Need Help? We are right here!
Need Help? We are right here!
Thanks for your Enquiry. Our team will soon reach out to you.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
Search Results:
×Laravel Passport Single Sign On (SSO) for Your Application miniOrange provides a ready to use solution for Your application. This solution ensures that you are ready to roll out secure access to your application using Laravel Passport within minutes.
miniOrange offers free help through a consultation call with our System Engineers to configure SSO for different apps using Laravel Passport as IDP in your environment with 30-day free trial.
For this, you need to just send us an email at idpsupport@xecurify.com to book a slot and we'll help you in no time.
composer create-project --prefer-dist laravel/laravel blog
composer require laravel/passport
Laravel\Passport\PassportServiceProvider::class,
namespace App;
use Laravel\Passport\HasApiTokens;
use Illuminate\Contracts\Auth\MustVerifyEmail;
use Illuminate\Foundation\Auth\User as Authenticatable;
use Illuminate\Notifications\Notifiable;
class User extends Authenticatable
{
use HasApiTokens, Notifiable;
/**
* The attributes that are mass assignable.
*
* @var array
*/
protected $fillable = [
'name', 'email', 'password',
];
/**
* The attributes that should be hidden for arrays.
*
* @var array
*/
protected $hidden = [
'password', 'remember_token',
];
/**
* The attributes that should be cast to native types.
*
* @var array
*/
protected $casts = [
'email_verified_at' => 'datetime',
];
}
namespace App\Providers;
use Laravel\Passport\Passport;
use Illuminate\Foundation\Support\Providers\AuthServiceProvider as ServiceProvider;
use Illuminate\Support\Facades\Gate;
class AuthServiceProvider extends ServiceProvider
{
/**
* The policy mappings for the application.
*
* @var array
*/
protected $policies = [
// 'App\Model' => 'App\Policies\ModelPolicy',
];
/**
* Register any authentication / authorization services.
*
* @return void
*/
public function boot()
{
$this->registerPolicies();
Passport::routes();
//
}
}
'guards' => [
'web' => [
'driver' => 'session',
'provider' => 'users',
],
'api' => [
'driver' => 'passport',
'provider' => 'users',
'hash' => false,
],
],
Which user ID should the client be assigned to?:
> 1
What should we name the client?:
> Demo OAuth2 Client Account
Where should we redirect the request after authorization? [https://localhost/auth/callback]:
> https://localhost/oauth2_client/callback.php
New client created successfully.
Client ID: 1
Client secret: zMm0tQ9Cp7LbjK3QTgPy1pssoT1X0u7sg0YWUW01
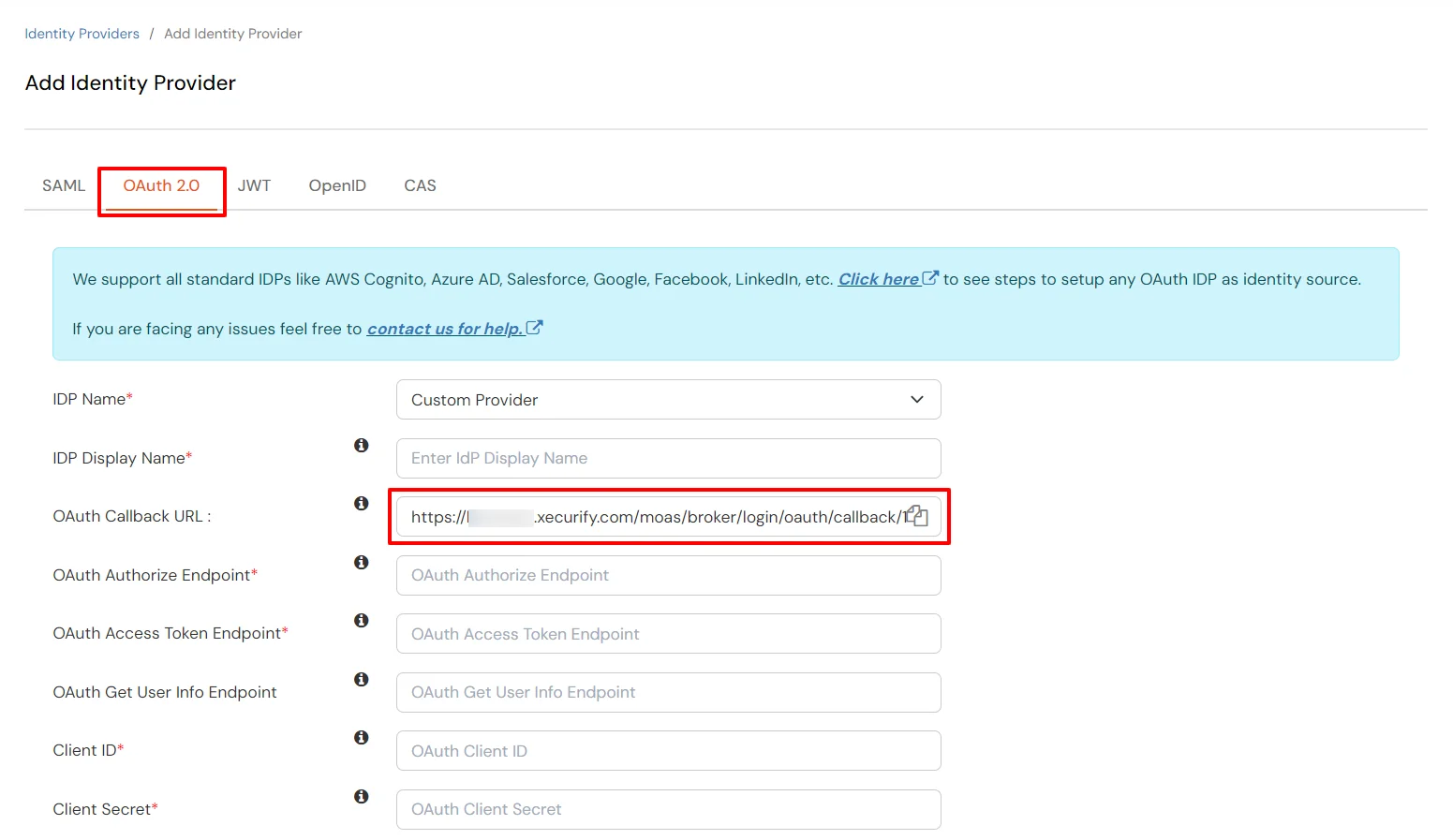
| IdP Name | Custom Provider |
| IdP Display Name | Choose appropriate Name |
| OAuth Authorize Endpoint | https://your-laravel-site-url/oauth/authorize | OAuth Access Token Endpoint | https://your-laravel-site-url/oauth/token | OAuth Get User Info Endpoint (optional) | https://your-laravel-site-url/api/user/get |
| Client ID | From step 1 |
| Client secret | From step 1 |
| Scope | auto |
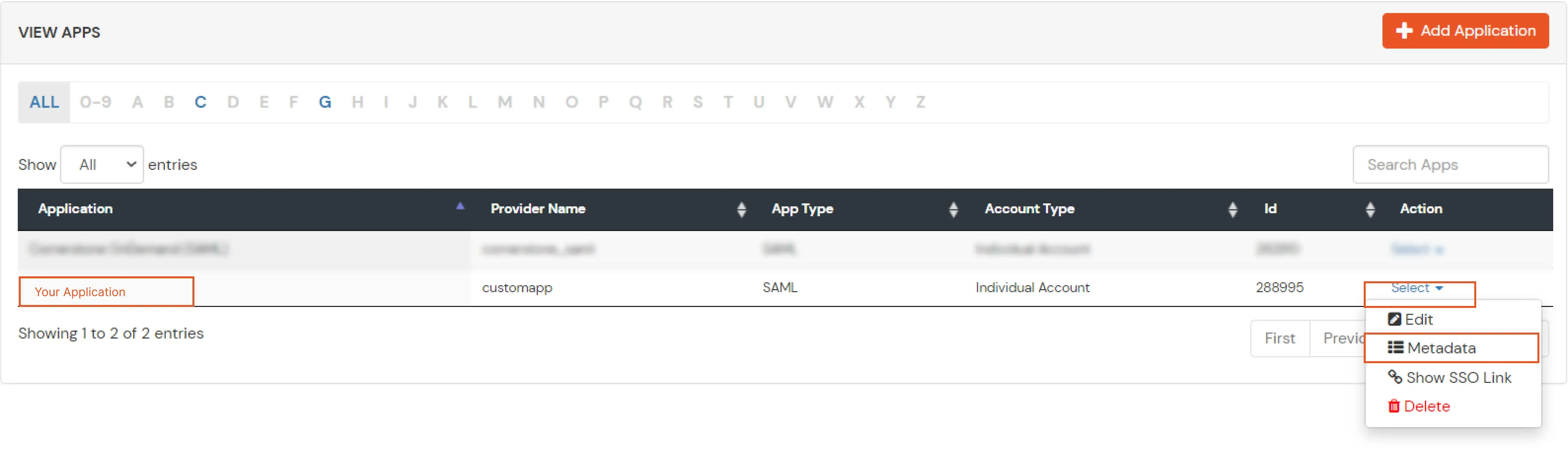
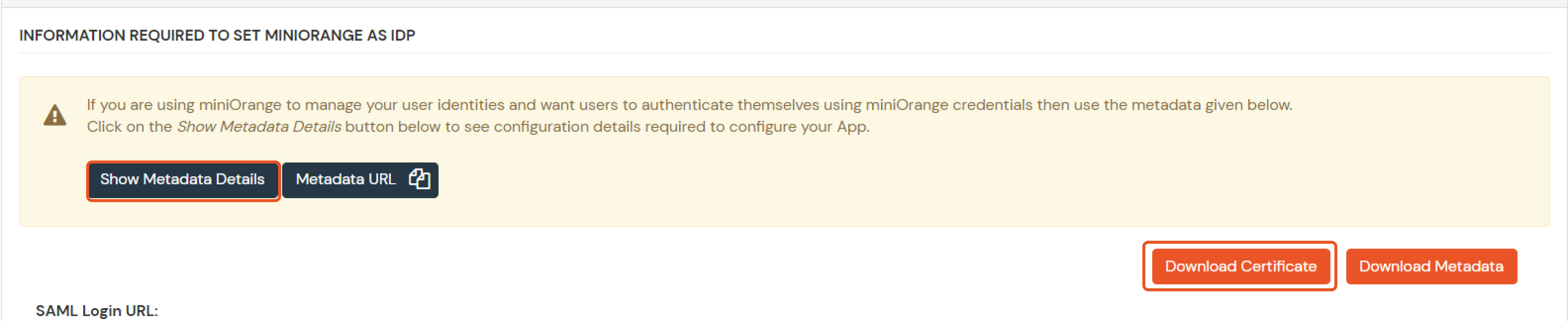
If you have already configured your application in miniOrange you can skip the following steps.
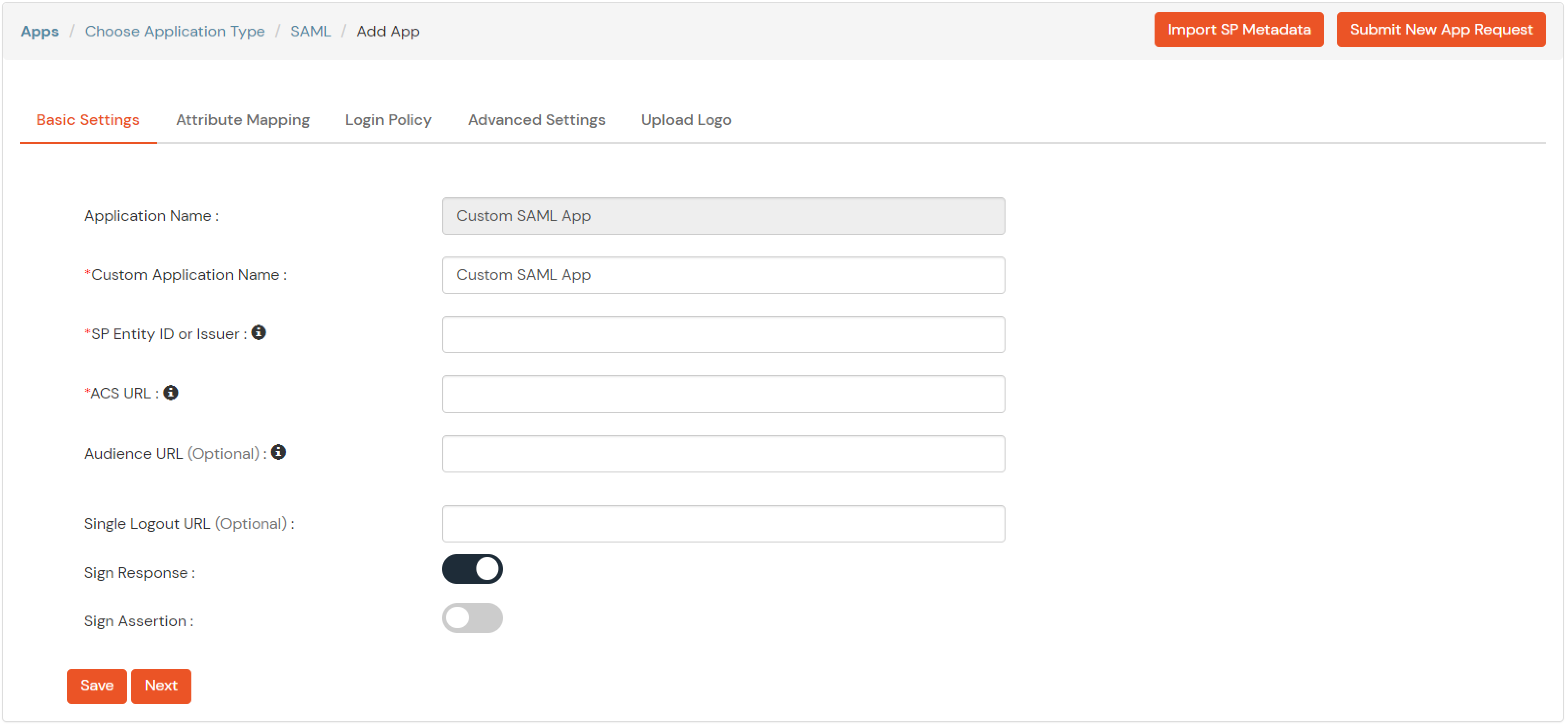
| Service Provider Name | Choose appropriate name according to your choice |
| SP Entity ID or Issuer | Your Application Entity ID |
| ACS URL X.509 Certificate (optional) | Your Application Assertion Consumer Service URL |
| NameID format | Select urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress |
| Response Signed | Unchecked |
| Assertion Signed | Checked |
| Encrypted Assertion | Unchecked |
| Group policy | Default |
| Login Method | Password |

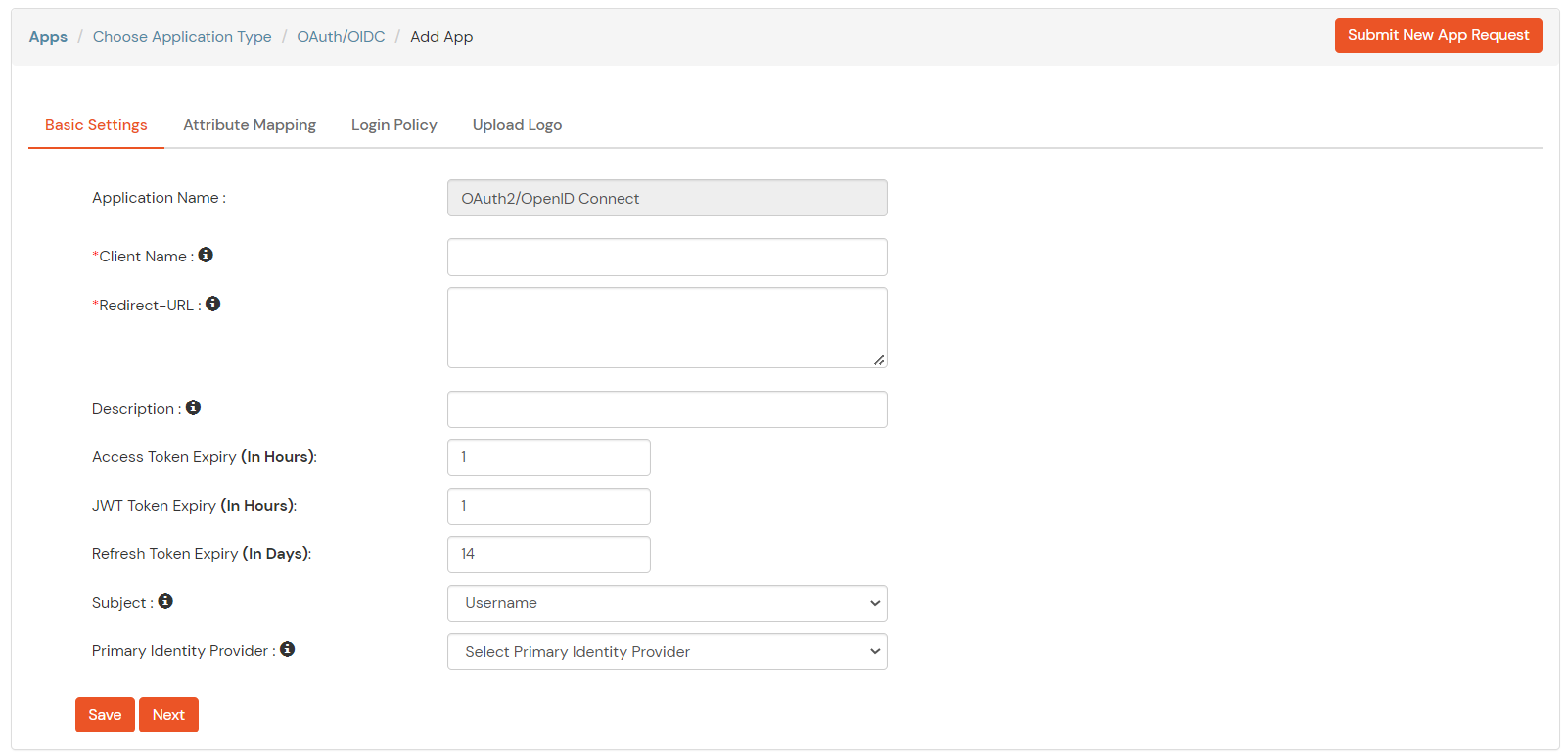
| Client Name | Add appropriate Name |
| Redirect URL | Get the Redirect-URL from your OAuth Client |
| Description | Add if required |
| Group Name | Default |
| Policy Name | As per your Choice |
| Login Method | Password |
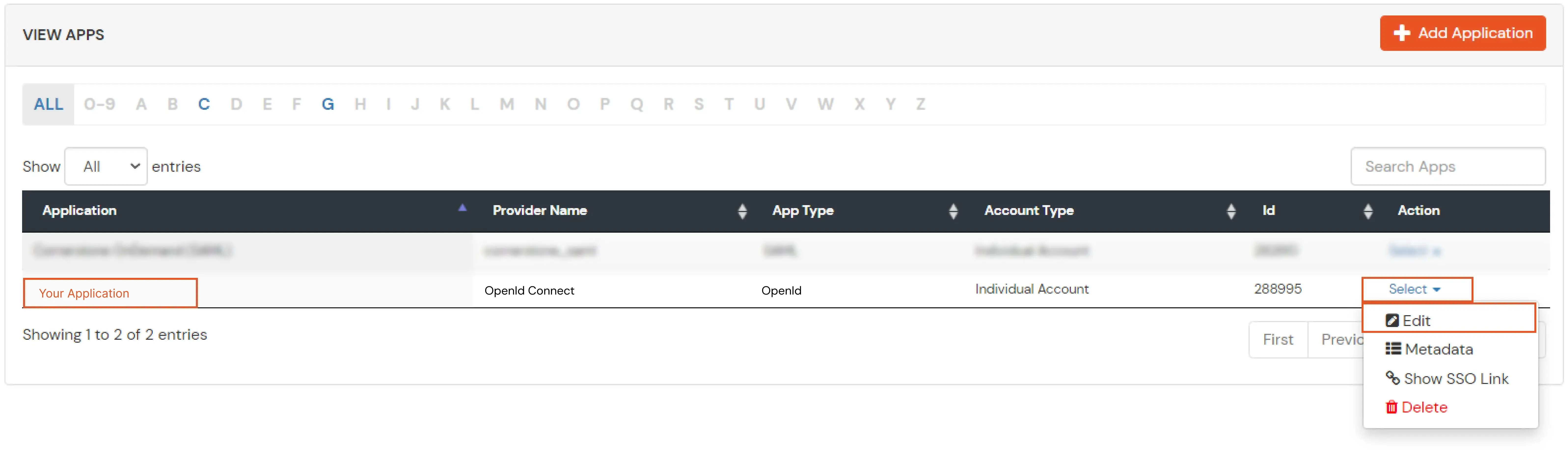
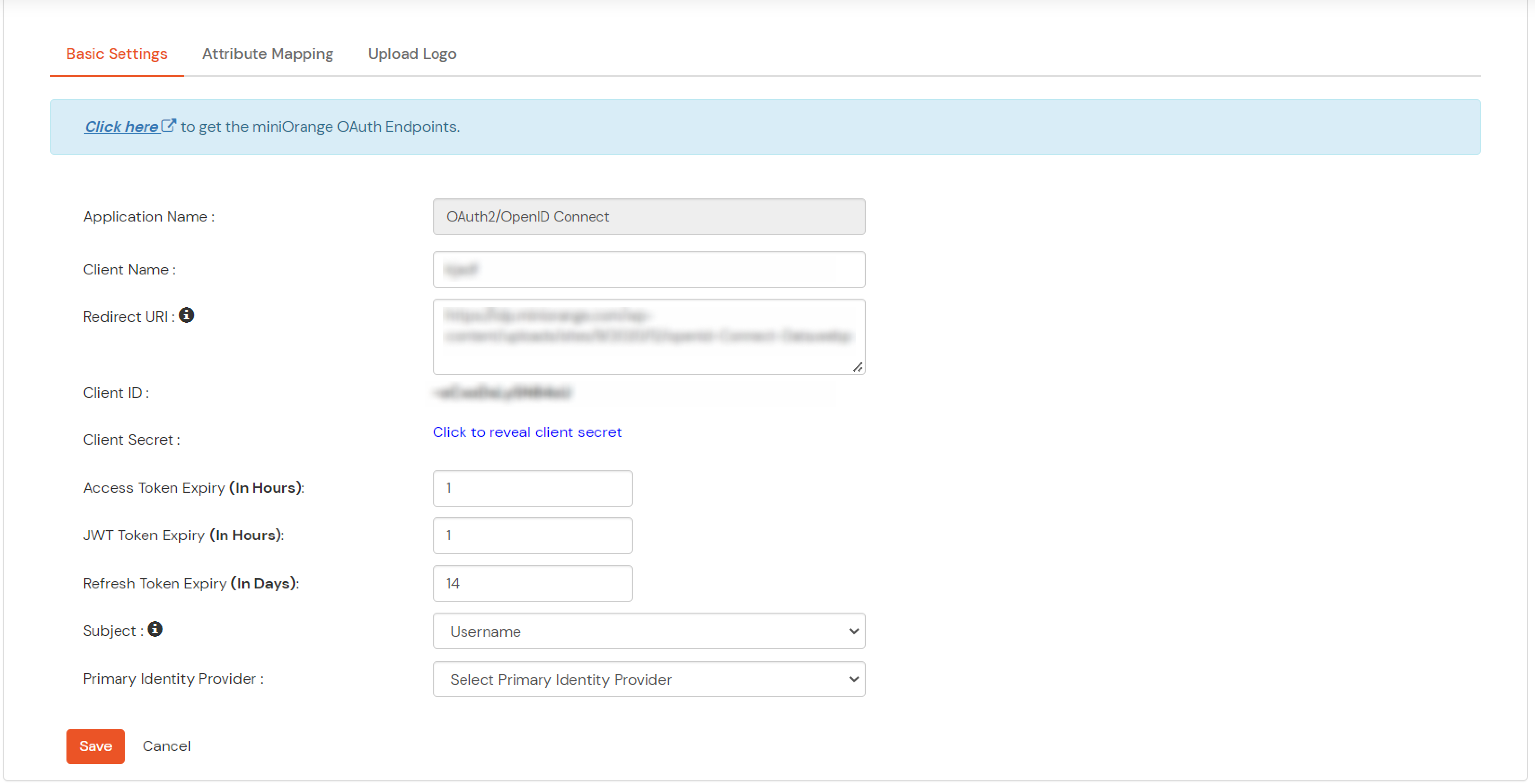
Note: Choose the Authorization Endpoint according to the identity source you configure.
https://{mycompany.domainname.com}/moas/idp/openidssohttps://{mycompany.domainname.com}/broker/login/oauth{customerid}
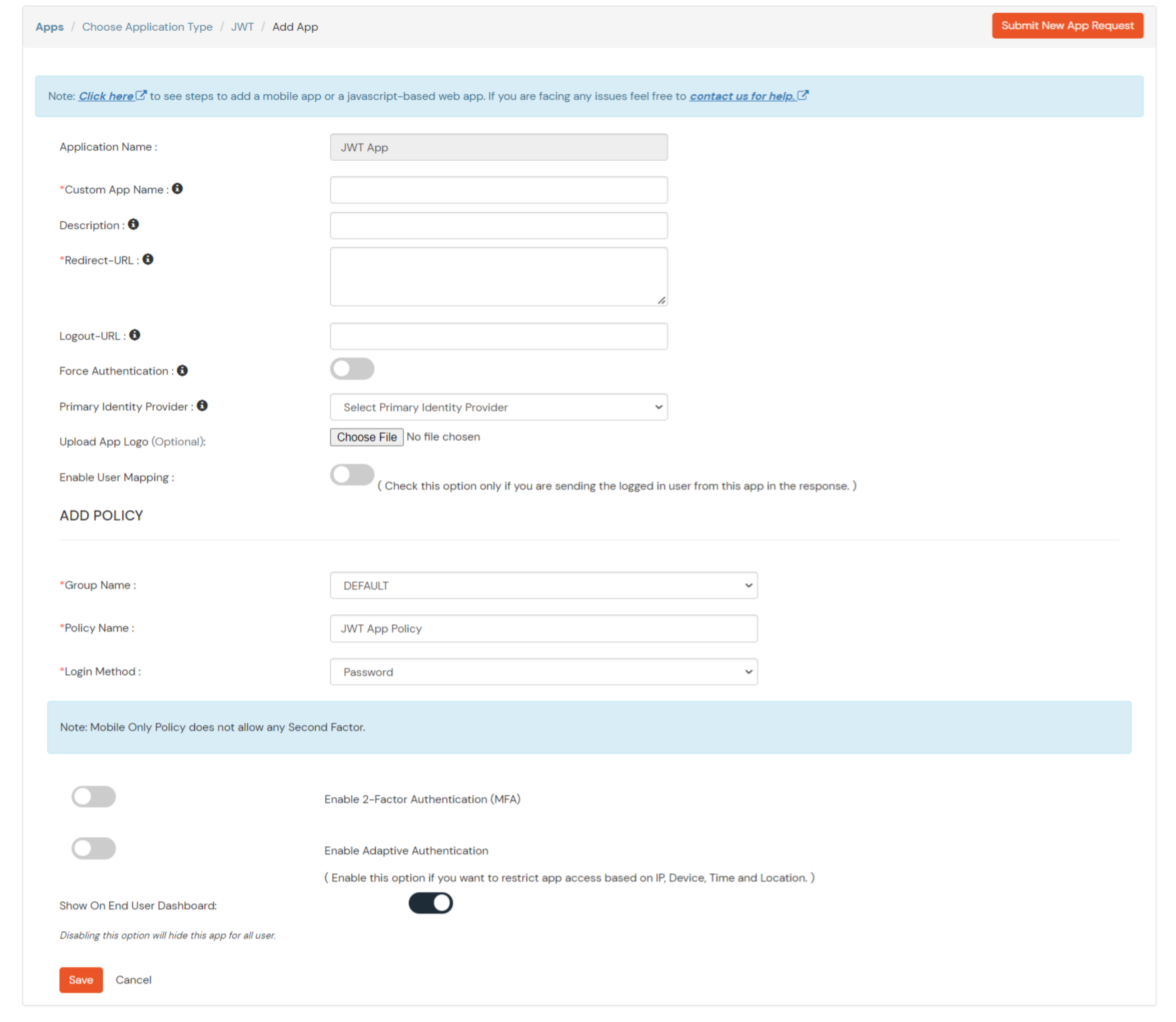
In case you are setting up SSO with Mobile Applications where you can't create an endpoint for Redirect or Callback URL, use below URL.
https://login.xecurify.com/moas/jwt/mobile
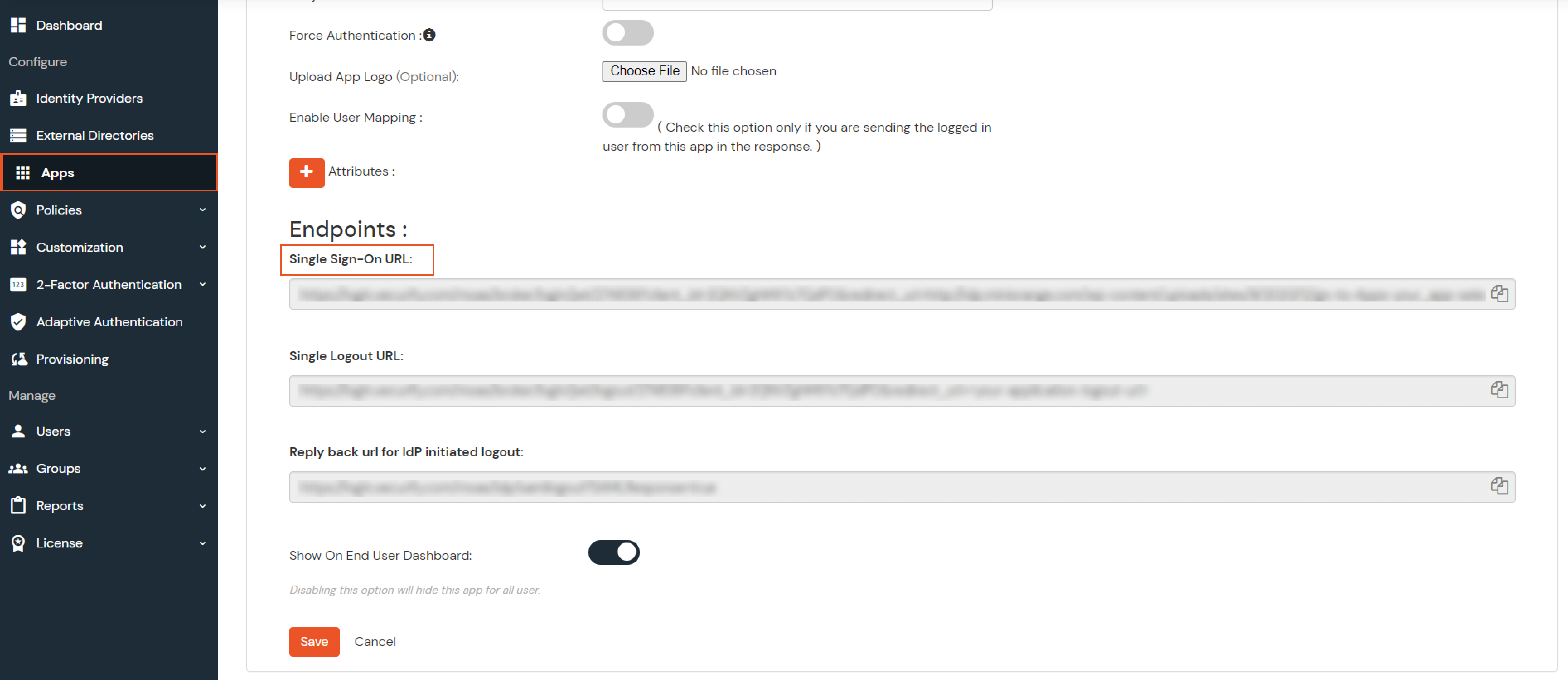
Few usecases where customers configure multiple IDPs -
| For Cloud IDP - | https://login.xecurify.com/moas/discovery?customerId=<customer_id> |
| For On-Premise IDP - | https://yourdomain.com/discovery?customerId=<customer_id> |
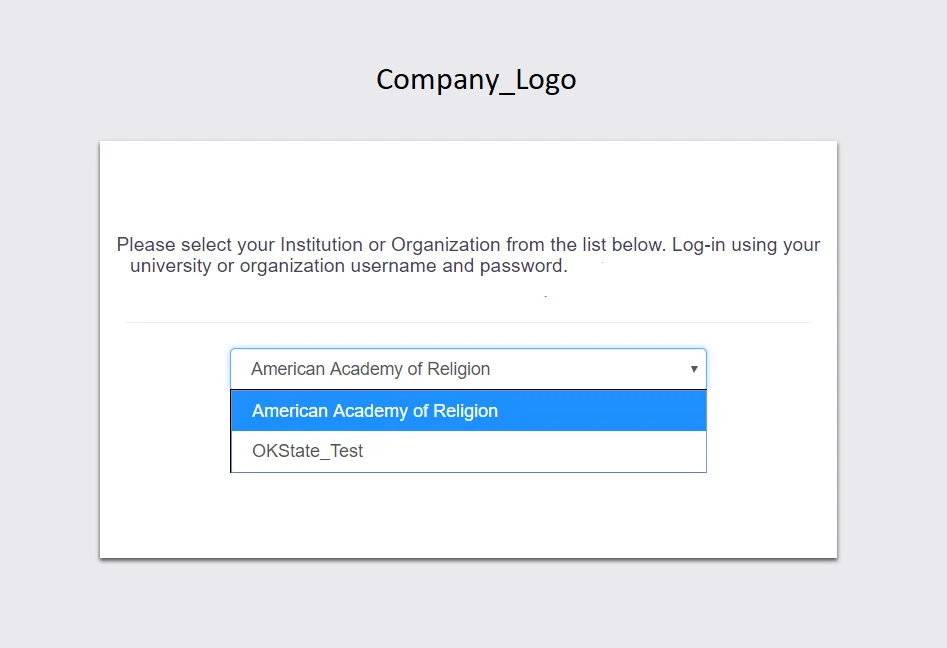
You can see the screenshot below of the IDP Selection Page with a list of IDPs.
Note: To view the IDP in drop-down list, go to Identity Providers tab > against your configured IDP > Select >Edit , here Enable the Show IdP to Users option.