Need Help? We are right here!
Search Results:
×






Network devices such as firewalls, routers, and switches serve as the frontline defenders of an organization's network infrastructure, safeguarding sensitive data, critical applications, and proprietary information from cyber threats. These devices enforce security policies, regulate network traffic, and ensure secure communication between devices within the network. However, if attackers successfully compromise network devices, the impacts can be severe and far-reaching. Breaches of network devices can lead to data breaches, operational disruptions, financial losses, reputational damage, and regulatory consequences.
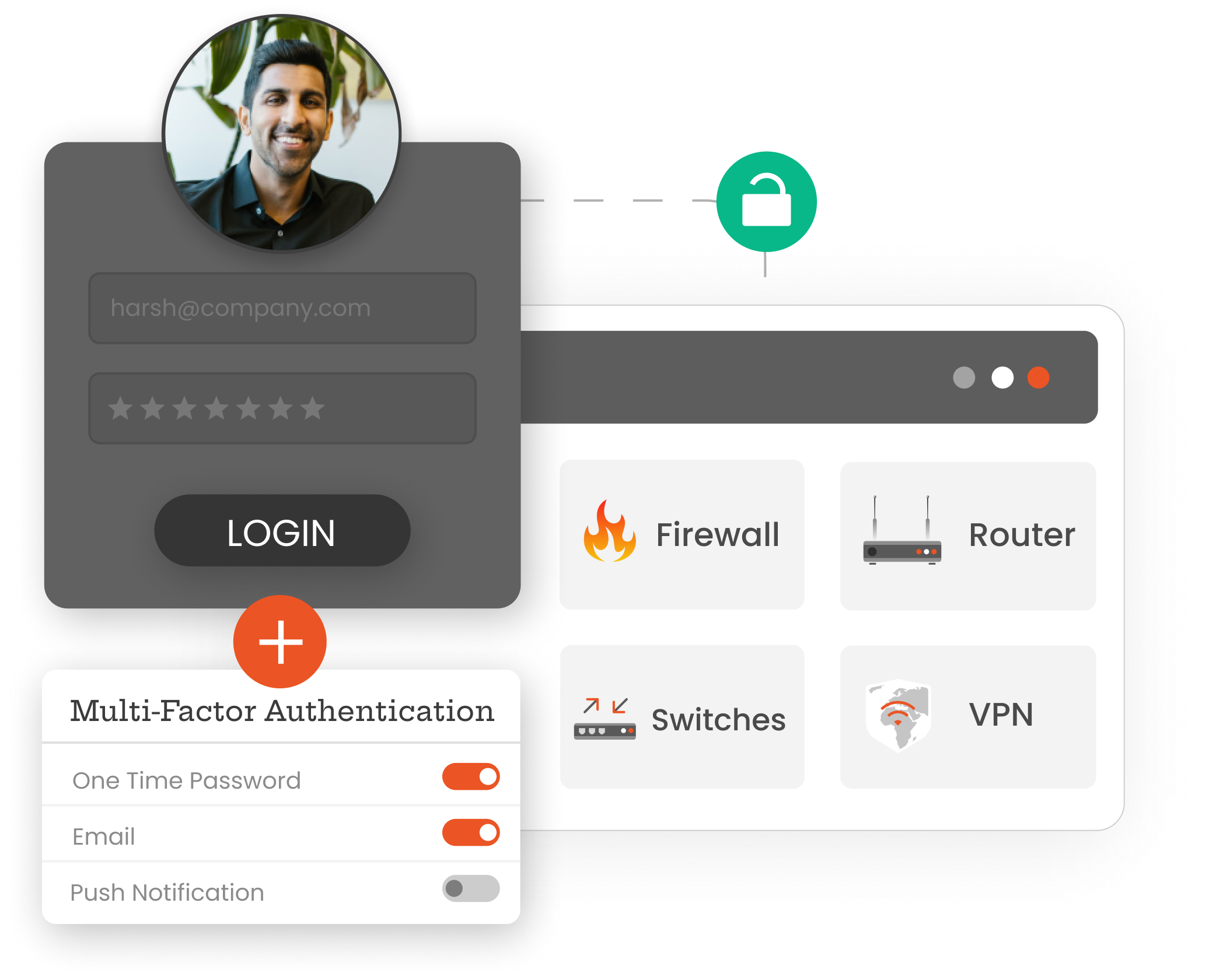
Stop password spraying, brute force attacks, and stolen credential exploitation with multi-layered authentication that requires physical possession of approved devices alongside traditional login credentials.
Meet stringent compliance requirements, including SOC 2, ISO 27001, and industry-specific regulations with comprehensive audit trails and policy enforcement for all network device access.
Defend against sophisticated attack vectors, including credential stuffing, phishing, and lateral movement, with adaptive authentication that analyzes user behavior and device context in real-time.
Integrate effortlessly with existing network management workflows through RADIUS, TACACS+, and LDAP protocols while maintaining high availability and performance across your entire infrastructure.
Secure perimeter defense systems with multi-factor authentication, preventing unauthorized access to firewall configurations, rule modifications, and security policy changes that protect organizational boundaries.
Protect routing infrastructure and network traffic management systems with advanced MFA, ensuring only verified administrators can modify routing tables, configure protocols, and manage connectivity.
Safeguard network switching infrastructure with robust authentication controls, preventing unauthorized VLAN modifications, port configurations, and network segmentation changes that maintain operational integrity and security.
Secure broadband and dial-up connection devices with multi-layered authentication, protecting internet gateway configurations, connection parameters, and network access points from unauthorized administrative changes.
Fortify wireless network infrastructure with comprehensive MFA protection, ensuring only authorized personnel can modify wireless configurations, security settings, and network access controls for WiFi.





I can't speak highly enough regarding miniOrange, I am totally satisfied with the process and results in every regard.
5.0

Awesome tech service, Awesome product. Overall Awesome people. This solution is very simple and easy to implement
5.0
Complete protocol compatibility ensures seamless integration with existing network infrastructure, supporting PAP, MSCHAPv2, EAP, RadSec for RADIUS, and PAP, ASCII for TACACS+.
Flexible security options include SMS OTP, push notifications, hardware tokens, biometric verification, and the miniOrange Authenticator app for enhanced network device protection.
The comprehensive AAA framework provides separate authentication, authorization, and accounting processes with full packet encryption, reliable TCP communication, and detailed audit trails.
*Please contact us to get volume discounts for higher user tiers.
Multi-factor authentication creates multiple security barriers, significantly reducing the risk of unauthorized access even when credentials are compromised, protecting critical network infrastructure from cyber threats.
Eliminate risks from disgruntled employees, contractors, or compromised internal accounts by requiring additional verification factors beyond traditional passwords for all network device access attempts.
Avoid expensive security breaches, downtime costs, and recovery expenses by implementing proactive multi-factor authentication that prevents unauthorized network device access at a fraction of breach costs.
