Need Help? We are right here!
Need Help? We are right here!
Thanks for your Enquiry. Our team will soon reach out to you.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
Search Results:
×Cybersecurity grew into a major problem during the pandemic as remote workers provided ample new opportunities for attacks. As a result, companies are concerned more than ever about IAM services like SSO, MFA, etc.
In this document, we will introduce you to one such SSO protocol OAuth 2.0, how it works, what is it used for, how JWT comes into the picture, how can your organization benefit by using OAuth 2.0 and, JWT as part of your IAM system.
OAuth 2.0 (Open Authorization) is an authorization framework that enables applications to obtain limited access to user accounts on an HTTP service. It delegates user authentication to the service that hosts the user account and authorizes third-party applications to access the user account.
OAuth 2.0 provides authorization flows for web and desktop applications, and mobile devices.
This page contains detailed information about the OAuth 2.0 endpoints that miniOrange exposes on its authorization servers.
OpenID Connect (OIDC) is a thin identity layer on top of the OAuth 2.0 protocol for handling user authentication. OAuth 2.0 is the standard protocol for authorization and OIDC the protocol for authentication of users. Together, these two protocols enable you to access multiple apps and websites in a safe way, without having to log in several times, through single sign-on (SSO).
To learn about the OpenID Connect protocol visit this page.
JWT (JSON Web Token) is an open standard (RFC 7519) that defines a compact and self-contained way for securely transmitting information between parties as a JSON object. This information can be verified and trusted because it is digitally signed using a secret (with the HMAC algorithm) or a public/private key pair using RSA or ECDSA.
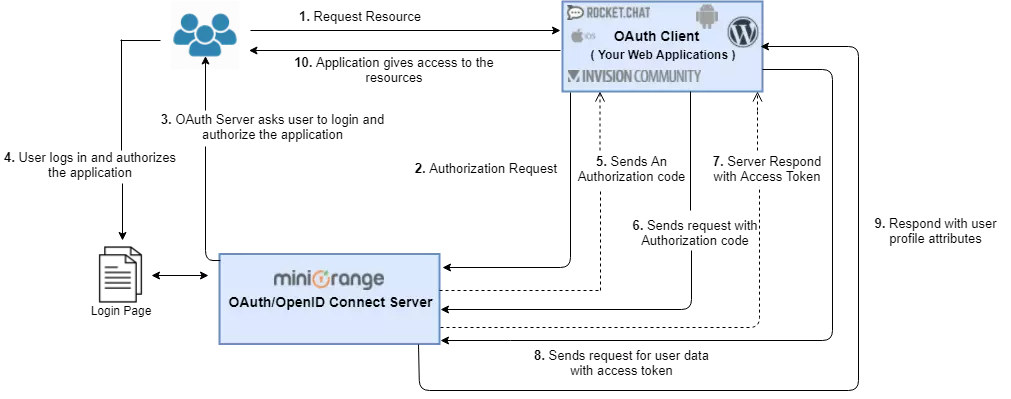
In this scenario, you can achieve Single Sign On (SSO) into your web application using miniOrange IdP with OAuth 2.0 / OpenID Connect (OIDC) protocol. Your web application will act as an OAuth 2.0 client.
JWT (JSON Web Token, usually referred to as id_token) contains the user’s identity data. It is used by the client application to get user information like the user’s name, email address, etc. On your Callback endpoint, you can read and parse the JWT token (User info). Structure of JSON Web Token (JWT):
JWT consists of three parts separated by dots (.)
(eg - xxxx.yyyyyyyyyyyy.zzzzzz), which are:
Once you have the user info JSON. You can initiate your login by passing the email/username information to your local authentication functionality.
JWT contains the following JSON attributes:
| Field | Description |
|---|---|
| iss | HTTPS URI that indicates the issuer |
| sub | identifier of the user at the issuer |
| aud | client_id of the requesting client |
| nonce | the nonce parameter value received from the client |
| exp | expiration time of this token |
| iat | The time when this token was issued |
| auth_time | time the authentication happened |
| at_hash | the first half of a hash of the access token |
miniOrange can help you enable SSO using OAuth 2.0 protocol for the following scenarios -
If you want to improve your business & reduce the burden of maintaining multiple credentials for an account that uses multiple services or just want to get to know us better, we’d love to hear from you.

Our Other Identity & Access Management Products