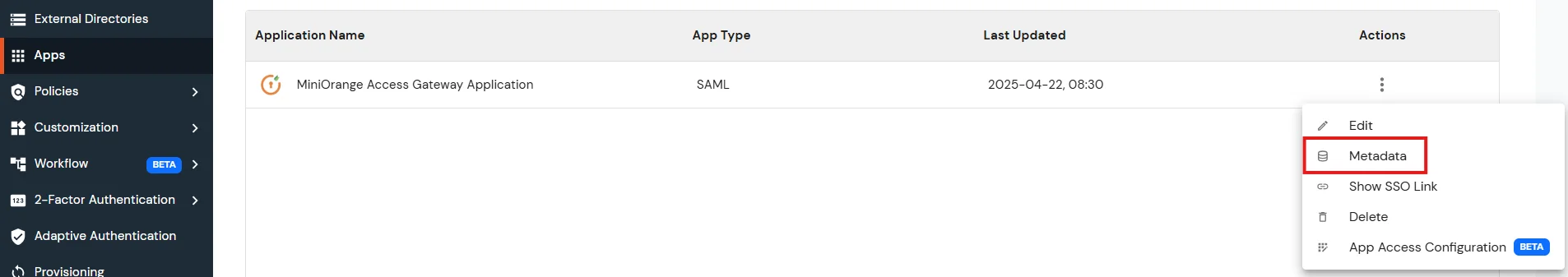
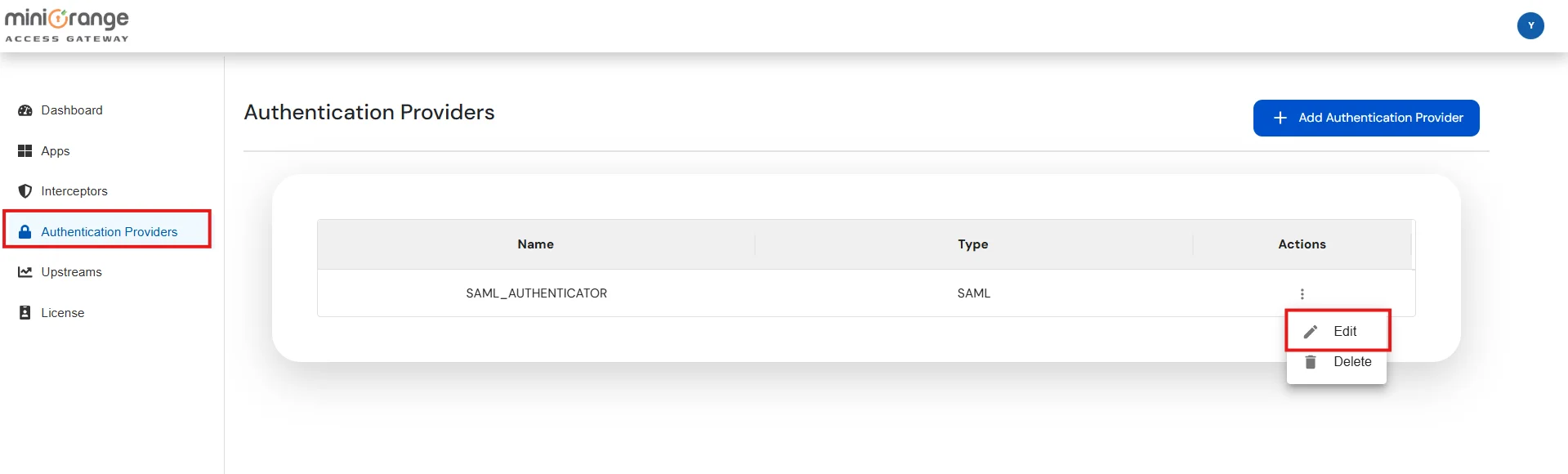
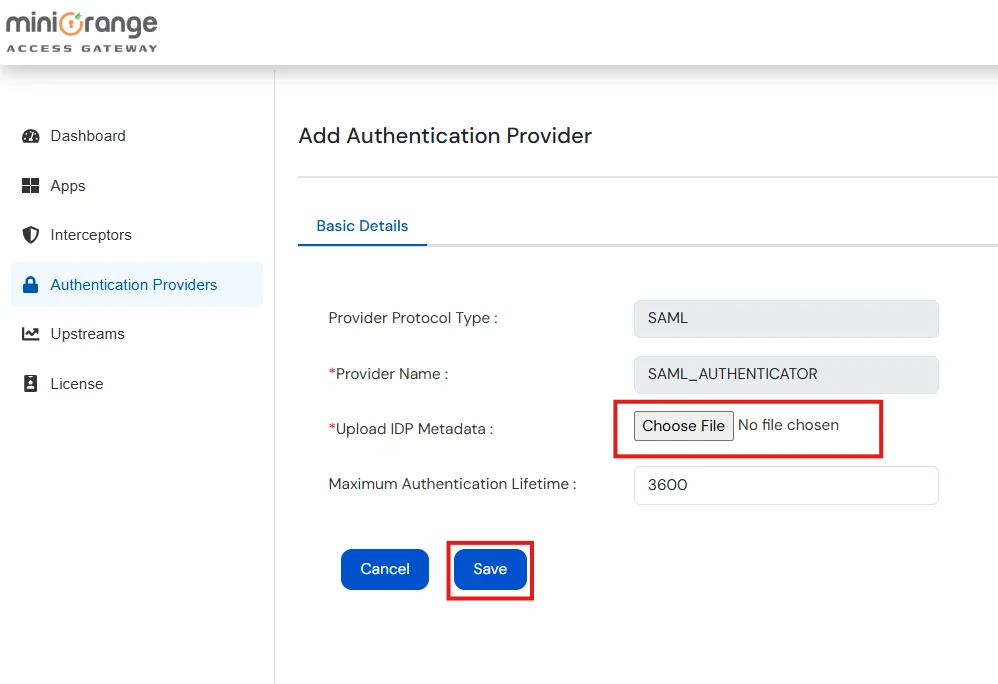
Note: Authentication Providers contain IDP configurations used for user authentication.
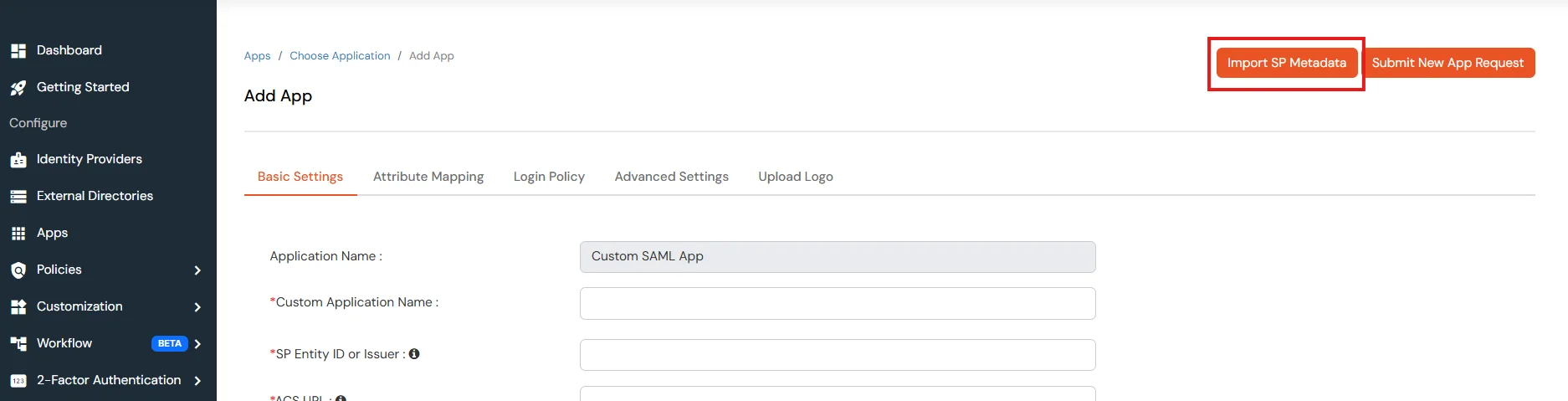
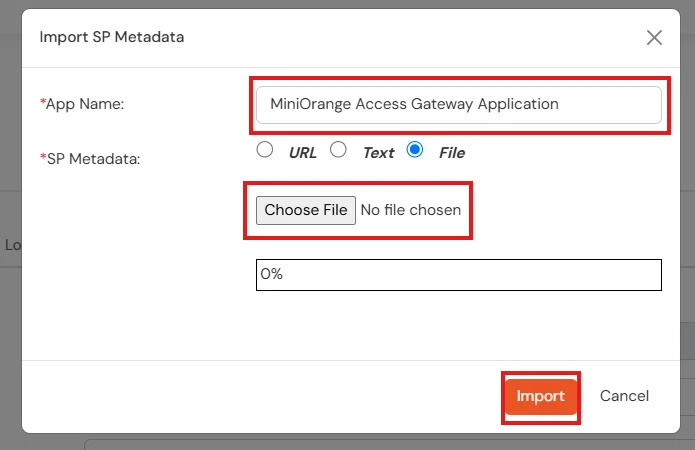
Note: Don’t upload any metadata file right now, we will come back to this in the upcoming steps.
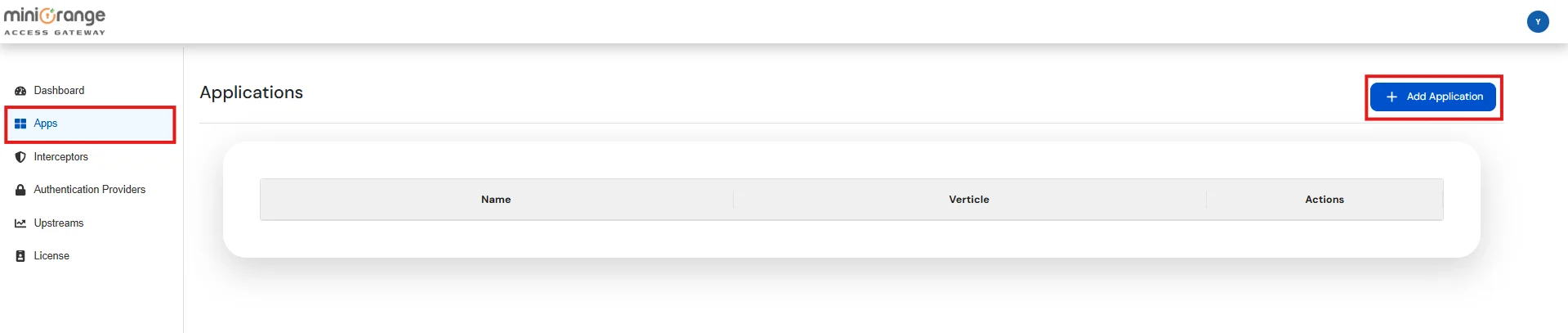

| Application Name | Enter a unique name to identity Application |
| Hostname | FQDN on which the Access Gateway will be accessed |
| Port | Port on which the Access Gateway will listen for HTTP requests |
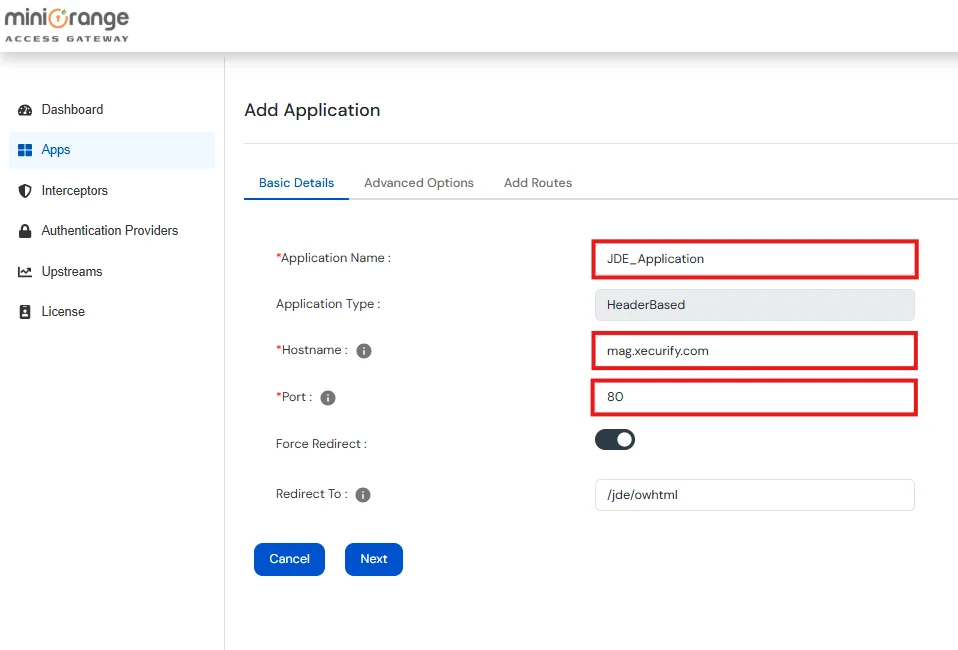
Note: The Hostname entered above must have a DNS entry pointing to the server on which miniOrange Access Gateway is deployed.
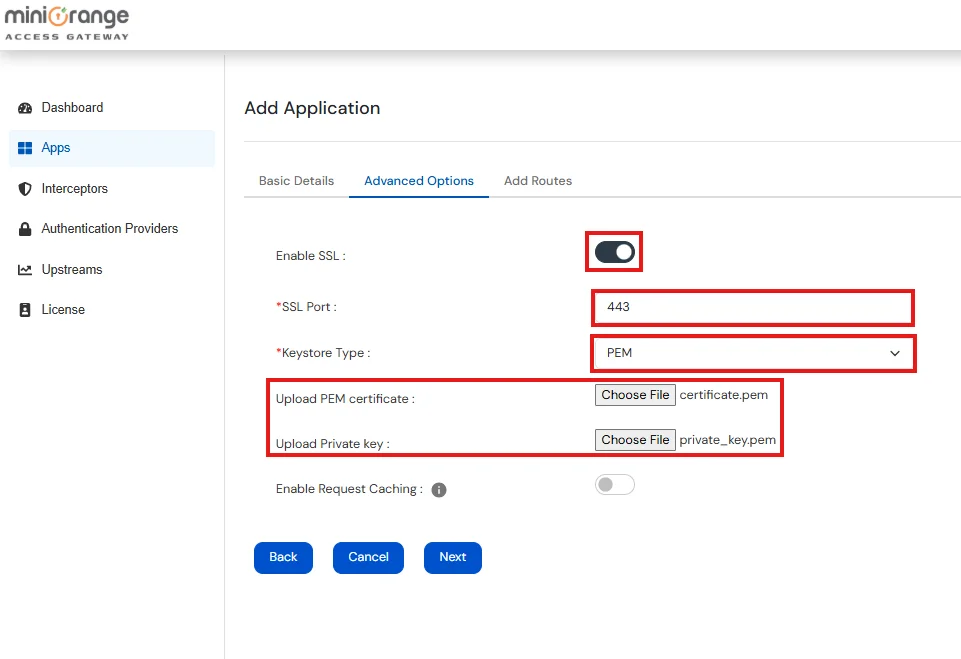
| Enable SSL | Enable this button if you want to allow Access Gateway to run on HTTPS |
| SSL Port | Enter the SSL Port number that the Access Gateway will listen on for HTTPS Requests |
| Keystore Type | Type of keystore used to SSL Certificates ( JKS, PKCS12, PEM ) |
| Upload Keystore | If Keystore Type is JKS / PKCS12, then upload keystore files with extensions .jks, .p12, .pfx |
| Upload PEM Certificate | If Keystore Type is PEM, then upload file with .pem extension |
| Upload Private Key | If Keystore Type is PEM, then upload private key with .pem extension |
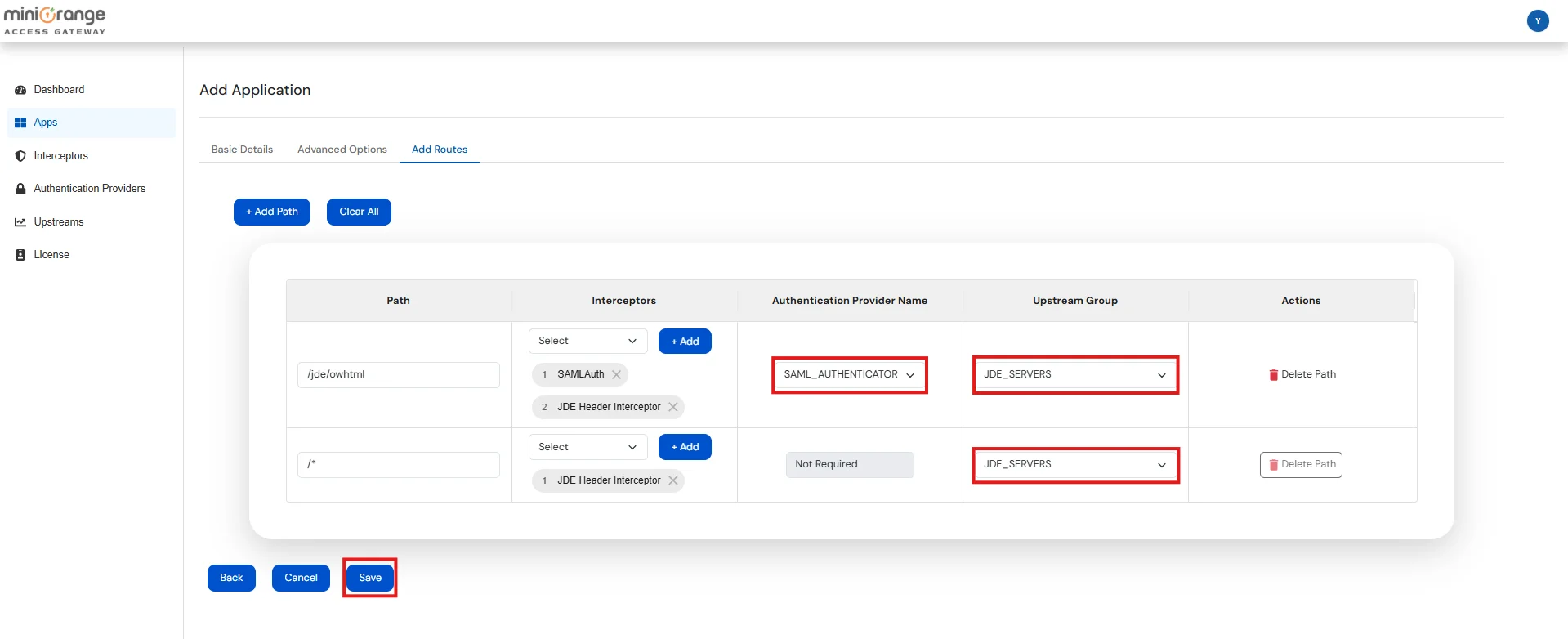
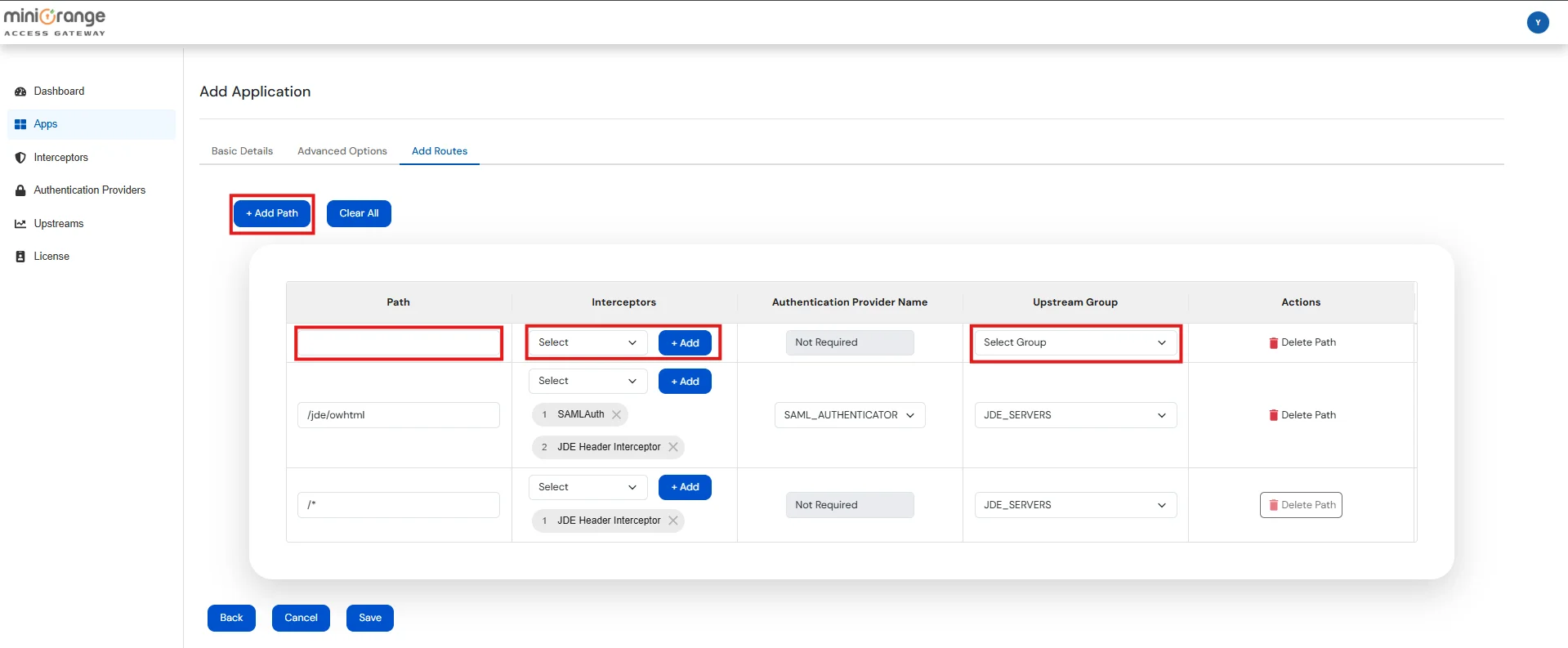
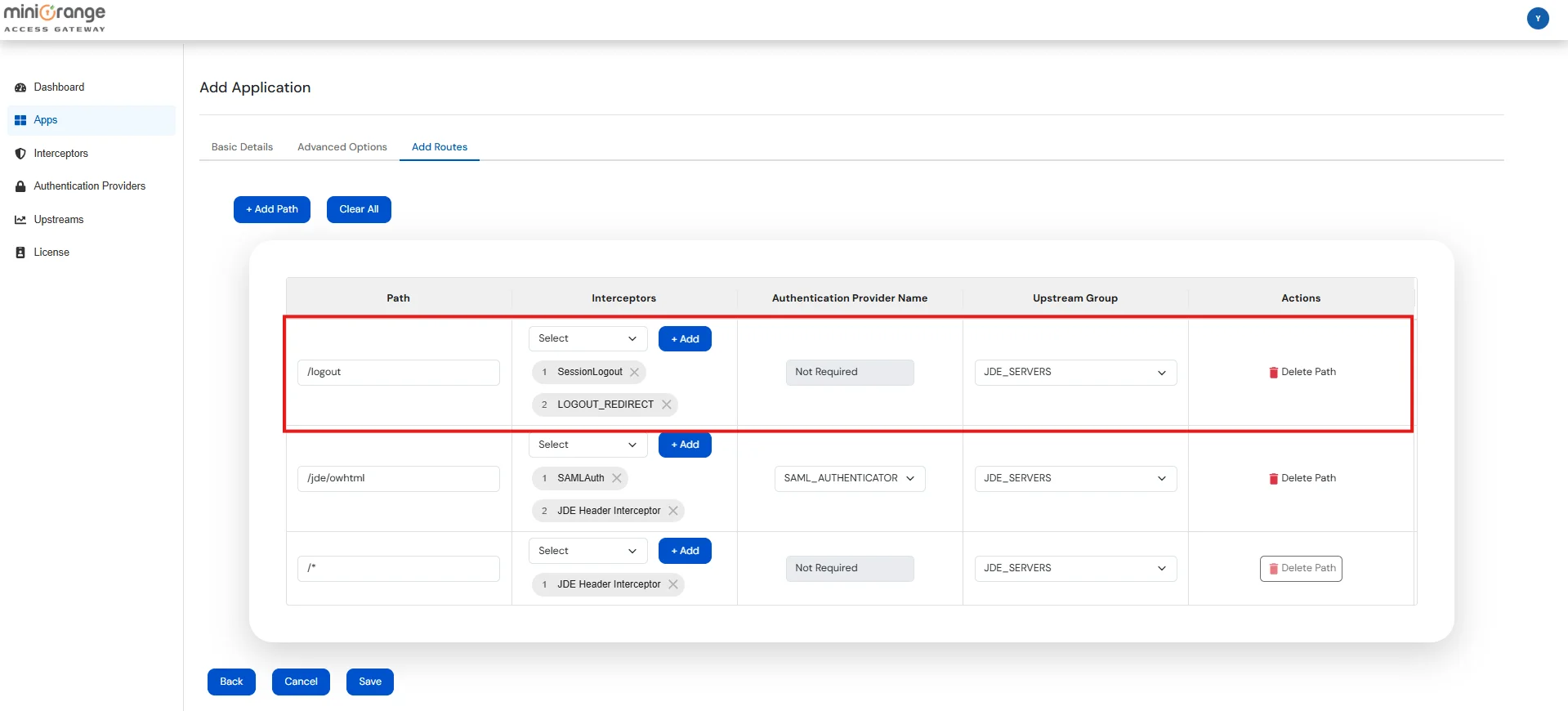
| Path | Defines the request URL pattern (e.g. /jde/owhtml, /*) that this route will handle. Supports exact paths or wildcards. |
| Interceptors | A list of interceptors that process the request before it's forwarded. You can add, remove, or reorder them. |
| Authentication Provider Name | Select the name from the list of configured Authentication Providers. This option will be enabled only if the SAMLAuth interceptor is present. |
| Upstream Group | Select the name from the list of configured Upstream Groups where the request should be forwarded. |

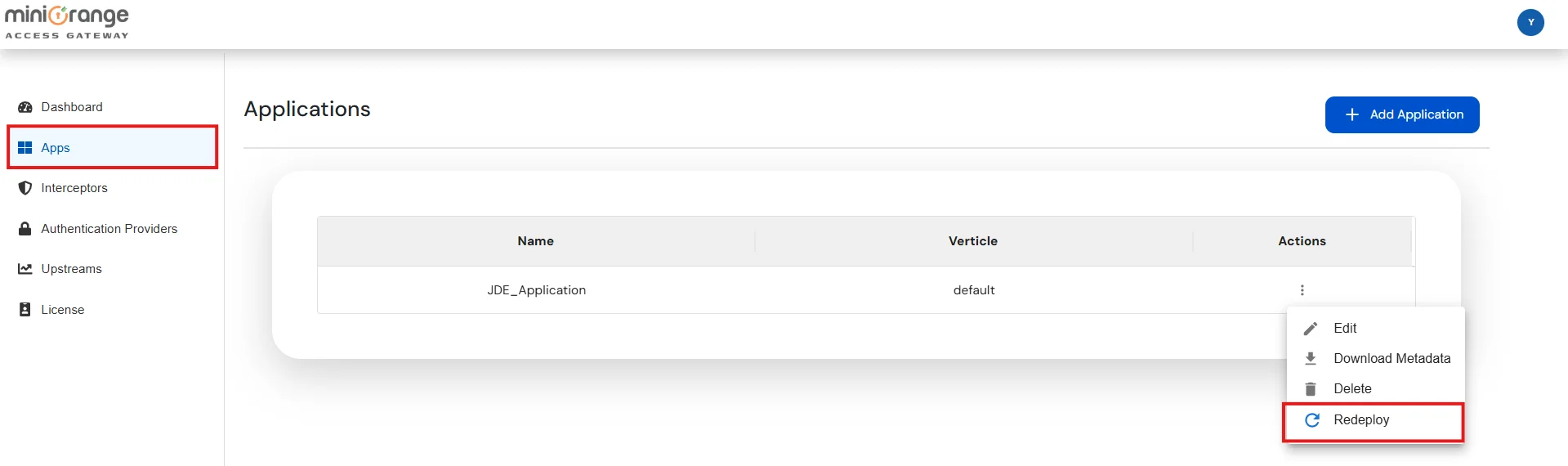
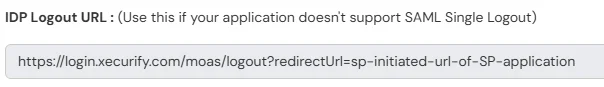
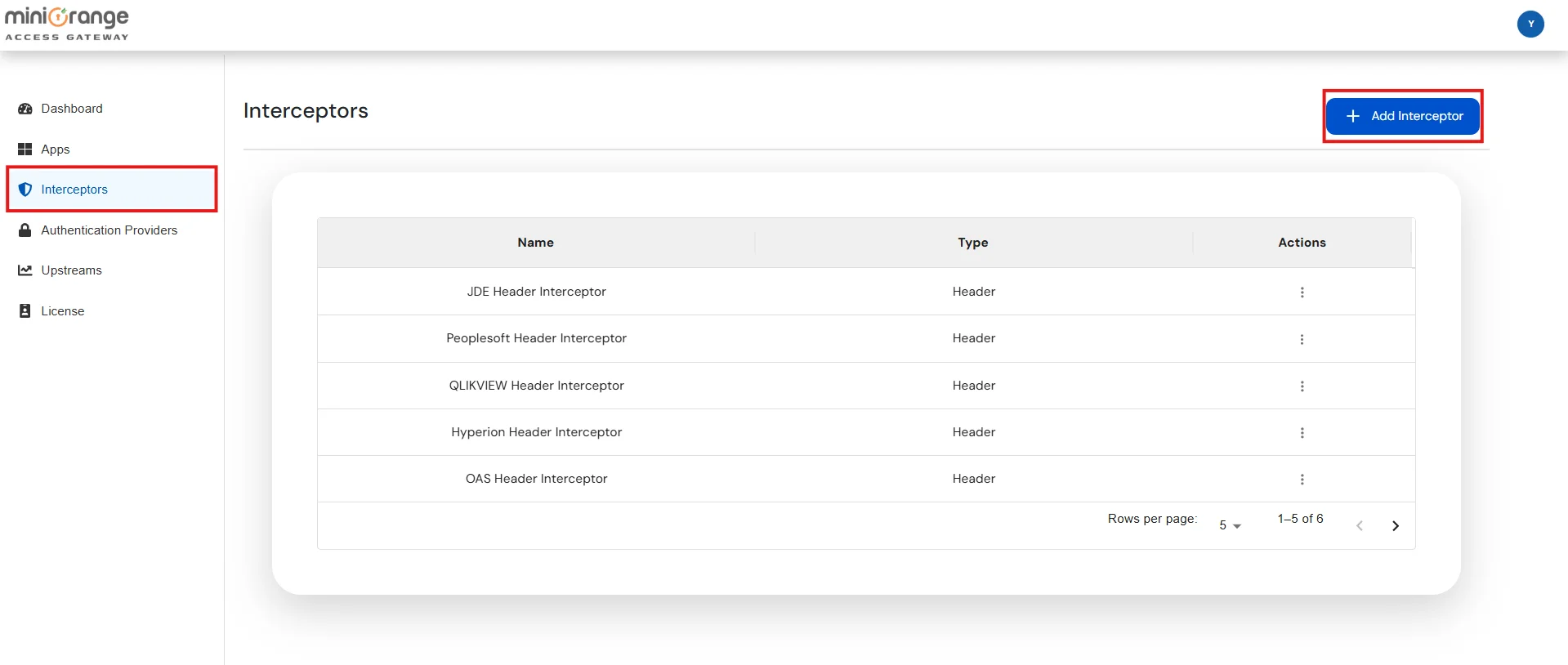
Note: Interceptors are components which act like filters, that process incoming requests before they are forwarded to the Upstream Server.
| Interceptor Type | Function |
|---|---|
| SAML | Forces SAML Authentication before forwarding the request to the upstream server. |
| Catch Cookies | Fetches cookies from the request and adds them to the corresponding response from the upstream server. |
| Session Logout | Destroys the session of the user in Access Gateway. |
| Clear Cache | Disables caching. |
| Header | Adds headers to the request as specified in the configuration. |
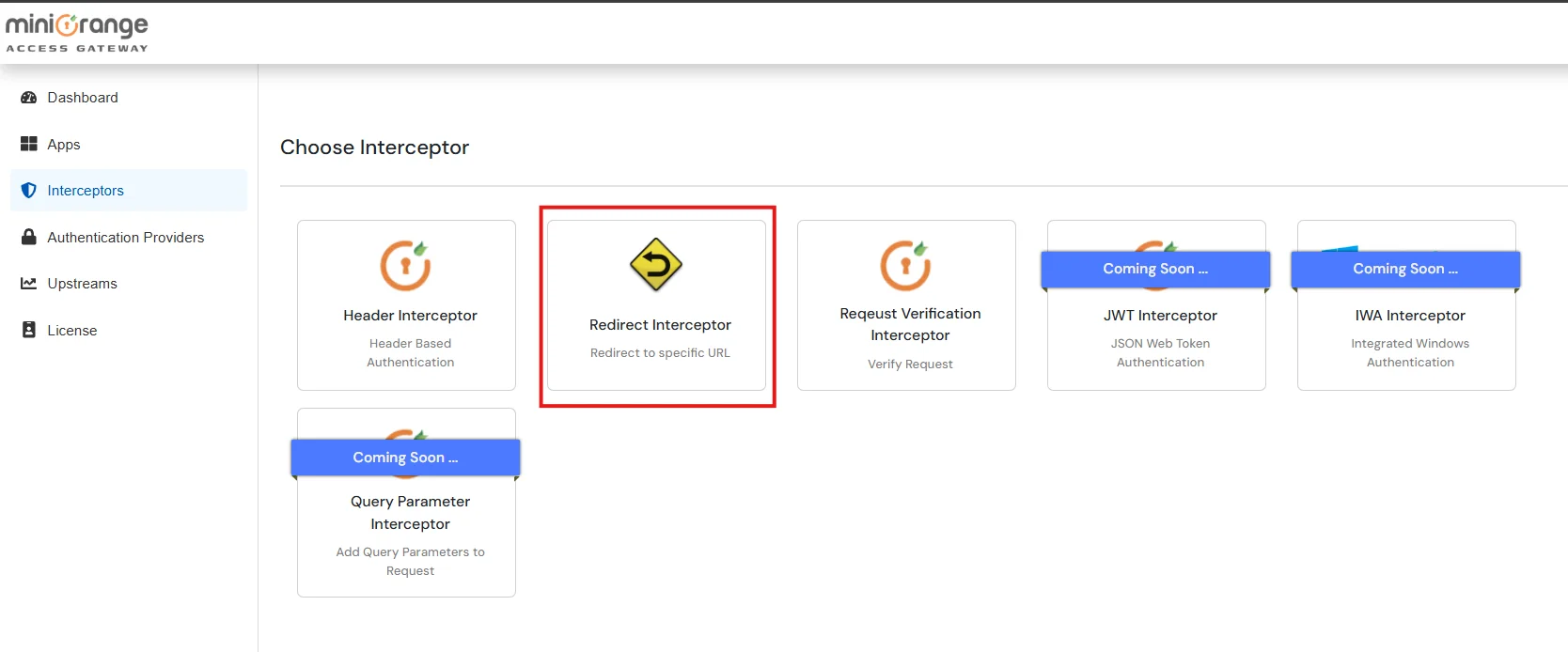
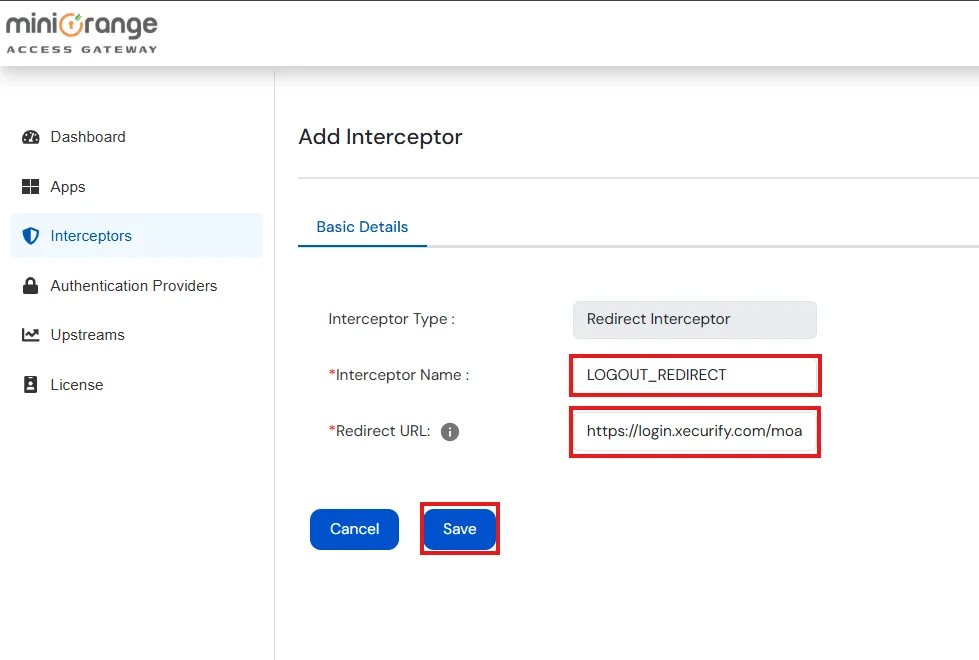
| Redirect | Redirects to the specified URL instead of forwarding the request to the upstream server. |
| Request Verification |
Checks for a specific parameter in the request body.
|