SumoLogic SIEM Integration Setup
SumoLogic SIEM is a cloud-based security solution that detects threats in real time, analyzes event and incident log data from all security tools. miniOrange provides secure access and full control to SumoLogic for enterprises and applications. With the help of the given guide you can configure SumoLogic easily.
Get Free Installation Help
miniOrange offers free help through a consultation call with our System Engineers to setup SIEM integration with your SumoLogic Instance in your environment with 30-day free trial.
For this, you need to just send us an email at idpsupport@xecurify.com to book a slot and we'll help you in no time.
1. Configure HTTP Collector Endpoint
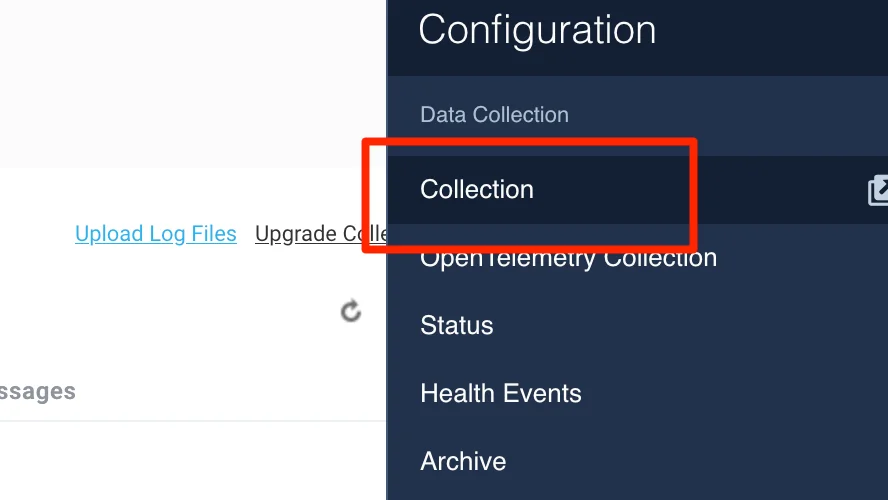
- Classic UI. In the main SumoLogic menu, select Manage Data > Collection > Collection.
New UI. In the SumoLogic top menu select Configuration, and then under Data Collection select Collection. You can also click the Go To... menu at the top of the screen and select Collection.
- In the Collectors page, click Add Source next to a Hosted Collector.
- Select HTTP Logs & Metrics.
- Enter a Name to display for the Source in the Sumo web application. Description is optional.
- Make sure to set Message Processing as Multiline Processing.
- Hit Save to save your Collector.
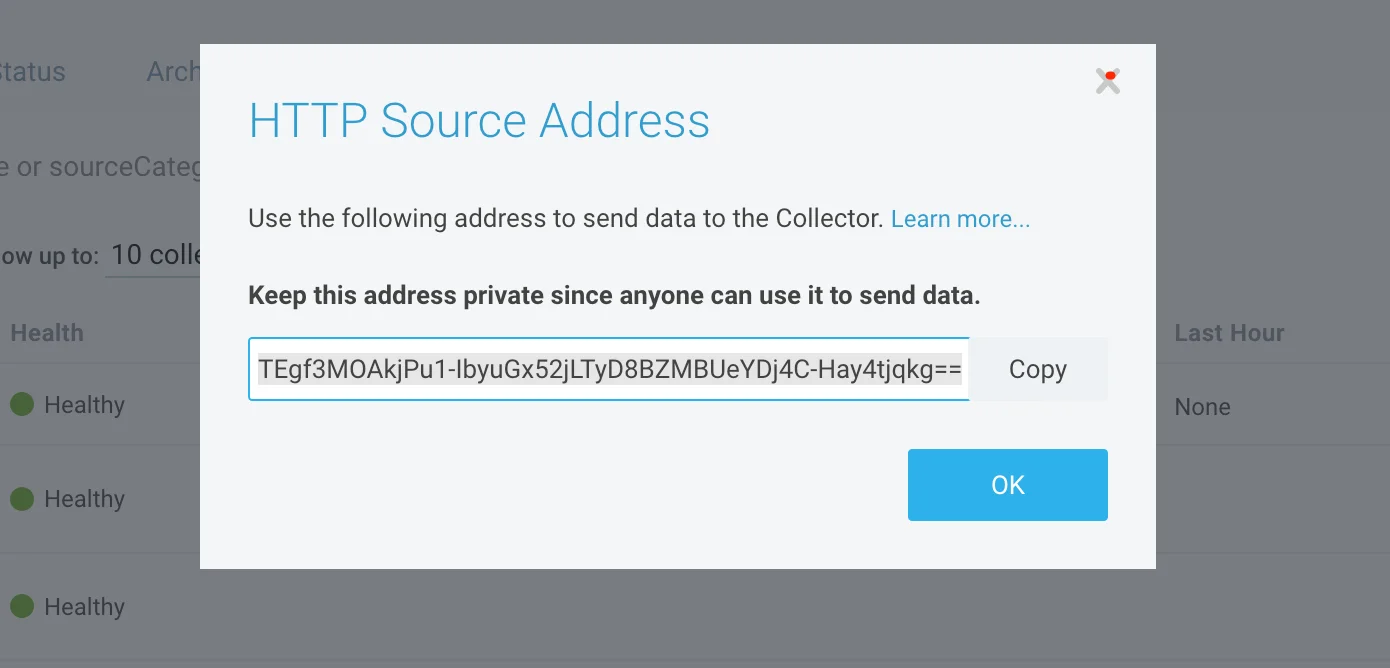
- Copy the endpoint by clicking on the Show URL link.
2. Configure SUMO Logic API Endpoint in miniOrange
3. Sample Search Filters
1. Filter Query for MFA Audits
_source=##name_of_your_source##
| where audit.audittype = "MFA_AUDIT"
| audit.target.identifier as Identifier
| audit.status as Status
| fromMillis(audit.createdDttm) as Time
| formatDate(Time,"dd/MM/yyyy HH:mm:ss") as FormattedTime
| count by Identifier, Status, FormattedTime
| fields -_count
2. Filter Query for Admin Audits
_source=##name_of_your_source##
| where audit.auditType = "ADMIN_AUDIT"
| audit.status as Status
| audit.target.identifier as Identifier
| audit.eventType as EventType
| count by Identifier, EventType, Status
| fields -_count
3. Filter Query for Password Reset Audits
_source=##name_of_your_source##
| where audit.auditType = "ADMIN_AUDIT"
| where audit.eventType = "Password Reset"
| audit.target.identifier as Identifier
| auditValue as AuditMessage
| audit.status as Status
| fromMillis(audit.createdDttm) as temptime
| formatDate(temptime,"dd/MM/yyyy HH:mm:ss") as FormattedTime
| count by Identifier, AuditMessage, Status, FormattedTime
| fields -_count
