Need Help? We are right here!
Search Results:
×Virtual Private Networks (VPN’S) is the primary source of providing Secure Remote Access to Organizational internal and on-premises applications. Basically, VPN acts as an encrypted channel for remote users to connect to the in-house applications. But with the rising cyberattacks, even a username-password based VPN authentication is not immune to the ever-increasing risk of user credential theft.
Organizations that provide users with just a username and password to log into their VPN connections could be exposed to data breaches if those user credentials are stolen. Protecting your organization’s VPN against user credential theft with Multi-Factor Authentication (MFA) adds an additional layer of security for your corporate network. When security is in-depth, with miniorange’s MFA protecting your VPN, you can:








Support almost all RADIUS protocols such as CHAP, PAP, etc to enable Multi-Factor Authentication (MFA) for VPNs.
Reduces authentication burden. Prompts for strong authentication only it's needed foremost. (changed IP, geographical area, device change, network change, etc)
Integrate with any third-party MFA authenticator apps such as Google, Microsoft, Authy, etc for VPN MFA Radius Solution
miniOrange effortlessly integrates with various Directories such as Active Directory, Azure AD, OpenLDAP, and more. Option for Local Authentication if you don’t have any external directories.
Set MFA over specific groups with comprehensive audit features to check audits and monitor user activities for enhanced security.
Enable MFA for your VPN without the need to install a Separate Radius Proxy Module.
miniOrange integrates with a wide range of VPNs and applications and provides secure remote access with an extra layer of Multi-Factor Authentication (MFA) security.
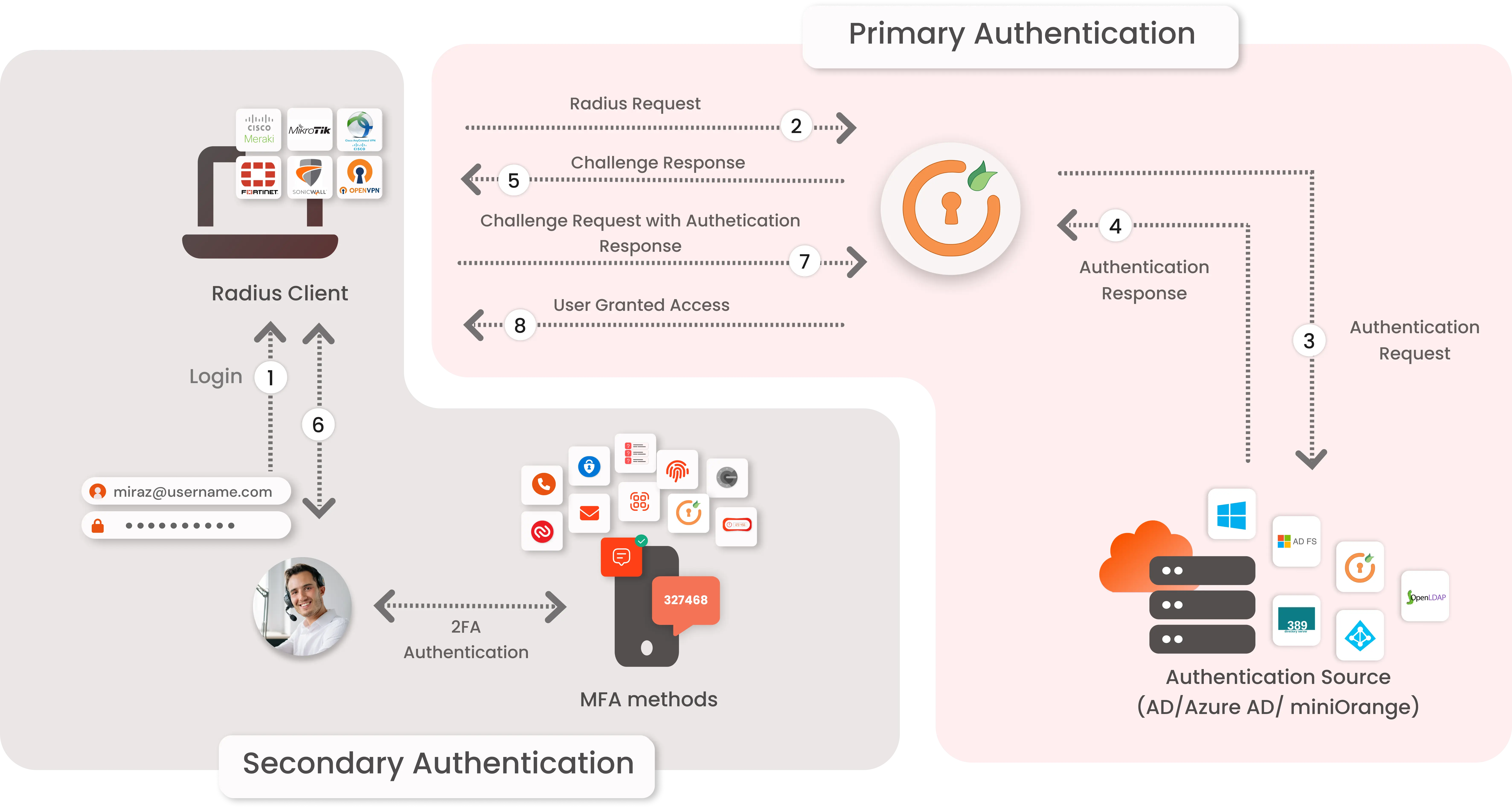
The user submits their username and password to access the VPN.
The VPN forwards the authentication request to the miniOrange RADIUS server.
miniOrange validates the user credentials against Active Directory (AD) or a database.
Upon successful validation, AD confirms the primary authentication to the miniOrange RADIUS server.
miniOrange challenges the user for 2-factor authentication (2FA), sending a code to their device.
The user submits the 2FA code, and miniOrange grants access to the VPN upon successful verification.
*Please contact us to get volume discounts for higher user tiers.
Identity solutions from miniOrange can be easily deployed in your organization's existing environment.
Protect all Active Directory logins with MFA Security. Prevent unauthorized access to all servers by enabling MFA.
Secure your Windows RDP logons, RD Gateway & SSH logins with Multi-Factor Authentication.
Enable MFA on TACACS/TACACS+ logins and all your network devices like routers & Switches.
Prevent unauthorized access to OWA (Outlook on the Web) & RD Web connections.
Enable SSO/MFA for all Office 365 apps on the cloud (Supporting SAML, OAuth, JWT, etc.)
Secure your Virtual Desktop Infrastructure (VDI) (like Citrix, VMWare, etc.) with MFA solution.

Check out VPN MFA Demo to see how you can secure your VPN access with Multi-Factor Authentication.
View DemoSecure authentication for all environments, protecting identity and access to data wherever users go. miniOrange MFA can help secure your VPN via factors such as OTPs (One Time Password), physical tokens, & authenticator apps.
Simplicity for both end-users and administrators. VPN MFA is easy to deploy & gives administrators more flexibility, visibility, and control. miniOrange's MFA for VPN is simple for end-users to verify their identity when accessing VPN.
MFA solution extends and adapts to all areas of your organization. miniOrange's MFA plays a pivotal role in providing visibility in all risk areas, from on-premises networks to mobile devices and the cloud.
NOTE: Bulk Upload would only work if you have completed SMTP configuration in miniOrange.
NOTE: The default behavior doesn’t send out an email to the users. If you wish to change this behavior then you will need to do so under the General Product Settings. You can find it by clicking the clogged wheel at the top right corner of the admin dashboard.
Click here to know more.Windows Server MFA (Multi-Factor Authentication) is a security measure that requires users to verify their identity through two or more methods before gaining access to a Windows Server. This typically combines something the user knows (password) with something they have (a mobile device or token) or something they are (biometric authentication). It enhances security by reducing the risk of unauthorized access, even if passwords are compromised. Please click here to know more: Windows Server MFA
