Need Help? We are right here!
Search Results:
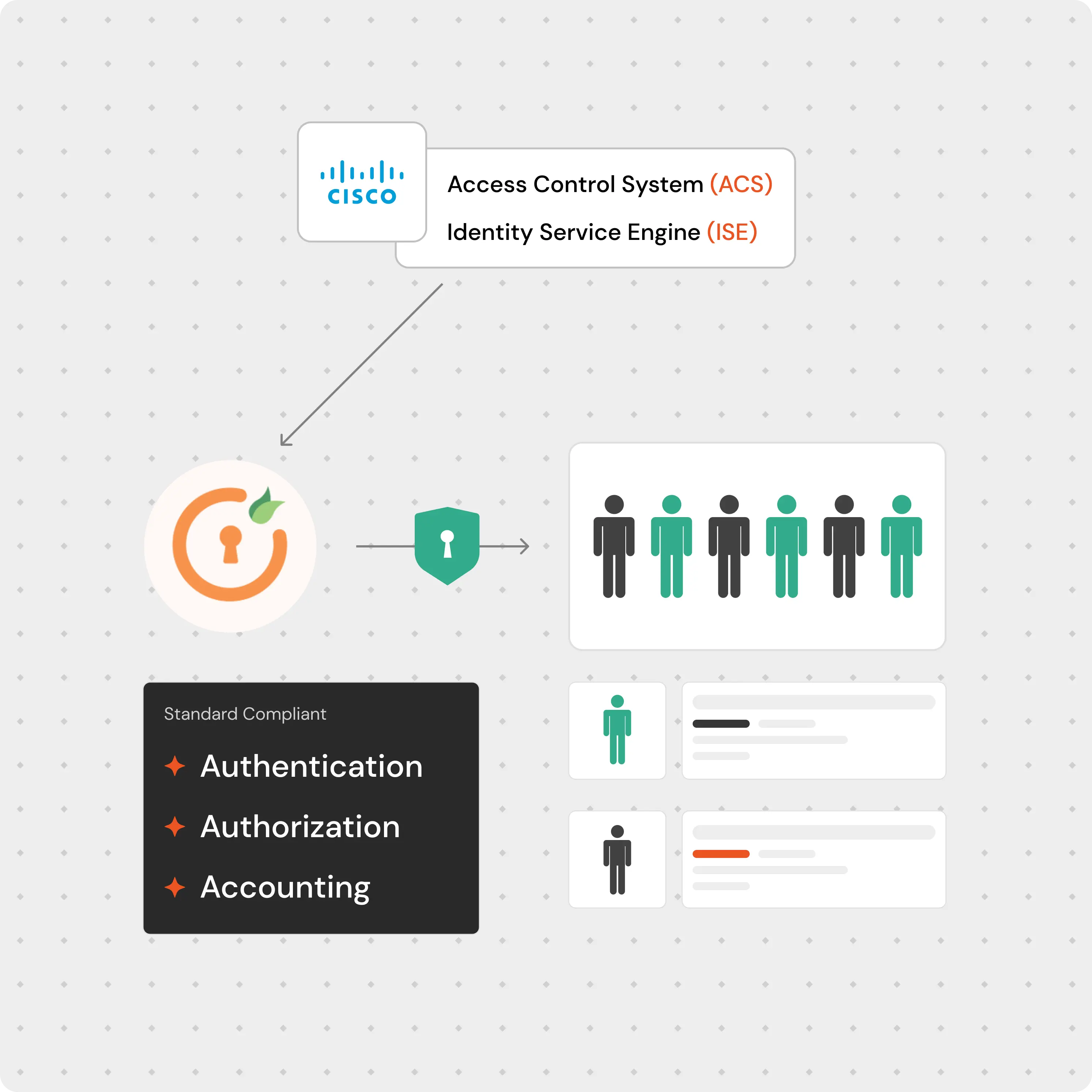
×TACACS, which stands for Terminal Access Controller Access-Control System, is a network protocol that was developed by Cisco. TACACS+ is an improved version of the original TACACS protocol, which is now popularly used in the industry for Authentication, Authorization, and Accounting (AAA) in network security.
TACACS/TACACS+ Authentication controls user access to devices like routers, NAS, and switches, separating authentication and allowing fine-grained access control. With encryption and support for command authorization, it significantly improves the security of enterprise networks.
Authentication is the action of determining who a user (or entity) is. Traditional authentication utilizes a username and a fixed password. However, fixed passwords have limitations. Many modern authentication mechanisms utilize "one-time" passwords or challenge-response queries. TACACS+ is designed to support all of these and be powerful enough to handle any future mechanisms.
Authorization is the action of determining what a user is allowed to do. TACACS+ authorization might provide yes or no answers regarding access to the required resource. It may also customize the service for a particular user based on the user’s requirements. The TACACS+ server might respond to these requests by allowing the service or placing a time restriction on the login shell.
Accounting is typically the third action after authentication and authorization. It is the action of recording what a user is doing, and/or has done. TACACS+ Accounting can serve two purposes. It may be used as an auditing tool for security services. Otherwise, It may also be used to account for services used, such as in a billing environment.
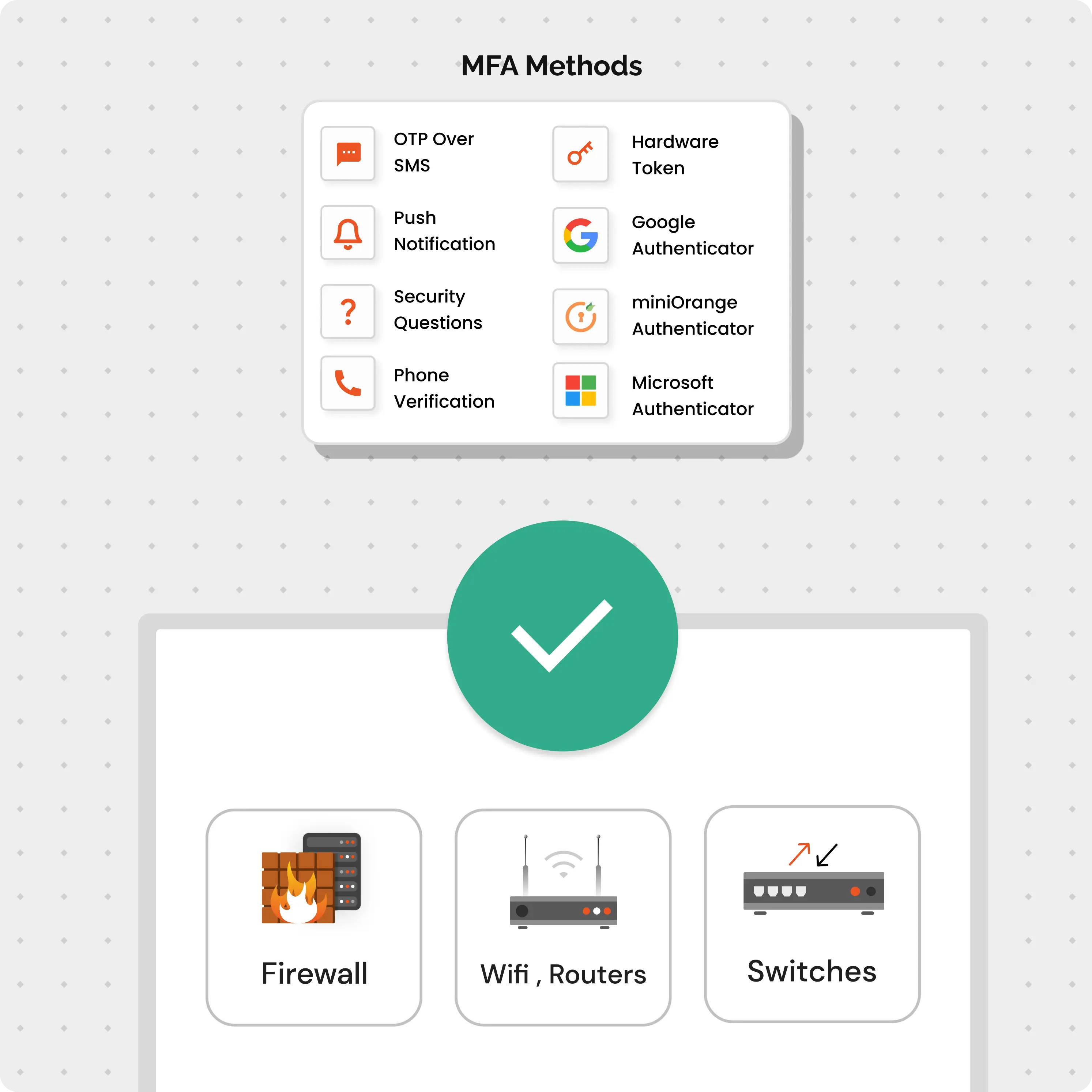
Secure authentication for all environments, protecting identity & data wherever users go. Protect your network devices with 15+ MFA methods like OTPs, physical tokens, & authenticator apps.
Administrators have more flexibility, visibility, and control. The solution is simple for end users to verify their identity when accessing network devices.
It is easy to set up user groups with different access to different equipment sets. Existing AD groups and users are fully supported, too.
Easily Integrate your existing LDAP/Active Directory in miniOrange to provide users login using their existing credentials and secure access to applications.
Whether you have Cisco, Juniper, Nokia, or other leading network devices, the miniOrange TACACS/TACACS+ solution offers cross-platform compatibility, ensuring consistent authentication across your entire network infrastructure.
Cisco Access Control System (ACS) is renowned for providing policy-based security services, offering standards-compliant Authentication, Authorization, and Accounting (AAA) for your network. With ACS, you can control user access and maintain stringent security policies.
Cisco Identity Services Engine (ISE) functions as a comprehensive security policy management platform, serving as a policy decision point that allows enterprises to enforce compliance, bolster infrastructure security, and optimize service operations.
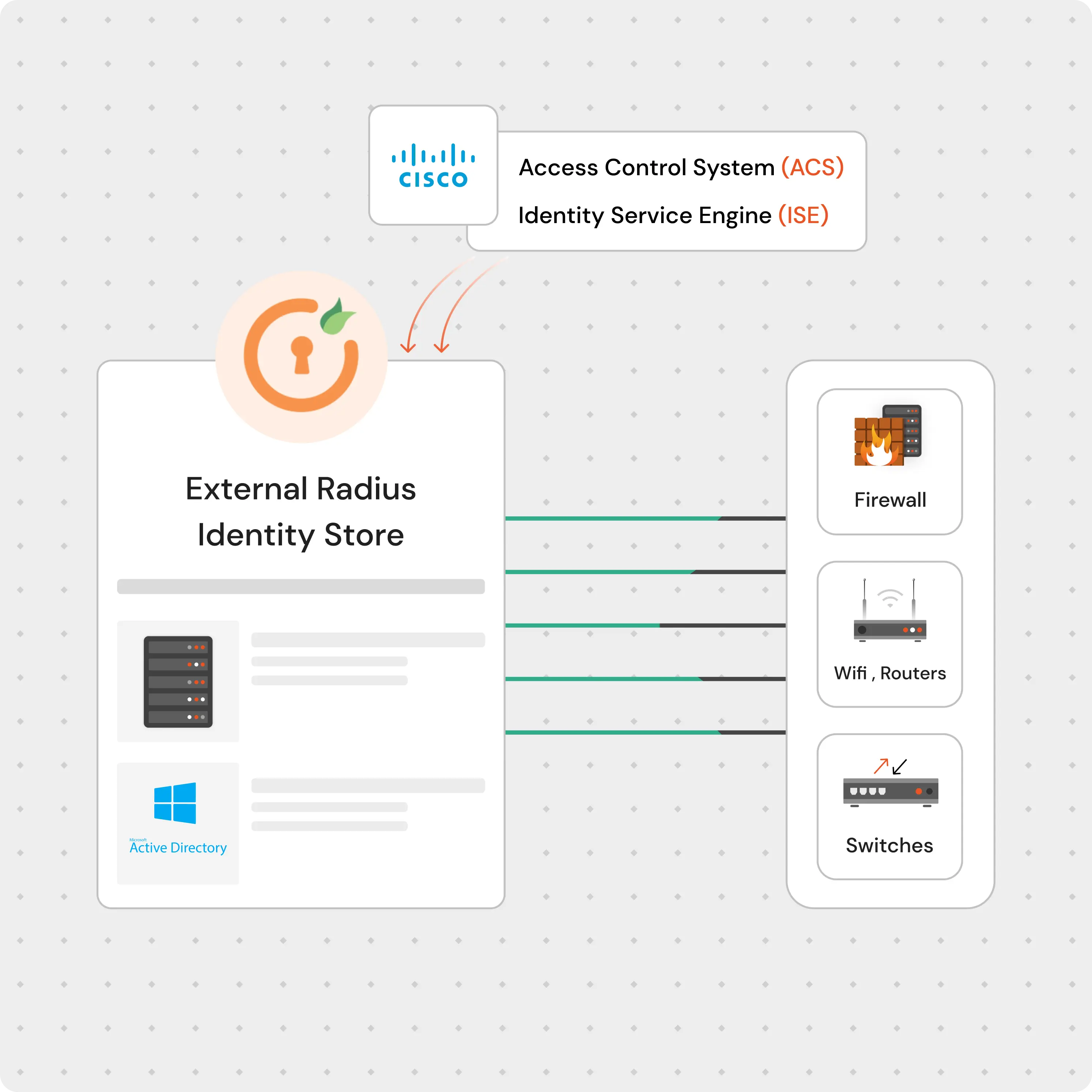
As an External RADIUS Identity Store for ACS/ISE, miniOrange streamlines your authentication process, enabling secure access to network resources across a wide range of network devices.
Connect your ACS/ISE to external identity stores such as LDAP, Microsoft AD, and RADIUS Identity Stores effortlessly. miniOrange ensures a seamless integration process, saving you time and effort.
Embrace flexibility with over 15 authentication methods, including OTP over SMS, Email, Push Notifications, and more. Our solution offers versatile options to cater to your unique user needs.
Leverage the robust capabilities of TACACS/TACACS+ authentication to fortify your network against unauthorized access and cyber threats.
Our TACACS+ Authentication solution supports Network Devices from Multiple Vendors:
Take your network security to the next level and add Multi-Factor Authentication (MFA) on top of your TACACS+ authentication mechanism to make your enterprise network invincible!
| Differential Factors | RADIUS | TACACS+ |
|---|---|---|
| Authentication vs. Authorization | RADIUS combines Authentication, Authorization & Accounting. | TACACS+ separates Authentication, Authorization, and Accounting. It allows granular access control. |
| Packet Encryption | RADIUS encrypts only the password in the access request packet. | TACACS+ encrypts the entire packet content, ensuring a higher level of security. |
| Packet Structure | Compact packet structure and smaller packet sizes. | Extensive packet structure and accommodates more attributes. |
| Transport Protocol | RADIUS uses UDP, which is faster but may result in data loss. | It uses TCP, which results in reliable and connection-oriented communication. |
| Vendor Support | RADIUS provides broad support, as it's an open-standard protocol. | Traditionally, TACACS+ provides better support on Cisco devices, as it is a proprietary protocol. But it is provided by several other vendors as well. |
| Router Management | Used for router access management in limited scenarios. | Primarily used for router access administration and offers more flexibility. |
| Traffic | Handles less complex traffic. | Suitable for managing more complex. |
| Interoperability | High interoperability. | Limited interoperability compared to RADIUS. |
